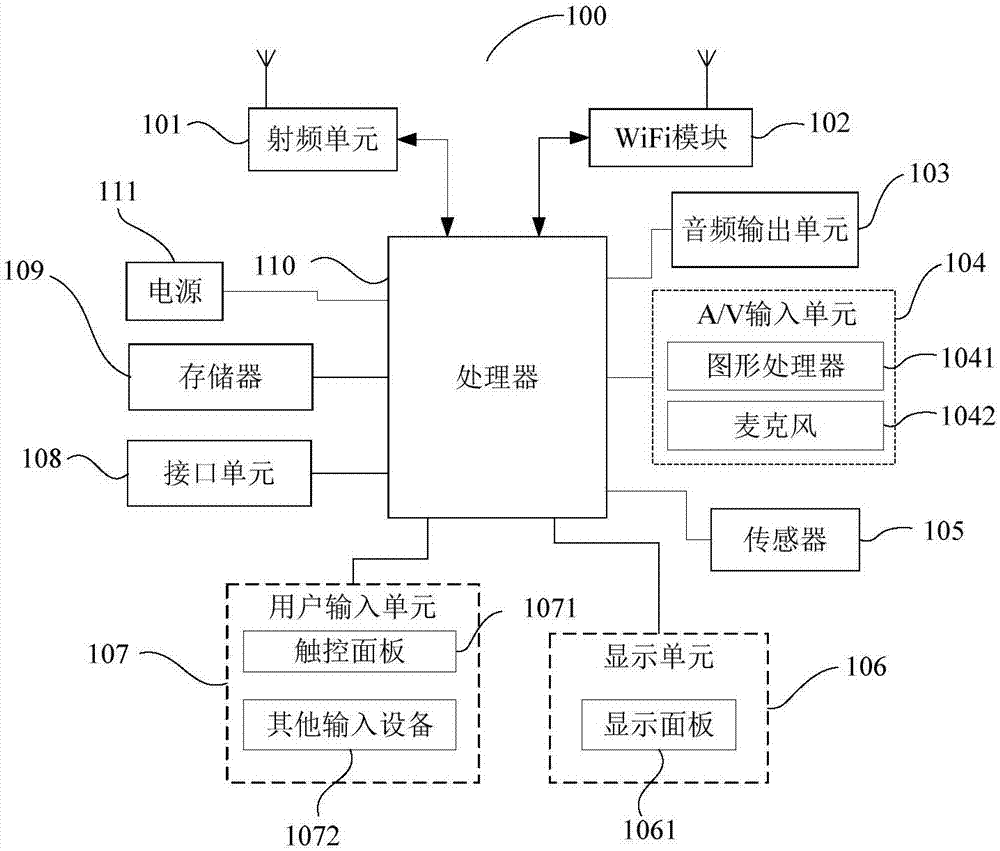
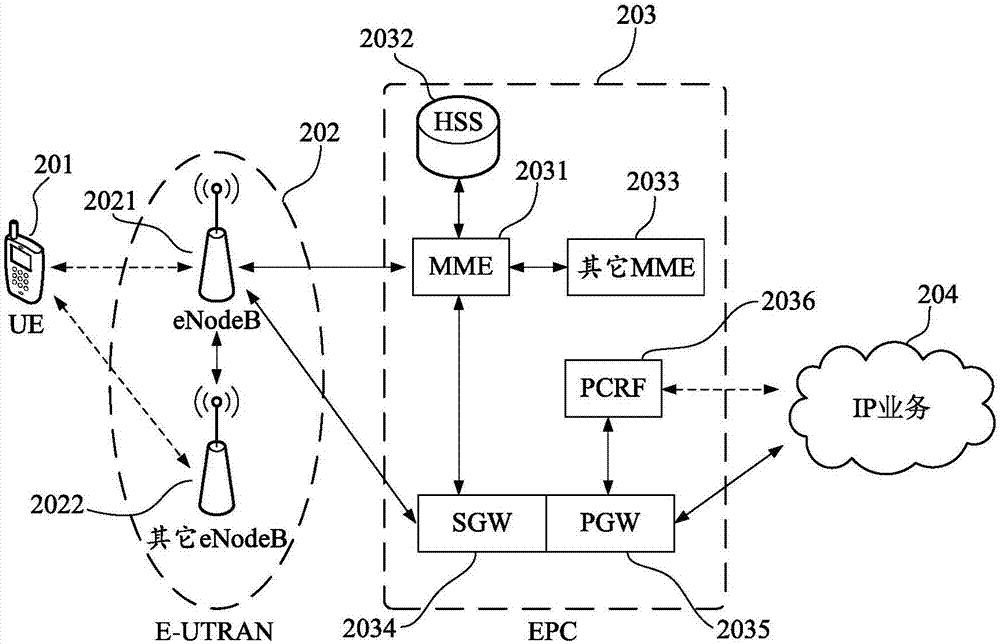
Method and apparatus for protecting contact information, and computer readable storage medium
A technology of contact information and contacts, which is applied in the field of information security, can solve problems such as contact leaks, and achieve the effect of improving user experience
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
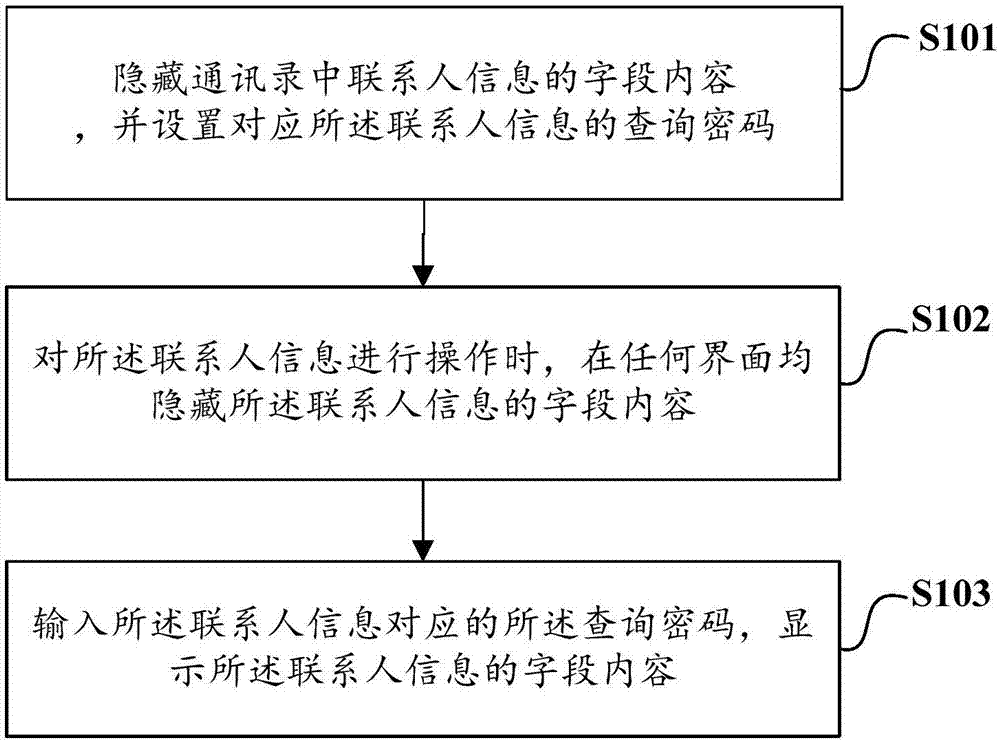
[0100] To achieve the above purpose, if image 3 As shown, the first method for protecting contact information provided by the present invention includes the following steps:
[0101] S101. Hide the field content of the contact information in the address book, and set a query password corresponding to the contact information;
[0102]S102. When operating on the contact information, hide the field content of the contact information on any interface;
[0103] S103. Input the query password corresponding to the contact information, and display the field content of the contact information.
[0104] For mobile terminals, the address book is a kind of database, which is integrated with the field hiding function. Through this field content hiding function, the mobile terminal can hide the field content corresponding to each contact in the address book, that is, in the address book The contact information is not displayed on the interface; during all operations of the mobile termina...
Embodiment 2
[0132] In another aspect of the present invention, in order to achieve the above purpose, the present invention also proposes a device for protecting contact information, which includes: a memory, a processor, and a device stored in the memory and operable on the processor A contact information protection program, when the contact information protection is executed by the processor, the steps of the following method for protecting contact information are implemented:
[0133] Hide the field content of the contact information in the address book, and set the query password corresponding to the contact information;
[0134] When operating on the contact information, hide the field content of the contact information on any interface;
[0135] Input the query password corresponding to the contact information, and display the field content of the contact information.
[0136] Wherein, when the contact information protection is executed by the processor, the following steps of the ...
Embodiment 3
[0165] In addition, in order to achieve the above object, the present invention also provides a computer-readable storage medium, where a contact information protection program is stored on the computer-readable storage medium, and when the contact information protection program is executed by the processor Steps to implement the method of protecting contact information as follows:
[0166] Hide the field content of the contact information in the address book, and set the query password corresponding to the contact information;
[0167] When operating on the contact information, the field content of the contact information is not displayed on any interface;
[0168] Input the query password corresponding to the contact information, and display the field content of the contact information;
[0169] The method, device, and computer-readable storage medium for protecting contact information provided by the present invention utilize the field hiding function of the contact databa...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com