Accuracy judgment test method based on vulnerability scanning
A vulnerability scanning and testing method technology, applied in the field of network security, can solve problems such as missed scanning of vulnerabilities, failure to send packets, and discarding of data returned by the target server beyond the delay, so as to avoid missed scanning, improve accuracy, and improve manual scanning efficiency Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0025] The present invention will be further described in detail below in conjunction with examples, but the embodiments of the present invention are not limited thereto.
[0026] A method for judging testing based on vulnerability scanning accuracy, comprising:
[0027] Step 1, the scanner starts scanning;
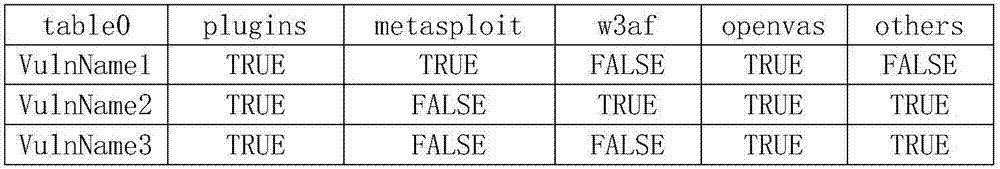
[0028] Step 2. Call self-developed plug-ins, metasploit, w3af, openvas, and some small open source frameworks or scripts;
[0029] Step 3, the first round of scanning is over, and the vulnerability names are obtained from different modules;
[0030] Step 4, the vulnerability name is stored in the database;
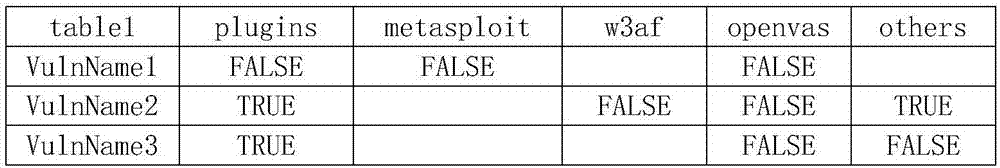
[0031] Step 5. There are modules or plug-ins with different vulnerability names corresponding to the vulnerability in the database;
[0032] Step 6. Call the module or plug-in that has the vulnerability scanning capability and has not scanned the vulnerability;
[0033] Step 7, collect the secondary scanning results, and calculate the probability of the existence ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com