Method for applying buffer overflowing on Intel-and-Linux64-integrated platform
A buffer overflow and platform technology, which is applied in the field of network security, can solve problems such as the method of exploiting few program overflows, and achieve the effect of increasing the scope of application
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
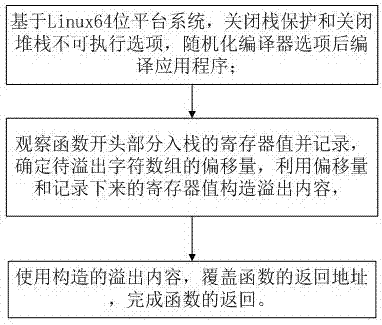
[0023] The invention provides a buffer overflow utilization method on the Intel and Linux64 platform, based on the Linux64 platform system, the application program is compiled after closing stack protection, non-executable stack and ASLR compiler options;
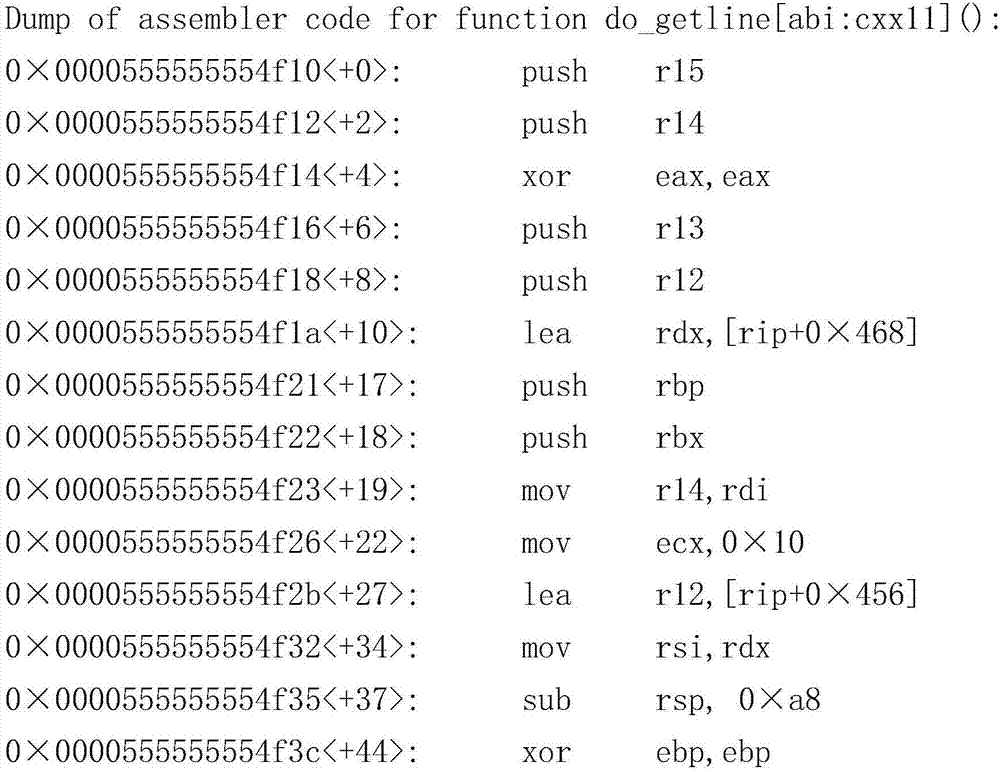
[0024] Observe and record the register value pushed onto the stack at the beginning of the function, determine the offset of the character array to be overflowed, and use the offset and the recorded register value to construct the overflow content.
[0025] Use the constructed overflow content to overwrite the return address of the function to complete the return of the function.
[0026] At the same time, it provides a buffer overflow exploitation system on Intel and Linux64 platforms.
[0027] In order to make the object, technical solution and advantages of the present invention clearer, the present invention will be further described in detail below in conjunction with specific examples.
[0028] The platform of this e...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com