Patents
Literature
196results about How to "Effective security protection" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
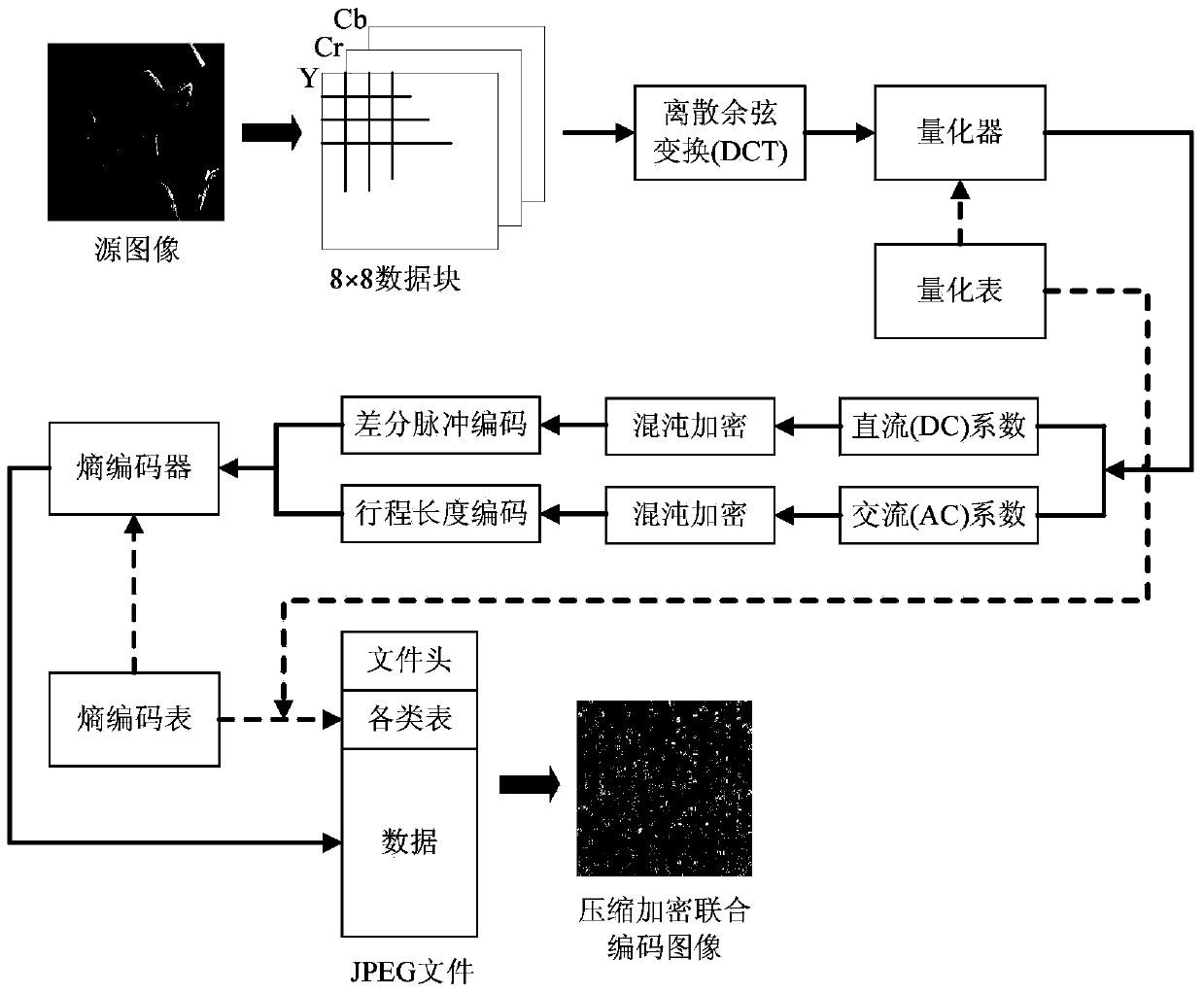
Digital image compressing, encrypting and encoding combined method
ActiveCN104144343ASolve the problem that effective compression cannot be performedEffective security protectionDigital video signal modificationAc coefficientJPEG
The invention discloses a digital image compressing, encrypting and encoding combined method, and belongs to the technical field of image encrypting. The method is achieved on the basis of the JPEG compressing and encoding standard which is most widely applied at present, and the encrypting algorithm based on chaos is integrated with the encoding process; according to the characteristic that DC coefficients and AC coefficients are separately encoded on the basis of the JPEG standard, the DC coefficients and the AC coefficients of an image are separately encrypted; in order to give consideration to both security and compressing efficiency, all the DC coefficients and part of the AC coefficients are encrypted through the method, coefficients at the same positions in all DCT blocks are divided into different groups and are scrambled and diffused within the groups, and damage to differential encoding and run length encoding in the encrypting process is reduced as much as possible; scrambling and diffusing are achieved on the basis of logistic chaotic mapping and Chebyshev chaotic mapping respectively. The experiments prove that the method has high data compressing capacity while providing effective image data security protection.
Owner:NORTHEASTERN UNIV
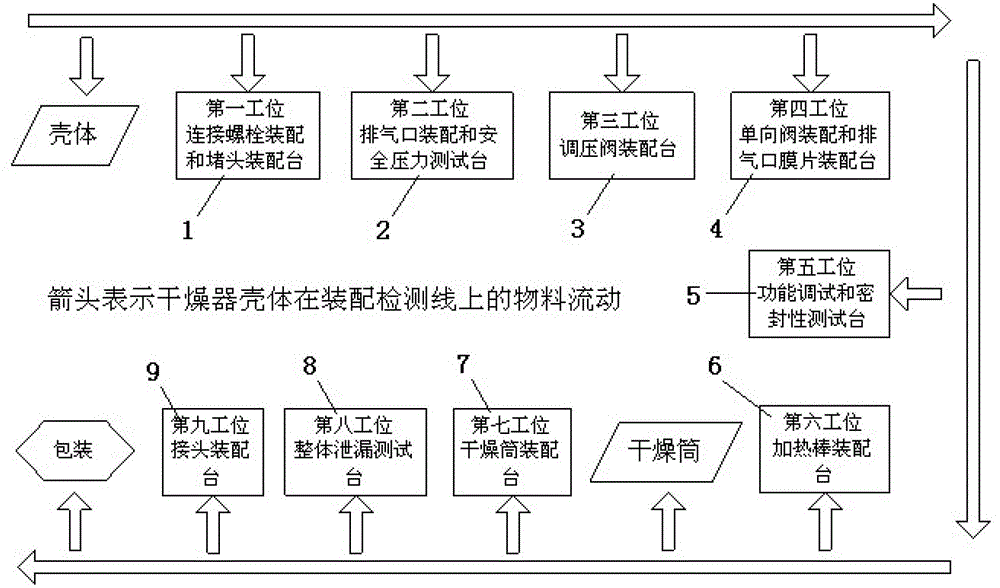
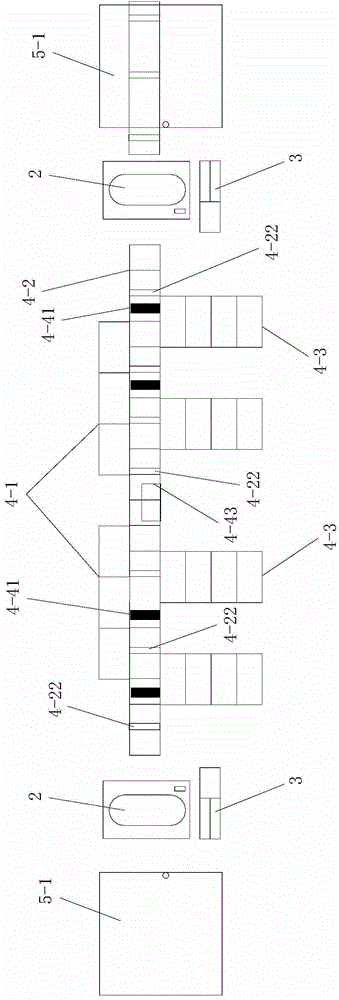
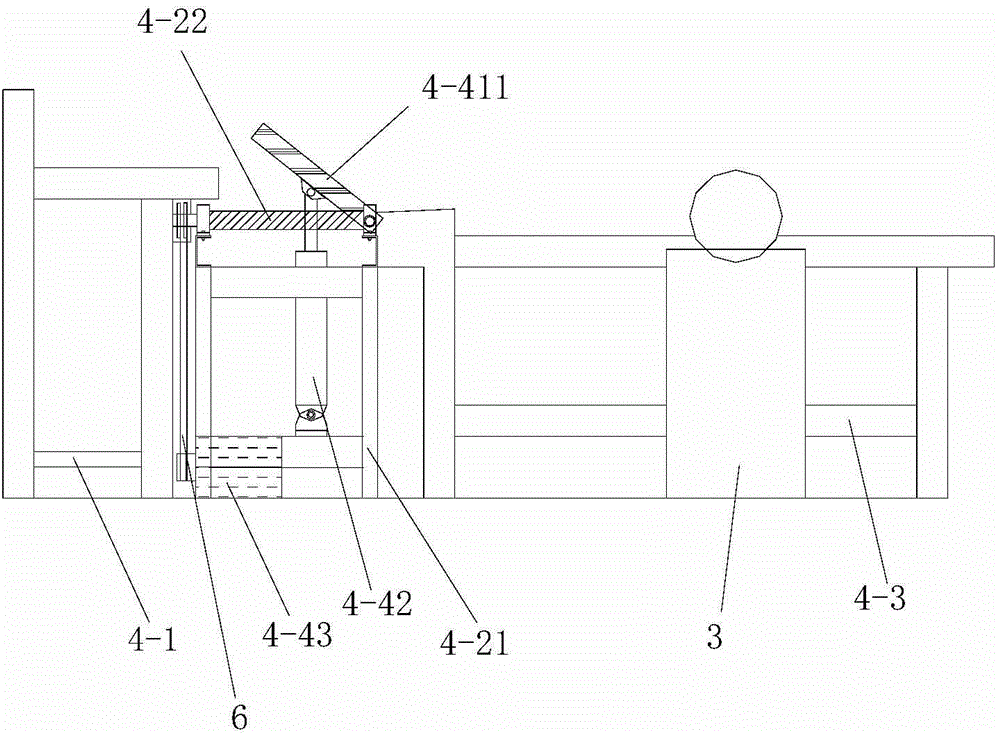
Automobile air dryer assembling and testing production line
ActiveCN103182645AReasonable structural designFlexible layout adjustmentVehicle testingMeasurement of fluid loss/gain rateTest efficiencyProduction line
The invention discloses an automobile air dryer assembling and testing production line. At present, assembly of most of automobile air dryers at home is in a scattered operation state and a testing method is a manual intermittent partial testing method; however, selection and matching of the conventional assembling and testing equipment are not reasonable enough and poor in coordination; and therefore, the assembling process of the automobile air dryer is poor in smoothness and low in assembling and testing efficiency. The automobile air dryer assembling and testing production line comprises a U-shaped workbench line body, wherein the U-shaped workbench line body comprises six assembling workstations, two testing workstations and an assembling and testing workstation, namely a first workstation, a second workstation, a third workstation, a fourth workstation, a fifth workstation, a sixth workstation, a seventh workstation, an eighth workstation and a ninth workstation sequentially; the adjacent workstations are related to each other through a material conveying belt. A shell of the assembled and tested air dryer is transferred among the workstations through the material conveying belts between the workstations, working procedures are continuous, and the workstations are related through the material conveying belts, so that the assembling pace is ensured and the manufacturing cost is reduced.
Owner:HANGZHOU WOLEI INTELLIGENT TECH
Embedded software safety protection system
InactiveCN102799819AAvoid gettingPrevent leakageUnauthorized memory use protectionComputer security arrangementsStatic random-access memoryProgrammable read-only memory
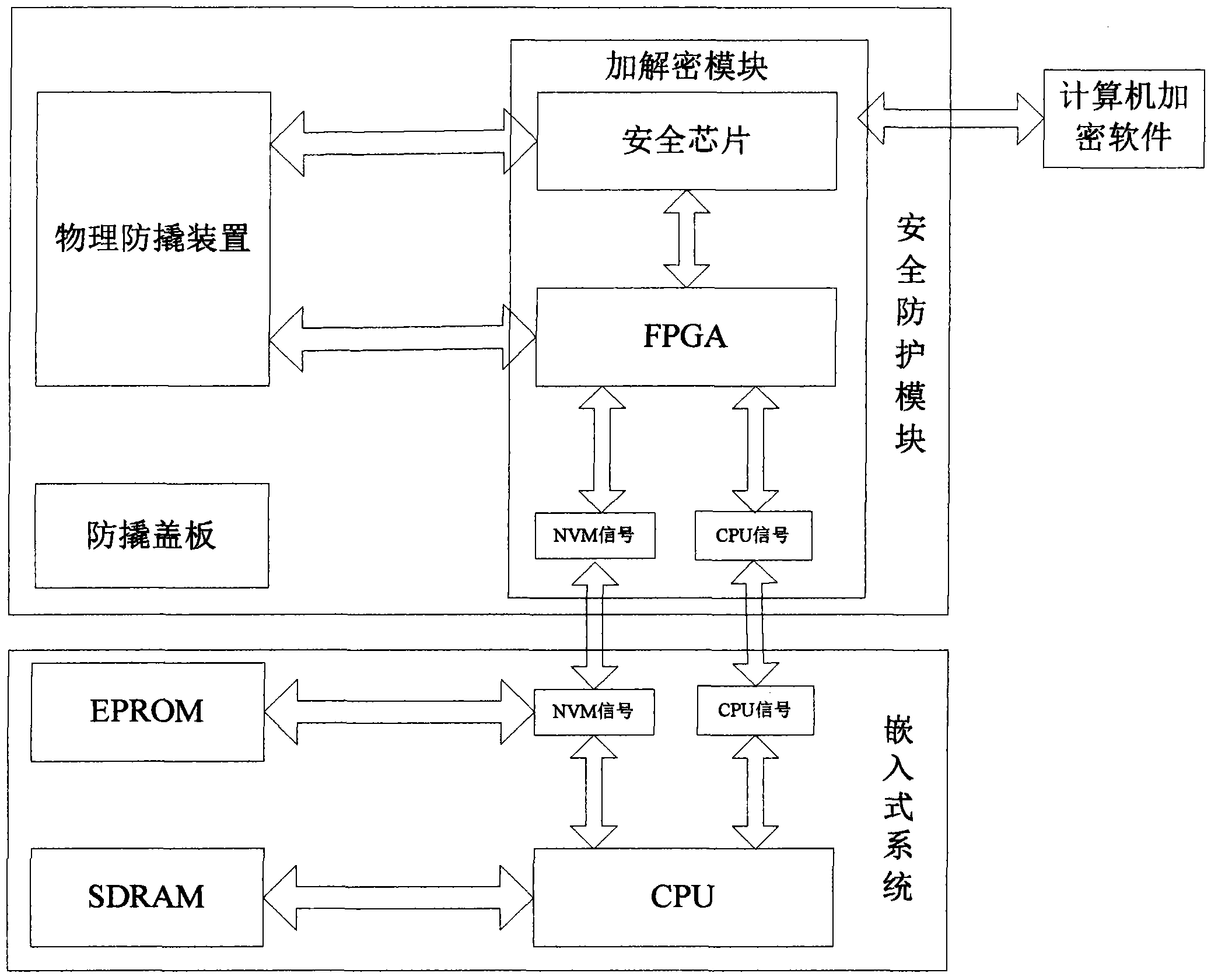
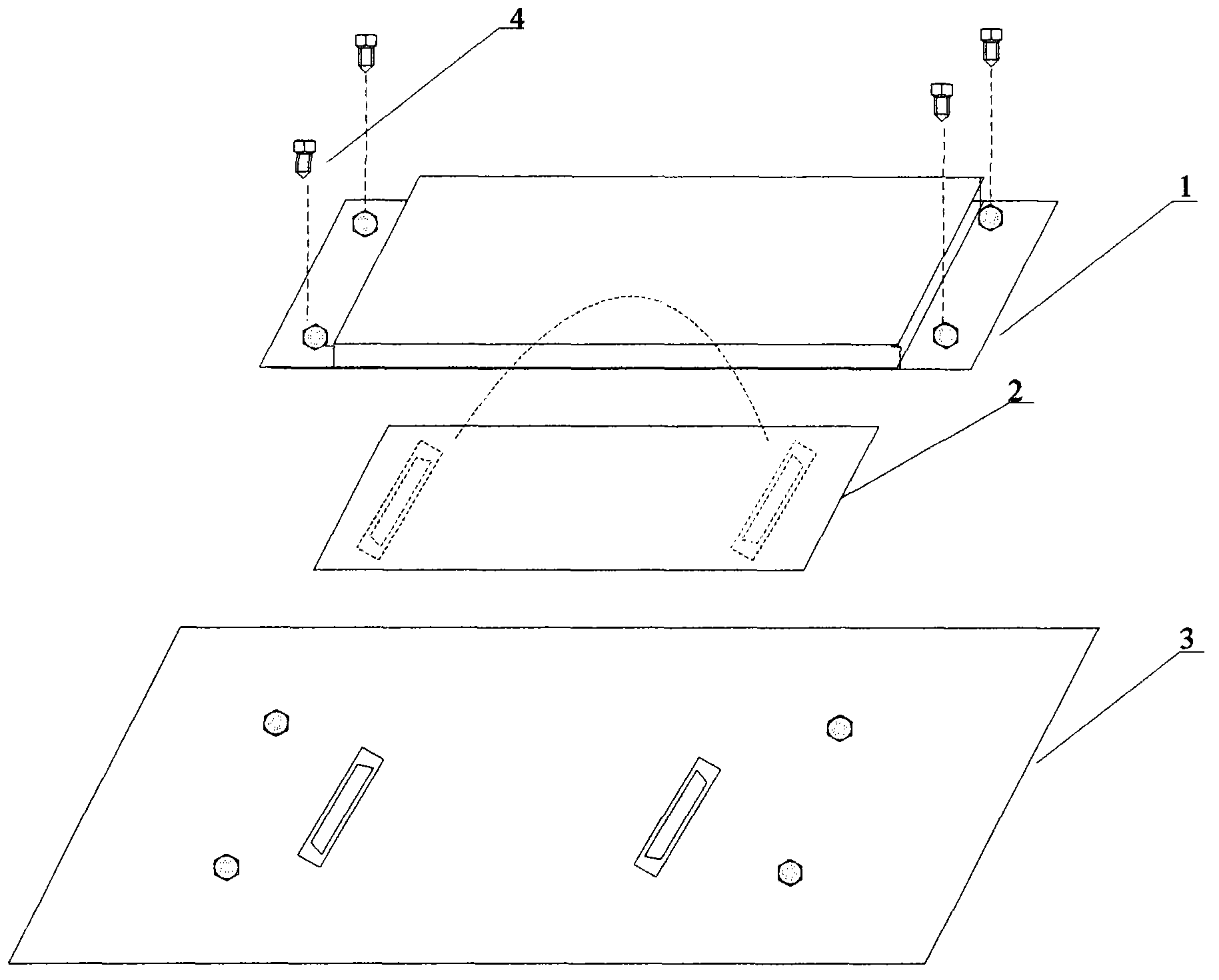
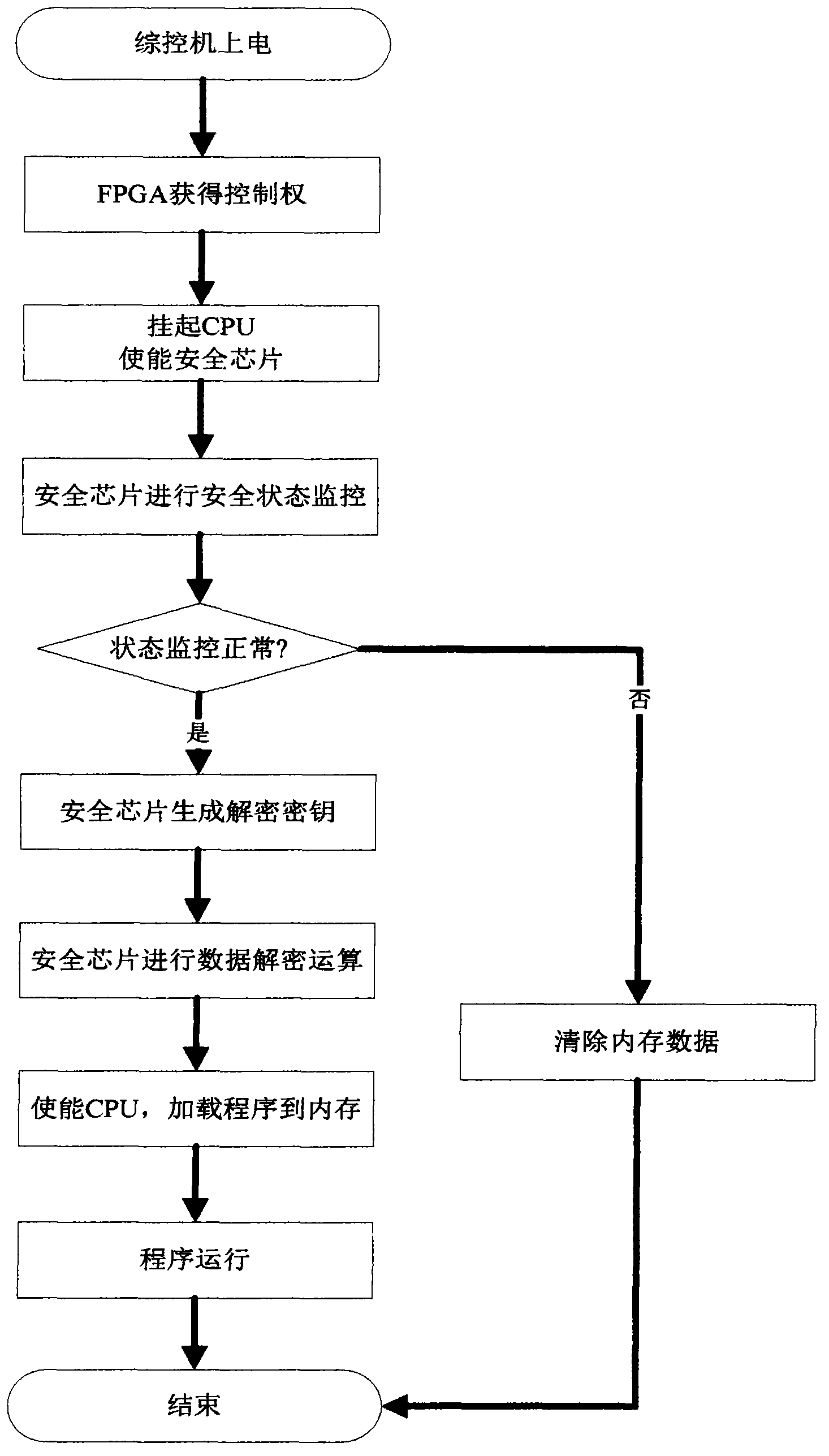
The invention belongs to the technical field of information safety, and in particular relates to an embedded software safety protection system which aims to improve the safety of embedded software. According to the system, a safety protection module is arranged on embedded equipment and comprises a physical prying-resistant device, a prying-resistant cover plate and a hardware encryption and decryption module circuit, wherein the hardware encryption and decryption module circuit is applied to adaption of a central processing unit (CPU) to data access of an electrically programmable read only memory (EPROM) and is matched with the physical prying-resistant device and the prying-resistant cover plate to dynamically protect static random access memory (SRAM) data. By virtue of the physical prying-resistant device and the prying-resistant cover plate, the system has destroy resistance and can prevent an attacker from acquiring sensitive information in a probe detection mode and the like; and moreover, the prying-resistant cover plate can shield electromagnetic radiation, thus preventing the attacker from attacking the safety system by utilizing the leakage of the electromagnetic radiation.
