Method and device for obtaining network security data
A network security and acquisition method technology, which is applied in the field of network security data acquisition methods and devices, can solve the problems of inability to analyze vulnerabilities, increase the rate of missed loopholes, and low network security, so as to reduce the rate of missed loopholes and improve network security. safety effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
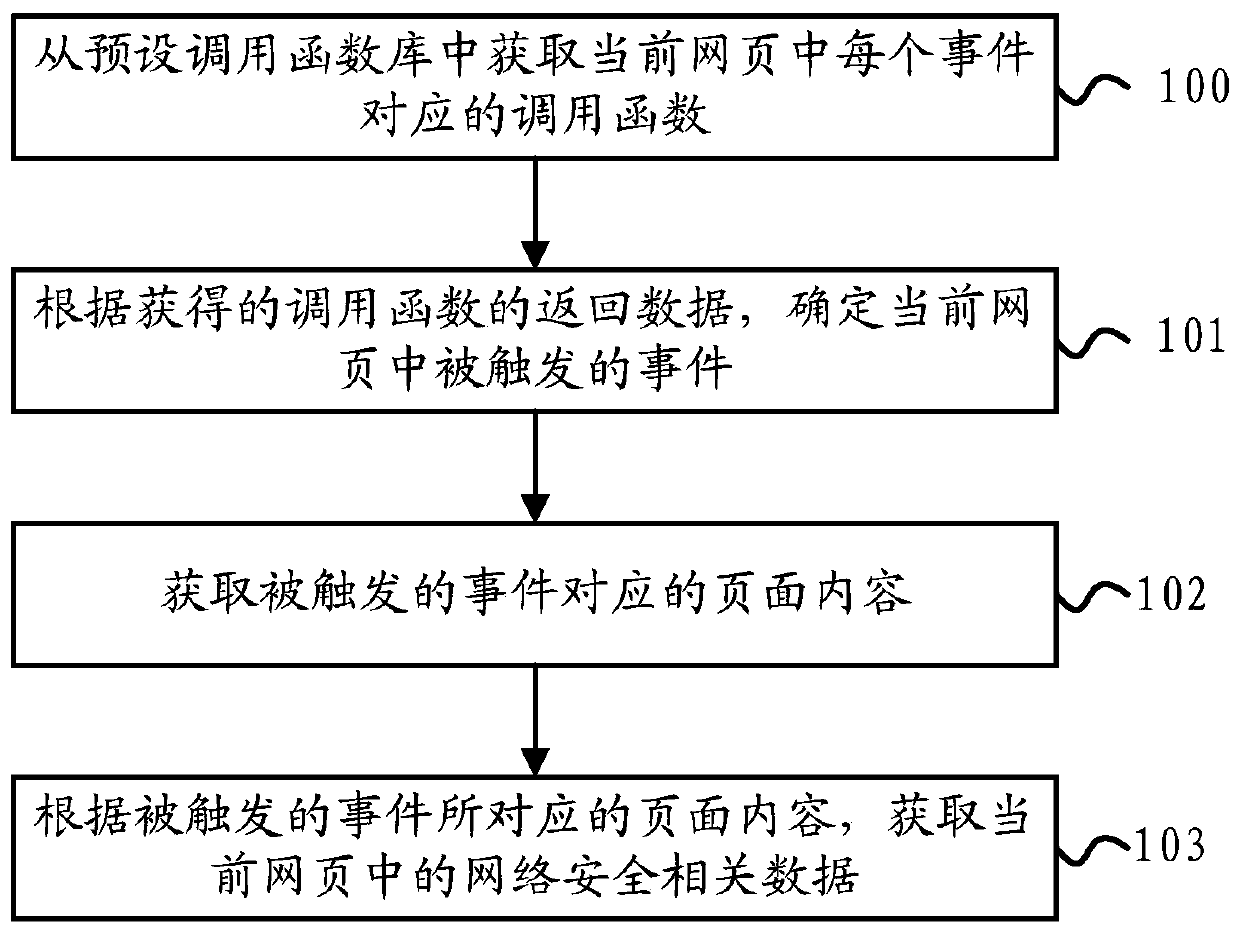
[0048] figure 1 It is a flow chart of Embodiment 1 of the network security data acquisition method of the embodiment of the present invention, as shown in figure 1 As shown, the method for obtaining network security data in the embodiment of the present invention may specifically include the following steps:
[0049] 100. Obtain the calling function corresponding to each event in the current webpage from the preset calling function library.
[0050] In a specific implementation process, in a webpage created by using Ajax, such as Web2.0, there will be corresponding events, so as to generate corresponding page content according to each event.
[0051] Because the webpage created by Ajax method can only get the content of the updated part without refreshing the entire page, after some events are executed, there is no new page content in the source code of the webpage, so that the crawler cannot get It is known that these events have been triggered, so that the relevant page co...
