WIFI proxy authentication method and system
An authentication method and authentication request technology, applied in transmission systems, safety devices, electrical components, etc., can solve problems such as inability to manage
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
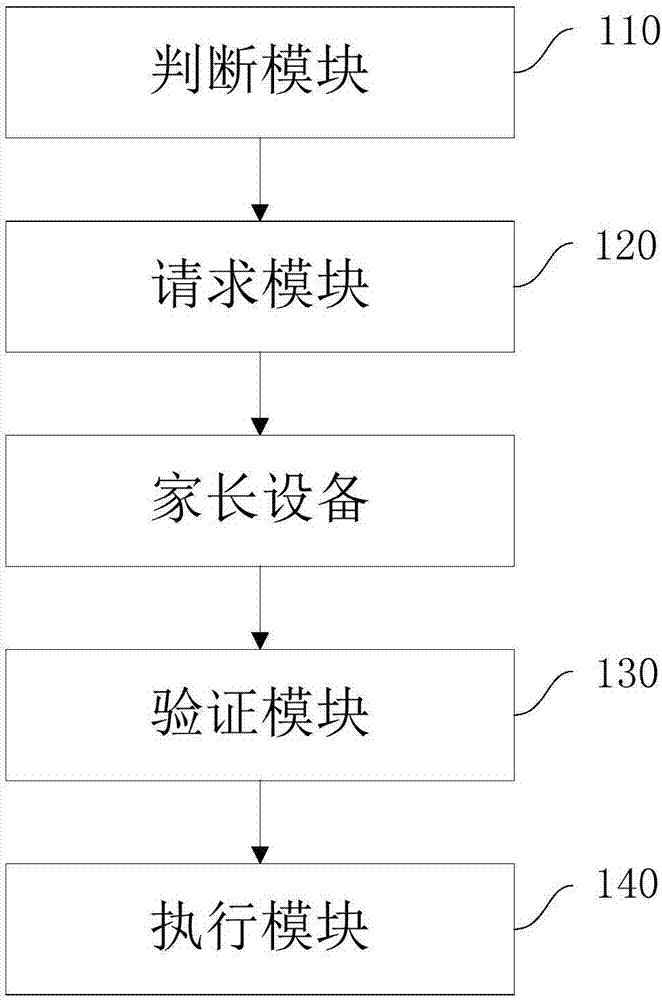
Image
Examples
Embodiment 1
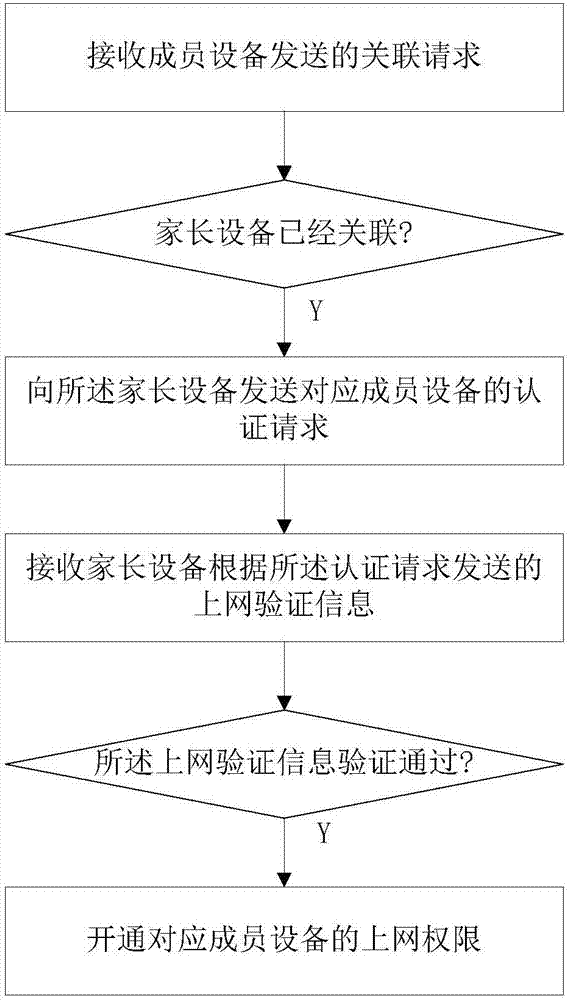
[0050] Such as figure 1 Shown is a flow chart of a WIFI proxy authentication method in this embodiment. The method is used to control the access authority of at least one member device through a parent device in a home network. The method specifically includes:
[0051] S1. When receiving an association request sent by a member device, determine whether the parent device has been associated;
[0052] In this step, when the member device is associated with the wireless access device, access to the external network is prohibited by default.
[0053] At this time, after the wireless access device accepts the association request of the member device, it checks and determines whether the parent device is also associated with the wireless access device.
[0054] S2. If the parent device has been associated, send an authentication request corresponding to the member device to the parent device;
[0055]In this step, if the AP checks and judges that the parent device is also associa...
Embodiment 2
[0079] The difference between this embodiment and the previous embodiments is that this embodiment also includes the situation that the parent device fails to process the access request of the member device in time.
[0080] Such as Figure 4 Shown is a flow chart of a WIFI proxy authentication method in this embodiment. The method is used to control the Internet access authority of at least one member device through a parent device in a home network. The method includes:
[0081] S1. When receiving an association request sent by a member device, determine whether the parent device has been associated;
[0082] S2. If the parent device has been associated, send an authentication request corresponding to the member device to the parent device;
[0083] In this embodiment, after the step S2, it further includes: monitoring the feedback information of the parent device within a predetermined time, and if no feedback information is received from the parent device within the prede...
Embodiment 3
[0095] The difference between this embodiment and the previous embodiments is that this embodiment also includes: the administrator can cancel the access permission of the member device through the parent device.
[0096] A kind of WIFI agent authentication method comprises in the present embodiment:
[0097] S1. When receiving an association request sent by a member device, determine whether the parent device has been associated;
[0098] S2. If the parent device has been associated, send an authentication request corresponding to the member device to the parent device;
[0099] S3. When receiving the online verification information sent by the parent device according to the authentication request, verifying the online verification information;
[0100] S4. When the verification of the Internet access verification information is passed, activate the Internet access permission of the corresponding member device.
[0101] In this embodiment, after the step S4, it further incl...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com