Owner:北京京航计算通讯研究所
A network application layer security protection system
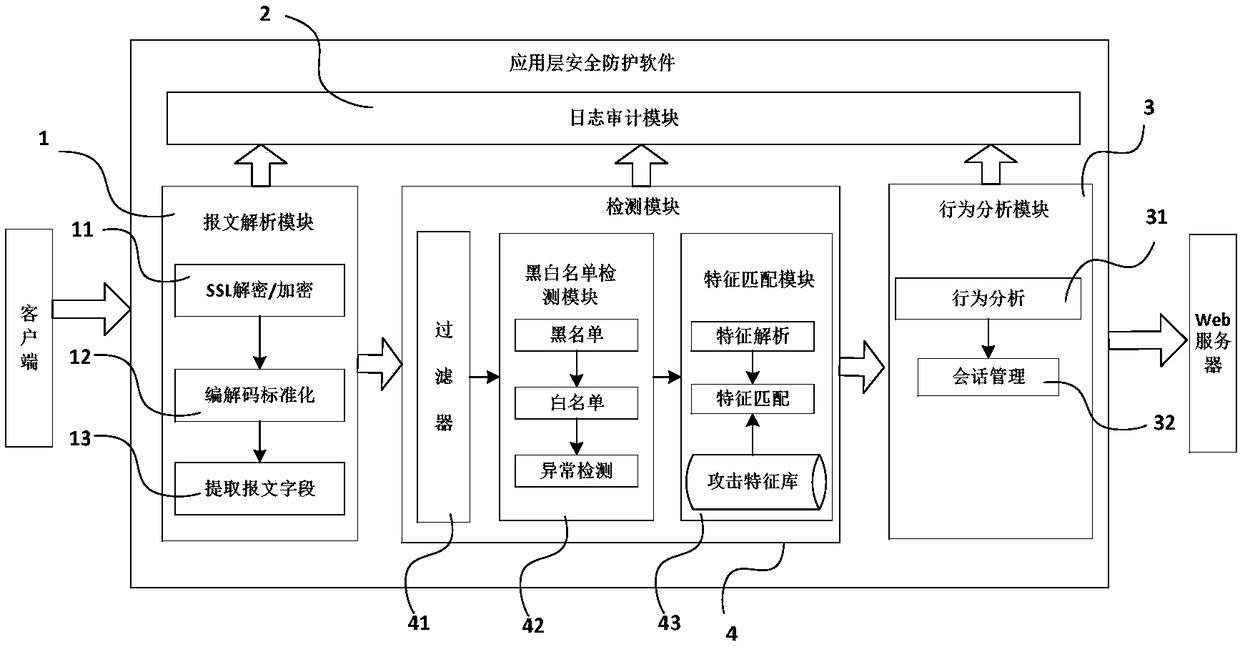
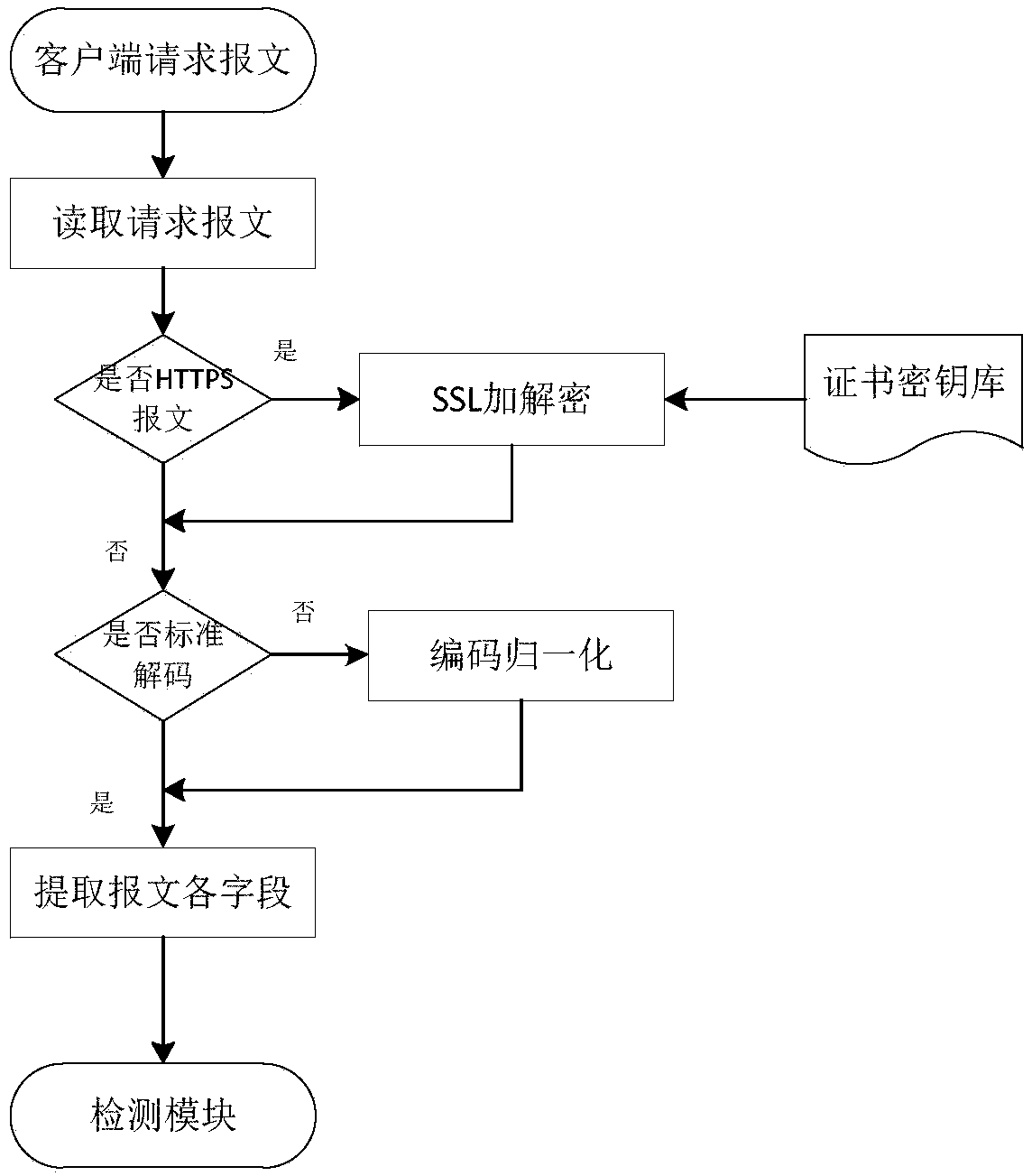
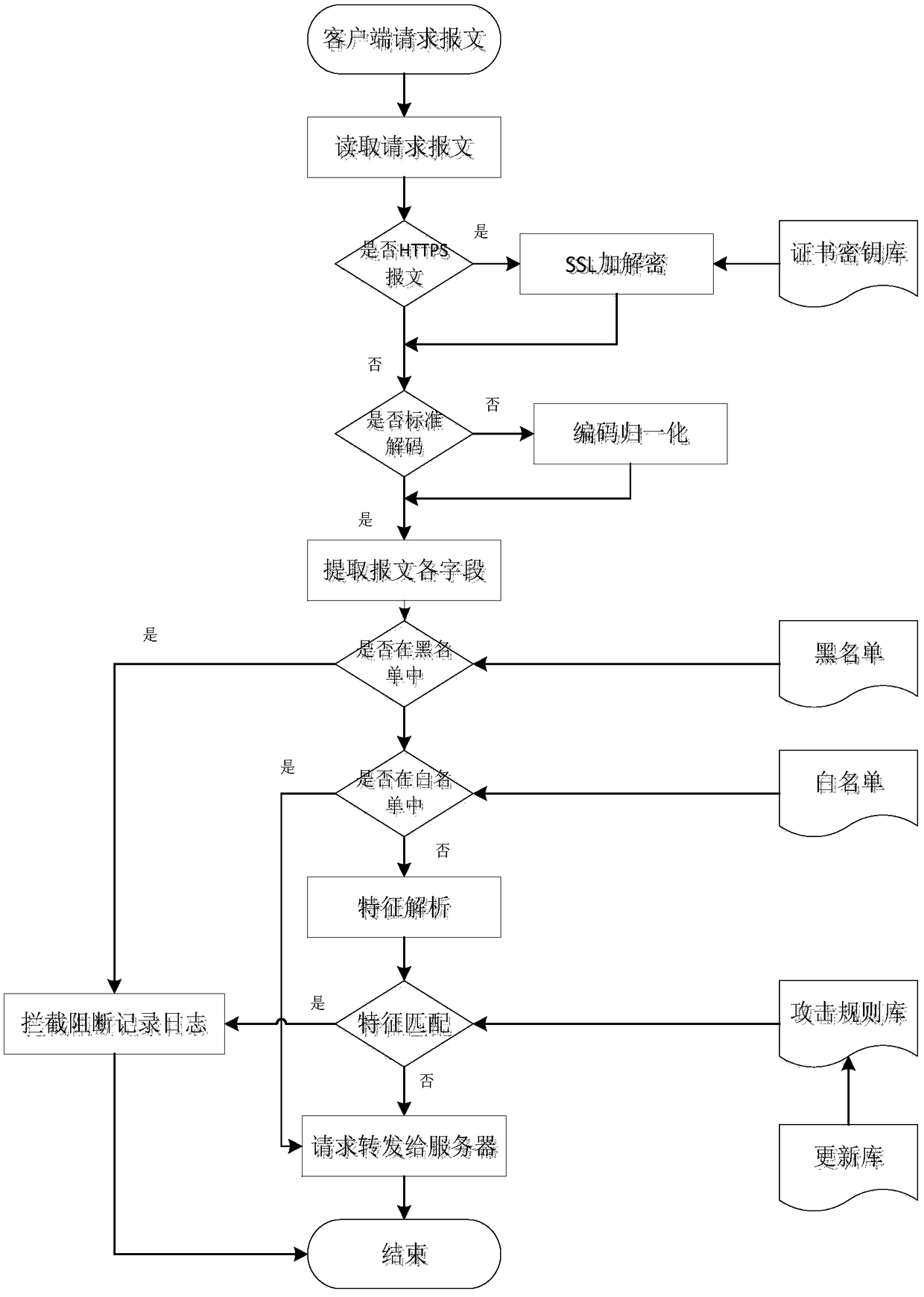
The invention discloses a network application layer security protection system, which comprises a message parsing module for judging and parsing the message, comprising SSL decryption, encoding and decoding standard normalization processing and message field information extraction, and then sending the extracted message characteristics to a detection module for attack detection; and a message parsing module for judging and parsing the message. The detection module comprises a filter, a black-and-white list detection module and a feature matching module. The behavior analysis module is used forverifying the DDoS attack to the message characteristic data passing through the detection module and outputting the verified message to the Web server. The log audit module is used for auditing behaviors and exceptions in the process of Web protection. In the process of feature analysis and matching, the behaviors of Web mail uploading, SMTP and FTP data transmission are transmitted to the log audit module for recording and analysis. In the process of security protection, the access records violating policies and rules are recorded.
Owner:BEIJING INST OF COMP TECH & APPL
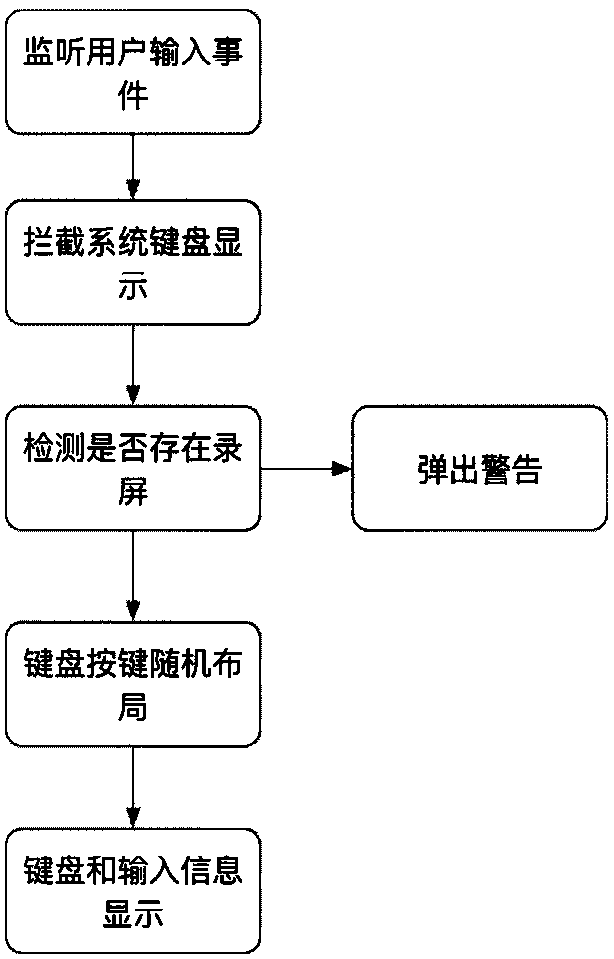
APP (Application) safety protection system and method under IOS (Iphone Operating System)
ActiveCN108595989AAvoid security issuesSecurity question validKey distribution for secure communicationEncryption apparatus with shift registers/memoriesProtective systemMobile app
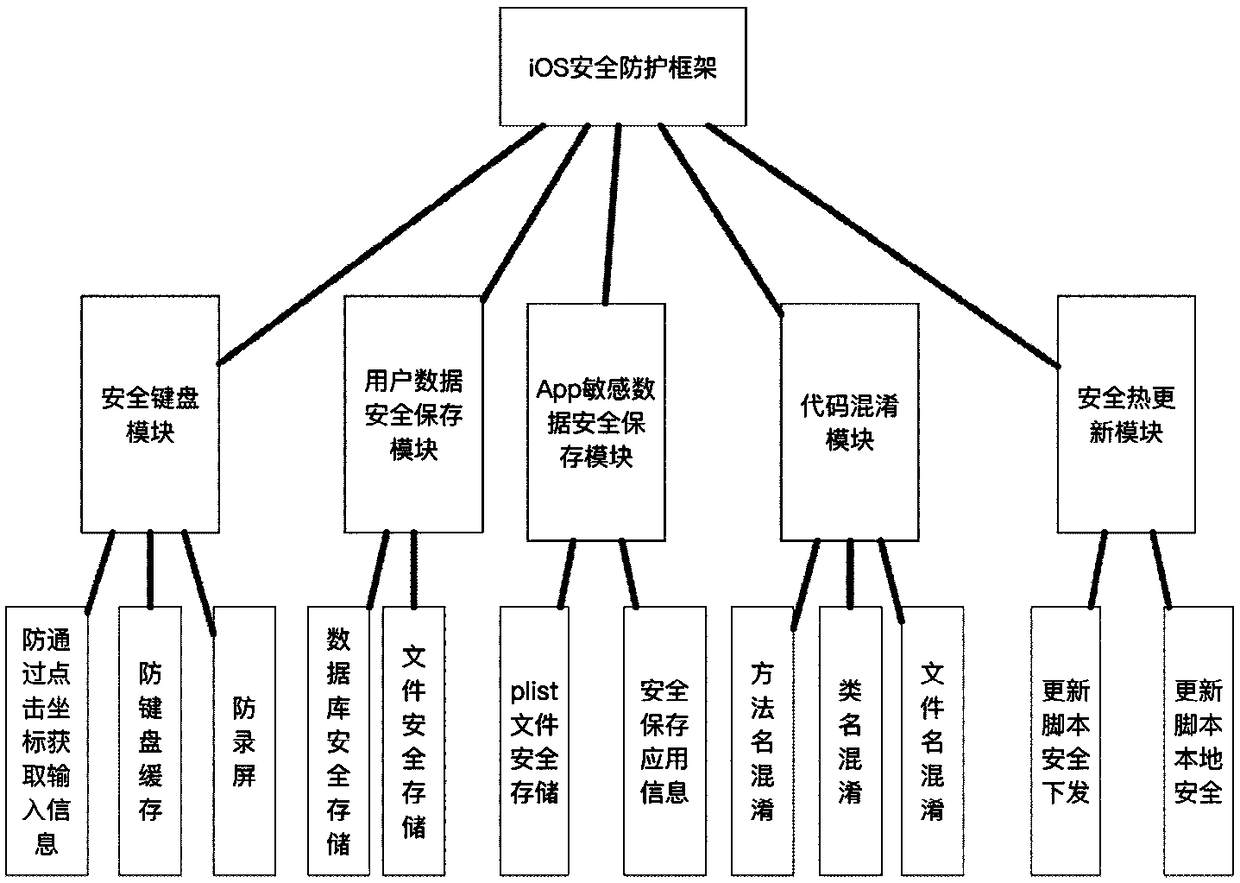
The invention discloses an APP (Application) safety protection system and method under an IOS (Iphone Operating System). The system comprise a safety keyboard module, a user data safety storage module, an App sensitive information storage module, a source code protection module and a safety hot update module, wherein the five safety protection modules are used for carrying out safety protection ona situation that an existing IOS mobile APP has defects and problems. By use of the system, solutions for five safety problems which are usually met in an existing iOS-App development process are integrated into a safety protection frame method, a developer only needs to apply the safety protection method to the App, effective safety protection can be carried out on the App through correct deployment, a developer can conveniently solve an App safety problem, development time is shortened, and the safety of the App is improved.
Owner:HANGZHOU DIANZI UNIV
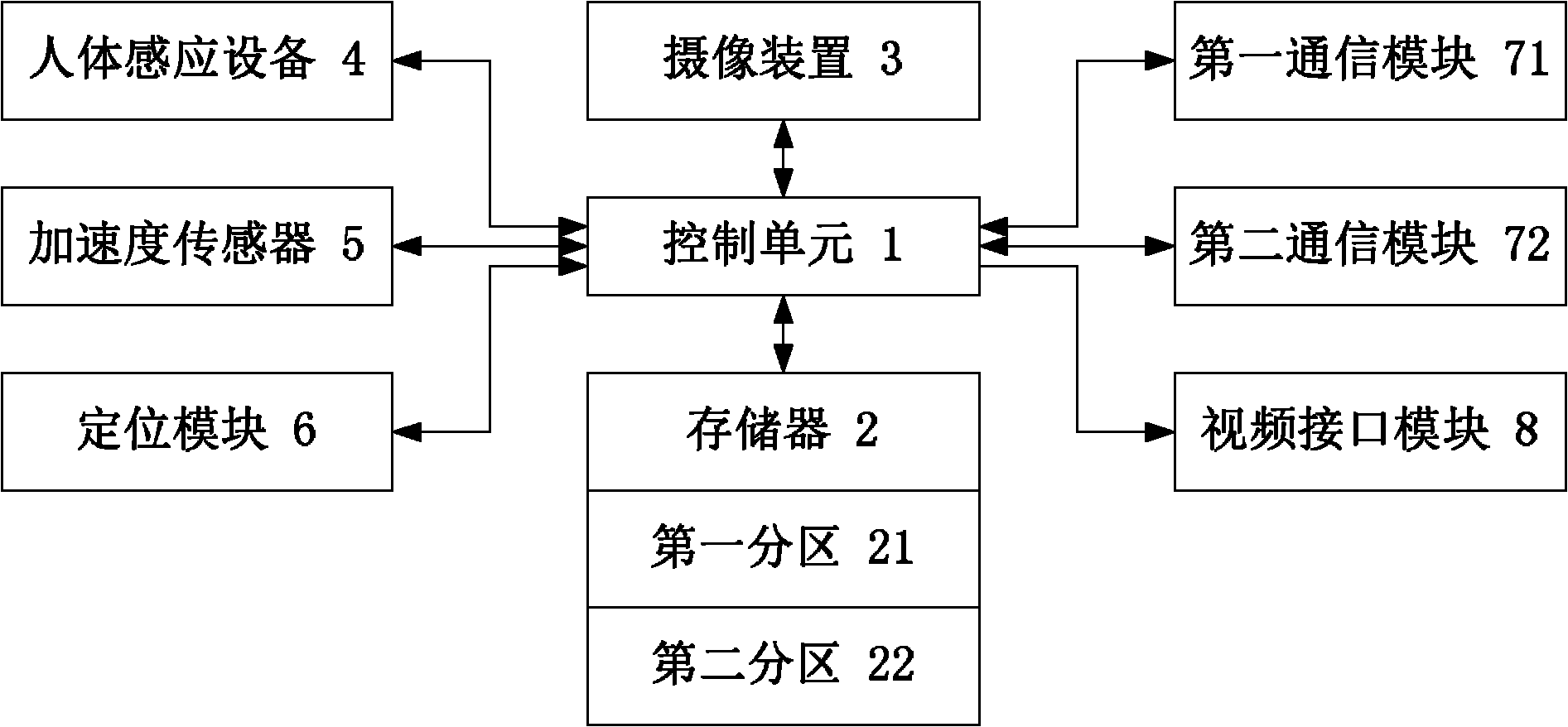
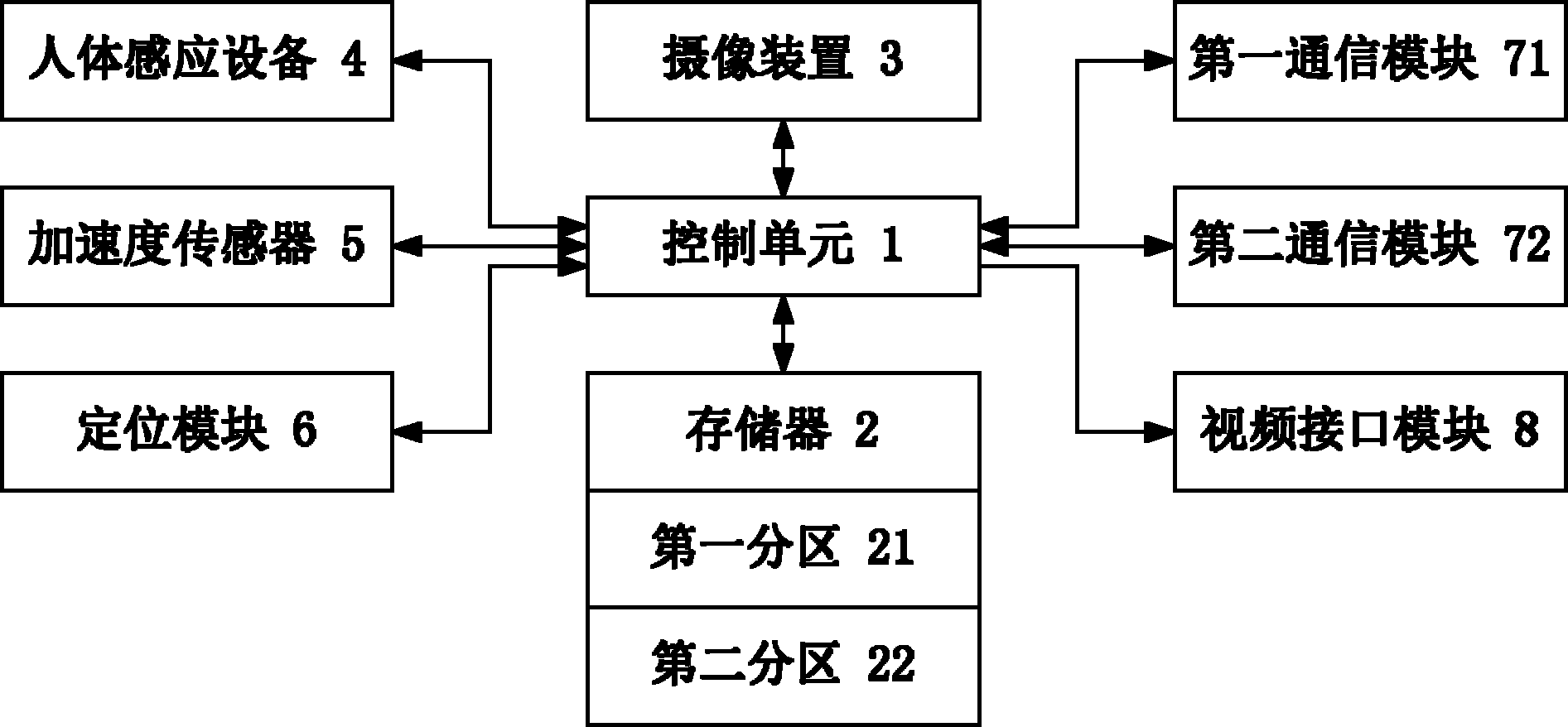
Video recording instrument of vehicle
InactiveCN102145683AEasy to investigateNot easy to formatTelevision system detailsRegistering/indicating working of vehiclesVideo recordVideo recording
The invention provides a video recording instrument of a vehicle, which comprises human body induction equipment, an acceleration sensor, a photographing device, a control unit and a storage, wherein the human body induction equipment is used for generating a first signal when a human body approaches the human body induction equipment; the acceleration sensor is used for generating a second signal when the movement of an automobile is detected; the control unit drives the photographing device to automatically detect the human body and identify the face of the human body when an automobile is in a shut-down state if the first signal and the second signal are received and meet preset conditions, and stores the photographing data as special data in a first partition after the successful identification, and the control unit judges whether the second signal which meets the preset conditions exists when detecting that the automobile is in a startup state, and stores the photographing data as the special data in the first partition if the second signal which meets the preset conditions exists, or stores the photographing data as ordinary data in a second partition; and the storage is used for storing the special data. In the invention, the acquisition, the storage and the safe transmission of the photographing data carrying human face information of a person who approaches the automobile are realized by dint of a microwave sensor, the acceleration sensor and the photographing device.
