A SQL injection detection method and device
A detection method and technology of time duration, applied in the field of network security, can solve the problems of false positives, low detection accuracy, false negatives, etc., and achieve the effects of accurate response time, improved accuracy, and reduced false positives and false positives.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
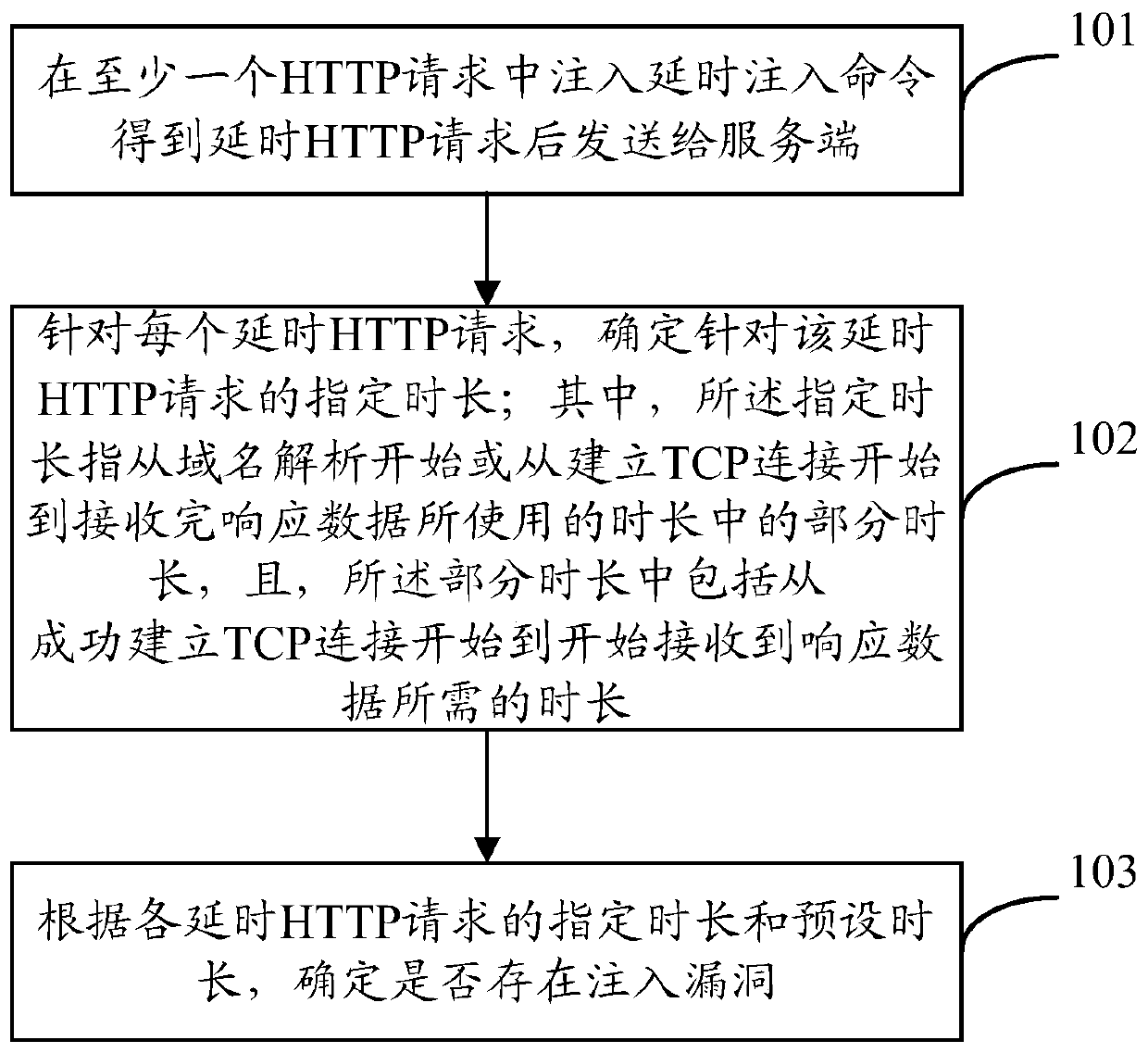
[0036] Such as figure 1 As mentioned above, it is a schematic flow chart of the method provided in the embodiment of the present application, and the method includes the following steps:
[0037] Step 101: Inject a delayed injection command into at least one HTTP request and send it to the server after obtaining the delayed HTTP request.
