System and method for private network access authentication and key negotiation of space vehicle and earth track
A technology for access authentication and key negotiation, which is applied in the field of access authentication and key negotiation of aerospace information network, access authentication and key agreement protocol for the track dedicated network of aerospace, vehicle and ground information integration, and can solve the problem of Problems such as large amount of calculation, inapplicability, and reduced efficiency of the access process achieve the effect of long replacement cycle, easy actual operation, and efficient access to authentication protocols
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
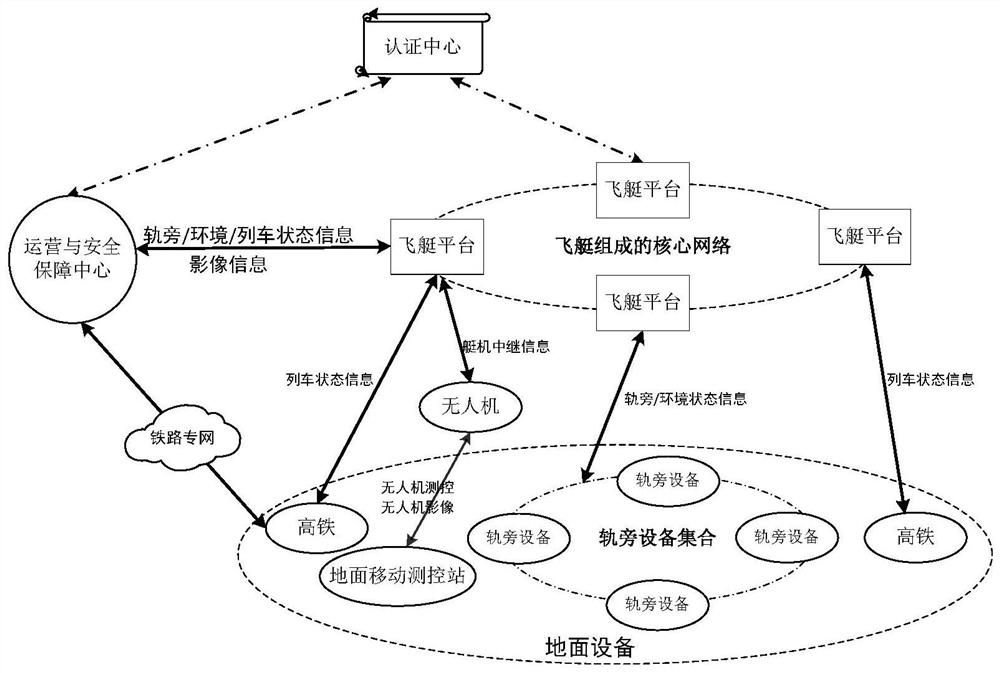
[0028] The space-space-vehicle-ground information integrated track special network is to use single or multiple stratospheric airships placed in the adjacent space above 20-50 kilometers to form a static stagnant platform, and to install communication signal receiving, processing and exchange platforms, which are convenient for ground high-speed rail users and Wayside sensor equipment provides wireless broadband point-to-multipoint services.
[0029] In this network, all network nodes use wireless communication. The openness of the wireless channel makes the transmission information easy to be monitored, and the limited wireless bandwidth resources make it difficult to apply complex security algorithms. In addition, since this system involves my country's railway transportation infrastructure, including key equipment such as high-speed rail, airships, ground mobile measurement and control stations, and safety operation guarantee centers, once an information security accident oc...
Embodiment 2
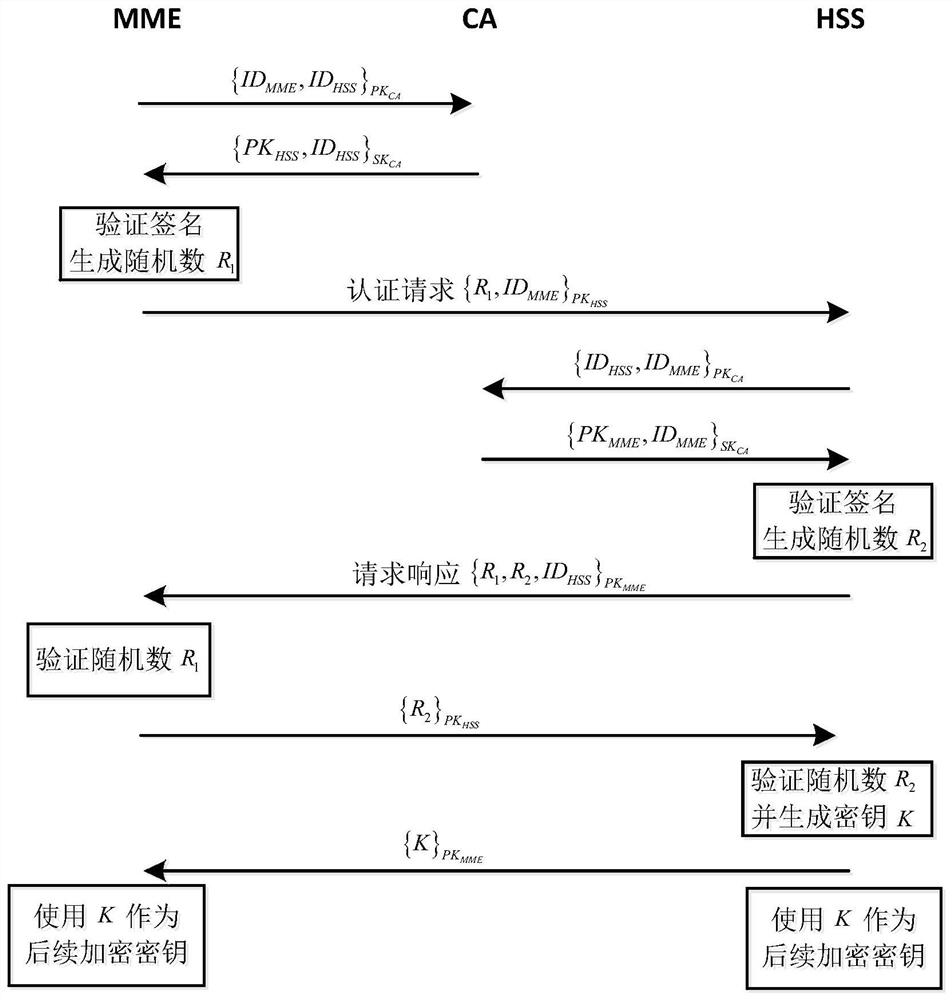
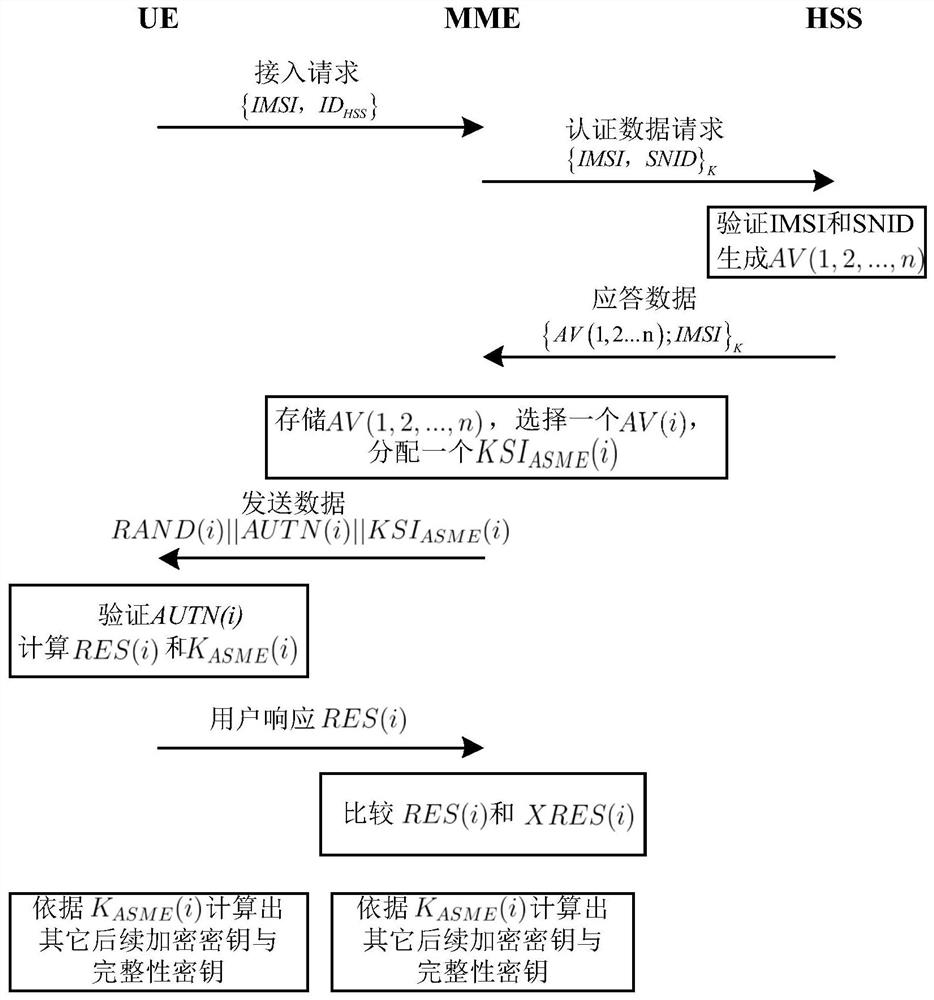
