Method for supervising approval operation, authorization operation and form operation
A form and operation record technology, applied in the fields of instruments, electronic digital data processing, digital data protection, etc., can solve the problems of confusing similar roles and permissions, difficult to remember the difference between roles and permissions with similar permissions, and increase authorization, so as to avoid confidentiality. Information leakage, convenient and quick settings
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0068] [Example 1] such as Figure 5 As shown, the method for monitoring and approving operations includes the following steps:
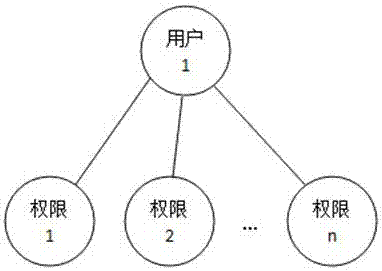
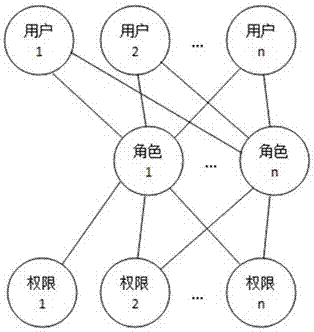
[0069] Create roles in the system, such as Figure 4 As shown, the role is an independent individual, not a group / class. At the same time, a role can only be associated with a unique user, and a user is associated with one or more roles; a user corresponds to an employee, and an employee corresponds to a user , employees determine their permissions through the roles associated with their corresponding users. Employees and users have a 1-to-1 relationship with each other and are bound for life. After a user corresponds to an employee, the user belongs to the employee, and the user cannot be associated with other employees; if the employee leaves, the user cannot correspond to other employees. After an employee joins the company again, the employee still uses the original user.
[0070] When the role performs an approval operation, record the role ...
Embodiment 2
[0077] [Example 2] such as Figure 6 As shown, the method for monitoring and approving operations includes the following steps:
[0078] Create roles in the system, such as Figure 4 As shown, the role is an independent individual, not a group / class. At the same time, a role can only be associated with a unique user, and a user is associated with one or more roles; a user corresponds to an employee, and an employee corresponds to a user , employees determine their permissions through the roles associated with their corresponding users.
[0079] When the role performs an approval operation, record the role that performs the approval operation;
[0080] Set one or more roles as supervised roles, and set one or more roles for each supervised role as its supervisor role;
[0081] The supervision role monitors the approval operation records performed by the supervised role (the supervision role can statistically view all the approval operation records performed by the supervised...
Embodiment 3
[0088] [Example 3] such as Figure 7 As shown, the method for monitoring authorized operations includes the following steps:
[0089] Create a role in the system. The role is an independent individual, not a group / class. At the same time, a role can only be associated with a unique user, and a user is associated with one or more roles;
[0090] When the role performs an authorization operation, record the role that performs the authorization operation;
[0091] Set one or more roles as monitoring roles, and set one or more roles for each monitoring role as its supervised role;
[0092] The supervisory role monitors the authorized operation records performed by the supervised role (the supervisory role can statistically view all the authorized operation records performed by the supervised role, so as to analyze the problems mapped by the relevant operation behavior of the supervised role and deal with them accordingly).
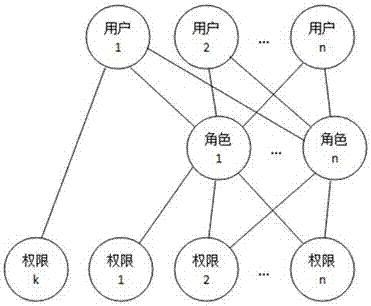
[0093] [Example 4] such as Figure 8 As shown, the me...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com