Owner:STEELMATE CO LTD
Multifunctional monitoring system of substation in zone
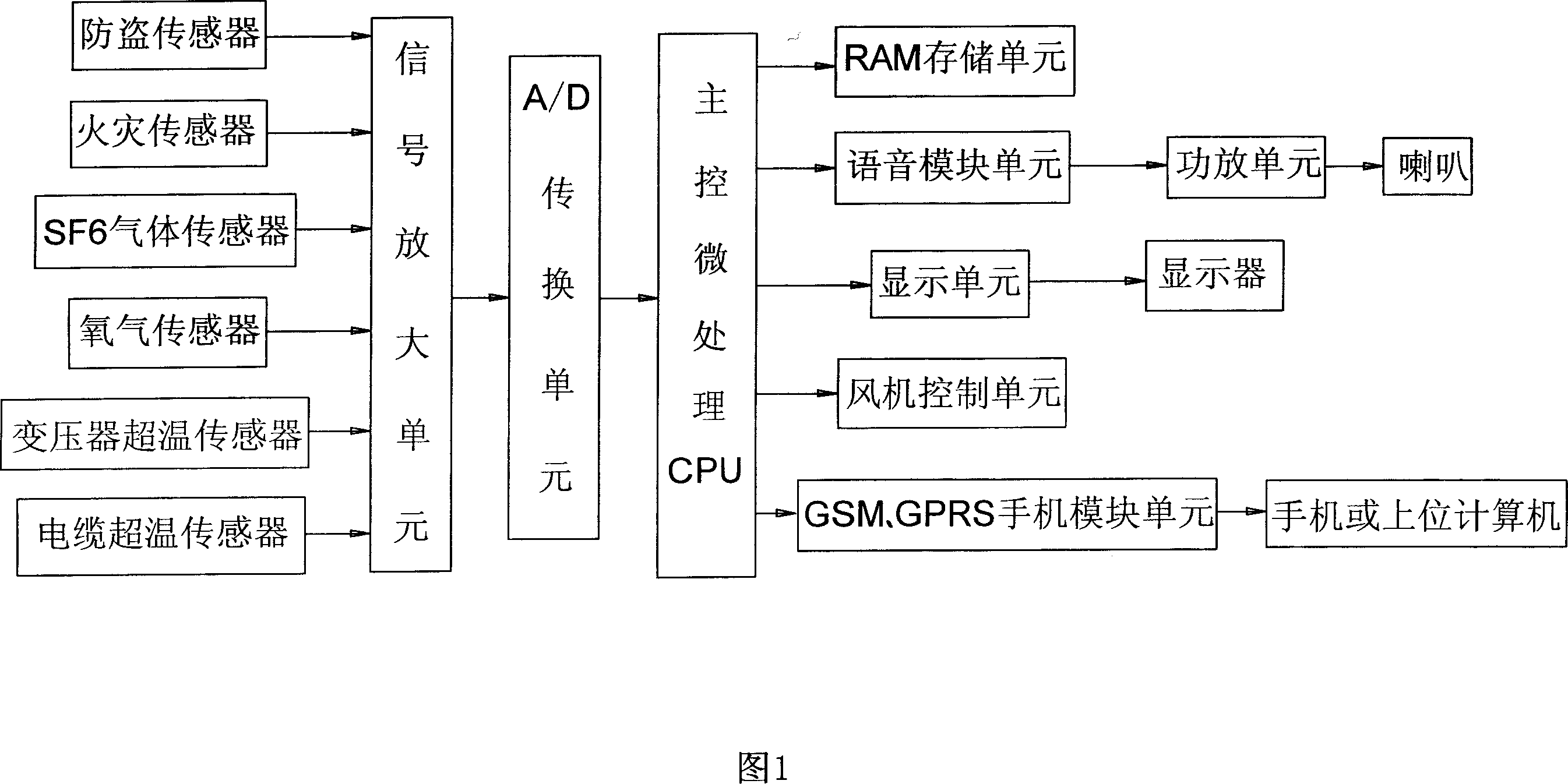
InactiveCN101030710AEffective security protectionMany monitoring itemsComputer controlCircuit arrangementsDaily operationTransformer
The invention is concerned with general intelligent on-line monitor process for existent safety defending hidden trouble during the process of daily operation to substation of uptown, especially a kind of multi-function monitor system to substation uptown. The sensor of preventing steal, fire, SF6 gas, oxygen, super-temperature of transformer and super-temperature of cable connects with signal magnify unit respectively, and the signal magnify unit connects with A / D conversion unit which is connecting with main tiny treatment CPU. The main tiny treatment CPU connects with RAM location, sound module unit, display unit, fan, control unit, GAM, GPRS mobile telephone module unit respectively. The sound module unit connects with power amplifier unit and the display unit connects with LCD display. The system carries long-distance alarm and control through GM and GPRS wireless communication network, and the data send to the high-class computer through GSM and GPRS, so one terminal can realize the wireless monitor to many host computers.
Owner:常州市科惠电力设备有限公司
Crane boom working parameter measuring method, controller, apparatus, and crane
InactiveCN102502406AImprove reliabilityHigh precisionCranesLoad-engaging elementsMeasurement deviceIndustrial engineering
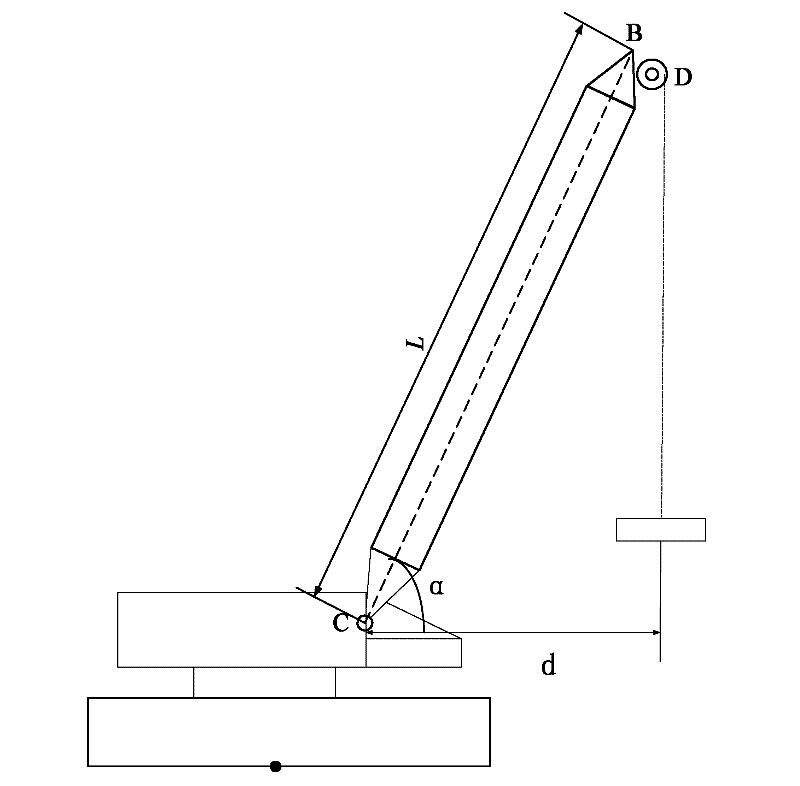
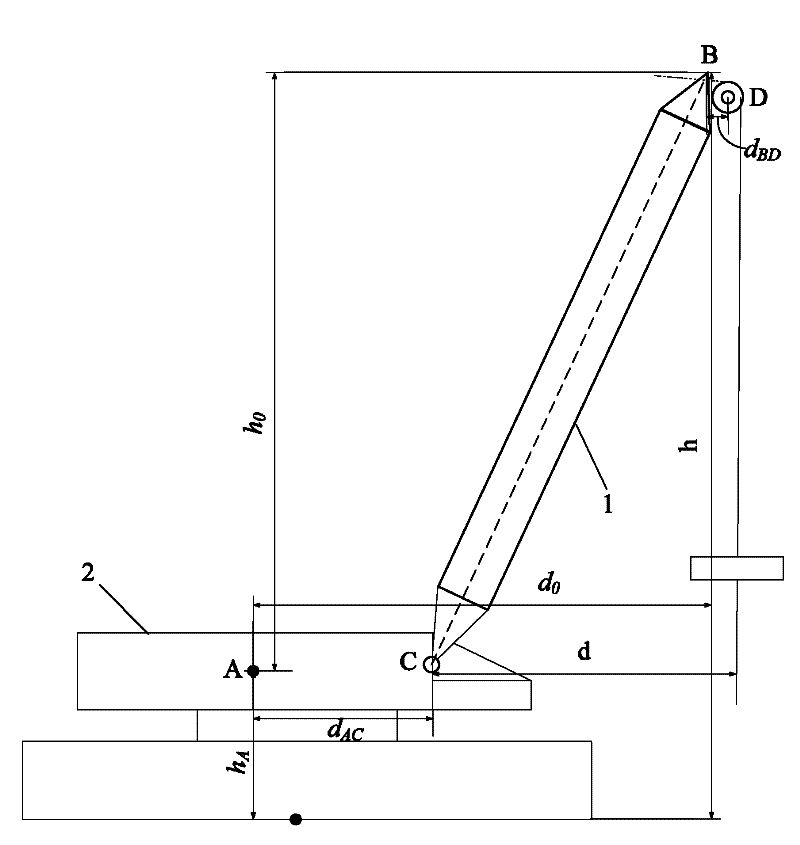
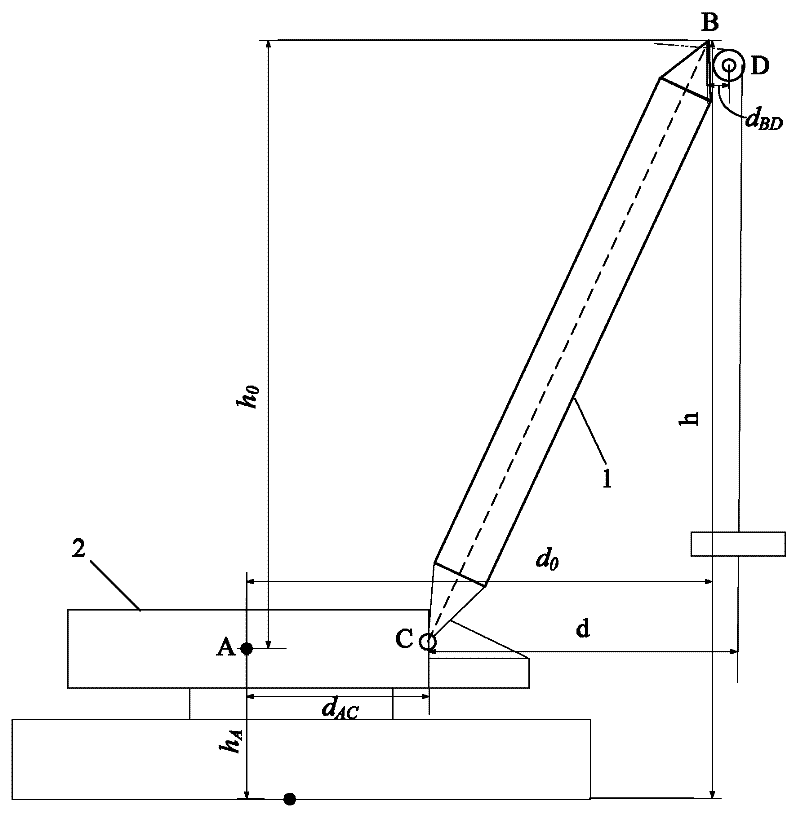
The invention discloses a crane boom working parameter measuring method. A hinge connection point is adopted as a point C. A point B on the top of the boom is connected with a lifting hook pulley. The center of the lifting hook pulley is adopted as a point D. A horizontal range between the point B and the point D is dBD. A point A is set on a crane body (2). A horizontal range d0 and a vertical range h0 between the point A and the point B are measured; a horizontal range dAC between the point A and the point C is measured; and a vertical height hA of the point A relative to the ground is measured. A working amplitude of the boom (1) is calculated according to a formula of d=d0-dAC+dBD, and a working height of the boom (1) is calculated according to a formula that h=h0+hA. The invention also provides a controller and a measuring apparatus employing the measuring method. According to the invention, a differential distance measuring technology is adopted for measuring the working parameters of the crane. Current working parameters of the crane can be precisely obtained without correction. Therefore, reliability and precision of a crane safety protection apparatus are improved, such that safety protection can be effectively carried out.
Owner:ZOOMLION HEAVY IND CO LTD
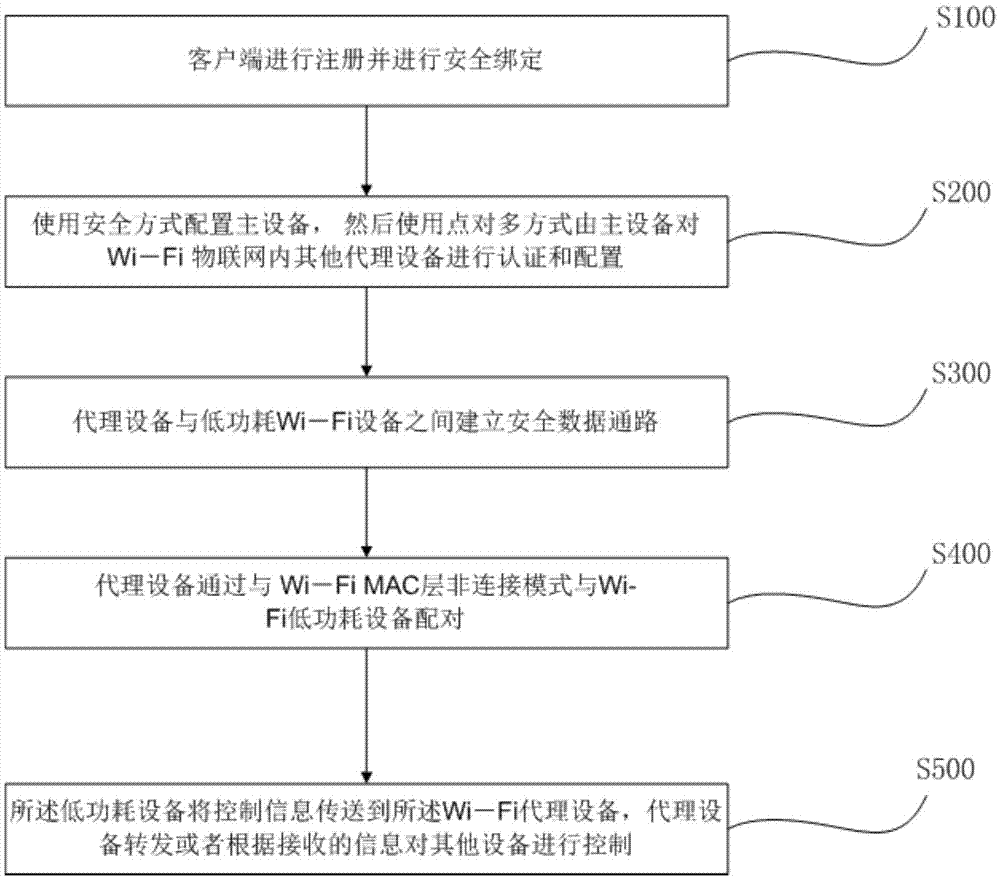
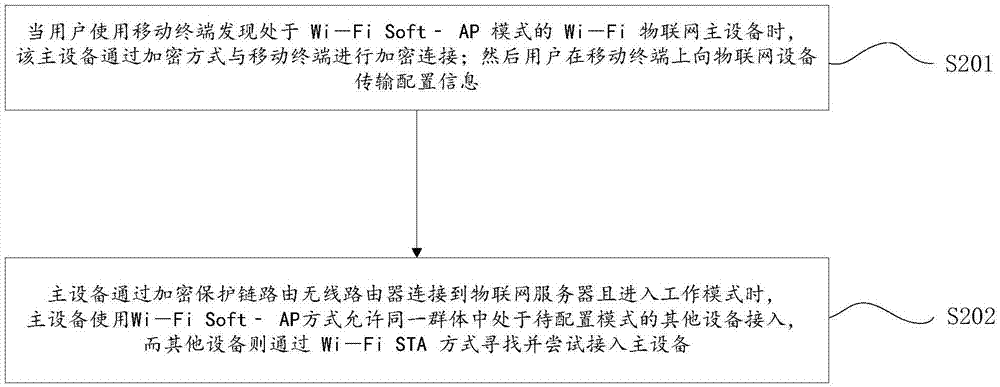
Proxy device Internet of Things configuration method with high safety and low power consumption, and system implementing method
ActiveCN105451231ASolve power consumptionSimple configurationPower managementConnection managementWi-FiInternet of Things
The invention provides a proxy device Internet of Things (IoT) configuration method with high safety and low power consumption, and a system implementing the method. The method comprises the following steps: a smart terminal is registered, and safety binding between the smart terminal and Wi-Fi IoT devices is carried out; a master device of one proxy device in the Wi-Fi IoT is configured in a safe mode, and then the master device authenticate and configure other proxy devices in the Wi-Fi IoT in a point-to-multipoint manner; a safety data path is established between the proxy devices and Wi-Fi devices with low power consumption; the proxy devices are paired with the Wi-Fi devices with low power consumption in a Wi-Fi MAC layer non-connection manner; the Wi-Fi devices with low power consumption can work and send specific information to the proxy devices when triggering conditions are met, and the proxy devices can forward the information or adjust the statuses of the other devices in the network according to the received specific information. The invention provides an IoT system which is extensible, easy to configure, and safe.
