An encryption method and device
An encryption method and encryption device technology, applied in the field of communication, can solve the problems of large memory space, low encryption efficiency of large files, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
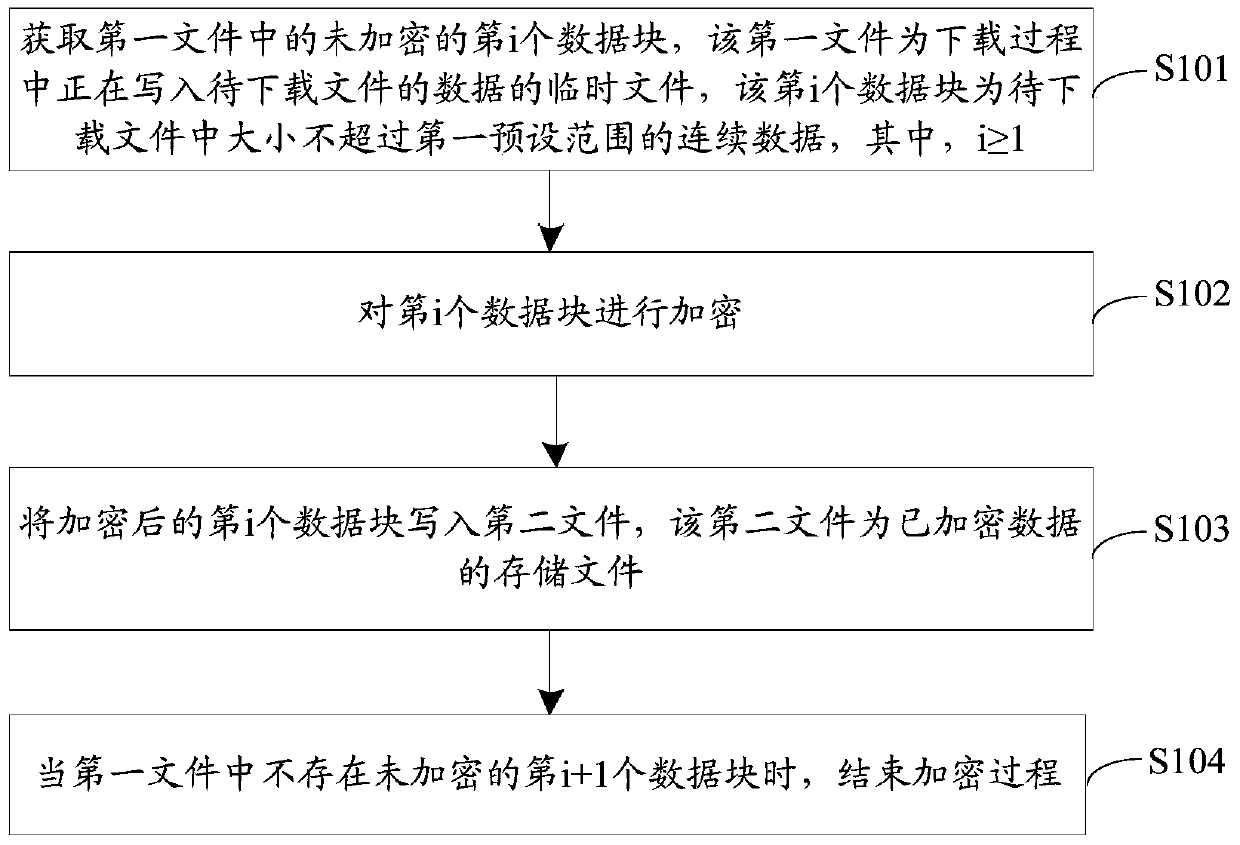
[0044] The embodiment of the present invention provides an encryption method, such as figure 1 As shown, the method may include:
[0045] S101. Obtain the unencrypted i-th data block in the first file, the first file is a temporary file that is writing the data of the file to be downloaded during the download process, and the i-th data block is the file to be downloaded with different sizes Continuous data beyond the first preset range, where i≥1.
[0046] The embodiment of the present invention is proposed when the file after data download or loading is to be encrypted in the above-mentioned terminal. The inventive concept is: when a file is downloaded or loaded in the terminal, the downloaded data part is Encryption, that is, the method of using space to replace time to reduce encryption time and improve encryption efficiency.
[0047] Optionally, the terminal in this embodiment of the present invention may be a mobile terminal, specifically, a smart phone, a tablet comput...