[0040] The composition of the access authentication and key agreement protocol for the space-aerospace-vehicle-ground information integration private network is the same as that in Embodiment 1. In the present invention, the symmetric key K is obtained through negotiation after the identity authentication is completed by the core network configuration authentication subsystem, and is applied to the user In the access authentication subsystem, the encryption of the link between the airship and the security and operation guarantee center in the user equipment access process is realized to ensure the safe transmission of communication data.
[0041] The improvement of the present invention avoids the problem of plaintext transmission in the original LTE security authentication mechanism. Compared with other LTE improvement schemes based on the global encryption method of public key cryptography, the symmetric encryption mechanism in the present invention has a smaller calculation a...
Embodiment 3
[0043] The composition of the access authentication and key agreement protocol for the dedicated network of aerospace, vehicle, and ground information integration is the same as that of Embodiment 1-2, and the access authentication is completed between the airship and the safety and operation support center, and the symmetric key obtained through negotiation K, establish a secure channel, as follows:
[0044] (1.a) The airship obtains the public key of the safety and operation assurance center;
[0045] (1.b) The airship uses the public key ground security and operation support center to send an access request;
[0046] (1.c) The Ground Security and Operation Support Center obtains the public key of the airship;
[0047] (1.d) The Ground Safety and Operation Support Center sends a request response to the airship;
[0048] (1.e) The airship verifies the authenticity of the safety and operation assurance center;
[0049] (1.f) After the security and operation support center v...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com