Embodiment 2
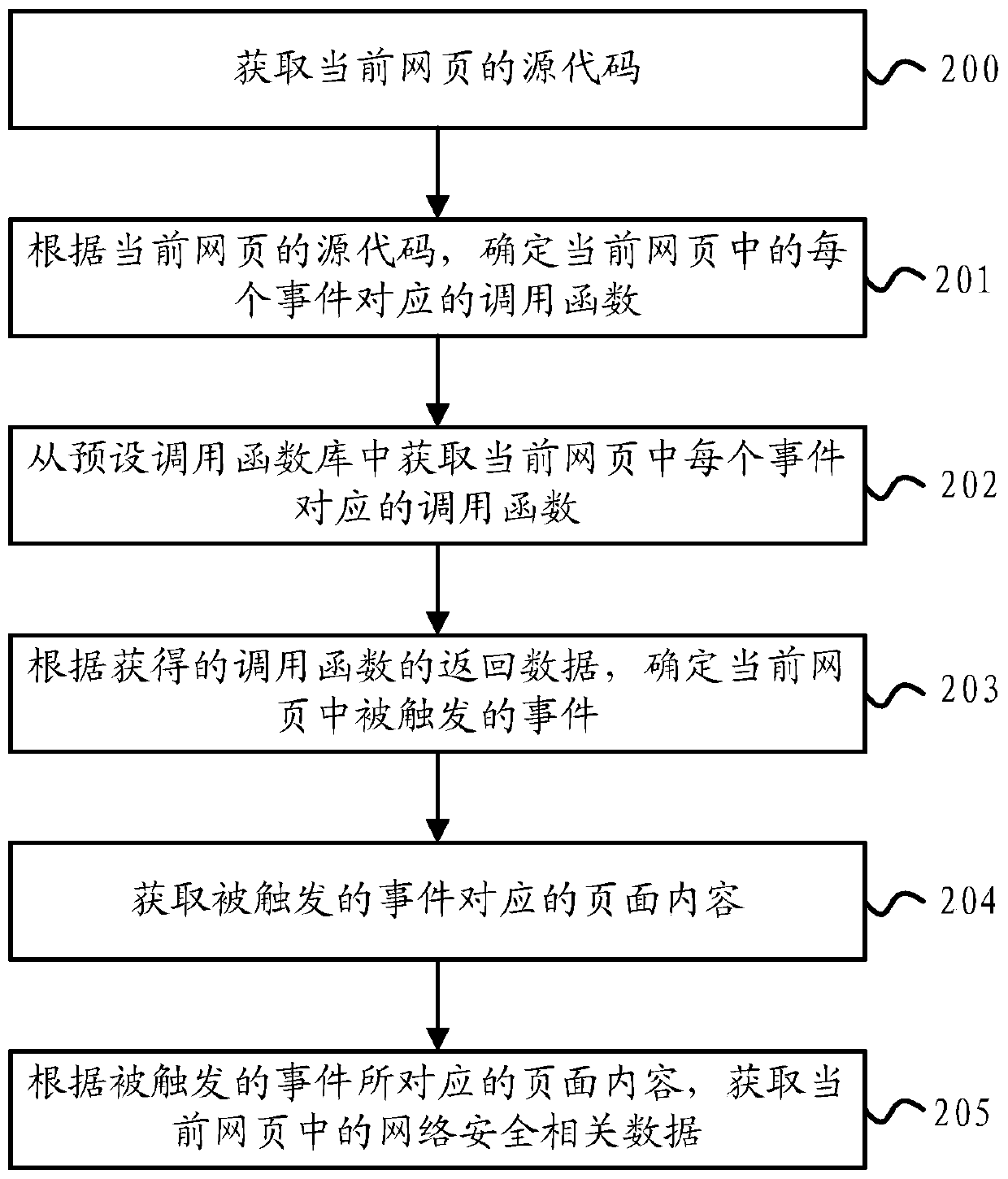
[0065] figure 2 It is a flow chart of Embodiment 2 of the network security data acquisition method of the embodiment of the present invention, as shown in figure 2 As shown, the network security data acquisition method of the embodiment of the present invention is in figure 1 On the basis of the illustrated embodiments, the technical solution of the present invention is further described in more detail.
[0066] Such as figure 2 As shown, the method for obtaining network security data in the embodiment of the present invention may specifically include the following steps:
[0067] 200. Obtain the source code of the current webpage.
[0068] The embodiment of the present invention can apply the sandbox technology to webpage protection. From the perspective of technical implementation, it is to change from preventing suspicious programs from accessing the system to redirecting suspicious programs' access to disks, registry tables, etc. Under the designated folder, thereby...
Embodiment 3
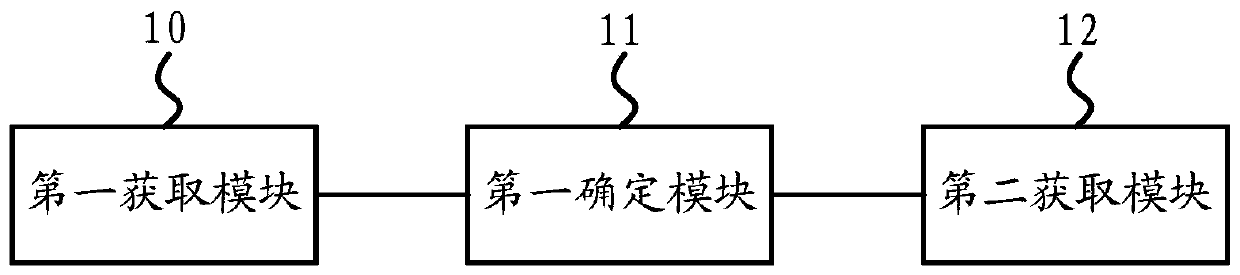
[0083] image 3 It is a schematic structural diagram of Embodiment 1 of the device for obtaining network security data according to the embodiment of the present invention, as shown in image 3 As shown, the apparatus for obtaining network security data in the embodiment of the present invention may include a first obtaining module 10 , a first determining module 11 and a second obtaining module 12 .
[0084] The first acquiring module 10 is configured to acquire the calling function corresponding to each event in the current web page from the preset calling function library.
[0085] The first determination module 11 is configured to determine the triggered event in the current webpage according to the return data of the calling function acquired by the first acquisition module 10 .
[0086] The second acquiring module 12 is configured to acquire the page content corresponding to the triggered event, and acquire network security-related data in the current web page according...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com