Method and device for detecting malicious software, computer device and readable storage medium
A malware and detection method technology, applied in the field of network security, can solve the problems of low accuracy of detection methods, achieve high accuracy, strong generalization ability, and accurate clustering results
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
specific Embodiment approach
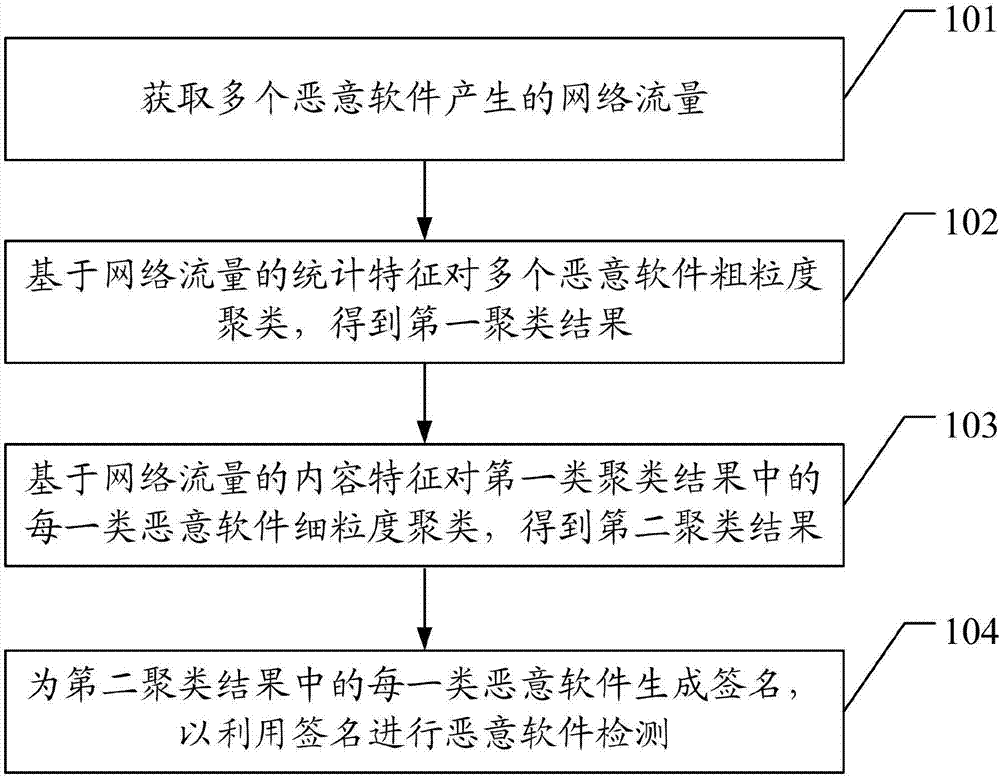
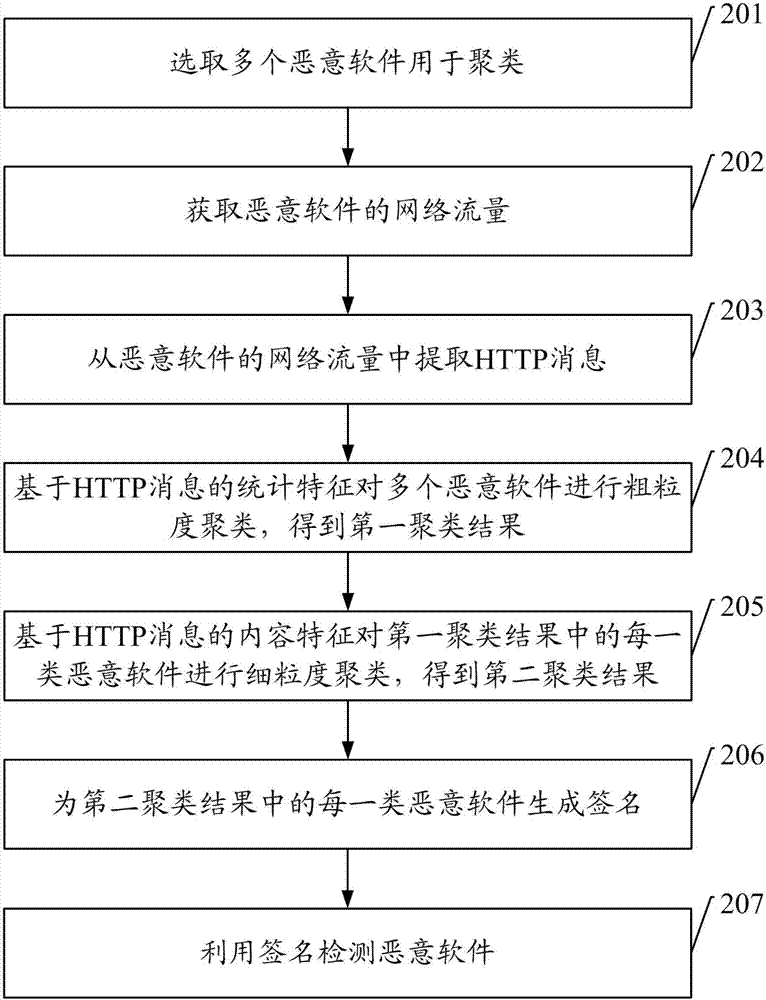
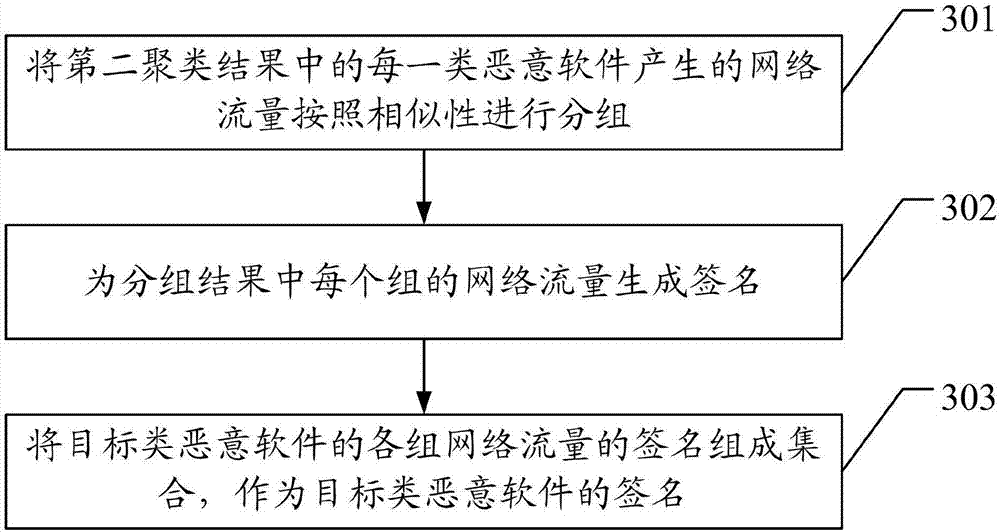
[0084] exist figure 1 In the corresponding embodiment, step 104 is used to generate a signature for each type of malware, and the signature should reflect the common characteristics of the network traffic of this type of malware or the family of malware, so as to be used to detect malware in this family of network traffic. There are many ways to generate signatures for each class of malware that reflect common characteristics of network traffic for that class of malware, see image 3 , the present invention provides a method for generating signatures for the same type of malware, which can be used as a specific implementation of step 104, an implementation of the method for generating signatures for each type of malware in the second clustering result of the present invention Examples include:
[0085] 301. Group the network traffic generated by each type of malicious software in the second clustering result according to similarity;
[0086] Assuming that the malware is clu...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com