Embodiment 2
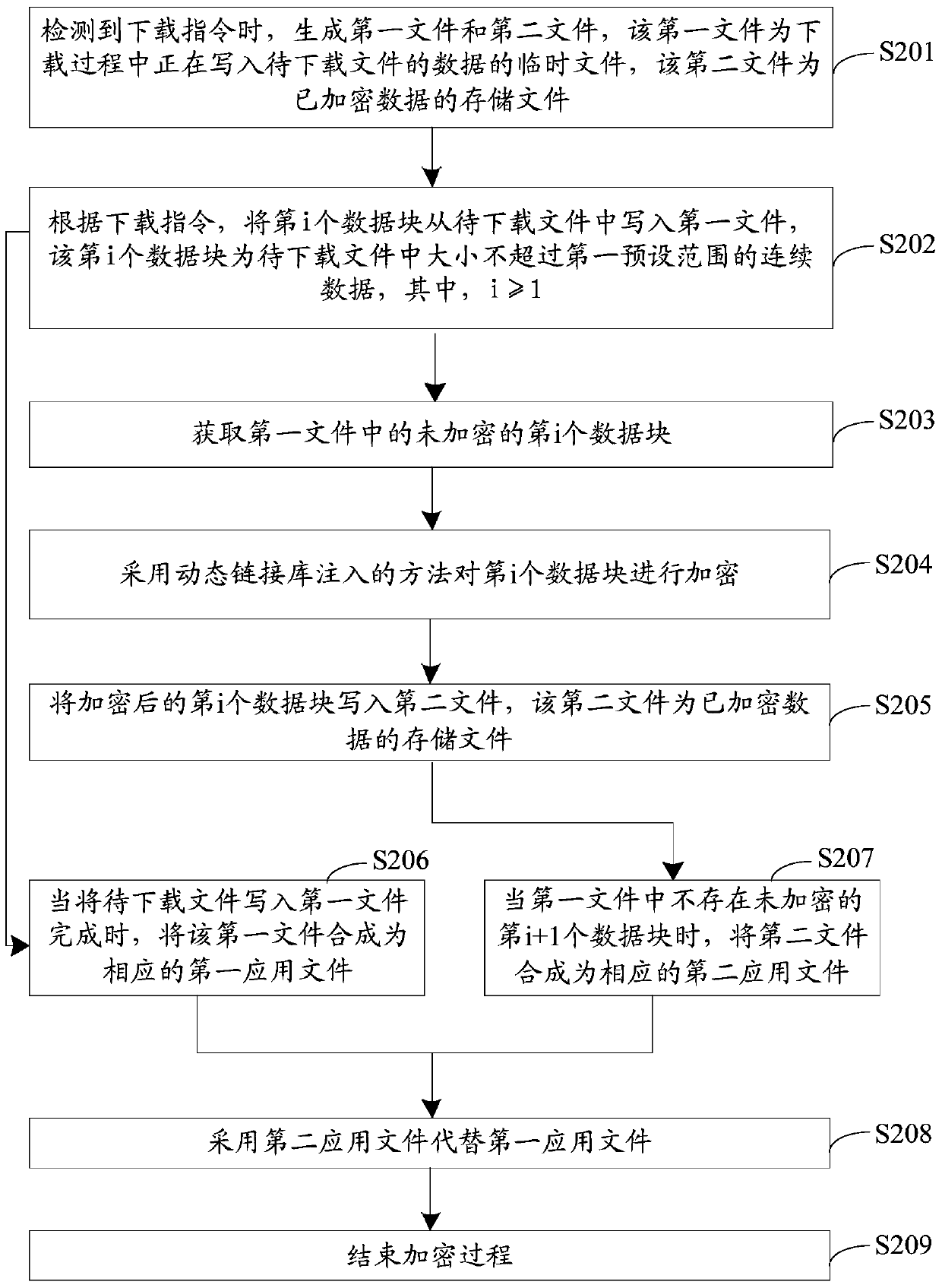
[0070] The embodiment of the present invention provides an encryption method, such as figure 2 As shown, the method may include:
[0071] S201. When a download instruction is detected, generate a first file and a second file, the first file is a temporary file in which data of the file to be downloaded is being written during the download process, and the second file is a storage file of encrypted data.
[0072] The embodiment of the present invention is proposed when the file after data download or loading is to be encrypted in the above-mentioned terminal. The inventive concept is: when a file is downloaded or loaded in the terminal, the downloaded data part is Encryption, that is, the method of using space to replace time to reduce encryption time and improve encryption efficiency.
[0073] Optionally, the terminal in this embodiment of the present invention may be a mobile terminal, specifically, a smart phone, a tablet computer, etc. that have file loading and storage f...
