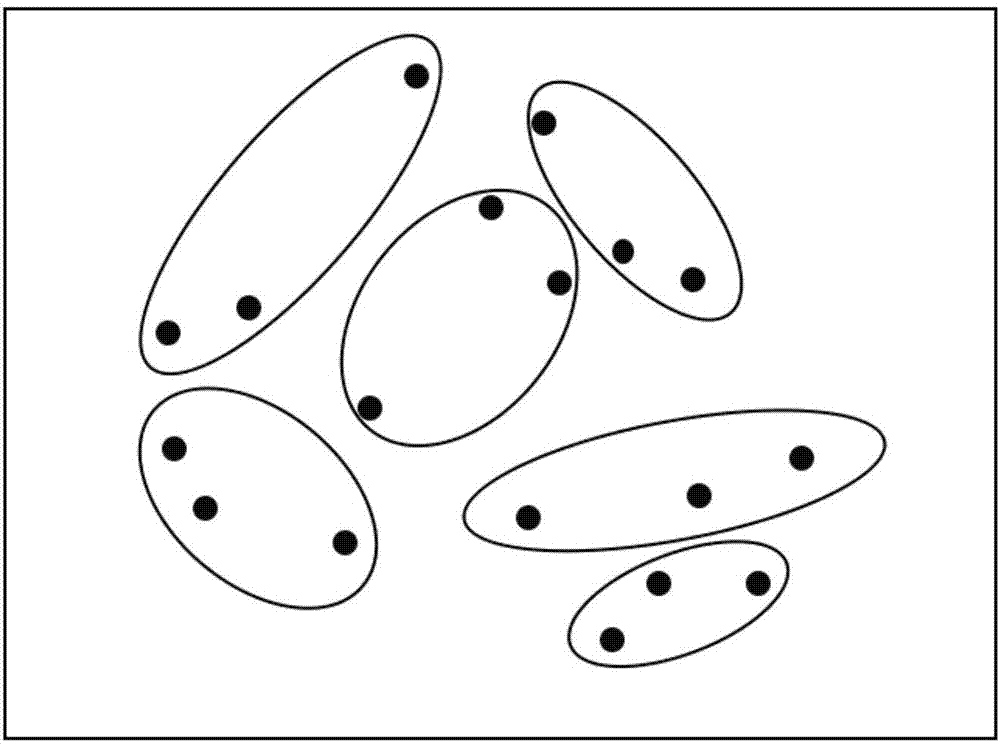
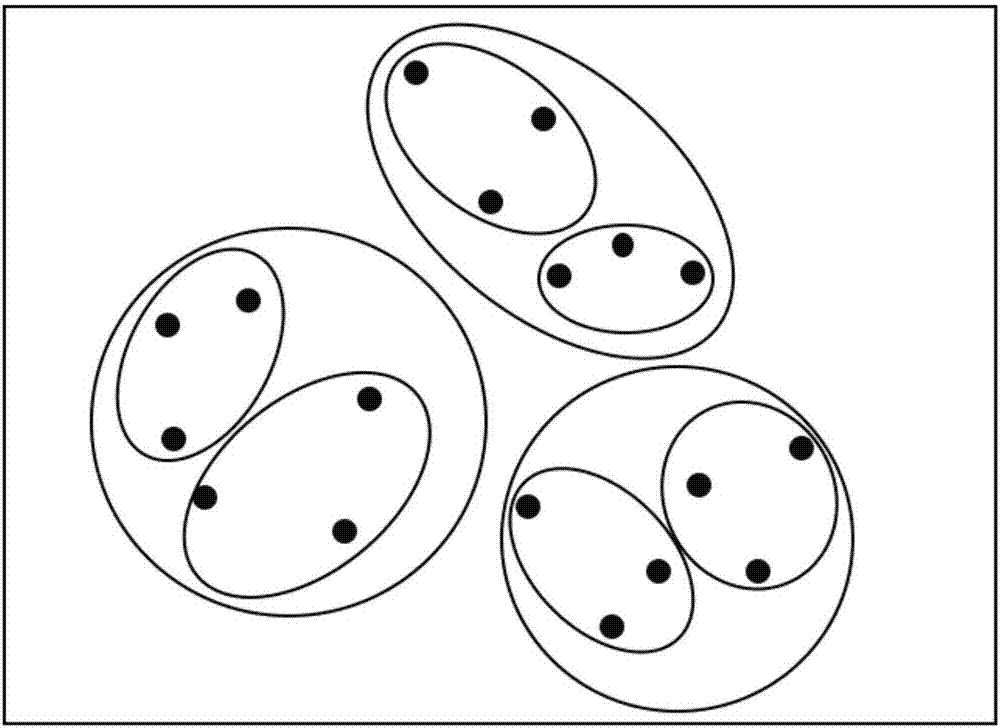
K-anonymous privacy protection method adopting density-based partition
A privacy protection and density technology, applied in the field of k-anonymity privacy protection based on density division, can solve the problems of reduced data set availability and high data information loss, and achieve the effect of reducing the amount of information loss
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0026] The present invention mainly proposes a k-anonymous privacy protection method based on density partitioning, and the concepts used in the method of the present invention are as follows.
[0027] 1. k-Anonymous Common Concepts
[0028] In the k-anonymity model, the attributes in the dataset are mainly divided into three types: identifiers, quasi-identifiers, and sensitive attributes. Identifier: An attribute that can uniquely identify a single individual, such as ID number, name, etc. Usually, such attributes need to be removed when publishing data. Quasi-identifier: A combination of several attributes in the data table, which can re-identify the user's private information by connecting with the external data table. Combinations such as zip code, date of birth, gender, etc. may be quasi-identifiers. Sensitive attributes: attributes containing private data, such as disease, salary, etc.
[0029] Definition 1 k-anonymous model: through the generalization or suppression...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com