Verification method and verification device
A verification method and a technology of a verification device, which are applied in the field of verification methods and verification devices for business chains, can solve problems such as difficulty in ensuring the integrity of business chain paths, and achieve the effects of ensuring integrity and avoiding security risks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0068] In order to make the purpose, technical solutions and advantages of the embodiments of the present invention more clear, specific embodiments will be described in detail below with reference to the accompanying drawings.
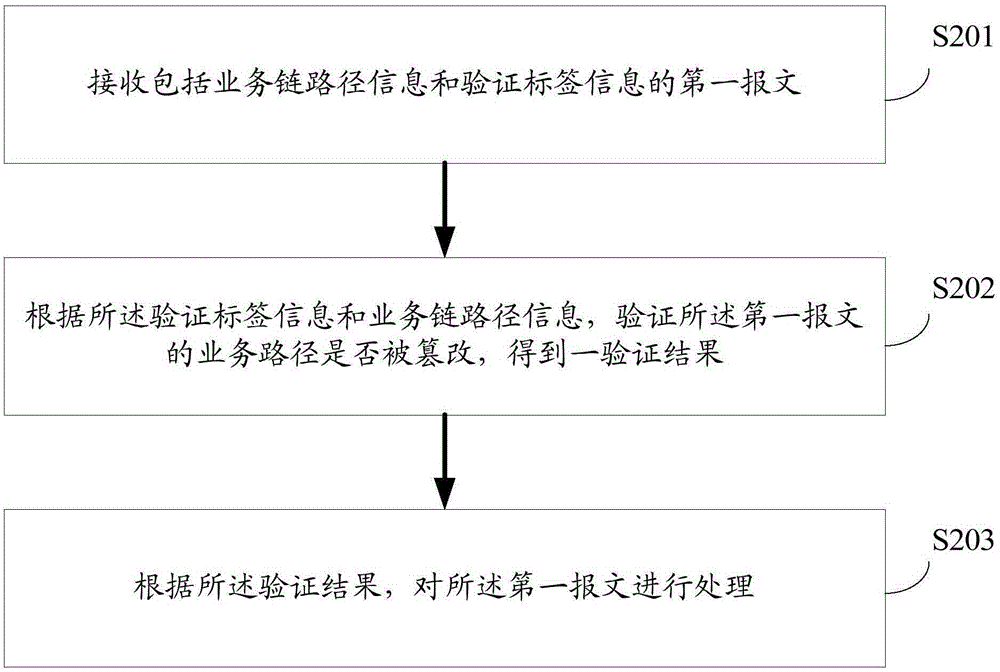
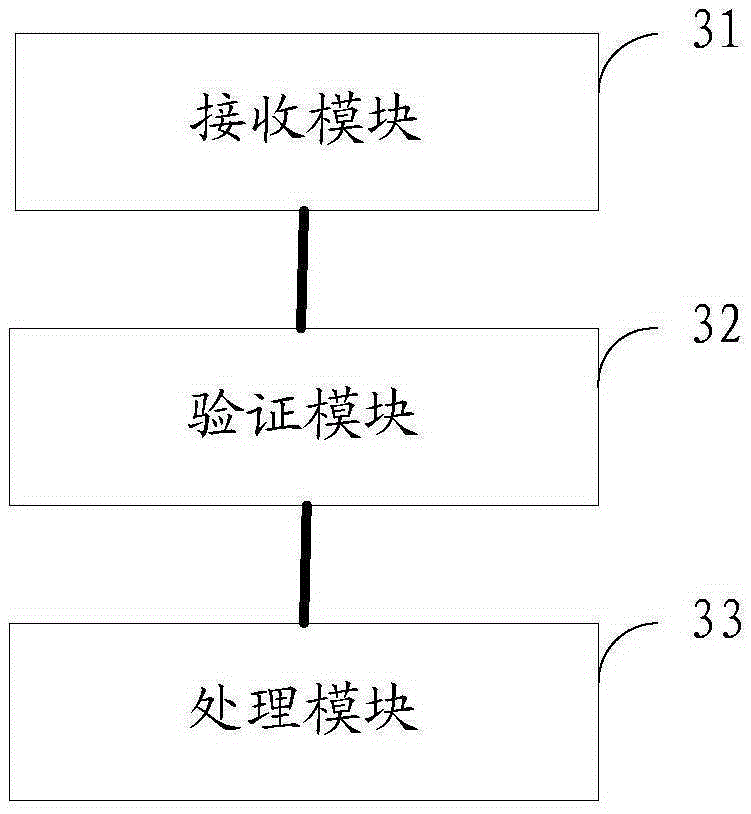
[0069] see figure 2 As mentioned above, the embodiment of the present invention provides a verification method, including:
[0070] S201: Receive a first message including service chain path information and verification label information;
[0071] S202: Verify whether the service path of the first message has been tampered with according to the verification tag information and the service chain path information, and obtain a verification result;
[0072] S203: Process the first message according to the verification result.
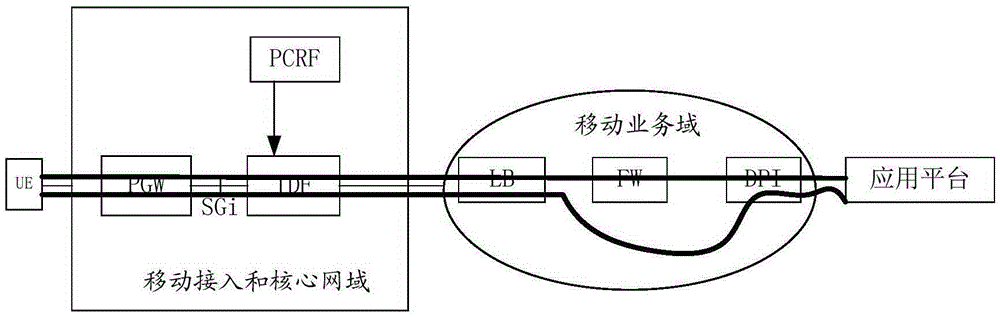
[0073] The verification method of the embodiment of the present invention can prevent the service path of the message between the user equipment and the application platform from being tampered with, so that it can be transmitt...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com