Enterprise economic management information safety system
A technology of information security system and economic management, applied in the field of enterprise economic management system, can solve the problems of easy system being breached, reduce system security, etc., and achieve the effect of improving security and improving security system
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0023] In order to make the object, technical solution and advantages of the present invention clearer, the present invention will be further described in detail below in conjunction with the accompanying drawings and specific embodiments. It should be understood that the specific embodiments described here are only used to explain the present invention, and are not intended to limit the present invention.
[0024] see figure 1 , the present embodiment adopts the following technical solutions:
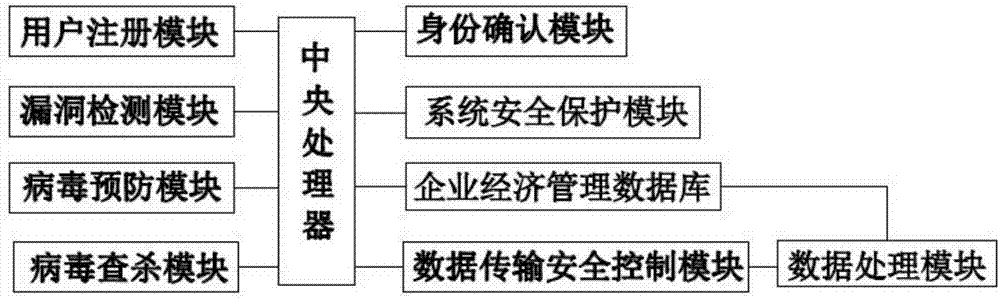
[0025] An enterprise economic management information security system, comprising
[0026] The user registration module is used to generate a biometric model corresponding to the user registration identity when the user registers, and save the biometric model in the user registration database;
[0027] The vulnerability detection module is used to detect the system vulnerabilities, install patches in time, enhance compatibility, plug the discovered security holes, and prevent the inva...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com