Defense method and system for domain name request attack
A defense system and domain name technology, applied in the field of communication, can solve problems such as server downtime, domain name server performance exhaustion, failure to respond to normal user domain name resolution requests, etc., to achieve the effect of defending against attacks and overcoming attack problems
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
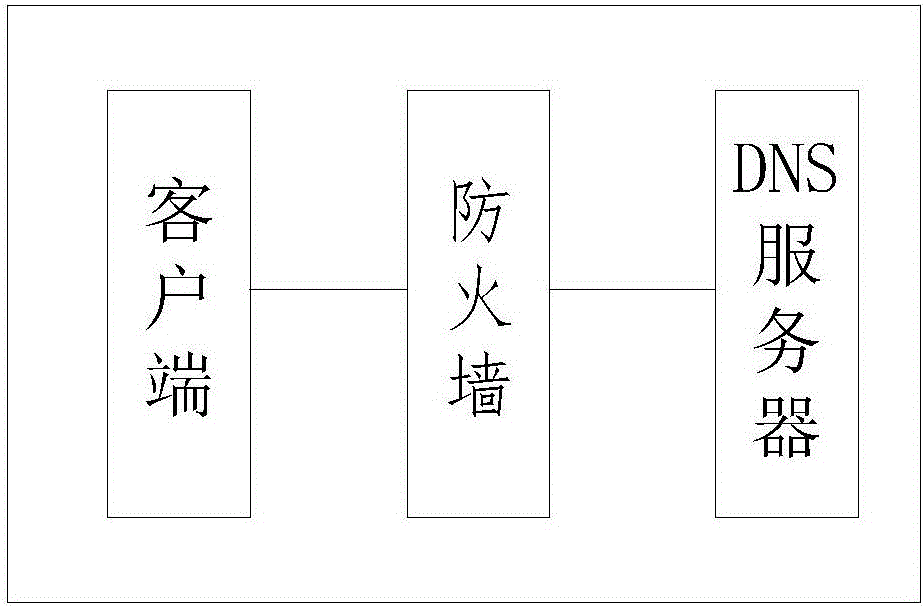
[0024] figure 1 is a schematic diagram of the application environment of the present invention;
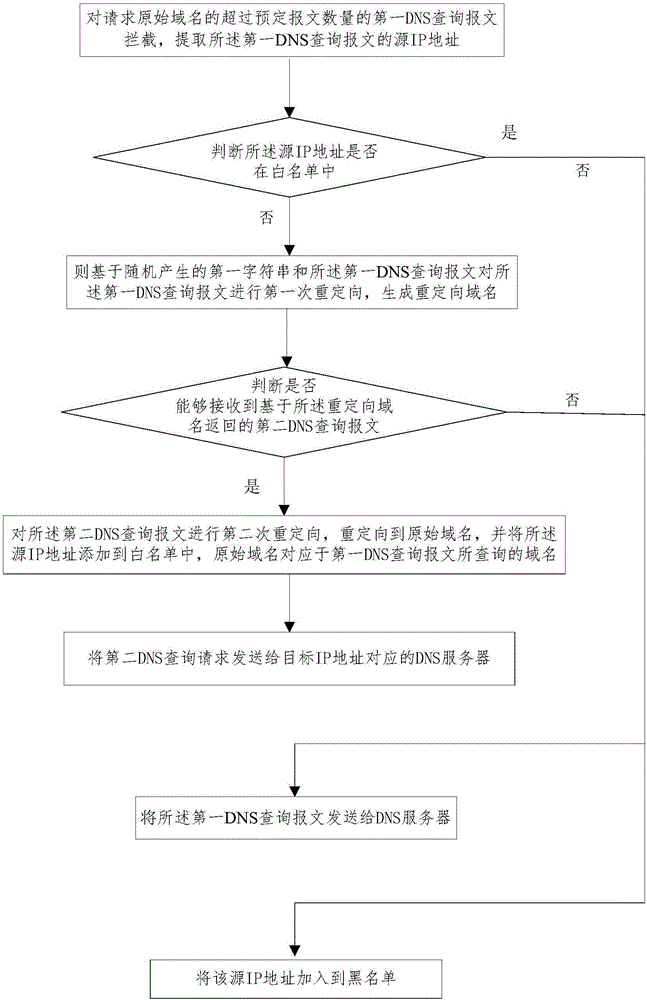
[0025] figure 2 It is a flowchart of a method for defending domain name request attacks provided by the first embodiment of the present invention.