Owner:ESPRESSIF SYST SHANGHAI
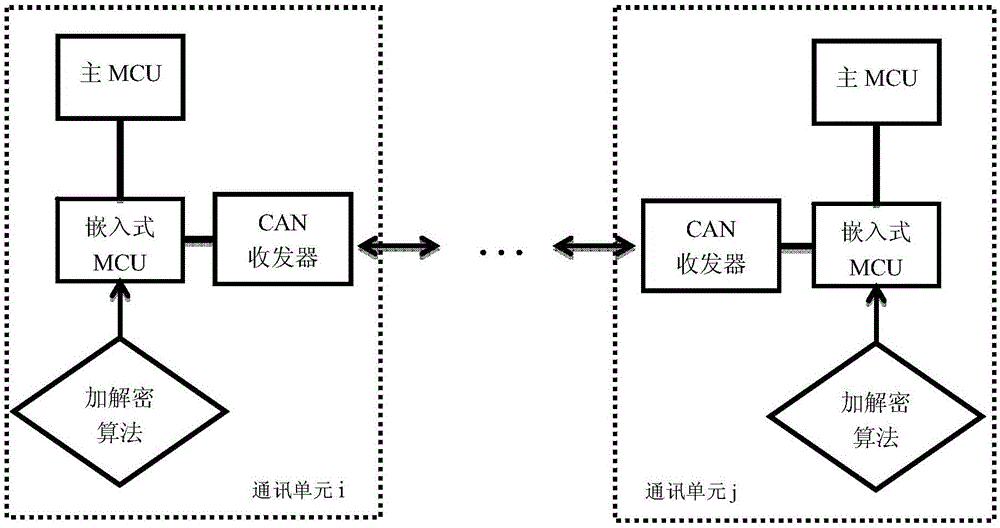
Electric automobile distributed controller information safety method and system
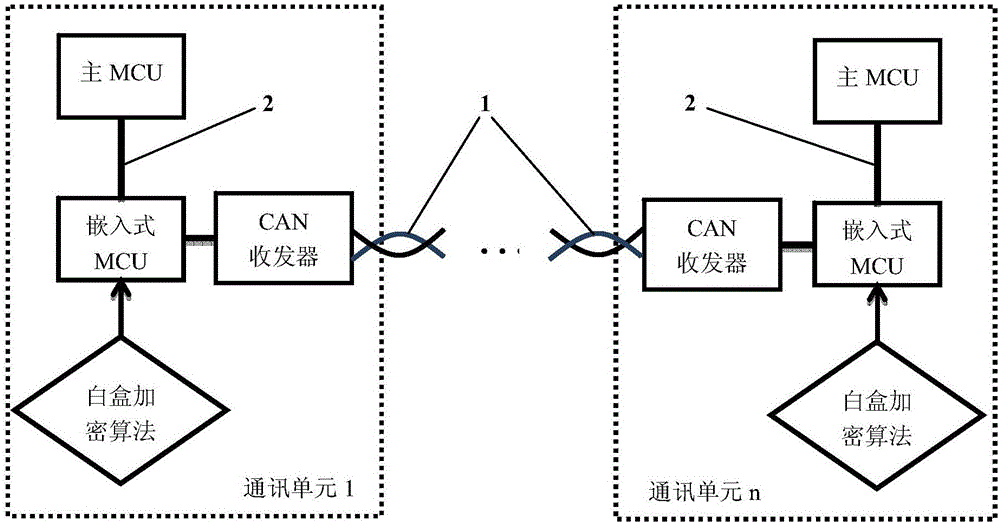
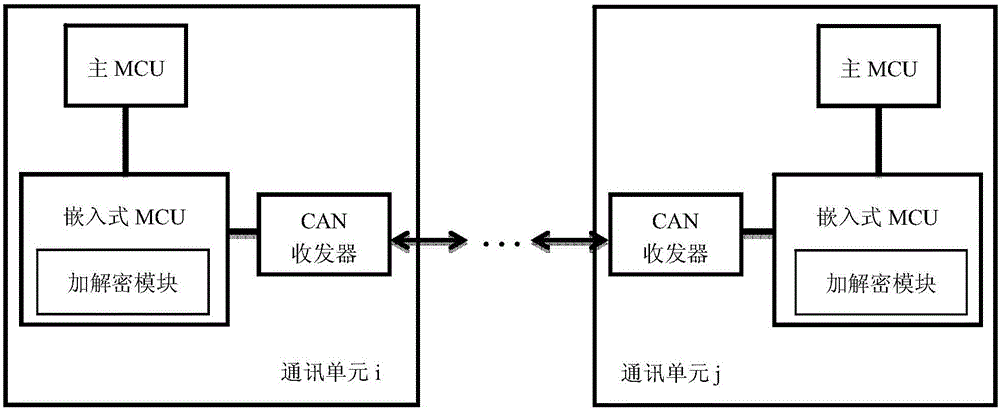
ActiveCN106143364AAgainst leaksPrevent leakageElectric/fluid circuitBus networksCommunication unitArea network
The invention relates to an electric automobile distributed controller information safety method and system. The information safety method is characterized in that an embedded MCU (Microprogrammed Control Unit) and a CAN (Controller Area Network) transceiver are added in each electric automobile controller, and are mutually connected in each electric automobile controller; the embedded MCU is connected with an existing main MCU in each electric automobile controller so as to form a communication unit of the corresponding electric automobile controller; the communication units are connected through respective CAN transceiver so as to form a distributed framework to carry out CAN information transceiving; an encryption and decryption algorithm is built in the embedded MCU in each communication unit so as to encrypt and decrypt CAN information at real time and carry out safety isolation protection. The information safety method provided by the invention can be used for monitoring and controlling electric automobile controller network data information transmission at real time, so that the safety monitoring and protection of the CAN information are effectively ensured.
Owner:BEIHANG UNIV
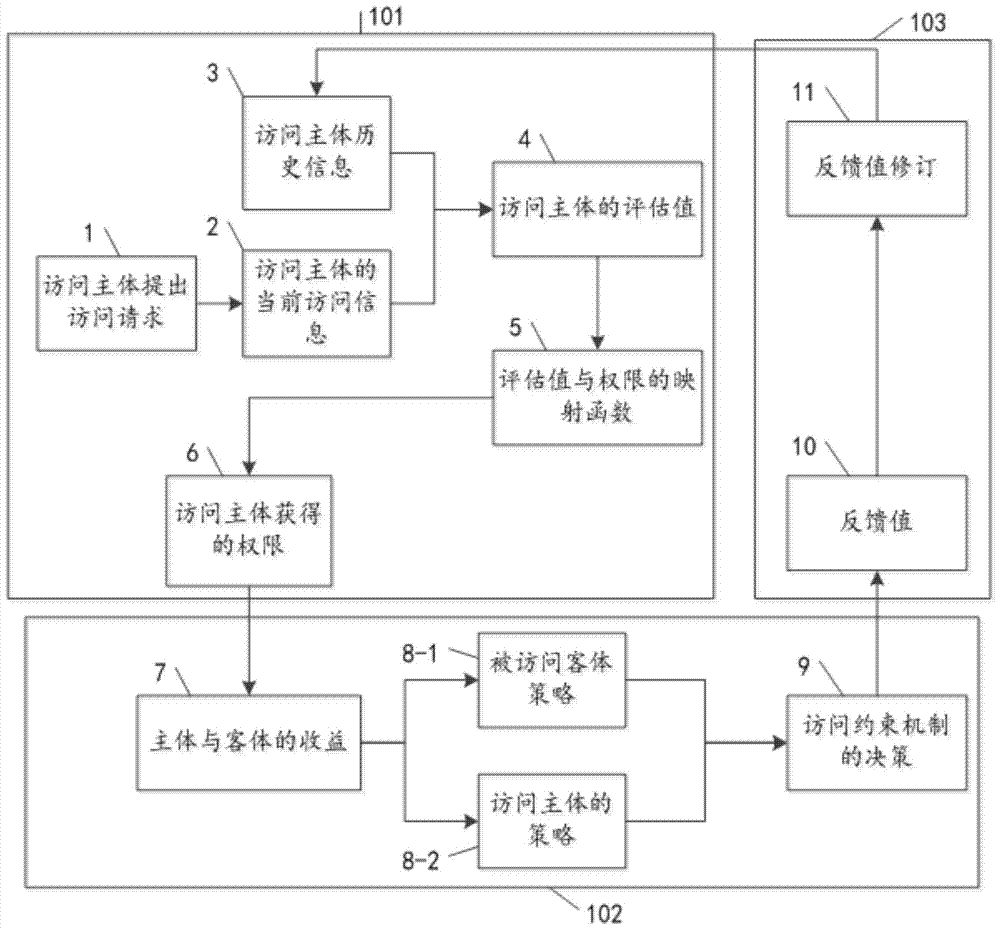
Access control method based on dynamic game
The invention discloses an access control method based on a dynamic game. The method comprises the access process, the game process and the feedback process. The access process is the access process that a subject has access to an object, and after the access subject puts forwards an access request, a permission set with which a user can be endowed is obtained, wherein the permission set corresponds to the assessed value of the latest access of the subject. The game process is a simulated game process between the access subject and the accessed object and an ultimate decision process of an access restraint mechanism, the Nash equilibrium is achieved through the dynamic game between the subject and the accessed object, the access subject is promoted to initiatively tend to the honest access, and the access restraint mechanism ultimately works out the acceptability to the access request proposed by the subject according to an access strategy. The feedback process is the process that according to the performance of the subject in the latest access, the access restraint mechanism works out the feedback value serving as the feedback information, and the feedback information is moderately amended. It is ensured that an access control mechanism provides more effective safety protection on the information, resources and services in the open network in the whole process.
Owner:山东政信大数据科技有限责任公司
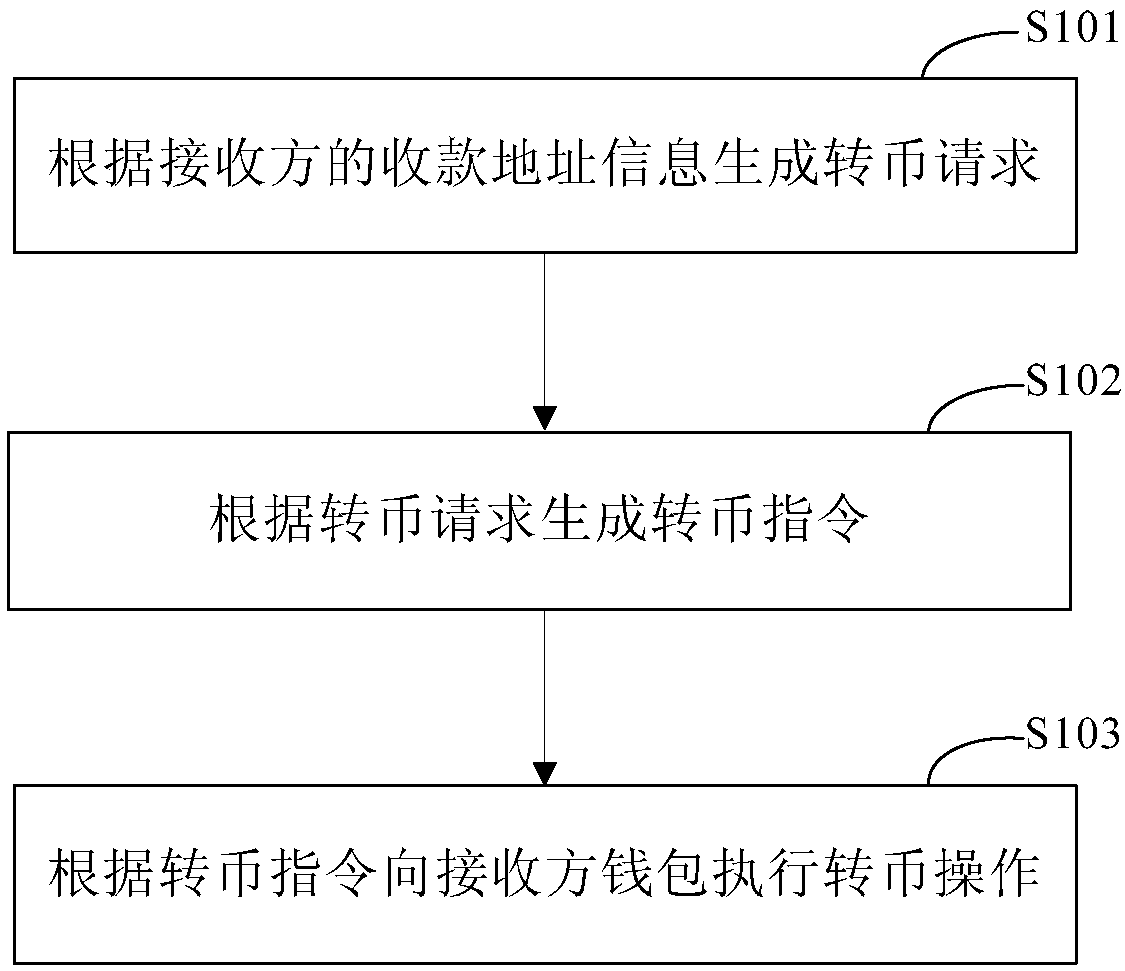
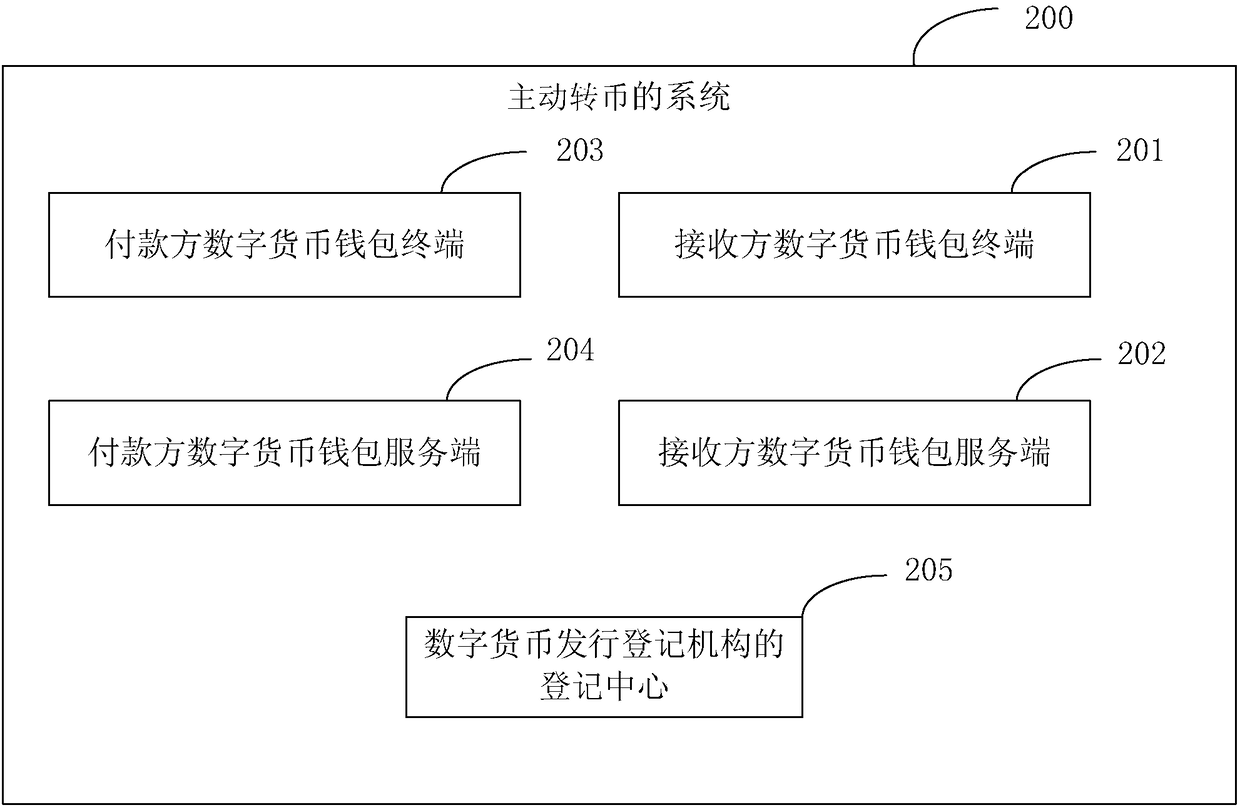
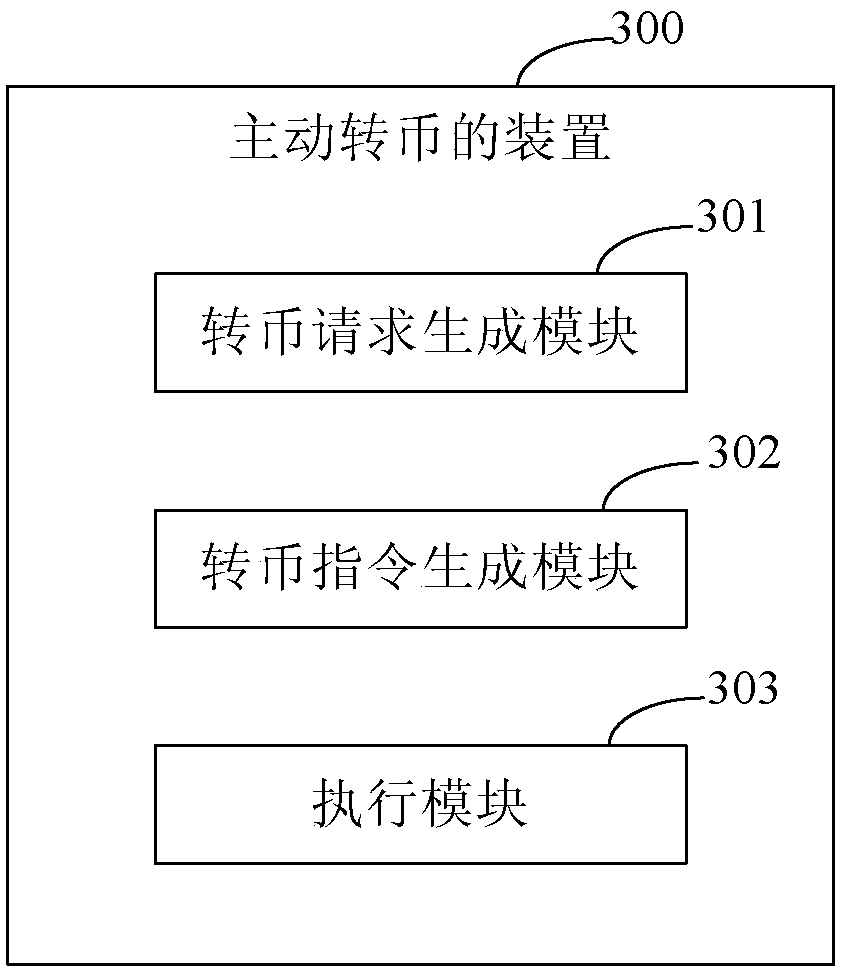
Method, apparatus, and system for active currency transferring
The embodiments of the invention provide a method, apparatus, and system for active currency transferring so that digital currency can be stored actually and a digital currency transferring mechanismthat is initiated by a payer between specific wallets can be realized. The method comprises: a currency transferring request is generated according to collection address information of a receiver; a currency transferring instruction is generated based on the currency transferring request; and according to the currency transferring request, currency transferring is carried out on a receiver walletbased on the currency transferring instruction.
Owner:THE PEOPLES BANK OF CHINA DIGITAL CURRENCY INST
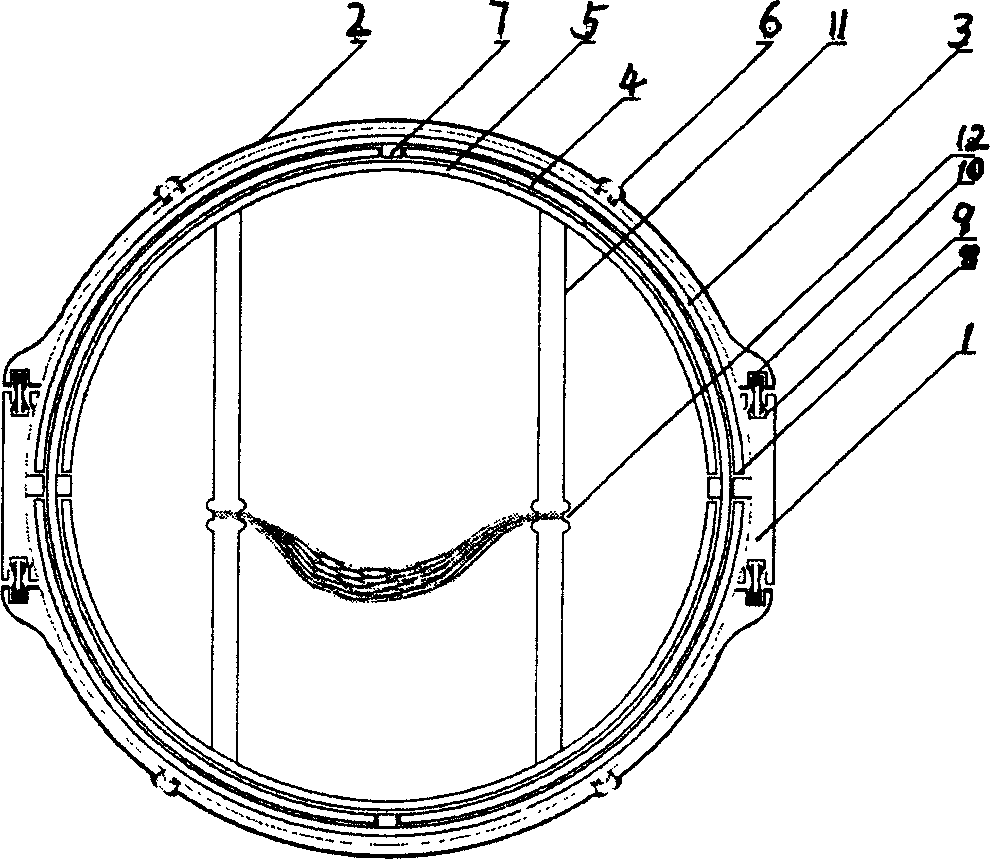
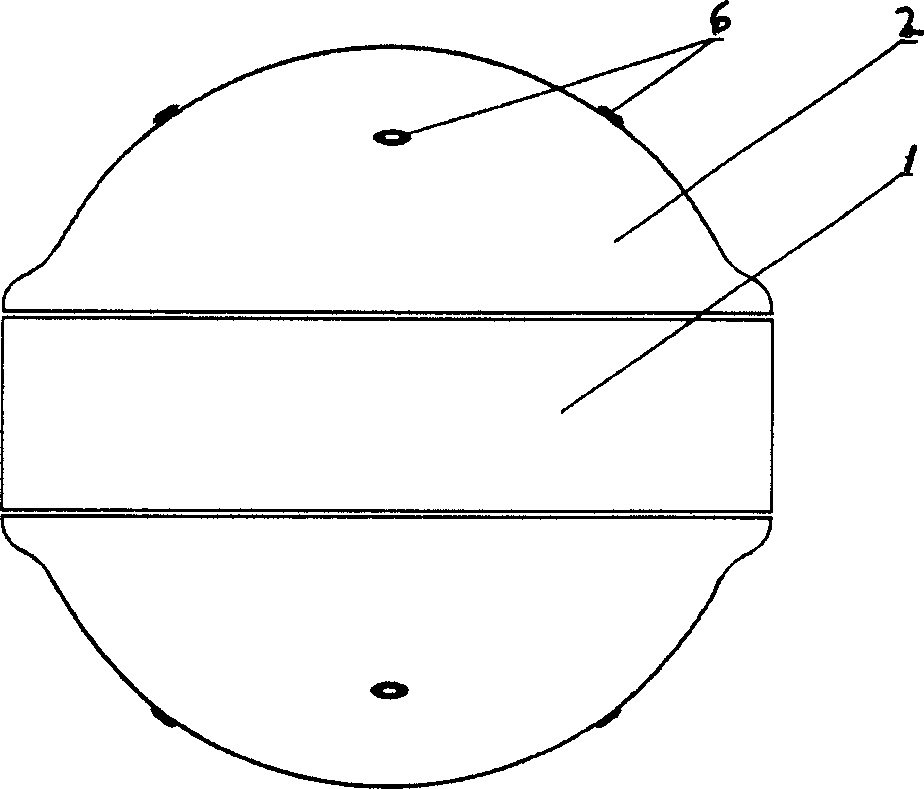
Water-life-saving device
The present invention relates to a water lifesaving device, it is characterized by that it mainly comprises a hollow ball-shaped external shell assembled by utilizing a table-shaped base seat and a ball-crown-shaped clamshell, on the external shell an air flow valve is set, and in the interior of said ball-shaped internal cavity three mutually perperdicular collars which are cover-mounted together are cover-mounted by means of rotation shaft, on the collar a man-carrying device is set. Its structure is novel, design is reasonable, safety is high, so that it has strong practicability.
