A Method of Coverage Analysis Method for Safety-Critical Embedded Software Object Code
A technology of embedded software and object code, used in software testing/debugging, instrumentation, error detection/correction, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
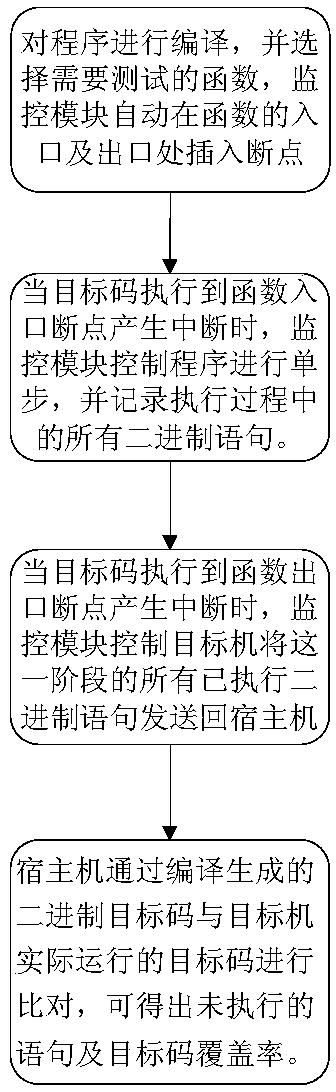
[0012] The specific embodiments of the present invention will be further described below in conjunction with the accompanying drawings. For the overall flow chart, see figure 1 ,Specific steps are as follows:
[0013] 步骤一在测试前,对某源码进行编译,获取到二进制码9421FFE8(地址0x04001c50)、93E10014、7C3F0B78、7C601B78、7C892378、B01F0008、7D204B78、B01F000A、A13F0008、A01F000A、7C090214、B01F000C、A01F000C、7C000734、7C030378、 81610000, 83EBFFFC, D615B78, 4E800020 (address 0x04001c98), and insert a breakpoint before the function entry 9421FFE8 instruction and after the function exit 4E800020
[0014] Step 2 When the target code executes to the address 0x04001c50 to generate an interrupt, the monitoring module controls the target machine to perform a single step. When the target machine enters a single step exception, the exception handling module records the target code 9421FFE8, 93E10014, 7C3F0B78, 7C601B78, 7C892378, B01F0008, 7D204B78, B01F000A, A13F0008, A01F000A, 7C090214, B01F000C, A01F000C, 7C000734, 7C030...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com