Unreliable environment-oriented audit log read-write managing method and system
A management method and log technology, applied in the field of information security, can solve problems such as damage to database tables, increased hardware costs and maintenance costs, unavailable equipment functions, etc., to reduce the probability of damage, increase the speed of log writing, and improve availability.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0027] In order to have a clearer understanding of the technical features, purposes and effects of the present invention, the specific implementation manners of the present invention will now be described in detail with reference to the accompanying drawings.
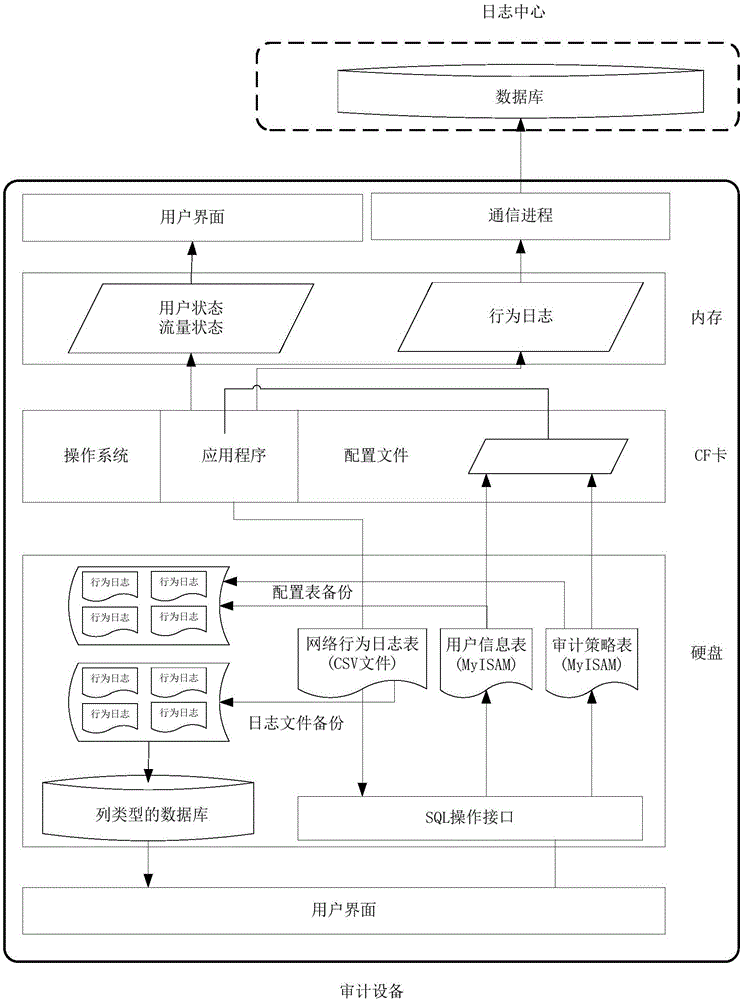
[0028] refer to figure 1 , is the structural diagram of the auditing equipment. Combine below figure 1 , to illustrate the method and system of the present invention.
[0029] Audit equipment includes three storage entities: memory, CF card, and hard disk.
[0030] The user status and traffic status are stored in the memory, and the user interface can be directly read through the interface;
[0031] The read-only partition of the CF card stores the operating system, system applications and configuration files. Only when the system is upgraded, the signature database is upgraded, and the database configuration file backup information on the hard disk is synchronized regularly, the read-only partition becomes writable...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com