Owner:戒忍 +2
Crane beam frame construction method
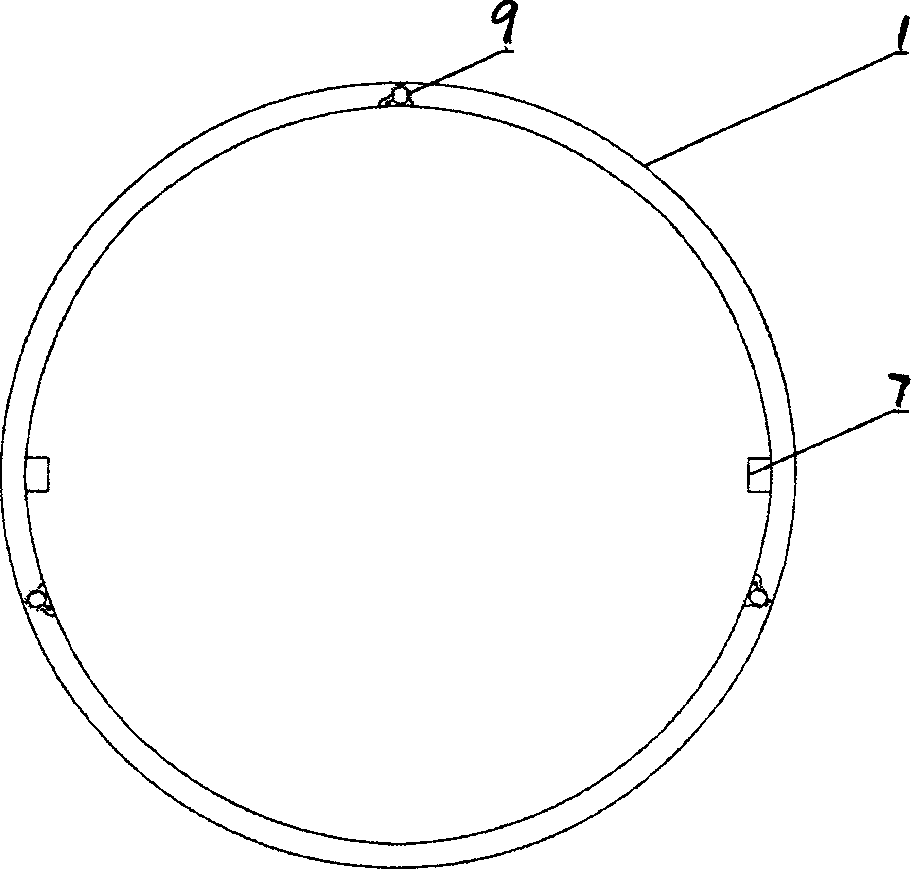
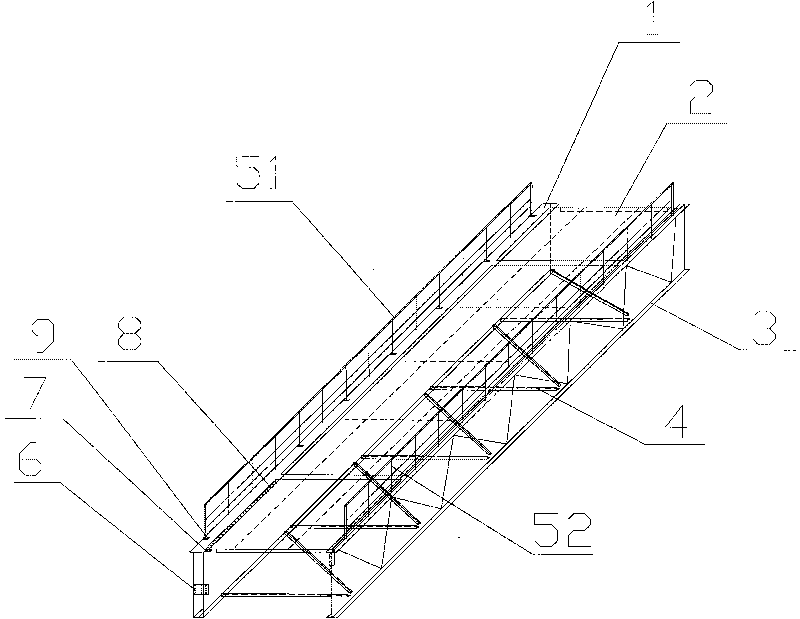
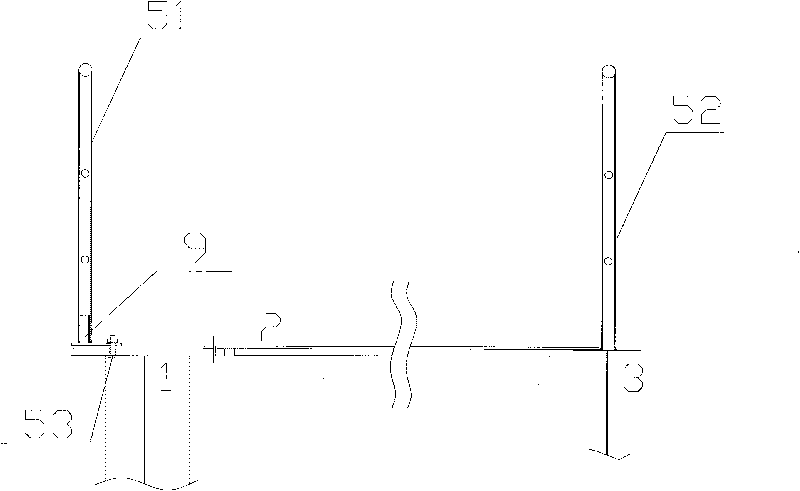
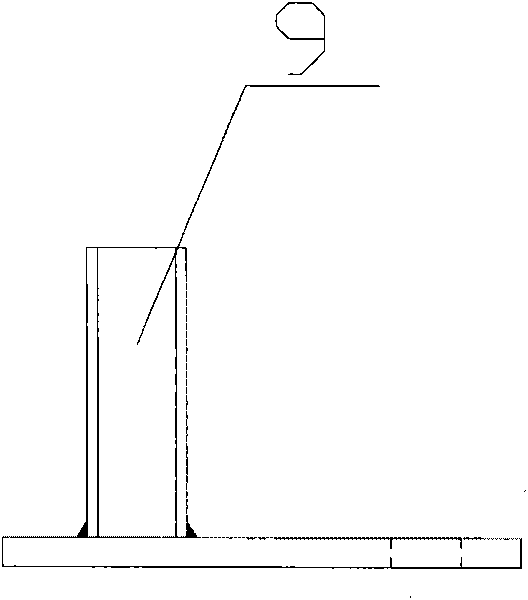
ActiveCN101759098AReduce the amount of work at heightsReduce investmentLoad-engaging girdersSupport planeBeam system
The invention relates to the crane beam system construction field, in particular to a crane beam frame construction method. The method comprises three steps of assembling on the ground, integral-hoisting and commissioning of formal railings. The crane beam frame comprises a crane beam (1), a brake board (2), a truss (3), a horizontal support frame (4), a connection plate (6), a hinge plate (7) and stopping plate bolts (8). The crane beam frame is characterized in that the crane beam frame also comprises temporary railings (51), formal railings (52), railing bolts (53) and connection members (9), the upper part of the crane beam (1) is fixed with the temporary railings (51) through the connection members (9) and the railing bolts (53), the upper part of the auxiliary truss (3) is welded and fixed with the formal railings (52); and the integral-hoisting and the commissioning of the formal railings are performed in turn after the crane beam frame is assembled on the ground. The invention reduces the quantity of works at heights, the operation is safe, the working efficiency and quality are high, the investment is little and the applicability is high.
Owner:MCC5 GROUP CORP SHANGHAI
Safety protection system, method and equipment and storage medium
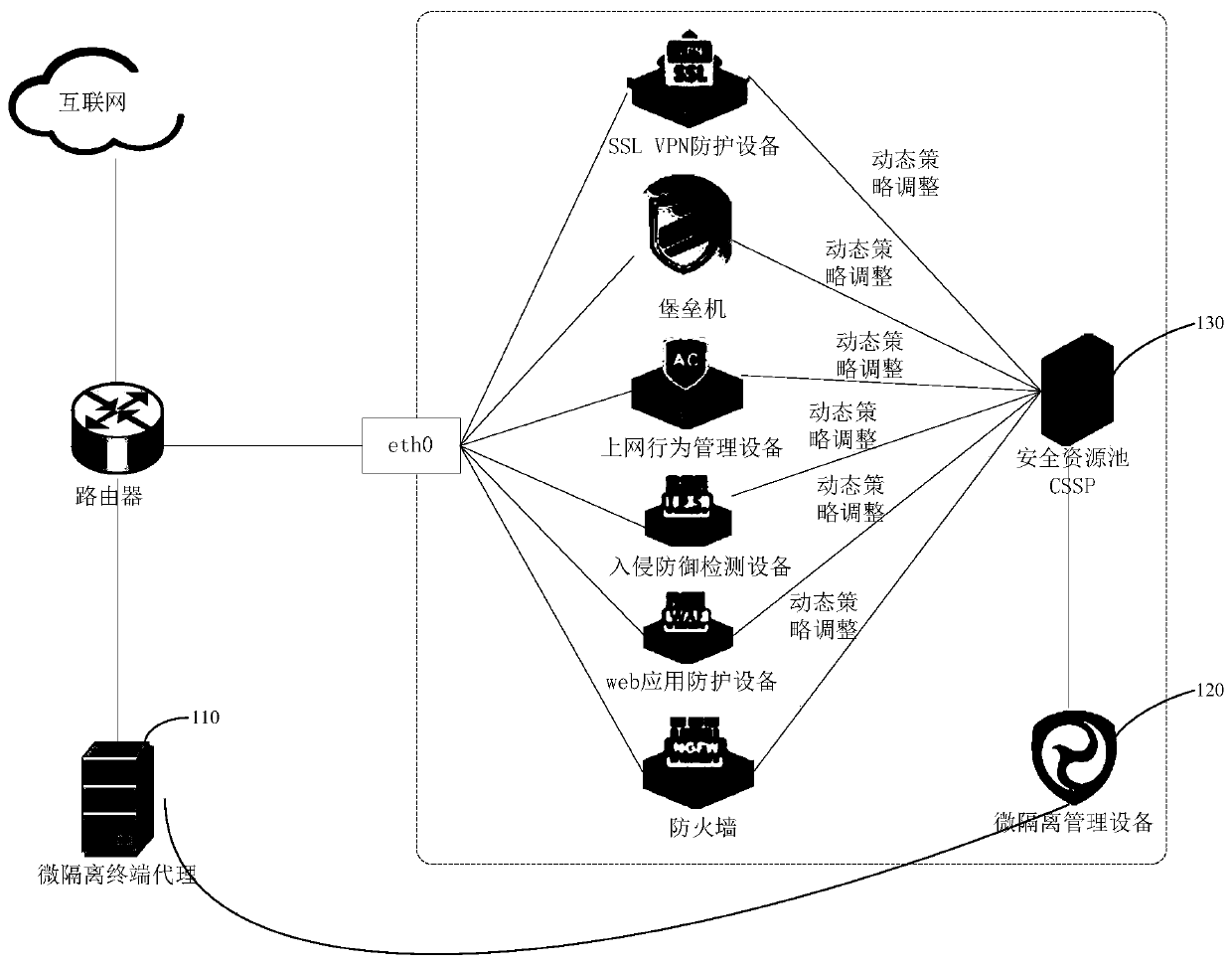
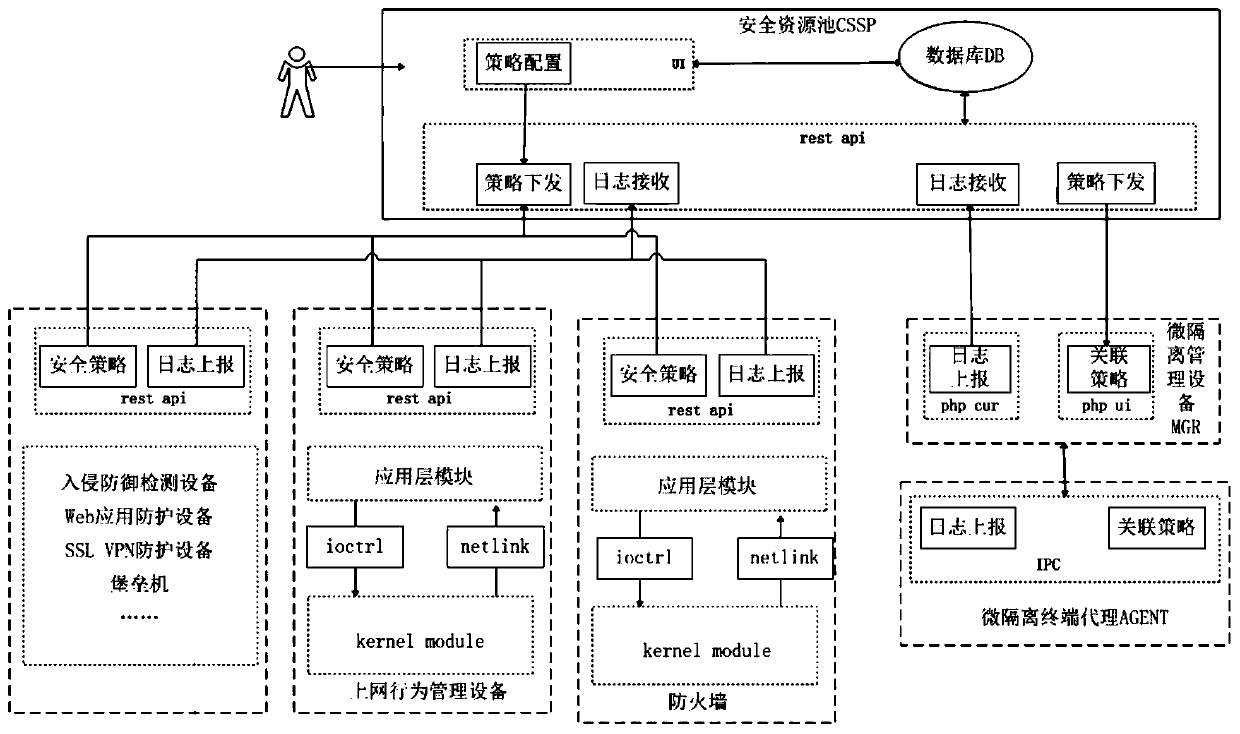
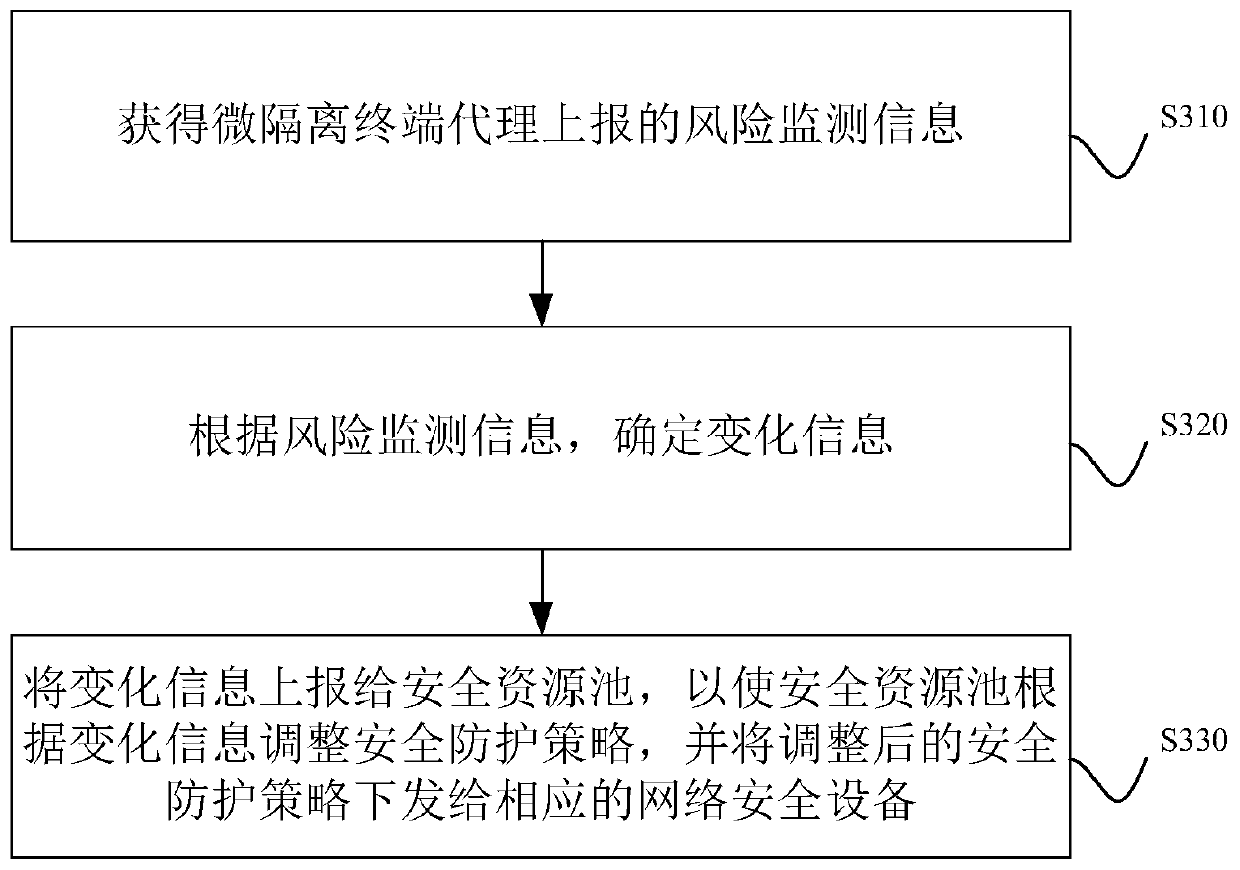
The invention discloses a security protection system. The system comprises a micro-isolation management device, a security resource pool and a micro-isolation terminal agent installed on a host of a service system. The micro-isolation terminal agent monitors the risk state of the host, obtains risk monitoring information and reports the risk monitoring information to the micro-isolation managementequipment; the micro-isolation management device reads the heartbeat information of the micro-isolation terminal agent, determines change information according to the risk monitoring information andthe heartbeat information, and reports the change information to the security resource pool; and the security resource pool adjusts a security protection strategy according to the change information and issues the security protection strategy to corresponding network security equipment. By applying the technical scheme provided by the embodiment of the invention, the network security device and the micro-isolation terminal in the host work cooperatively, and security protection can be effectively carried out on the host. The invention further discloses a safety protection method, micro-isolation management equipment and a computer readable storage medium which have corresponding technical effects.
Owner:SANGFOR TECH INC
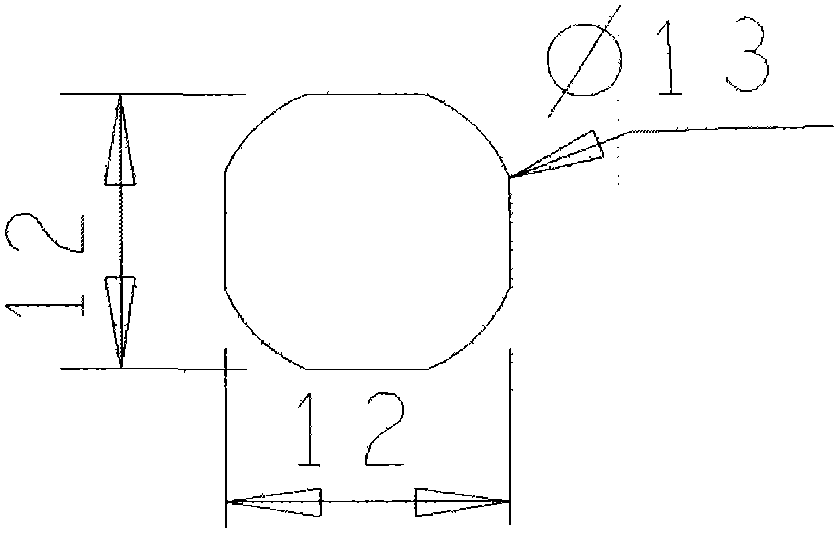
Miniature missile-borne data recording device
InactiveCN103500078AStrong resistance to high overloadSmall installation volumeInput/output to record carriersVIT signalsMissile
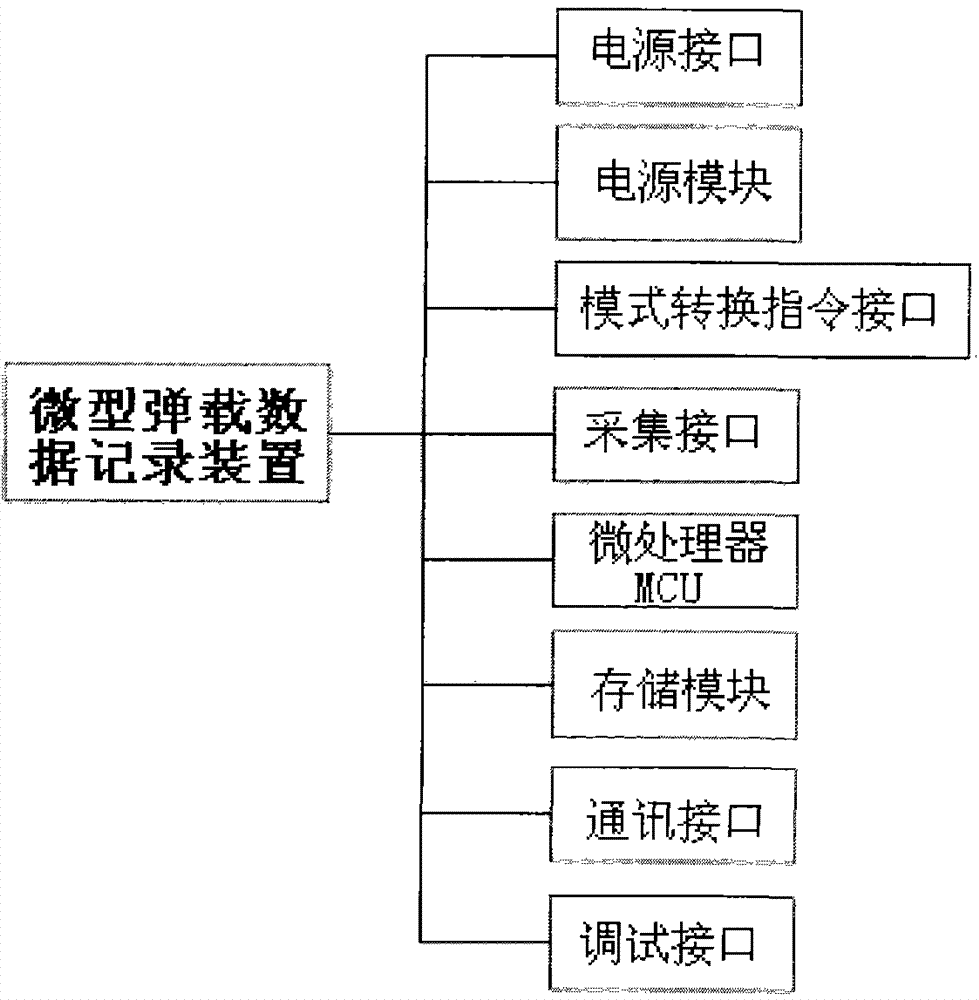
The invention belongs to the technical field of missile-borne data recording, and particularly relates to a miniature missile-borne data recording device. The miniature missile-borne data recording device is used for dynamically collecting and storing data through a platform in real time. A route of serial signal and multiple routes of digital or analog signals can be recorded through the recording device. The miniature missile-borne data recording device has the advantages of being very small in installation size, low in power consumption, low in cost, high in sampling rate, high in accuracy, capable of being repeatedly used and the like. The miniature missile-borne data recording device isolates a channel which receives data sampling instructions from a channel which receives upper computer data processing instructions through a mode conversion instruction interface, and therefore effective safety protectiveness can be provided, and abnormal conditions are avoided. Through the structural design of the technical scheme, the size of the appearance of the miniature missile-borne data recording device can be reduced to be 12*12*3.7(L*W*H)mm, the diagonal diameter of the device is 13mm, and the miniature missile-borne data recording device can be packaged through the packaging technology to form a module with the diameter of 15mm and the thickness of 6mm.
