Malicious code analysis method and system based on semi-supervised learning
A semi-supervised learning, malicious code technology, applied in the direction of platform integrity maintenance, etc., can solve problems such as overfitting, difficult to describe all the properties and characteristics of the code and behavior of malware, and extracting a single feature type.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0058] The present invention will be described in detail below with reference to the accompanying drawings and examples.
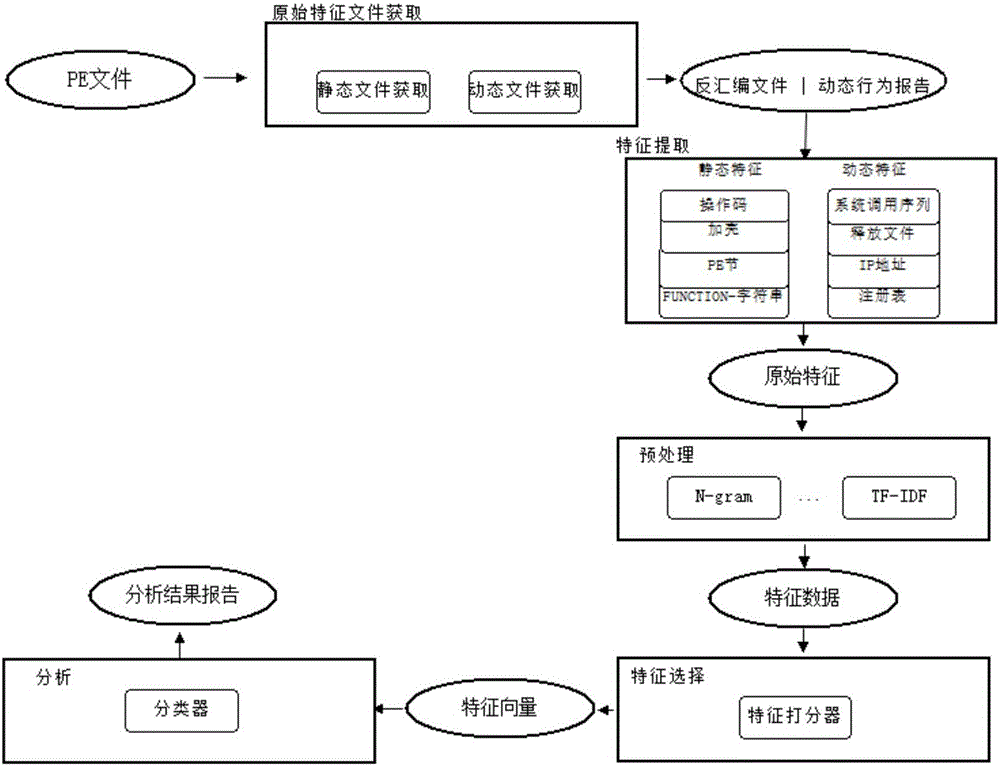
[0059] The invention provides a malicious code analysis system based on semi-supervised learning. According to the malicious code analysis process, it mainly includes five parts: an original feature file acquisition module, a feature extraction module, a preprocessing module, a feature selection module and an analysis module. like figure 1 shown.
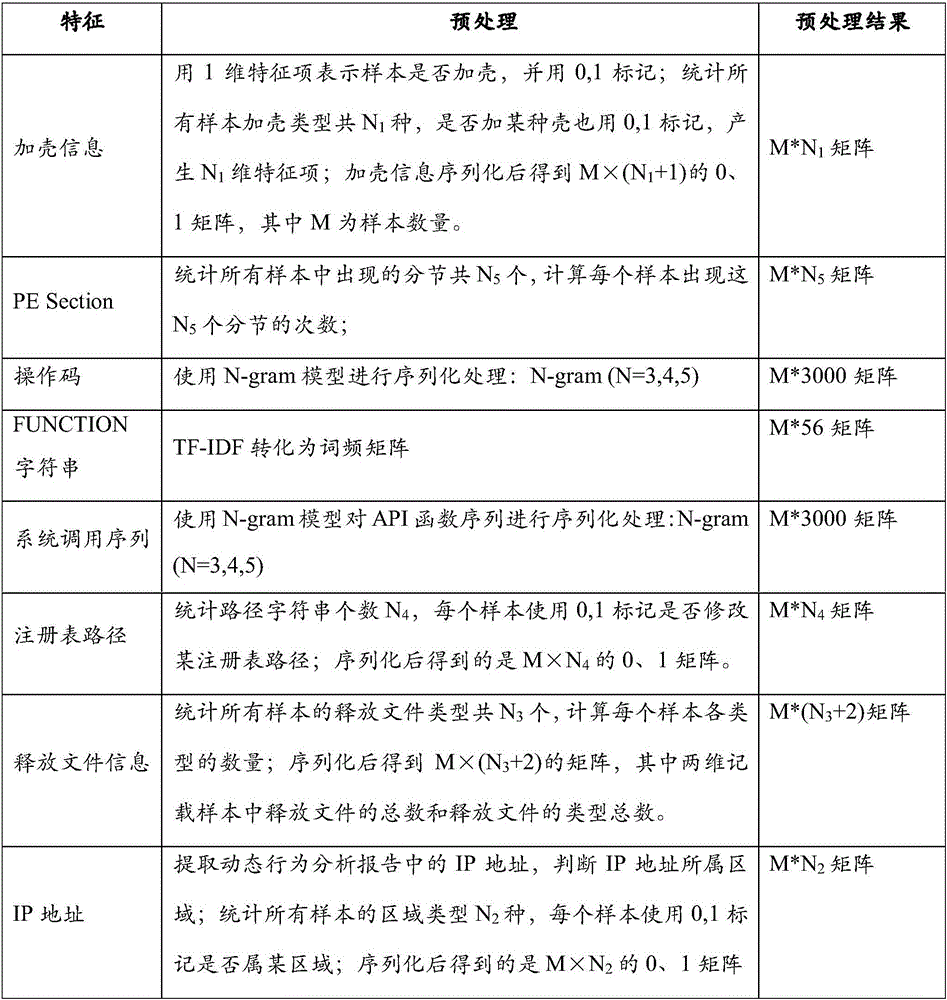
[0060] The original signature file obtains the disassembly file and dynamic behavior report of each sample in the malicious code sample set. The feature extraction module mainly finds the static and dynamic features that can effectively distinguish the malicious code family by analyzing the disassembly file and behavior of the malicious code, and extracts these original feature data from the disassembly file and dynamic behavior report of each sample. Including a variety of static features and a variety of dyn...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com