[0038] Among them, the delay injection command records the delay time that needs to be executed (that is, directly records the value of the delay time) or records the impact factor that represents the number of repeated executions of the characteristic expression (that is, indirectly indicates the value of the delay time value).
[0039]In the mode of indirectly indicating the value of the delay time, when the delay injection command is injected into at least one HTTP request, it is only necessary to set the impact factor of the number of repeated executions. Then, multiply the impact factor by the set coefficient to obtain the number of r...
Embodiment 2
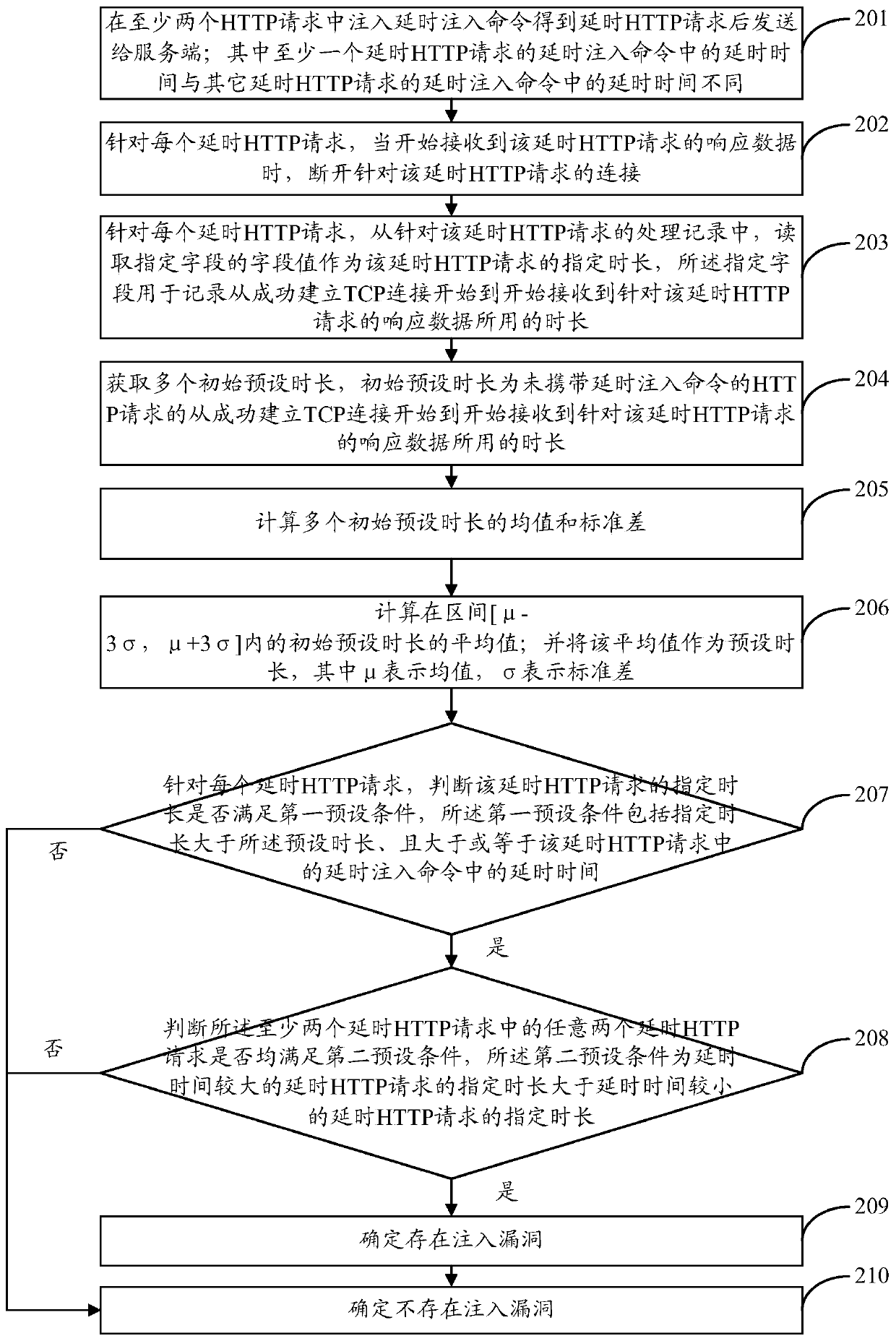
[0104] In order to facilitate a further understanding of the SQL injection detection method provided in the present application, the embodiment of the present application further describes the method. Such as figure 2 shown, including the following steps:
[0105] Step 201: Inject the delay injection command into at least two HTTP requests and send it to the server after obtaining the delay HTTP request; the delay time in the delay injection command of at least one delay HTTP request is the same as that of other delay HTTP requests The delay time in the delay injection command is different.