Owner:邓宏彬
Multi-defense wireless network security protection system and method
ActiveCN106792684ASafe and fast non-aware authenticationReduce the impactSecurity arrangementAddress Resolution ProtocolSecurity authentication
The invention discloses a multi-defense wireless network security protection system and method. The wireless network security protection system comprises a security authentication system, a wireless intrusion protection module, an ARP (Address Resolution Protocol) protection module and a data transmission monitoring module, wherein the security authentication system comprises a DHCP (Dynamic Host Configuration Protocol) server, an MAC (Media Access Control) address authentication system and a portal authentication system. Through adoption of the security protection system, on the three aspects of wireless authentication security, wireless security protection and cable network security, effective and comprehensive security protection is performed on a wireless network system from a plurality of angles.
Owner:STATE GRID INFORMATION & TELECOMM BRANCH +1
Method and system for processing user information
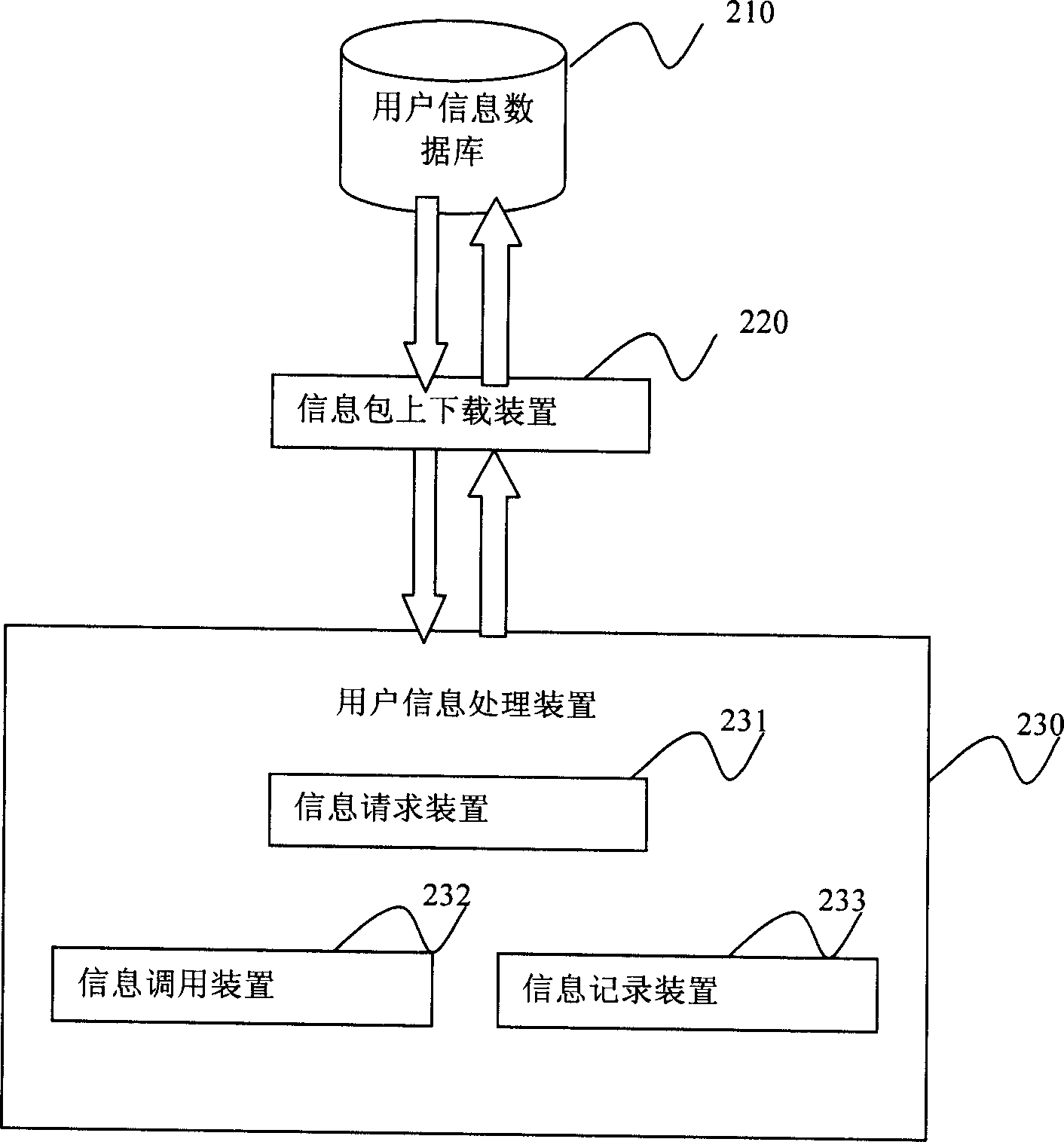
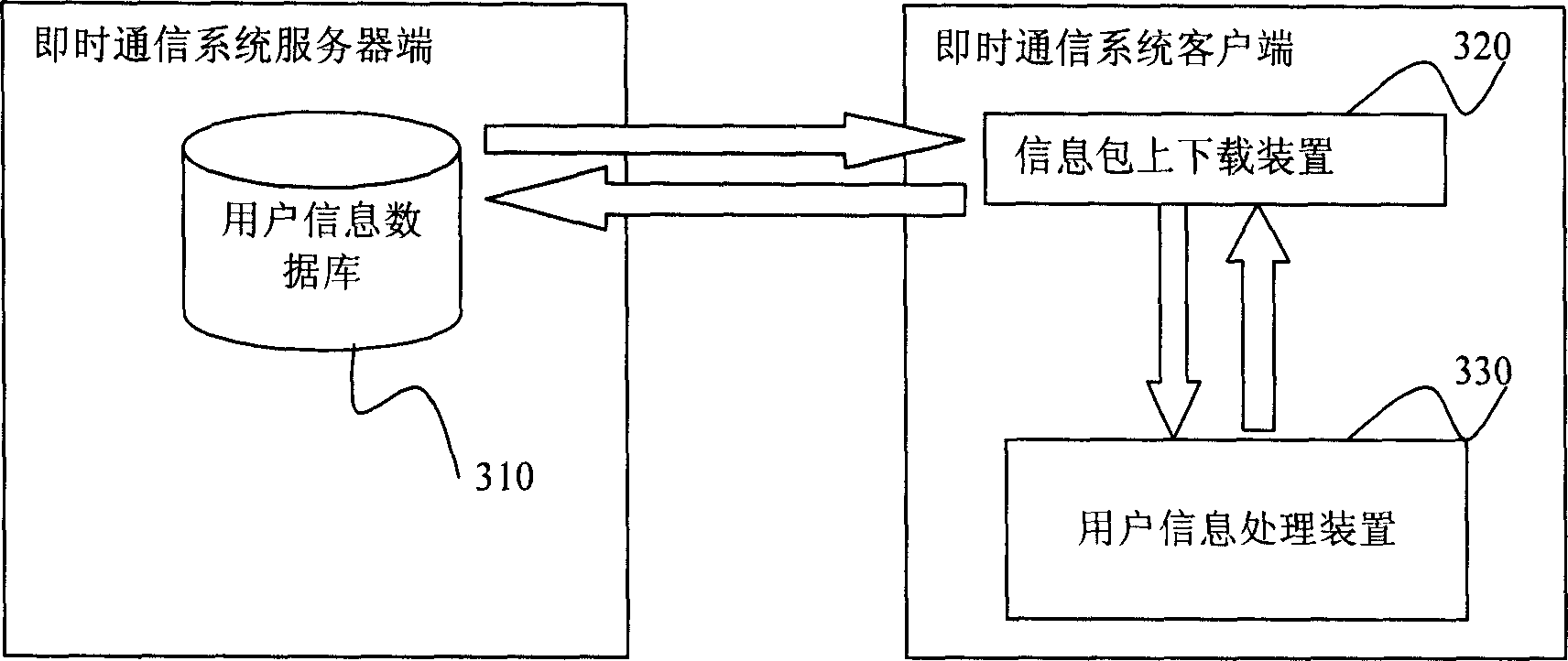
InactiveCN1841995AEffective security protectionEasy to operateSecuring communicationRelevant informationClient-side
The invention relates to a method for processing user information in an information mutual system which at east comprises a server end and a custom end. It comprises the following steps: a. loading and decoding the information package after successfully pleasing to register checking; b. calling for the user relative information preserved in user's information package; c. preserving the relative information during the user server course into the information package; d. when the user pleases to exit, encoding the information package and transmitting it to the user information database of the information package storage. The system comprises: a user information database used to store the information package of the user relative information, an information package transmitting device and a user information processor used to processing the user information.
Owner:TENCENT TECH (SHENZHEN) CO LTD
Trusted computing system and security protection system
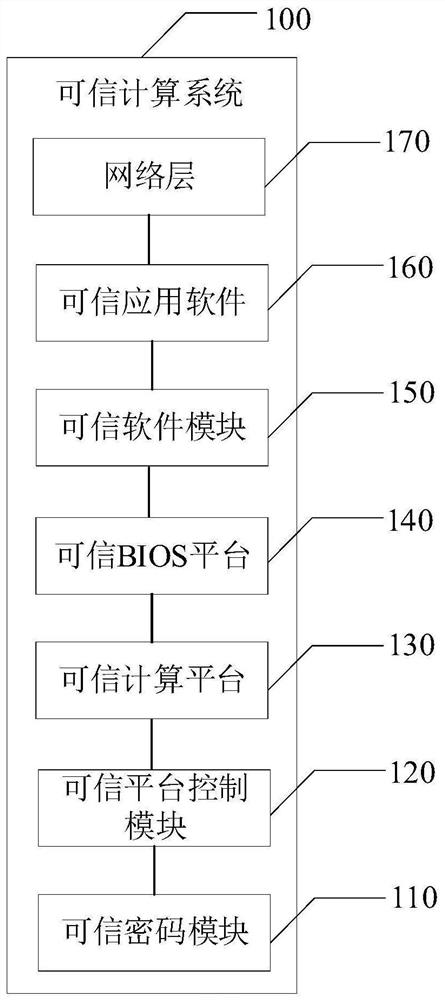
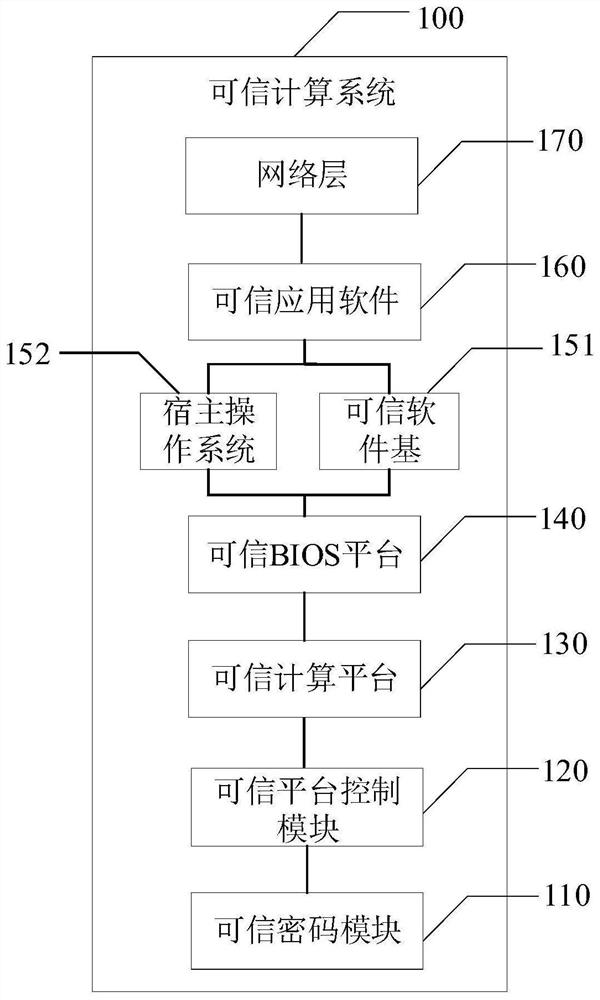
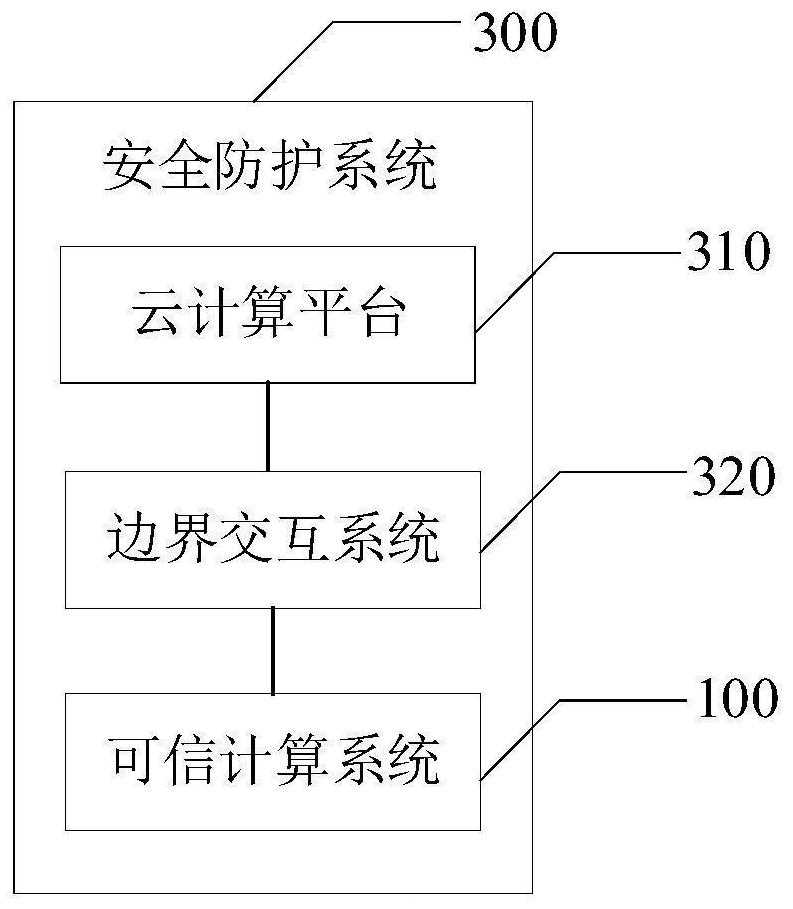
InactiveCN112784258AEffective security protectionPlatform integrity maintainancePasswordTrusted Computing
The invention provides a trusted computing system and a security protection system. A trusted cryptographic module in the trusted computing system provides cryptographic operation support for a trusted computing platform; the trusted platform control module adds a trust root on the basis of the trusted password module and combines a password with control. The trusted computing platform performs trusted measurement on each node of the trusted computing system; the trusted BIOS platform provides support for trust chain transmission of the trusted computing platform; the trusted software module performs trusted verification on each node of the trusted computing system and monitors the trusted computing system. The trusted application software is used as a system call between the trusted computing platform and the trusted cryptographic module; and the network layer performs strategy verification on the trusted application software, the trusted computing platform and the trusted cryptographic module. Through the trusted computing system with coexistence of operation and protection under the control of the security trusted strategy, security protection can be effectively provided for the network space in the big data environment.
Owner:国网宁夏电力有限公司信息通信公司
Battery charging protection circuit
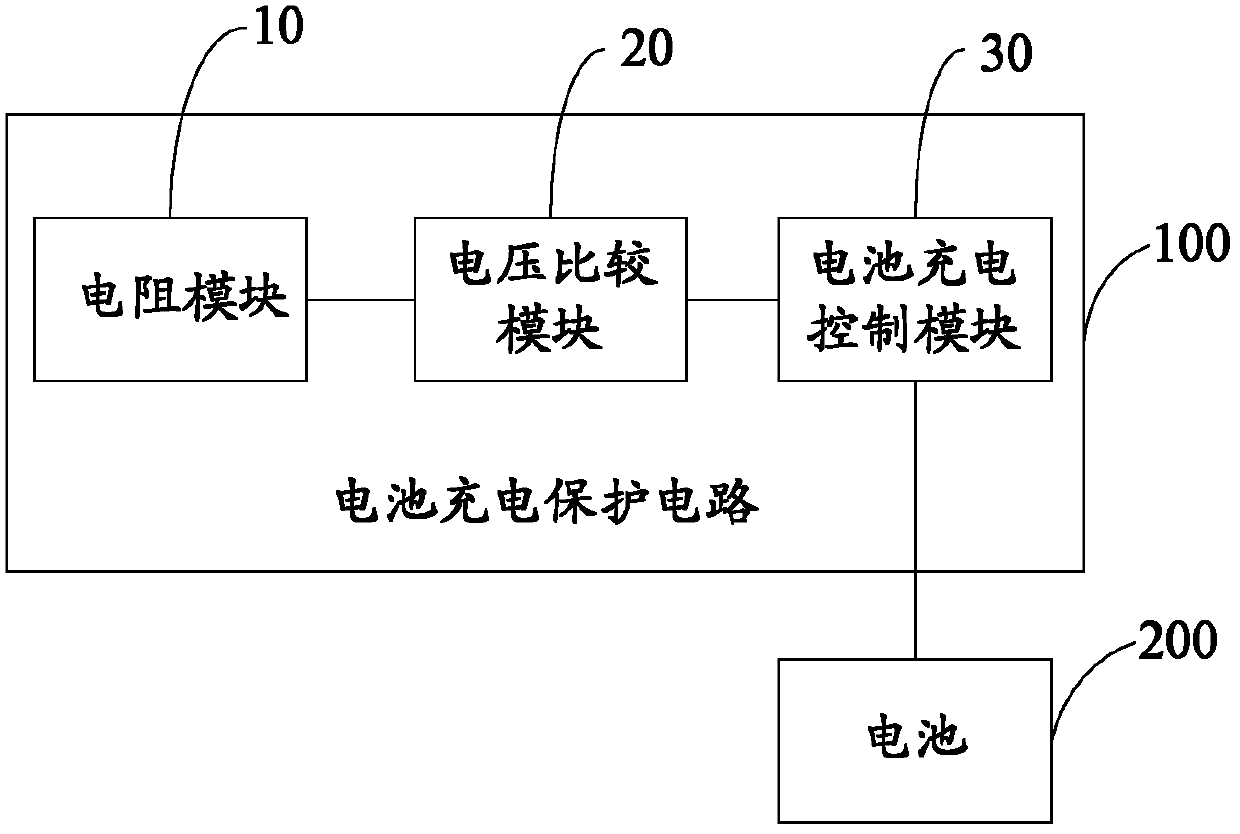
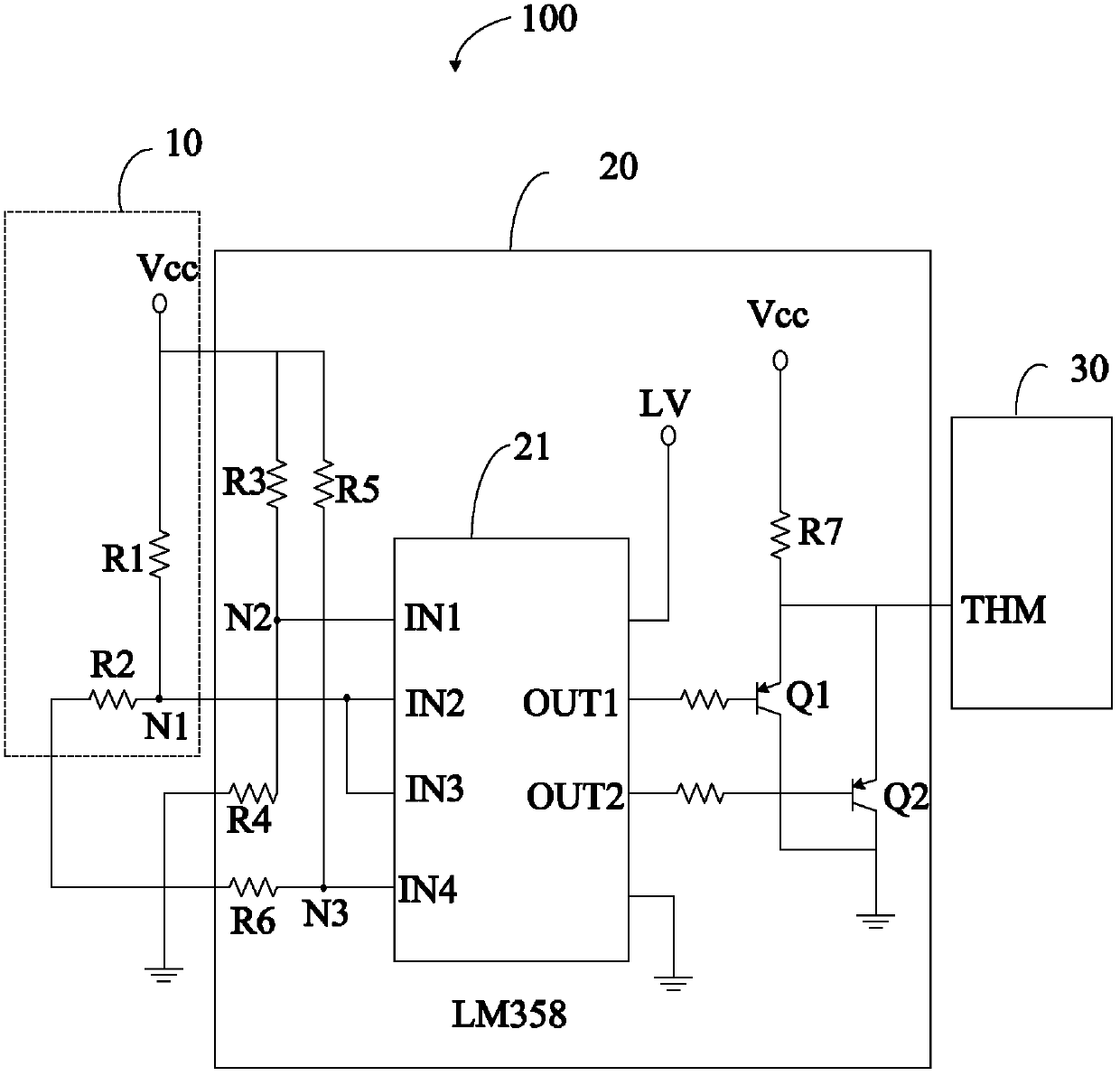
InactiveCN103311898ADetect temperatureEffective security protectionBatteries circuit arrangementsEmergency protective circuit arrangementsLower limitElectrical resistance and conductance
Owner:HONG FU JIN PRECISION IND (SHENZHEN) CO LTD +1
Drug sterile freeze-drying isolator system for laboratory
InactiveCN106016978ASimple structureImprove cleanlinessMechanical apparatusDrying solid materials without heatSterile environmentFreeze-drying
The invention discloses a drug sterile freeze-drying isolator system for a laboratory, and belongs to the field of drug making equipment. The system comprises a dry heat sterilizer system, a freeze dryer system and a sterile isolator system. The dry heat sterilizer system is connected with the sterile isolator system through a dry heat sterilizer seal connection system; the freeze dryer system is connected with the sterile isolator system through a freeze dryer seal connection system; and the drug sterile freeze-drying isolator system is simple in structure, high in cleanliness, good in sealing performance, capable of providing safe and reliable sterile environment for a freeze-drying experiment of novel sterile drugs and also capable of effectively avoiding the harm of toxic drugs to experimenters during toxic drug experimenting, and provides the effective safe protection for health of the experimenters, and meanwhile the system reduces the requirement of the equipment background environment, the running cost is saved, and the higher practicability is achieved.
