Hierarchical clustering-based log audit method
A hierarchical clustering and log technology, applied in the field of network security, can solve problems such as the inability to effectively audit massive logs, and achieve the effect of avoiding heavy and enhancing user experience
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0018] The invention aims at performing log audit by using a hierarchical clustering method, clustering the logs, and digging out abnormal log information.
[0019] Below in conjunction with accompanying drawing and embodiment the present invention will be further described:
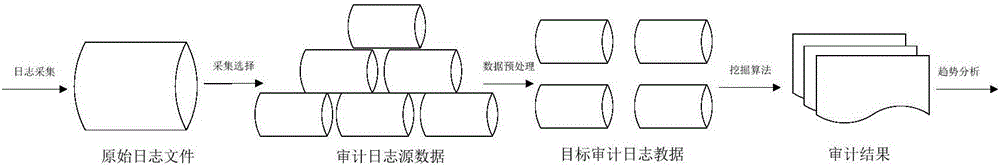
[0020] The log audit process is as follows: figure 1 shown.
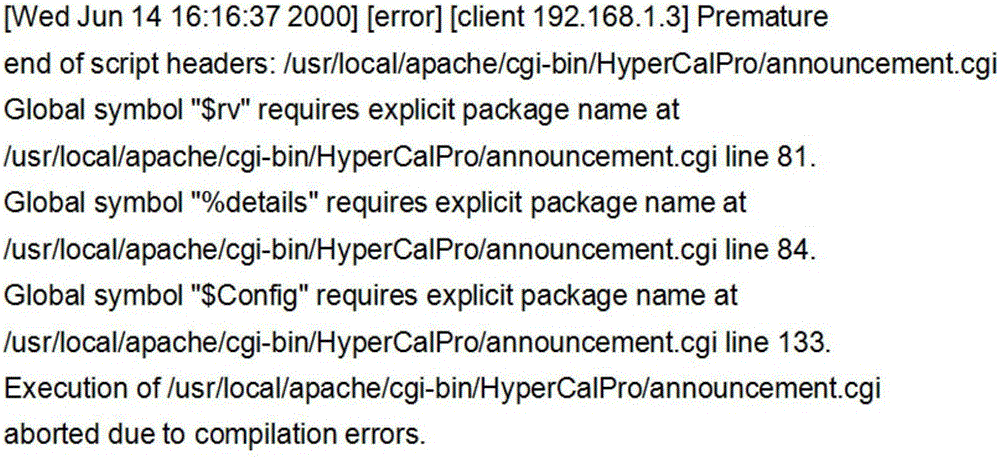
[0021] In the case of the obtained original log file, the log needs to be preprocessed, and the present invention performs log preprocessing based on a method of tf-idf weight. Taking web logs as an example, a common web log such as figure 2 shown.
[0022] It is not difficult to find that this log is semi-structured data, in which there are classification types, time and strings, and time and classification types can be extracted as specific attribute items separately. For variable descriptions, it is necessary to use tf-idf weight to select each The keyword of the log. The formula is as follows:
[0023]
[0024]
[0025] tf-idf...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com