Secure cloud service construction method and device based on mimic defense
A construction method and cloud service technology, applied in the field of security cloud service construction based on mimicry defense, to achieve the effect of improving endogenous security performance, avoiding vendor lock-in, and ensuring reliability and security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
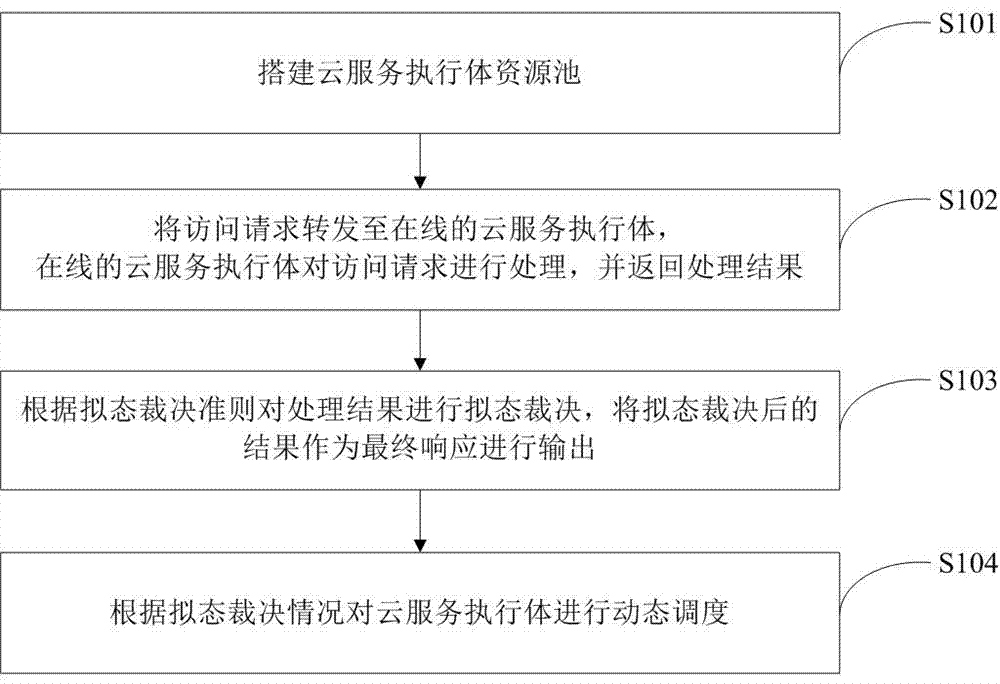
[0064] Such as figure 1 As shown, a method for constructing a security cloud service based on mimicry defense of the present invention includes the following steps:
[0065] Step S101: Build a cloud service executive resource pool.
[0066] Step S102: Forward the access request to the online cloud service executor, and the online cloud service executor processes the access request and returns a processing result.
[0067] Step S103: Perform a mimetic judgment on the processing result according to the mimetic judgment criterion, and output the result after the mimetic judgment as a final response.
[0068] Step S104: Dynamically schedule the cloud service executor according to the mimetic ruling.
Embodiment 2
[0070] Such as figure 2 As shown, another security cloud service construction method based on mimic defense of the present invention comprises the following steps:
[0071] Step S201: Build a cloud service executive resource pool, including:
[0072] Step S2011: Select several public clouds, such as Alibaba Cloud, Huawei Cloud, Kingsoft Cloud, Tencent Cloud, etc., and apply for cloud hosts from public cloud providers, such as putting forward different requirements according to the degree of heterogeneity, such as applying for cloud hosts with different operating systems etc., so that there is a certain difference between the cloud hosts applied for, and the cloud hosts of different public clouds form a diversified cloud service executive resource pool;
[0073] Step S2012: According to the degree of heterogeneity, install diversified and different versions of service realization software on cloud hosts provided by different cloud providers;
[0074] Step S2013: Perform secu...
Embodiment 3
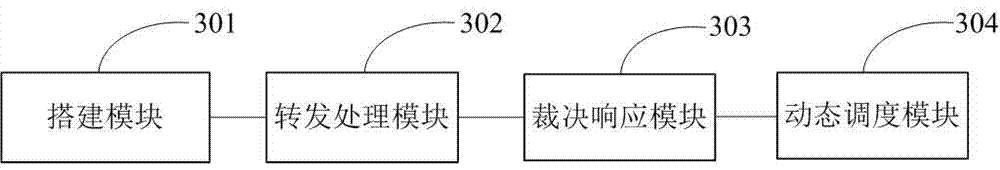
[0091] Such as image 3 As shown, a security cloud service construction device based on mimicry defense of the present invention includes:
[0092] The building module 301 is used to build a cloud service executive resource pool.
[0093] The forwarding processing module 302 is configured to forward the access request to the online cloud service executor, and the online cloud service executor processes the access request and returns a processing result.
[0094] The adjudication response module 303 is configured to perform a mimetic adjudication on the processing result according to the mimetic adjudication criterion, and output the result after the mimetic adjudication as a final response.
[0095] The dynamic scheduling module 304 is configured to dynamically schedule the cloud service executor according to the mimetic ruling.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com