Owner:SHINVA MEDICAL INSTR CO LTD
Batch machining device and technology for reinforcing-steel-bar straight threads
ActiveCN104786107ASimple structureReasonable designOther manufacturing equipments/toolsMetal working apparatusRebarScrew thread
The invention discloses a batch machining device and technology for reinforcing-steel-bar straight threads. The machining device comprises a left reinforcing-steel-bar straight thread machining device body, a right reinforcing-steel-bar straight thread machining device body, a left protective shed, a right protective shed and an automatic conveying platform for conveying to-be-machined reinforcing steel bars. The left reinforcing-steel-bar straight thread machining device body and the right reinforcing-steel-bar straight thread machining device body are used for machining the two ends of the to-be-machined reinforcing steel bars respectively. The automatic conveying platform is located between the two reinforcing-steel-bar straight thread machining device bodies. Each reinforcing-steel-bar straight thread machining device body comprises a reinforcing-steel-bar cutting device for cutting the to-be-machined reinforcing steel bars and a straight-thread threading machine for carrying out threading on the to-be-machined reinforcing steel bars. The automatic conveying platform comprises a reinforcing-steel-bar containing frame, a first transverse conveying frame, a threading machining frame and a reinforcing-steel-bar longitudinal movement mechanism. The machining technology includes the steps of 1, reinforcing-steel-bar lifting; 2, reinforcing-steel-bar cutting; 3, reinforcing-steel-bar secondary forward moving; 4, reinforcing-steel-bar threading; 5, reinforcing-steel-bar third-time forward moving. The machining device and technology are reasonable in design, easy and convenient to machine, manufacture, use and operate and good in use effect; the reinforcing-steel-bar straight thread batch machining process can be easily, conveniently and rapidly completed.
Owner:陕西华鑫鼎业建筑物资有限公司
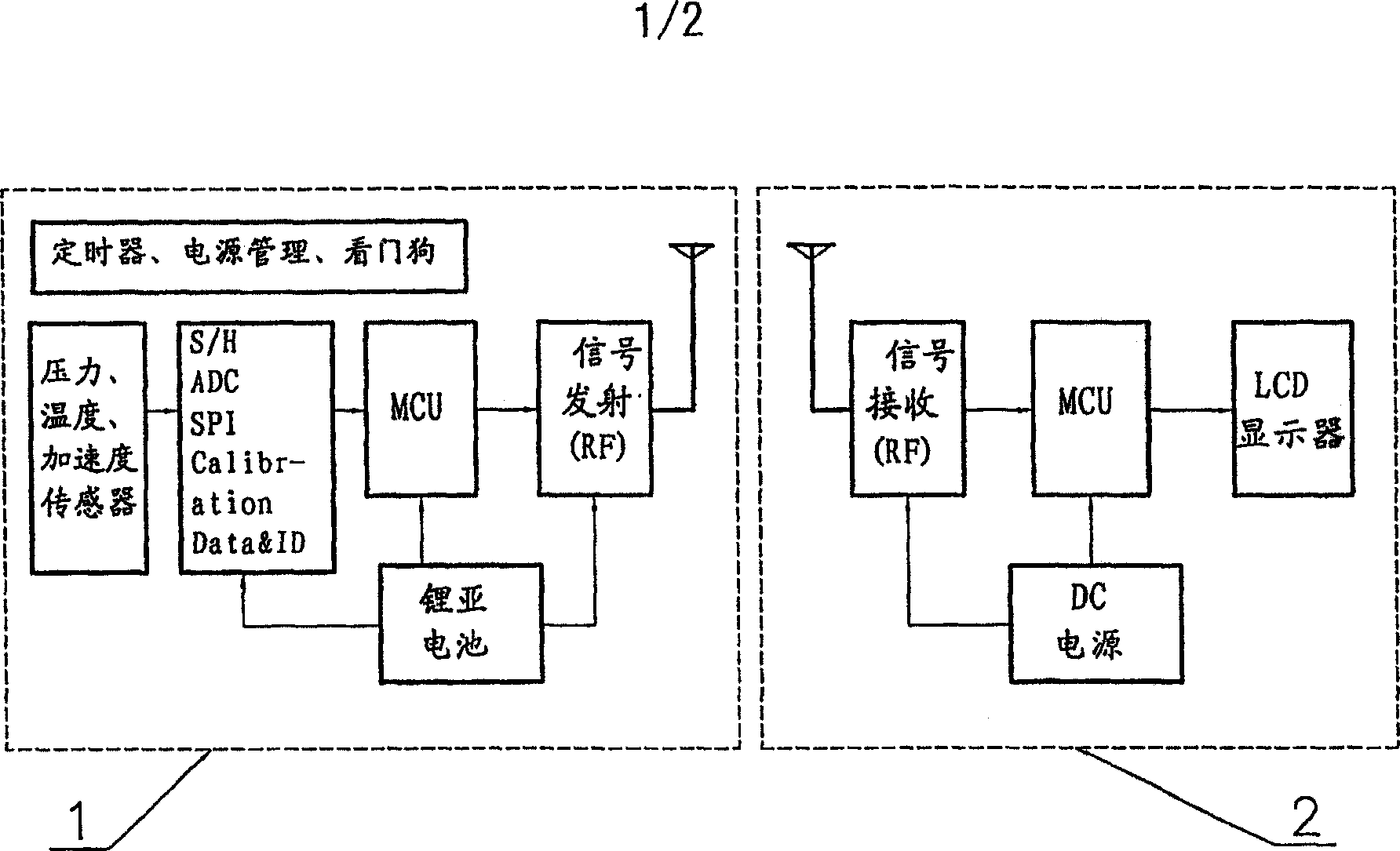
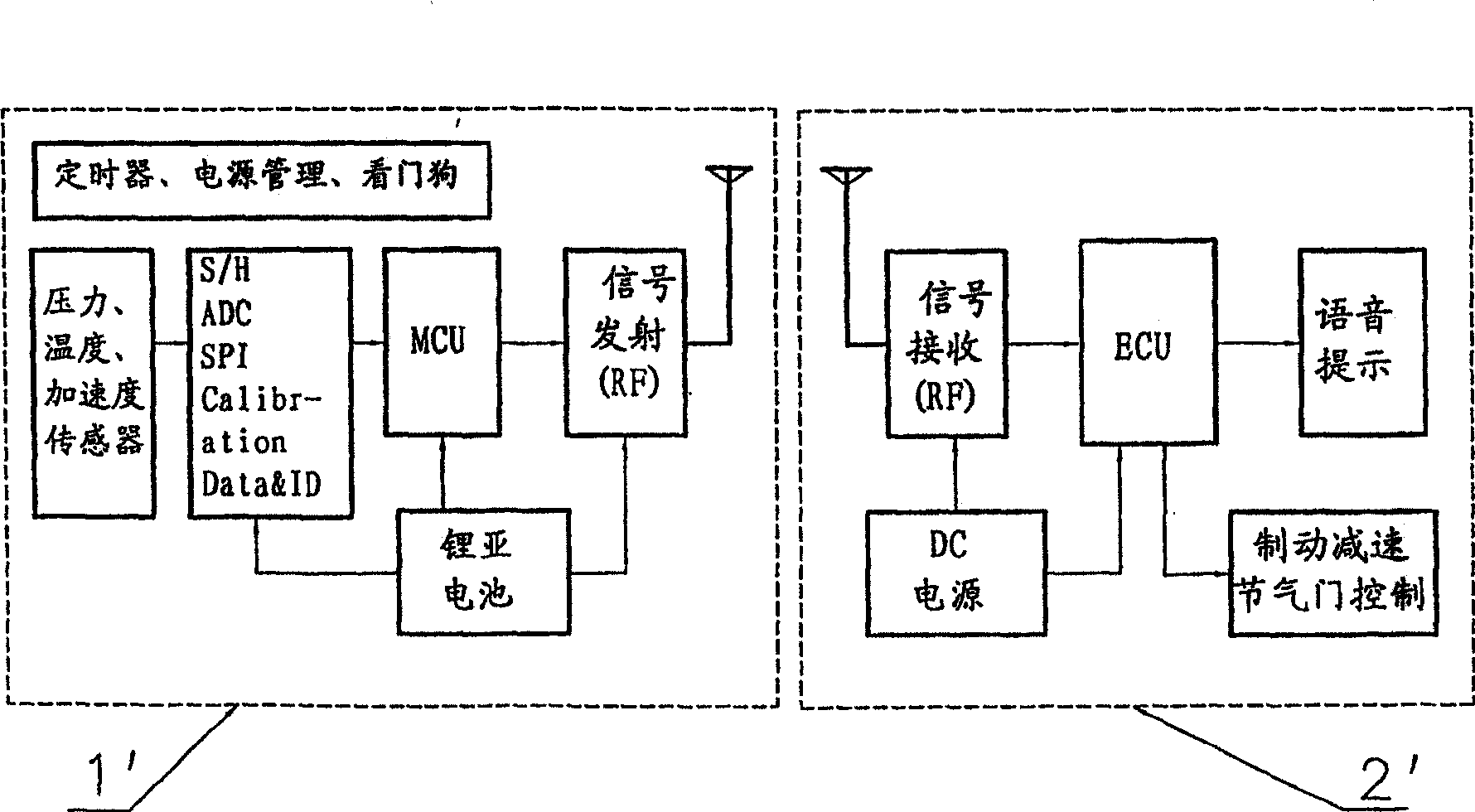
Tyre monitoring system
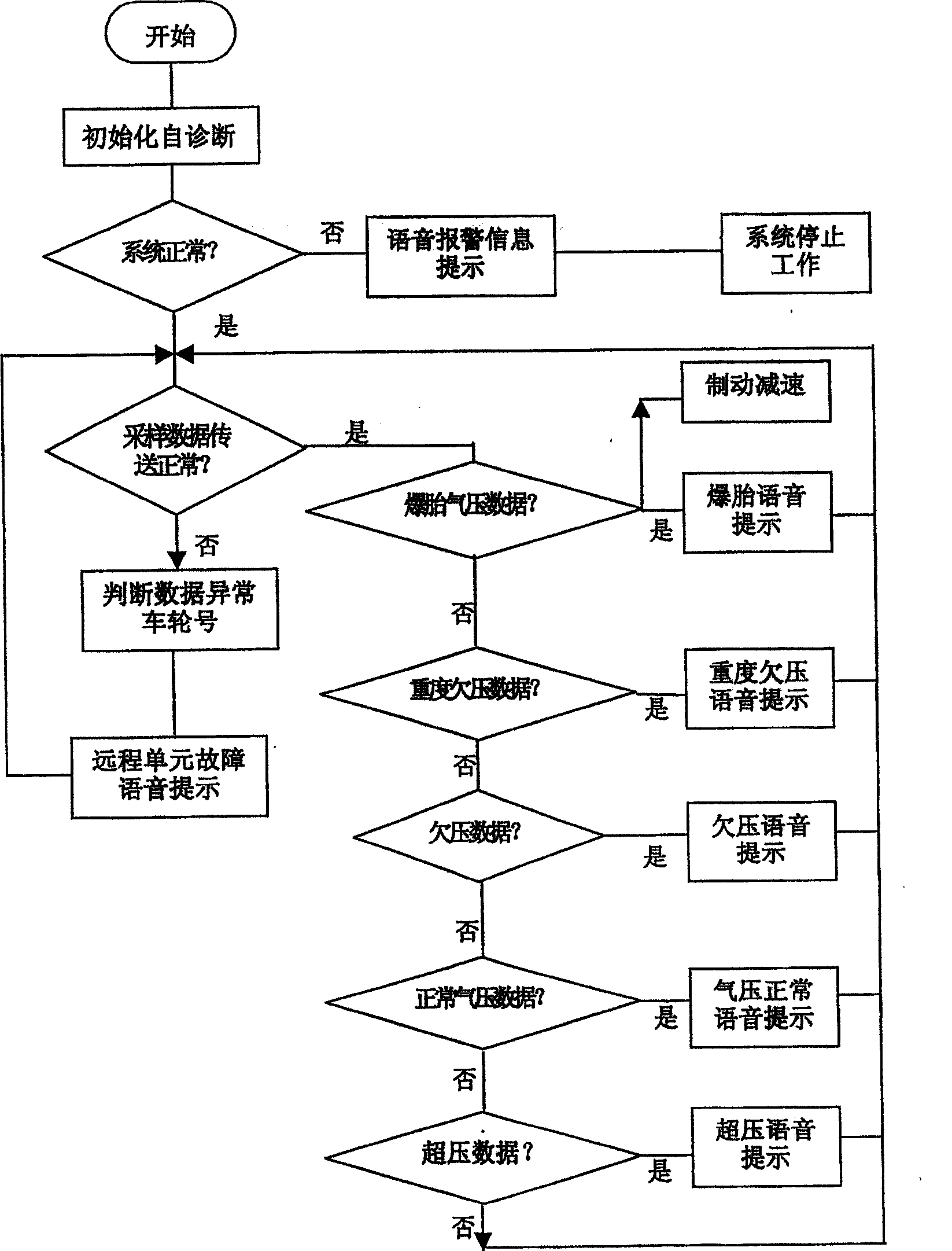
ActiveCN100463811CLighten traffic loadReduce distractionsTyre measurementsMonitoring systemEngineering
A system for monitoring the tire comprises a long-distance tire-detecting unit mounted inside the tire, a center processing unit, a voice alerting unit and a braking mechanism. The long-distance tire-detecting unit detects and samples the pressure and temperature of the tire, then produces a sampled signal of tire condition and transmits the signal to the CPU by wireless communication. The CPU receives and processes the sampled signal of tire condition, then produces a voice alerting instruction or a braking instruction. The voice alerting instruction is sent to the voice alerting unit, and the braking instruction is sent to the braking mechanism. The voice alerting unit is used to receive the voice alerting instruction and output the voice alerting information. The braking mechanism is used to receive the braking instruction and execute the braking behavior. Thus this system can provide effective safeguard protection in the case of accident air leakage and burst of the tire.
Owner:ZHEJIANG GEELY HLDG GRP CO LTD
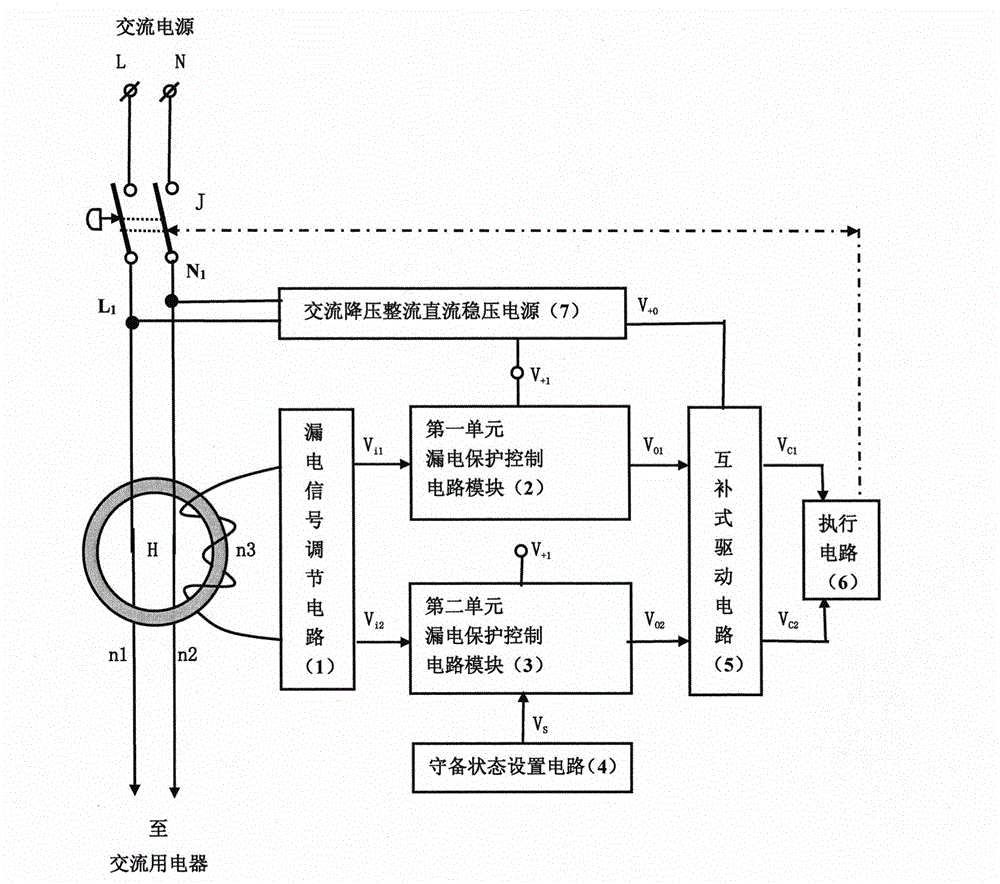
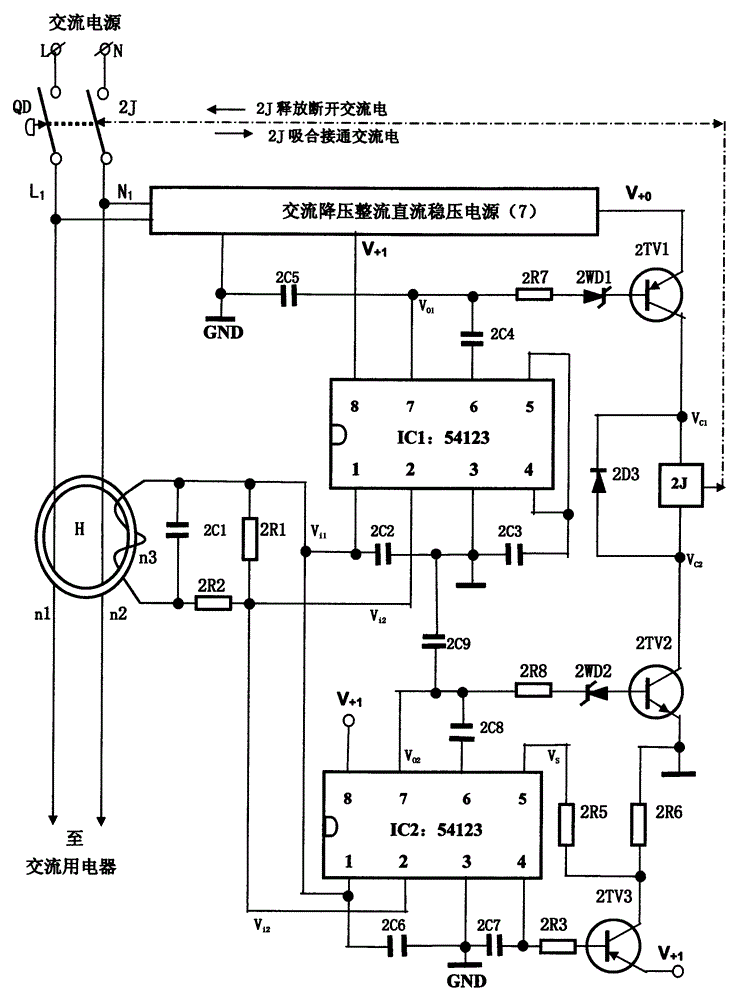
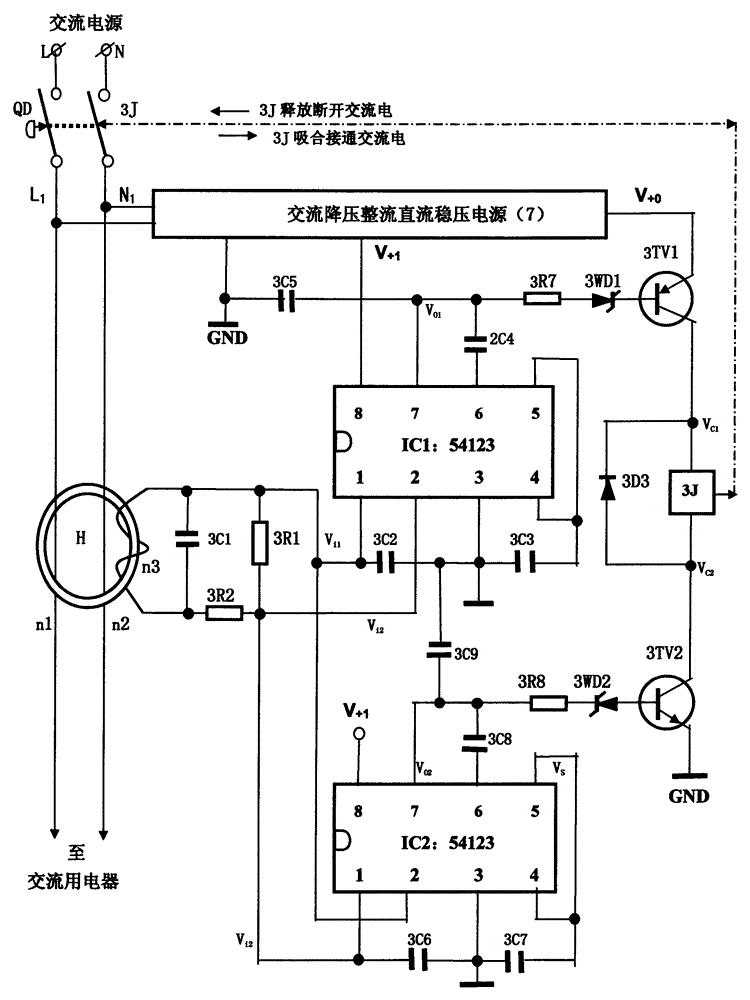
Very effective leakage protector
InactiveCN104993451AAvoiding Failed False Guaranteed Operational StatusImprove protectionEmergency protective arrangements for automatic disconnectionComputer moduleEngineering
The invention relates to a very effective leakage protector. The technical scheme adopted by the invention is that the inputs terminals of two or more than two electric leakage protection control circuit module detect and regulate the electric leakage signal in parallel, the output terminal performs series control driving and executes the circuit method to control AC power supply of the AC electric usage device; the electric leakage signal regulation circuit input terminal is connected to the secondary coil of the zero sequence current mutual inductor; the two parallel or more than two electric leakage protection control circuit module is powered by DC voltage V+1; the DC voltage V+0 supplies power to drive and the execution circuit. The beneficial effects of the invention is that the very efficient leakage protector not only can perform safety protection control on the electric leakage or electric shocking of the AC electric device during an normal operation, but also can enforce the driving execution circuit to cut off the AC power supply of the AC electric appliance, so that the AC electric appliance and the electric user are safe and the personal safety can be effectively protected under abnormal condition.
