Security device for preventing unauthorized removal of merchandise
An unlicensed and commercial technology, applied in the field of security systems, can solve problems such as inability to fully exert its effectiveness, and achieve the effect of effective structure, simple structure and easy connection
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
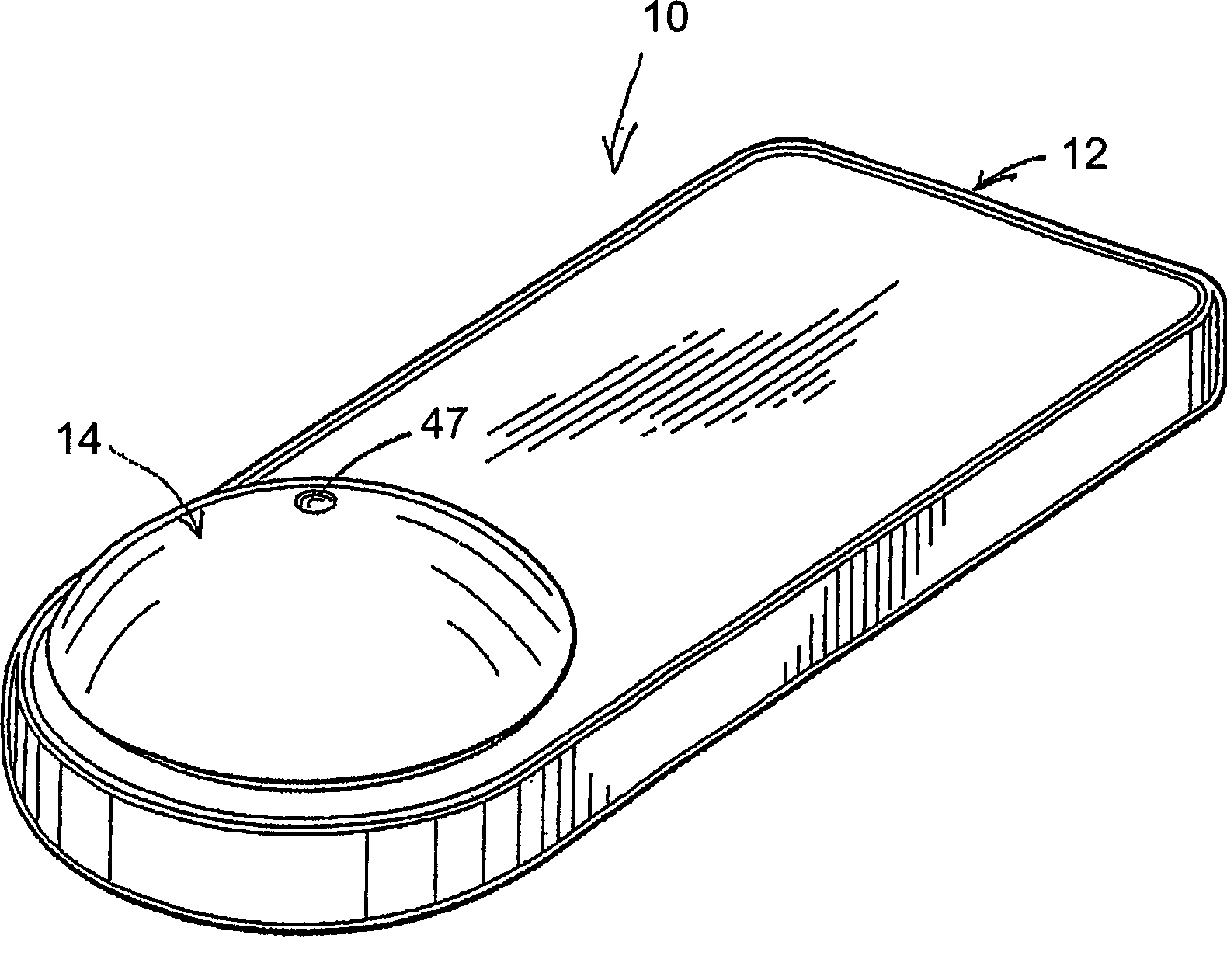
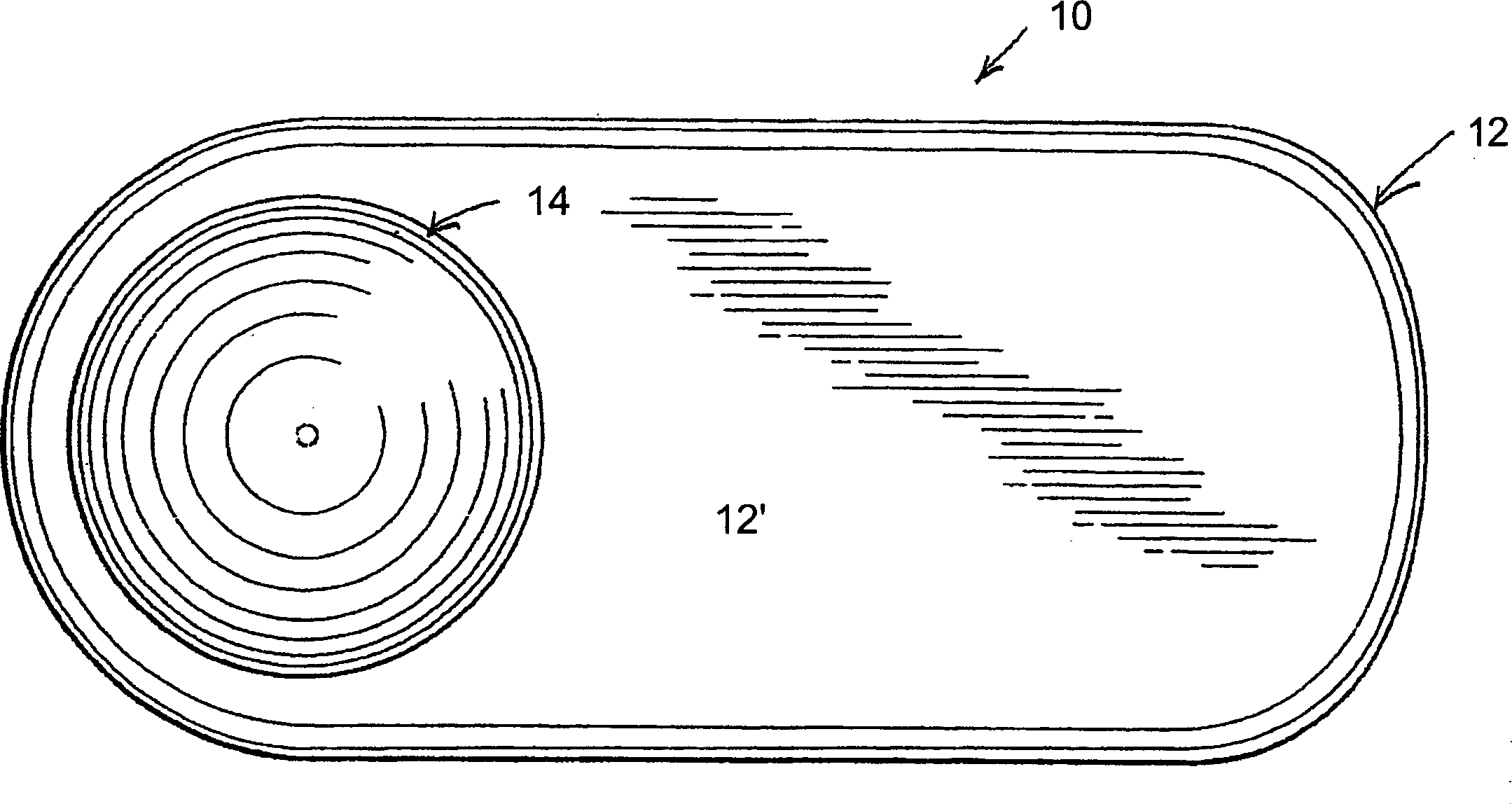
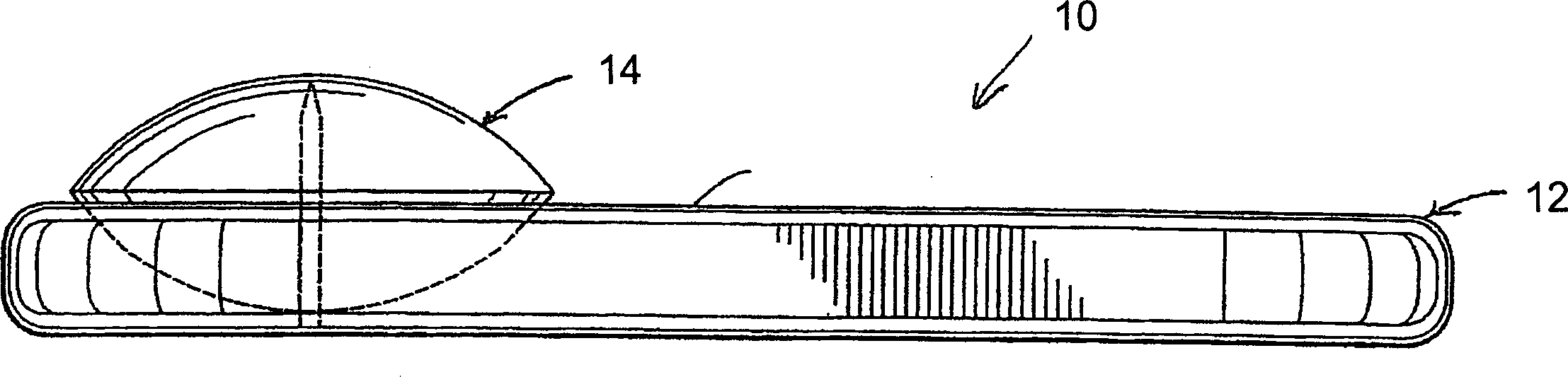
[0046] As shown in the drawings, the present invention is directed to a security tag assembly generally indicated at 10 and comprising at least one base 12 and at least one attachment 14 . However, multiple bases 12 and multiple attachments 14 are typically used in practice of the present invention, such as when multiple different products are to be protected and / or monitored. Additionally, the security tag assembly 10 is of the type configured to be removably secured to various types of merchandise 18 to prevent unauthorized removal of the merchandise 18 from certain areas and locations. Typical applications for the security assembly 10 of the present invention include attaching a base 12 and any of a plurality of attachments 14 to an article 18 to be secured. In this way, security tag assembly 10 can be quickly and easily removed from its working location by authorized individuals using approved techniques and / or hardware. On the contrary, it is very difficult for an unauth...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com