Malicious code detecting method applicable to android App
A malicious code detection and malicious code technology, applied in computer security devices, instruments, electrical digital data processing, etc., can solve the problems of high time-consuming and inability to accurately and comprehensively detect malicious code behaviors, achieve rapid classification and detection, and improve response Ability, speed-up effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0028] The present invention will be further described below in conjunction with the accompanying drawings and embodiments.
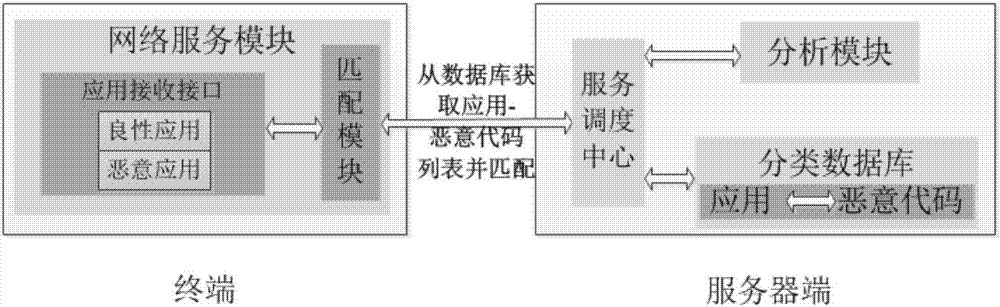
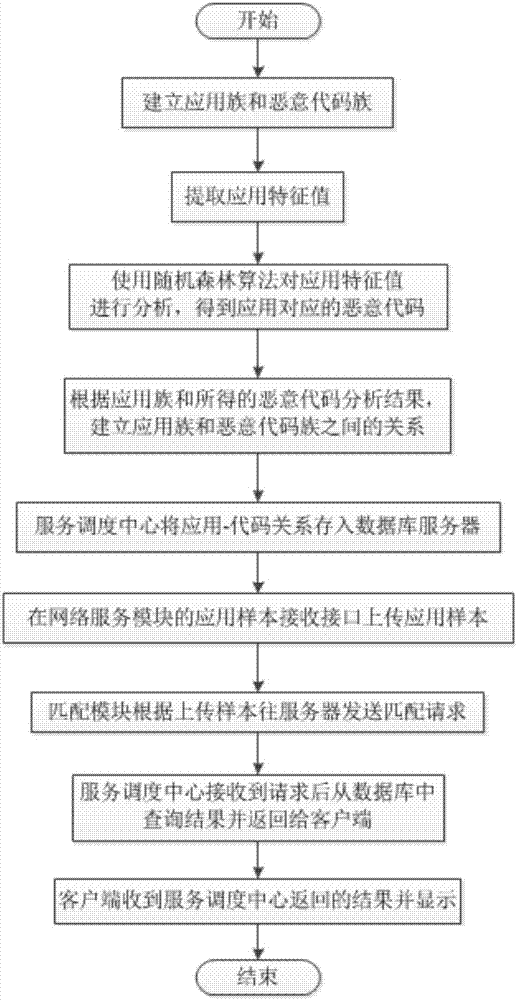
[0029] The embodiment of the present invention is an Android application malicious code detection model based on a terminal, a server and a network. The model architecture diagram of this method is shown in figure 1 shown. , The terminal is a webpage system with BS architecture, which can run on traditional PCs, tablets or mobile phones, such as Windows, Android, etc. The core of the terminal is a network service module, which is composed of an application receiving interface and a matching module. The server side includes a service dispatching center. The service dispatching center calls the corresponding service technology to serve it according to the service request of the terminal. Specifically, the application receiving interface uploads an application sample and sends a request to the server, and the service dispatching center communicates it wi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com