[0026] Such as figure 1 As shown, the present invention provides a defense method for domain name request attacks, which is applied to firewalls, including:
[0027] Step S11: intercepting the first domain name resolution query message requesting the original domain name exceeding the predetermined number of messages, and extracting the source IP address of the first domain name resolution query message.
[0028] Specifically, the original domain name in this step S11 refers to the domain name that needs to be queried input by the user in the client. If the user needs to query the www.test.com website, input it in the domain name query input column of the client, then "www.test .com" is the original domain name of the user's quer...
Embodiment 2
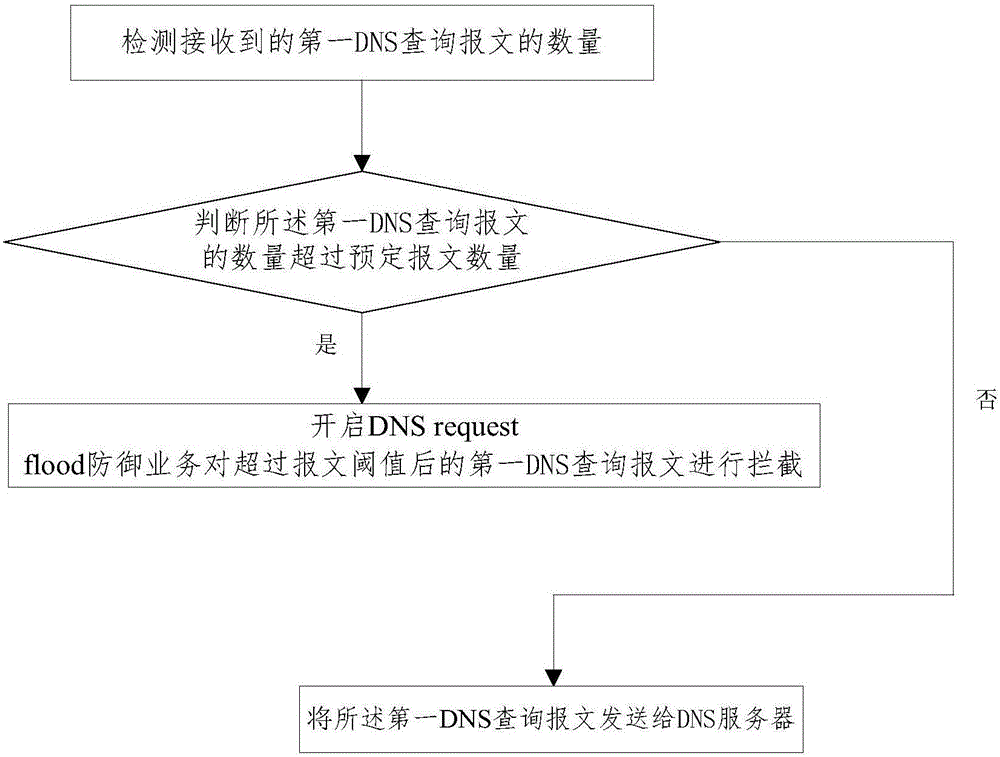
[0043] On the basis of Embodiment 1, the present invention also includes such as figure 2 The flow shown in step S11 before the firewall detects the number of first domain name resolution query packets.
[0044] figure 2 It is a flow chart of the firewall detecting the number of first domain name resolution query packets before step S11.
[0045] Such as figure 2 as shown,
[0046] S111. Detect the number of received first domain name resolution query messages;
[0047] S112, judging that the number of the first domain name resolution query messages exceeds the predetermined number of messages
[0048] S113, if the number of the first domain name resolution query messages exceeds the predetermined number of messages, enable the domain name resolution request flood defense service to intercept the first domain name resolution query messages exceeding the message threshold
[0049] Specifically, before the step of intercepting the first domain name resolution query messa...
Embodiment 3
[0052] image 3 It is a schematic diagram of module relationship of a defense system against domain name request attack in Embodiment 3 of the present invention.
[0053] Such as image 3 As shown, the embodiment of the present invention provides a defense system for domain name request attacks, which is applied to firewalls, including:
[0054] The extracting module 100 is used to intercept the first domain name resolution query message requesting the original domain name and exceeding the predetermined number of messages, and extract the source IP address of the first domain name resolution query message;
[0055] Specifically, the original domain name refers to the domain name that needs to be queried entered by the user in the client. If the user needs to query the www.test.com website, enter it in the domain name query input field of the client, then "www.test.com" is It is the original domain name of the user's query. After the user enters the domain name, the domain ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com