Android malicious software detection system and Android malicious software detection method based on signature and data flow mode excavation
A malicious software and pattern mining technology, applied in the direction of electronic digital data processing, instrument, platform integrity maintenance, etc., can solve the problems of high requirements for classification features, inability to solve false positives, easy to generate false positives, etc., to improve detection speed , Improve the effect of repeated detection problems and avoid false positive problems
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0038]Below in conjunction with accompanying drawing, technical scheme of the present invention is described in further detail:
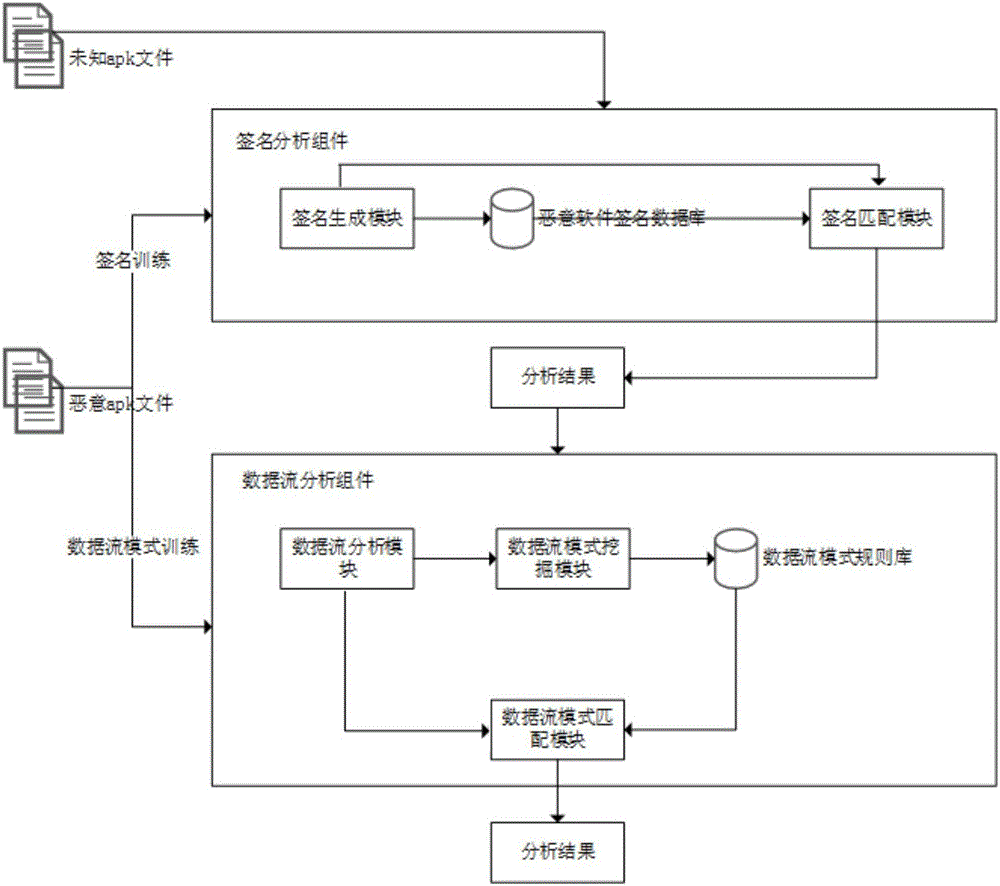
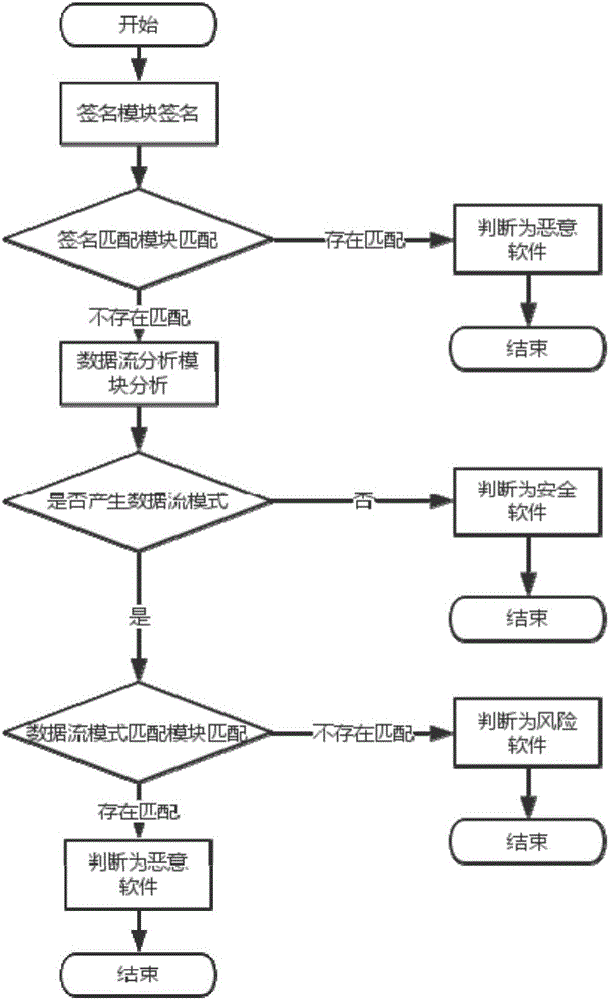
[0039] This paper discloses an Android malware detection system based on signature and data flow pattern mining, which is a static analysis detection system, which does not require the dynamic operation of the software to be tested. This system contains two components: signature analysis component and data flow analysis component. The signature analysis component optimizes the system’s speed of checking known malware, and the frequent patterns of malware data streams can be obtained through the analysis of the data flow analysis component, which can be used as rules to guide the detection of unknown software. The two components are described below.
[0040] 1) Signature analysis component
[0041] The signature analysis component includes a signature generation module, a malware signature database and a signature matching module; wherein the signa...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com