A low -entropy mask leak protection method and its implementation system for protecting the SM4 password chip
A cryptographic chip and leakage protection technology, applied in the field of information security, can solve the problems affecting the operation efficiency of SM4 cryptographic chips and the high cost of ordinary masking methods
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0034] The technical content of the present invention will be further described in detail below in conjunction with the accompanying drawings.
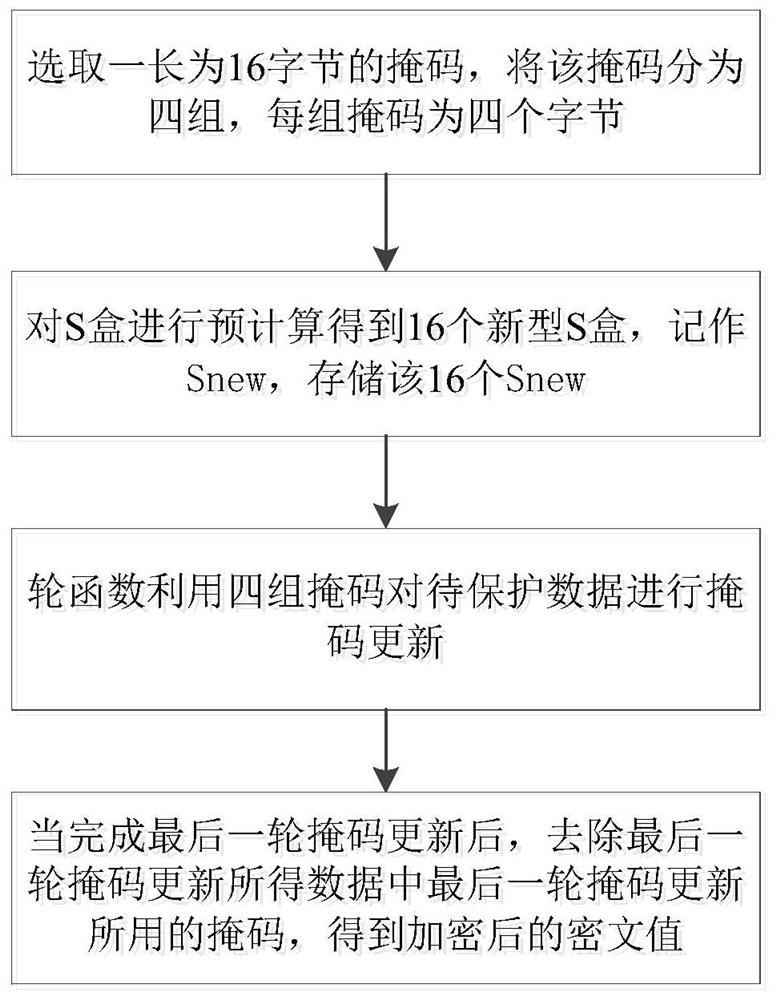
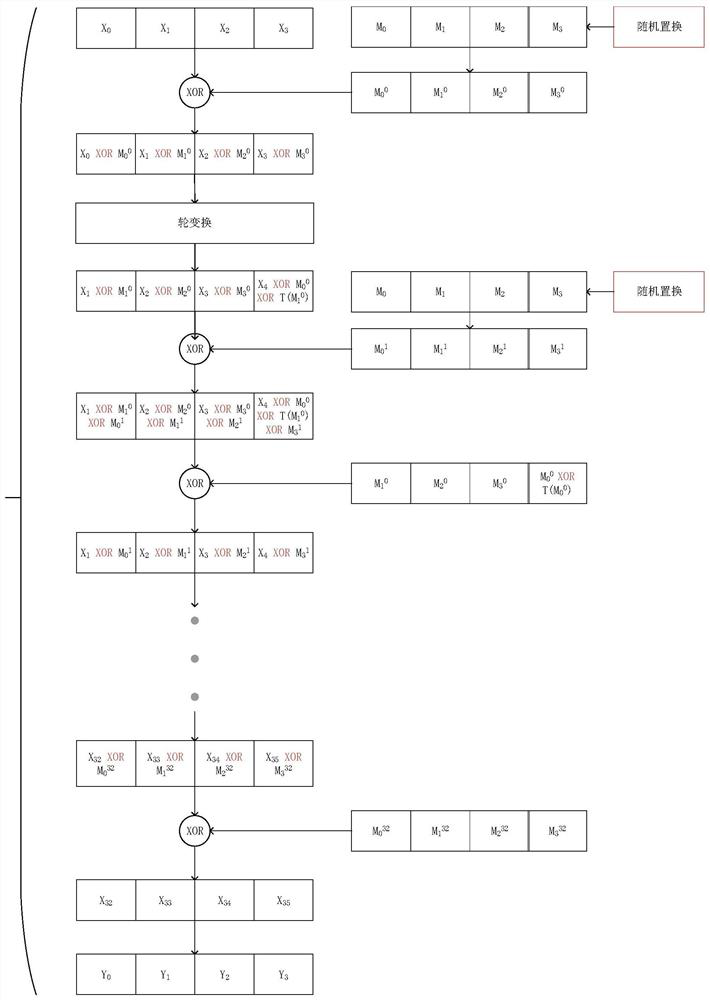
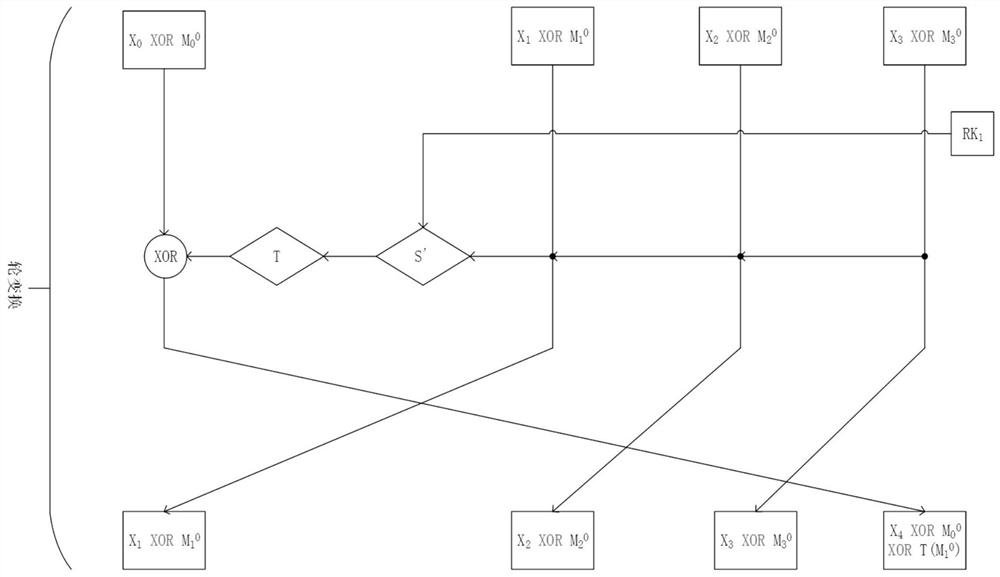
[0035] The method process of the present invention is as figure 1 As shown, first select a mask with a length of 16 bytes, divide the mask into four groups, and each group of masks is four bytes, that is, 32 bits; then pre-calculate the S box to obtain 16 new S box, denoted as S new , storing the 16 S new ; The pre-computation method is: use the elements in each group of masks as the input of the S box, where the input mask of the S box is M i middle element M ij , then the S-box output mask is M i+1 middle element M (i+1)j , the values of i and j are both 0 to 3, when the value of i+1 is 4, let i+1 be 0; then the round function uses the four sets of masks in step 1) to update the mask of the data to be protected; Among them, in each round of encryption, the use order of the four groups of masks is first determined; then the m...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com