Method and device for detecting data leakage interface
A technology for interface detection and data leakage, which is applied in the field of information security, can solve the problems of low efficiency of privacy leakage interface detection, and achieve the effects of authenticity, reduced labor costs, and wide data coverage
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0044] It should be understood that the specific embodiments described here are only used to explain the present invention, not to limit the present invention.
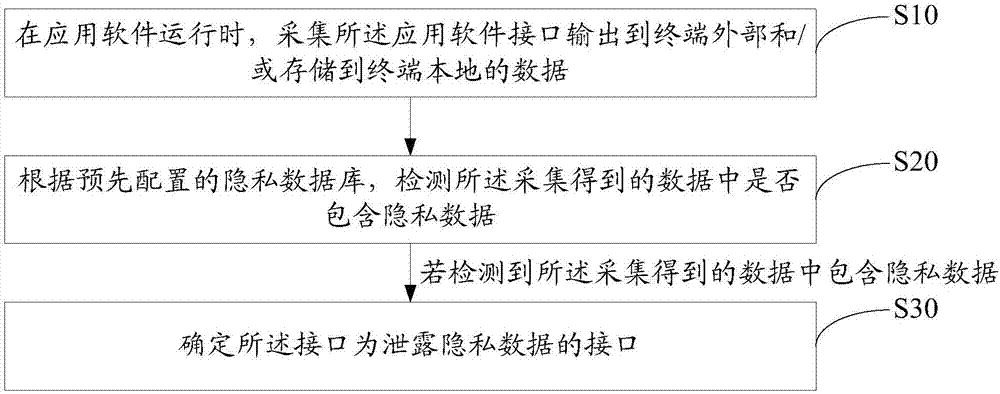
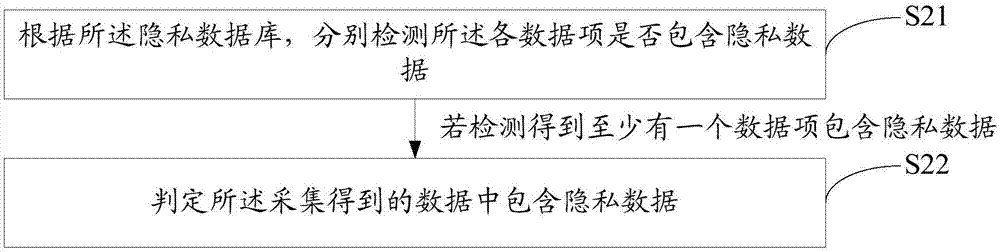
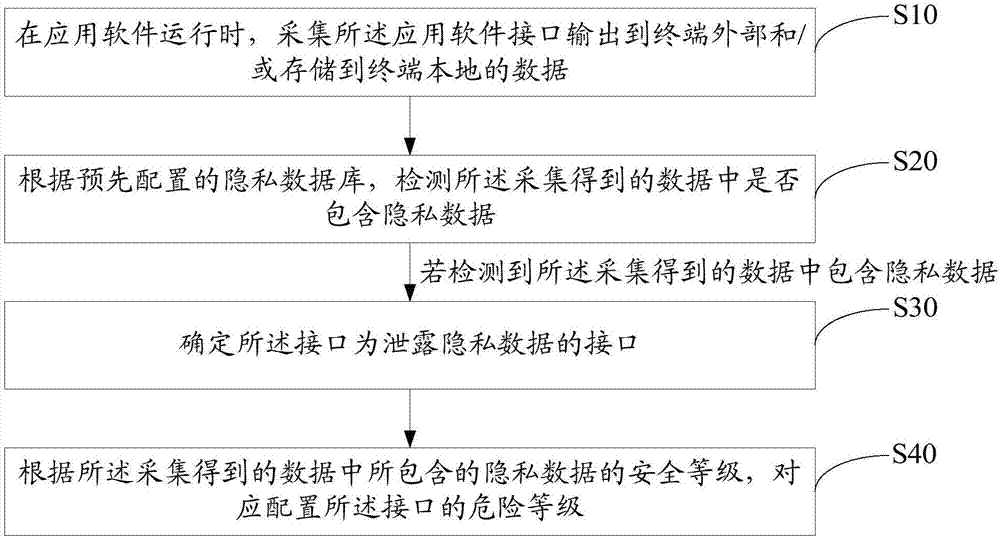
[0045] refer to figure 1 The first embodiment of the method for detecting a data leakage interface of the present invention provides a method for detecting a data leakage interface, the method for detecting a data leakage interface includes:
[0046] Step S10 , when the application software is running, collect the data output from the application software interface to the outside of the terminal and / or stored locally in the terminal.
[0047] The present invention collects the externally output data during the operation of the application software, automatically detects whether the externally output data contains private data offline, does not need manual detection, does not rely on manual experience, and can automatically check the privacy of the application software in an all-round way Leakage issues, avoid false p...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com