A smart password network real-name identity management method and platform
A smart password and identity management technology, which is applied in the field of smart password network real-name system identity management and platform, can solve problems such as the difficulty of police investigation and sentencing, and achieve the effect of facilitating identity tracking
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
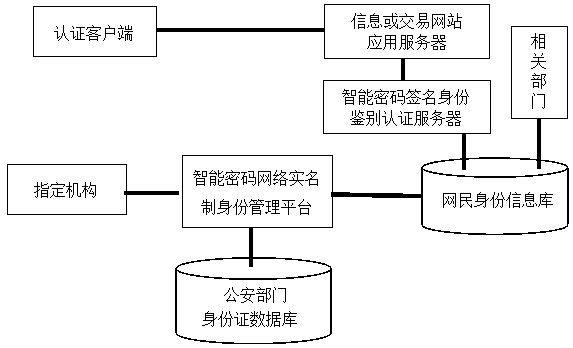
[0014] Described in this embodiment is a kind of smart password network real-name system identity management method and platform, said method platform includes: designated organization, netizen identity information database, relevant departments, ID database of public security department, information or transaction service website application server, Authentication client, smart password signature authentication authentication server, such as figure 1shown. The designated agency is the terminal of the management platform that verifies and records the real identity information of netizens before going online, applies for the issuance of online real-name ID cards, and includes changes in the identity information of netizens. The netizen identity information database includes the netizen's name, date of birth, gender, educational background, network real-name identity card number, home address, identity card number, fingerprint information and other personal information. Relevan...
Embodiment 2
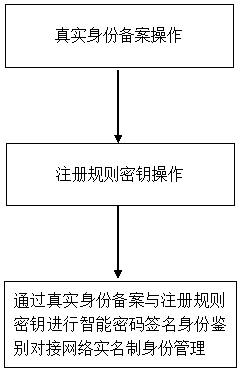
[0021] This embodiment is an improvement in the smart password network real-name system identity management method described in the first embodiment and the improvement in the platform through real identity filing and registration rule keys for intelligent password signature identity authentication docking network real-name system identity management steps, such as image 3 shown.
[0022] The sub-steps in the identity management steps of the real-name identity management step include:
[0023] The login authentication client enters the network real-name system ID card number or the user account or network name bound to the network real-name system ID card number, uses the rule key and the dynamic password of the smart password signer of the mobile phone to calculate through the rule key operation key and the rule key operation module The sub-step of sending the smart password for signature transformation to the authentication server, and simultaneously transmitting the smart ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com