[0106] Step 202: For each delayed HTTP request, disconnect the connection for the delayed HTTP request when the response data of the delayed HTTP request is started to be received.
[0107] Step 203: For each delayed HTTP request, from the processing record for the delayed HTTP request, read the field value of the specified field as the specified duration of the delayed HTTP request, a...
Embodiment 3
[0120] Based on the same inventive concept, the embodiment of the present application also provides a SQL injection detection device, the SQL injection detection principle of the device is similar to the SQL injection detection principle of the above SQL injection detection method. For details, please refer to the content of the above method, which will not be repeated here.
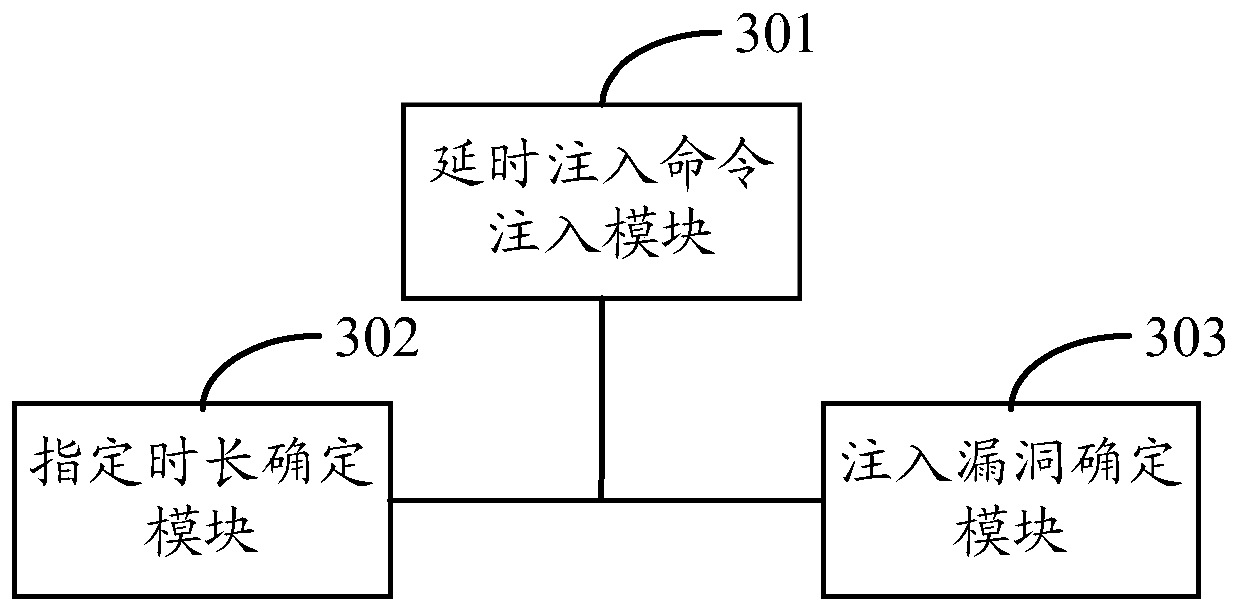
[0121] Such as image 3 Shown, is the structural representation of this device, and described device comprises:
[0122] Delayed injection command injection module 301: for injecting a delayed injection command into at least one HTTP request and sending it to the server after obtaining a delayed HTTP request.
[0123] Specified duration determination module 302: for each delayed HTTP request, determine the specified duration for the delayed HTTP request; wherein, the specified duration refers to the period from the beginning of domain name resolution or from the establishment of a TCP connection to the ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com