Owner:刘圣平
Security device for preventing unauthorized removal of merchandise
ActiveCN1801229AEffective security protectionOvercome problemsStampsLocks for portable objectsEngineeringPurchasing
A security tag assembly and security system associated therewith prevent the unauthorized removal of merchandise from a given area, such as a retail establishment. The security tag assembly comprises a base and at least one attachment member removably connected in an operative position on the merchandise being protected. A locking assembly including a locking member is structured to restrict detachment of the attachment member and is forcibly disposed out of movement restricting relation to said connector member when the base and the attachment member are separated. A detachment assembly and a data registering processor may include a two-way communication link which facilitates processing of the merchandise data disposed on the security tag assembly, such that the purchasing of the merchandise and the removal of the security tag assembly can be effectively accomplished without jeopardizing the security of the merchandise being sold.
Owner:BRAEBURN ASSET HLDG +1
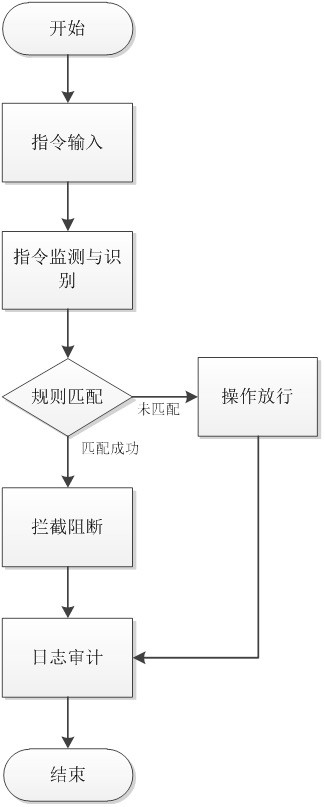
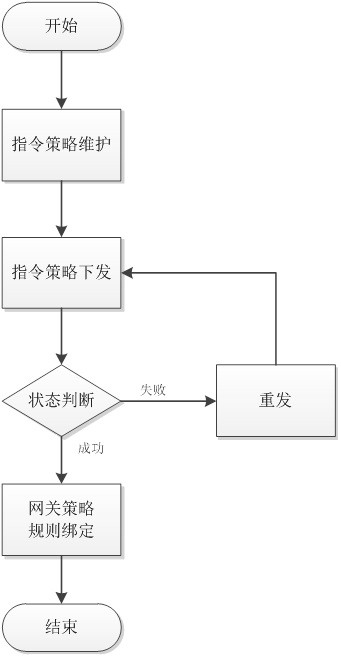
Security operation and maintenance instruction blocking device and method based on industrial control system
InactiveCN113311809AEasy to identifyImprove the effect of early warningProgramme controlElectric testing/monitoringComputer scienceIndustrial control system
The invention relates to the field of industrial control system security defense, in particular to a security operation and maintenance instruction blocking device and method based on an industrial control system. The blocking method comprises the steps: an operation and maintenance terminal obtains an industrial control operation and maintenance instruction input by a user; an operation and maintenance gateway performs rule matching on the encrypted operation and maintenance instruction content and an instruction strategy locally bound to the operation and maintenance gateway; a matching result is output, and if the operation and maintenance instruction content is successfully matched with the instruction strategy, intercepting and blocking are carried out by the operation and maintenance gateway; if the matching is not successful, operation is carried out, and interception is not carried out; and the operation and maintenance gateway records a log and sends the log to an operation and maintenance terminal background for log auditing. According to the invention, the blocking of a risk instruction is realized, and the occurrence of equipment faults caused by misoperation of operation and maintenance personnel is prevented.
Owner:苗叶
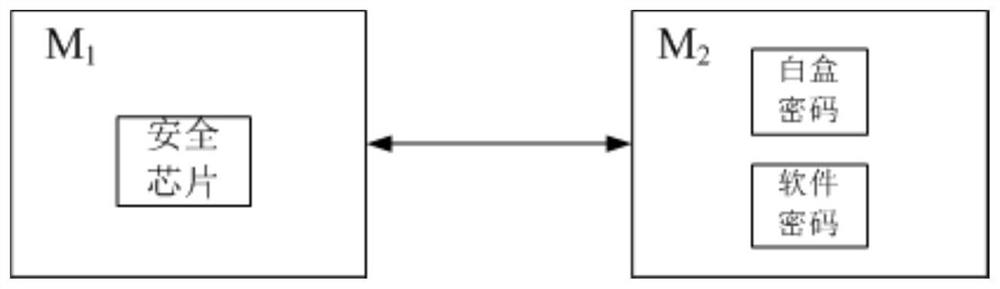
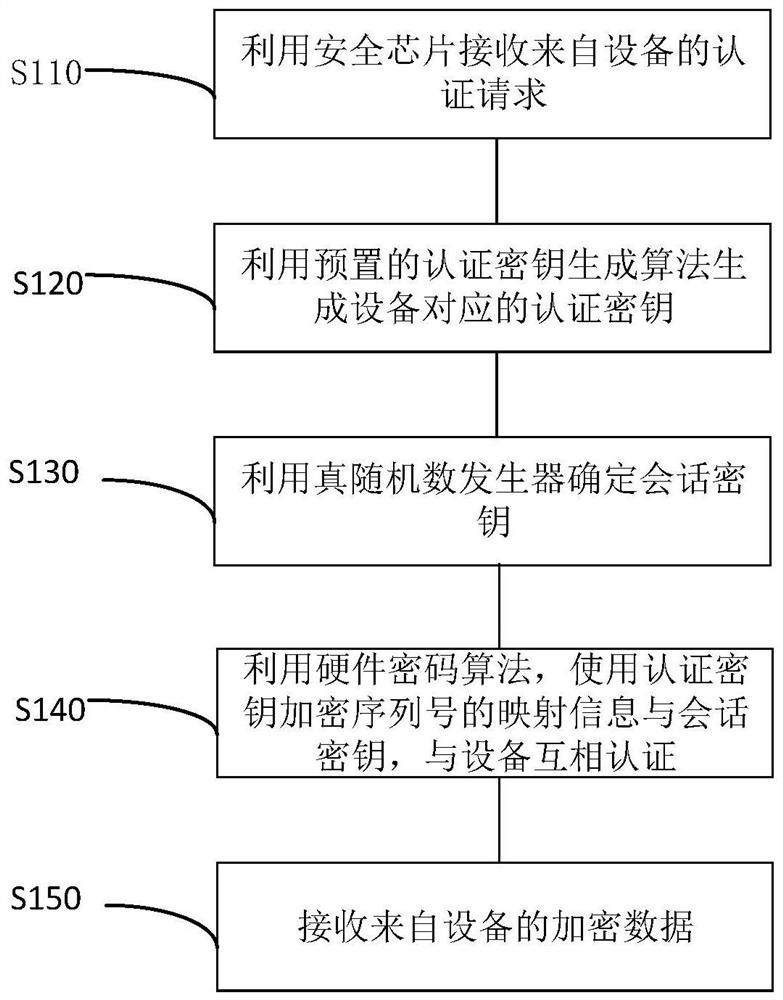
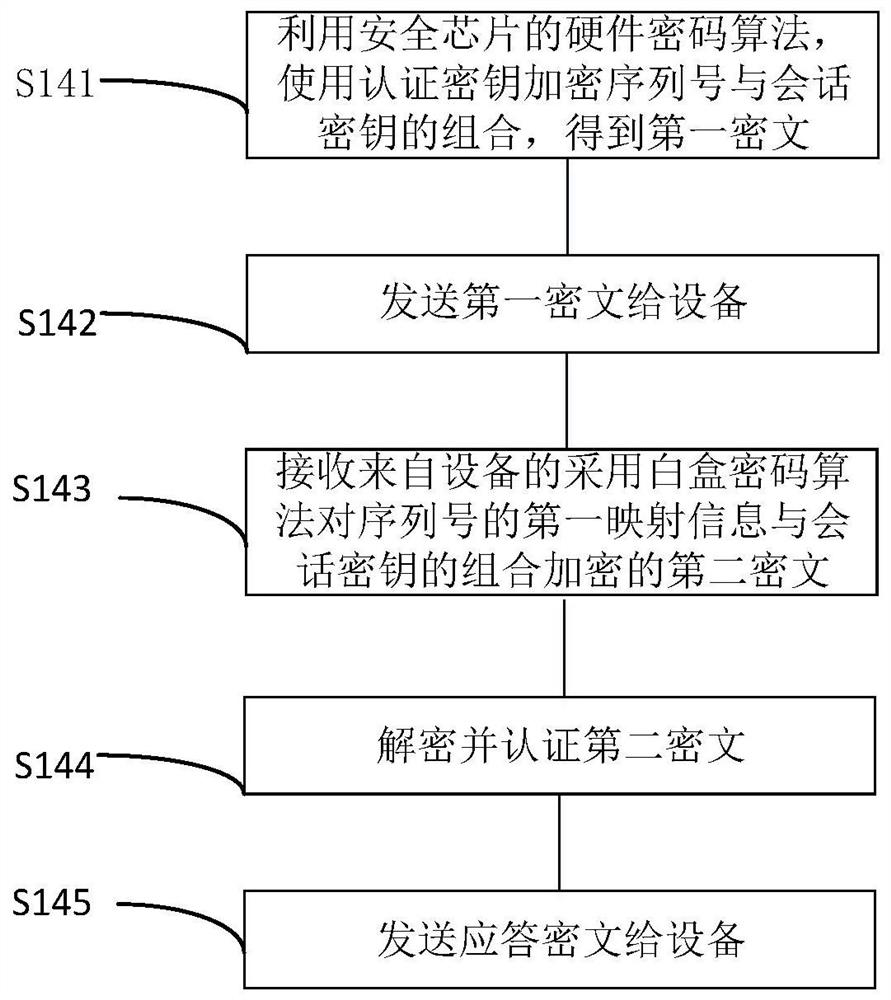
Internet of things, identity authentication and secret communication method, chip, equipment and medium
PendingCN113132087ASolve the initialization problemShorten the development cycleKey distribution for secure communicationInstrumentsInternet privacyThe Internet
The invention provides an internet of things, an identity authentication and secret communication method, a security chip, equipment and a medium. The Internet of Things comprises at least one first device and at least one second device, and a security chip is configured in the first device; a white-box cryptographic algorithm is configured in the second equipment; wherein the first equipment performs identity authentication and secret communication with the second equipment through the security chip.
Owner:NATIONZ TECH INC
Novel safety device for drilling building materials
InactiveCN106426009AImprove performanceAvoid damage to building materialsPortable power-driven toolsPortable drilling machinesBuilding materialArchitectural engineering
Owner:CHENGDU XUNDE SCI & TECH
Climbing system for power transmission line iron tower
The invention discloses a climbing system for a power transmission line iron tower. The system comprises a power transmission line iron tower climbing assistant (80) and a guide rail (90), wherein thepower transmission line iron tower climbing assistant (80) comprises an upper body (10) and a lower body (20), and the upper body (10) comprises a driving mechanism (30), a transmission belt mechanism (40) and a pressing mechanism (50); the guide rail (90) is inserted into a groove (12) defined by a transmission belt (45), a first lower cross beam (21) and a second lower cross beam (22); the pressing mechanism (50) can press the belt surface of the transmission belt (45) against the working surface (91) of the guide rail, and the climbing system for the power transmission line iron tower canmove along the guide rail (90) by operation of the transmission belt mechanism (40). The climbing system for the power transmission line iron tower can provide constant lifting force for workers who need to climb the tower, so that climbing is more flexible and comfortable, and the workers can conveniently climb up and down the iron tower.
Owner:BEIJING GUOWANG FUDA SCI & TECH DEV
Three-stage brushless micro gas turbine electricity generation grid-connecting device and grid connecting method
InactiveCN101667736AReduce shockImprove protectionSingle network parallel feeding arrangementsControl signalTransformer
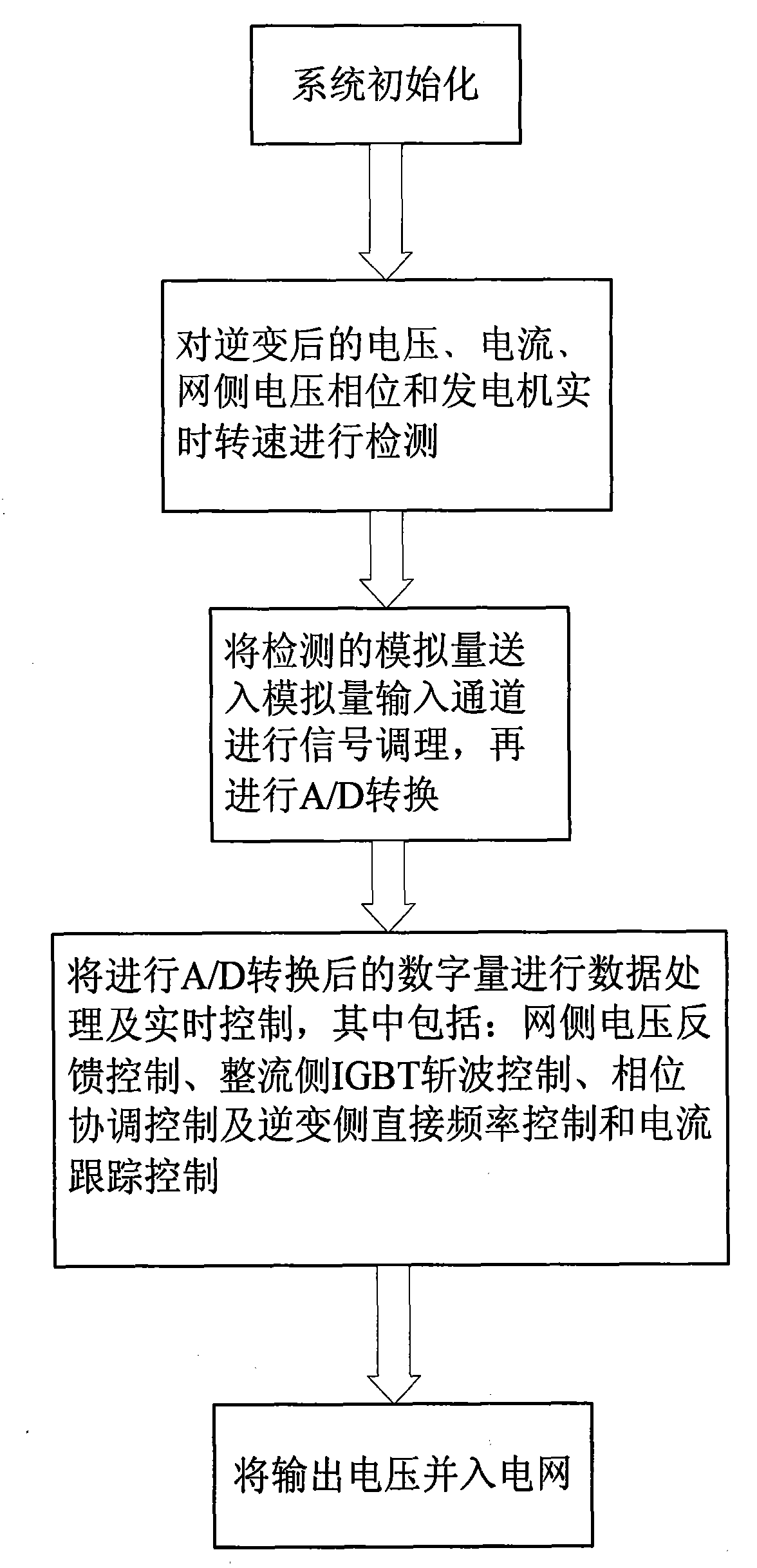
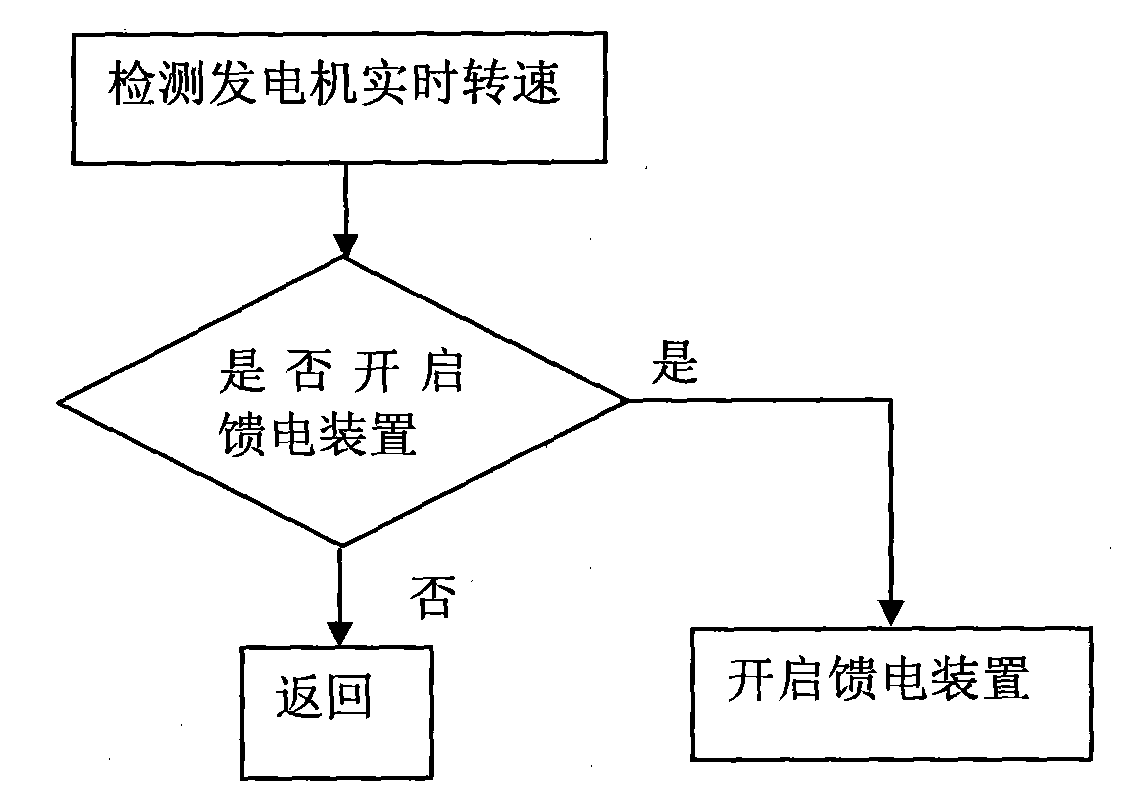
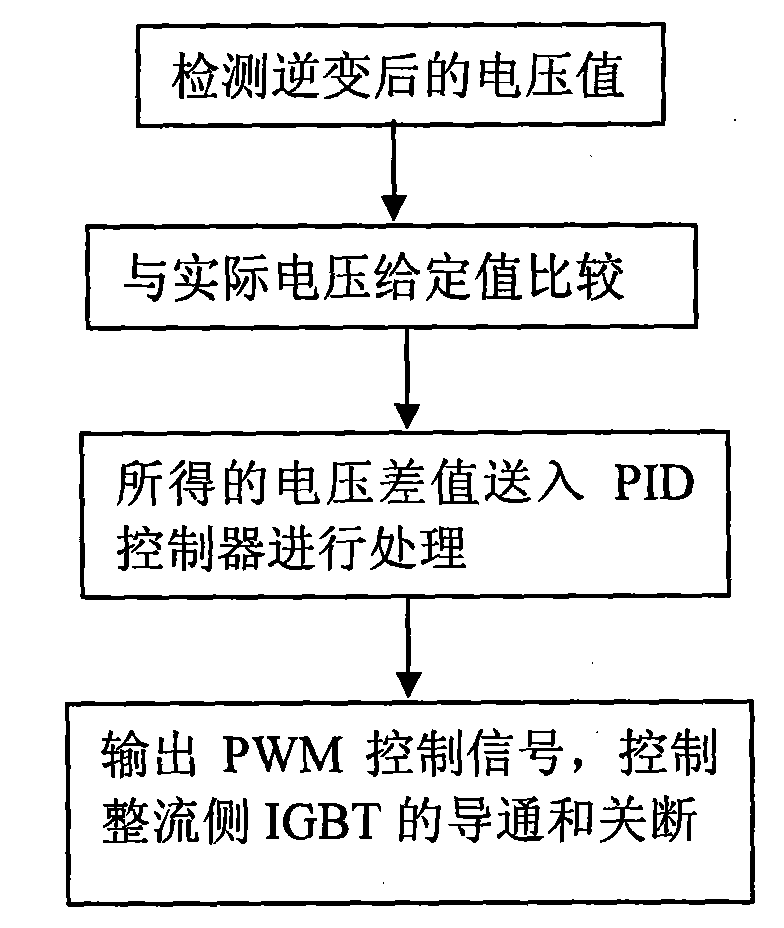
The invention relates to a three-stage brushless micro gas turbine electricity generation grid-connecting device and a grid connecting method, belonging to the technical field of gas turbine electricity generation. The invention can improve the grid connecting speed and electricity generation quality and effectively reduce the impact on an electricity grid in grid connecting. The three-stage brushless micro gas turbine electricity generation grid-connecting device comprises a microprocessor; the output end of a micro gas turbine is connected with an IGBT chopper circuit via a rectifier circuitand a filter circuit, and the IGBT chopper circuit is connected with an inverter; a PWM output interface is connected with the IGBT chopper circuit and an enabling end of the inverter via an IGBT drive circuit, and an electricity grid feed control signal is connected with an power energy input port via a feed device; a detection device is connected with an A / D conversion module via an analog input channel; a phase coordination control signal is connected with a phase coordinator; and a voltage measuring transformator is connected with a phase-locked loop frequency multiplication circuit and acapture port via a shaping circuit, and the phase-locked frequency multiplication circuit is connected with an external interrupt pin of the microprocessor. The grid connecting method adopts grid side voltage feed control, rectification side IGBT chopping control, phase coordination control, inversion side direct frequency control and current tracking control.
Owner:NORTHEASTERN UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com