State transition diagram based XSS (cross-site scripting) vulnerability detection method
A state transition diagram and vulnerability detection technology, which is applied in the direction of instrumentation, electrical digital data processing, platform integrity maintenance, etc., can solve problems such as insufficient injection point capabilities
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
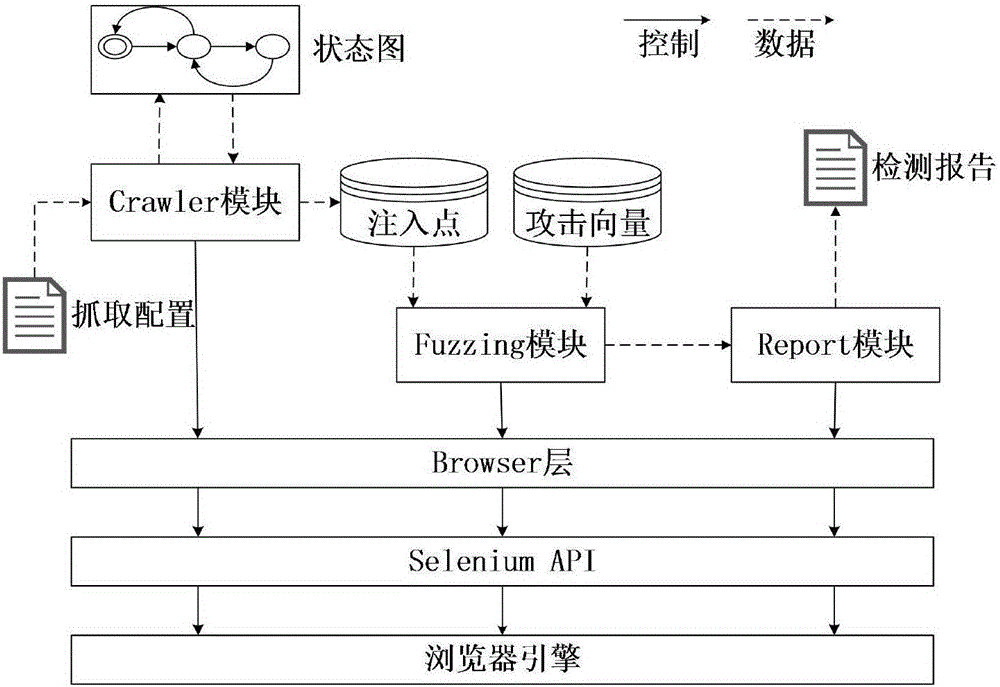
[0022] The principle of this system is to call the Selenium API to test the black box of the Web server. It consists of three modules: Crawler module, Fuzzing module and Report module. System architecture such as figure 1 shown.
[0023] Crawler module
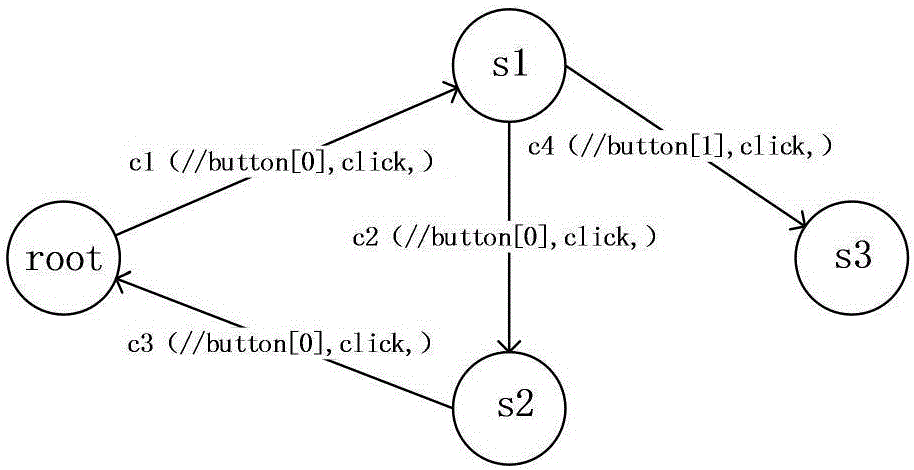
[0024] The Crawler module implements the functions of building state diagrams and mining injection points. The algorithm creates state diagrams in a depth-first manner. The algorithm description is shown in Algorithm 1.
[0025] Algorithm 1. Constructing state diagram and mining injection point algorithm
[0026] Input: Start Website URL
[0027] Output: state diagram and list of injection points
[0028] 0. Initialize an empty url_list, add url to url_list
[0029] 1. If there is no unprocessed url in url_list, otherwise skip to step 10
[0030] 2. Take out an unprocessed url, analyze whether the url has parameters, if the url does not jump out of the domain and the marked resource is not a picture, file, etc., reques...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com