Ransomware defense method and device
A technology of software and software encryption, which is applied in the field of information security, can solve the problems of no solution proposed, the inability to detect unknown ransomware, and the inability to prevent it, so as to achieve the effect of defending against ransomware
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0015] According to an embodiment of the present invention, a method embodiment of a ransomware defense method is provided. It should be noted that the steps shown in the flow chart of the accompanying drawings can be executed in a computer system such as a set of computer-executable instructions, and , although a logical order is shown in the flowcharts, in some cases the steps shown or described may be performed in an order different from that shown or described herein.
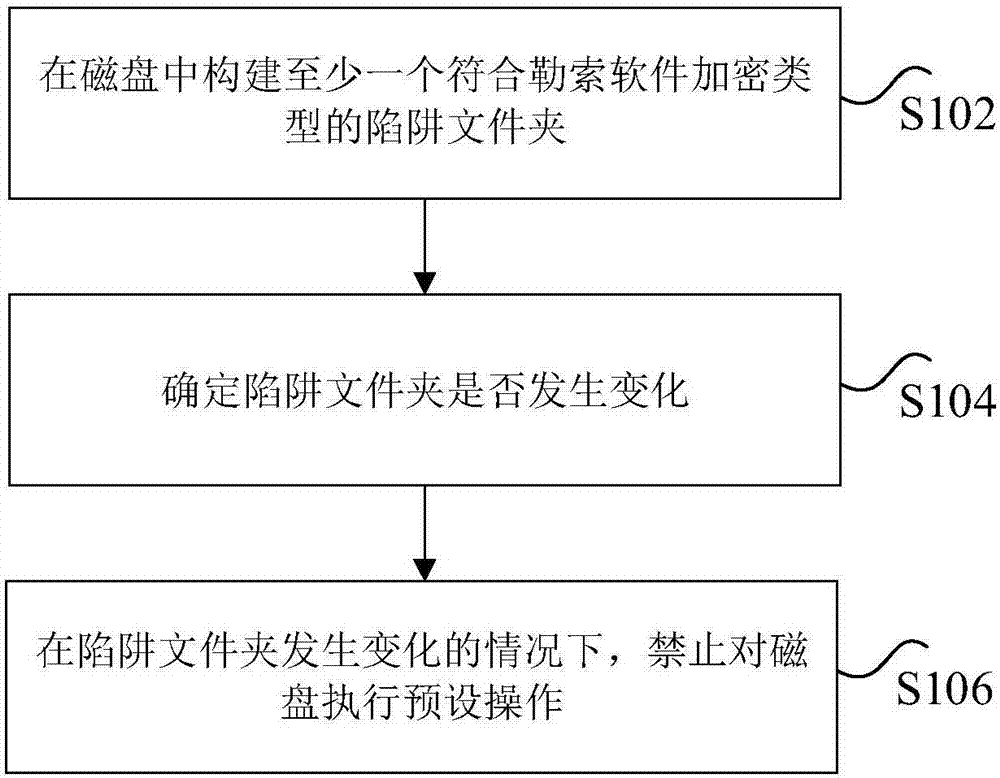
[0016] figure 1 is a ransomware defense method according to an embodiment of the present invention, such as figure 1 As shown, the method includes the following steps:
[0017] Step S102, constructing at least one trap folder conforming to the encryption type of ransomware in the disk.
[0018] Specifically, the suffix or file format of the files in the trap folder constructed to meet the encryption type of ransomware, including but not limited to the following types:
[0019]1cd,dbf,dt,cf,cfu,mxl,epf,kd...
Embodiment 2
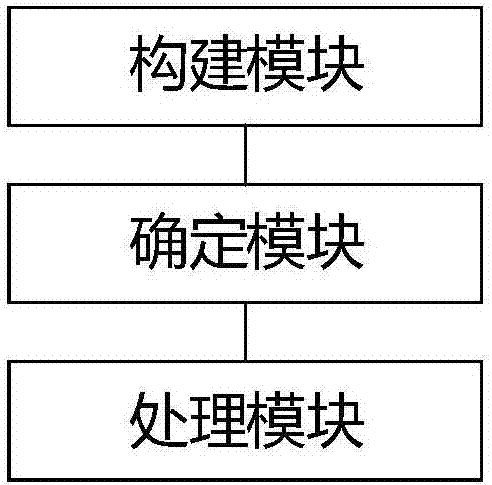
[0059] According to an embodiment of the present invention, a product embodiment of a ransomware defense device is provided, figure 2 is a ransomware defense device according to an embodiment of the present invention, such as figure 2 As shown, the device includes a construction module, a determination module and a processing module, wherein the construction module is used to construct at least one trap folder conforming to the encryption type of ransomware in the disk; the determination module is used to determine whether the trap folder changes , wherein the change includes at least one of the following: modifying, deleting, renaming the trap folder, and adding new files to the trap folder; the processing module is used to prohibit the execution of presets on the disk when the trap folder changes operate.
[0060] It should be noted here that the above construction modules, determination modules and processing modules correspond to steps S102 to S106 in Embodiment 1, and th...
Embodiment 3
[0073] According to an embodiment of the present invention, a storage medium is provided, the storage medium includes a stored program, wherein when the program is running, the device where the storage medium is located is controlled to execute the ransomware defense method described above.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com