Embodiment 3
[0112] Such as Figure 4 As shown, the embodiment of the present invention provides a terminal 1, the terminal 1 may include:
[0113] The obtaining unit 10 is used to obtain the unencrypted i-th data block in the first file, the first file is a temporary file that is writing the data of the file to be downloaded during the download process, and the i-th data block is The continuous data whose size does not exceed the first preset range in the file to be downloaded, wherein i≥1.
[0114] An encryption unit 11, configured to encrypt the i-th data block acquired by the acquisition unit 10.
[0115] The writing unit 12 is configured to write the ith data block encrypted by the encryption unit 11 into a second file, and the second file is a storage file of encrypted data.
[0116] The end unit 13 is configured to end the encryption process when there is no unencrypted (i+1)th data block in the first file acquired by the acquisition unit 10 .
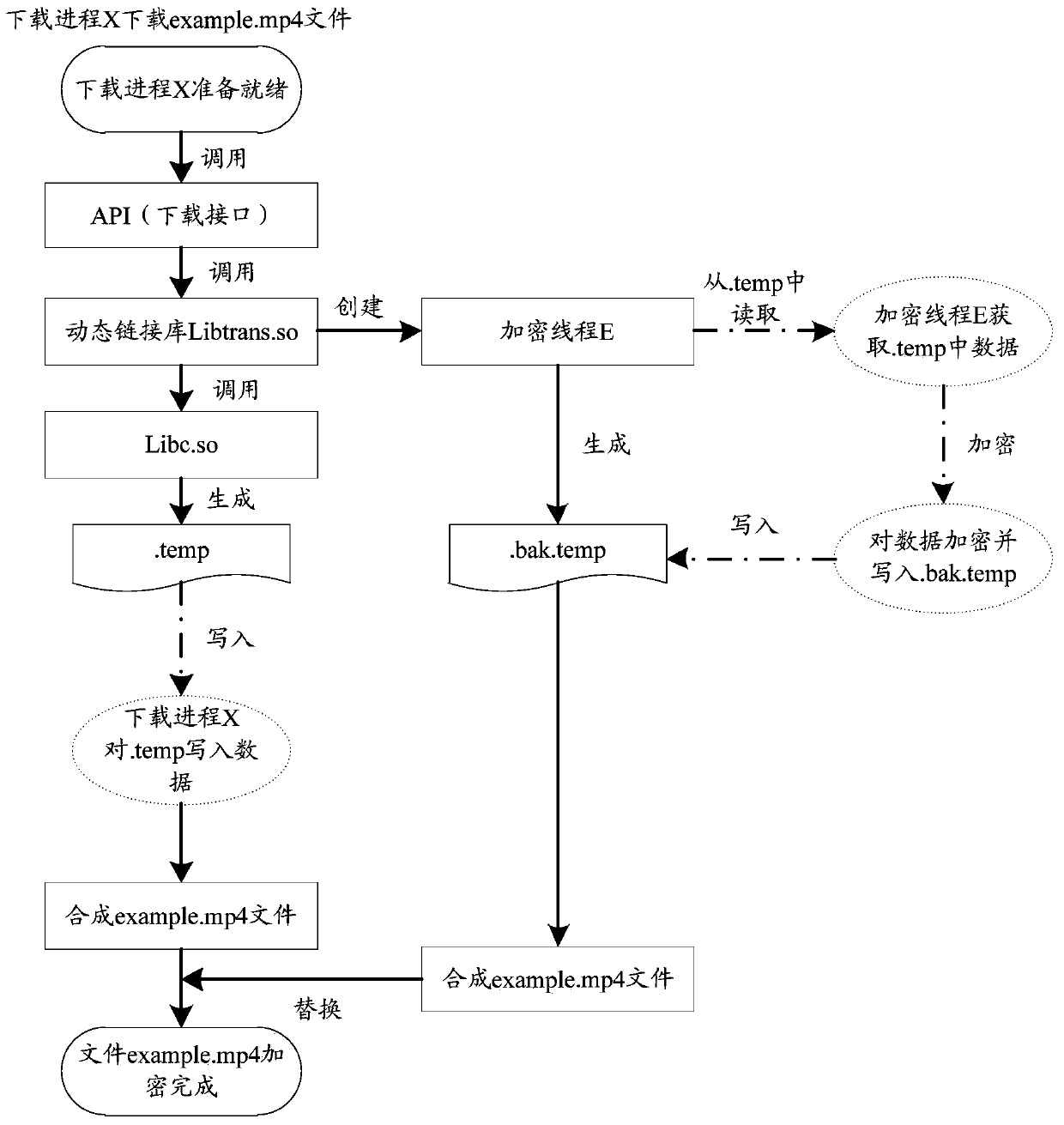
[0117] optional, such as Figure ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com