A picture hiding method, restoration method and picture hiding system for protecting personal privacy
A personal privacy and image technology, applied in transmission systems, image data processing, image data processing, etc., can solve the problem of low image processing efficiency, and achieve the effect of avoiding encryption and improving image processing efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
example
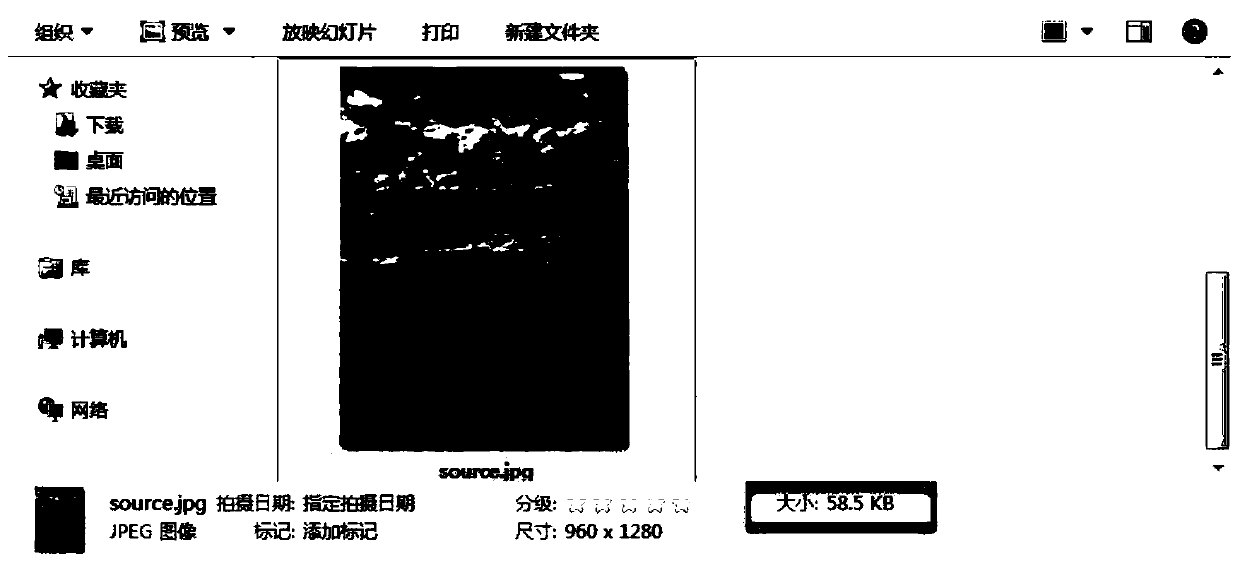
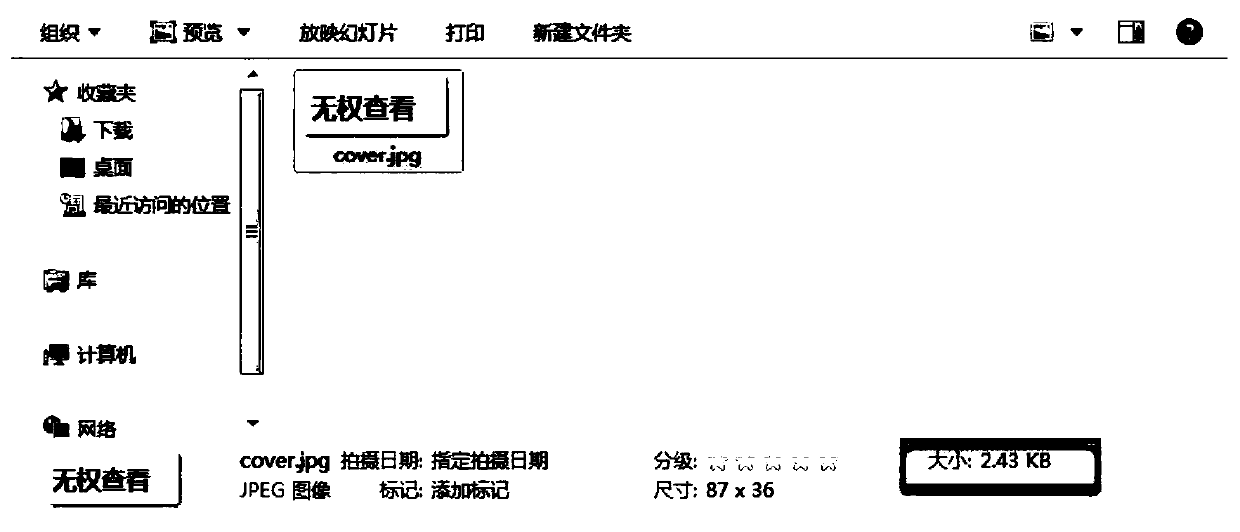
[0111] Example: A method of image hiding to protect personal privacy, the process of processing the original image: due to space limitations, only the process of processing the original image is demonstrated; first prepare two images and one is the image to be encrypted, such as figure 1 As shown, its size is 58.5KB, and the other is a display picture, which does not involve privacy information, such as figure 2 As shown, its size is 2.43KB. Include the following steps:
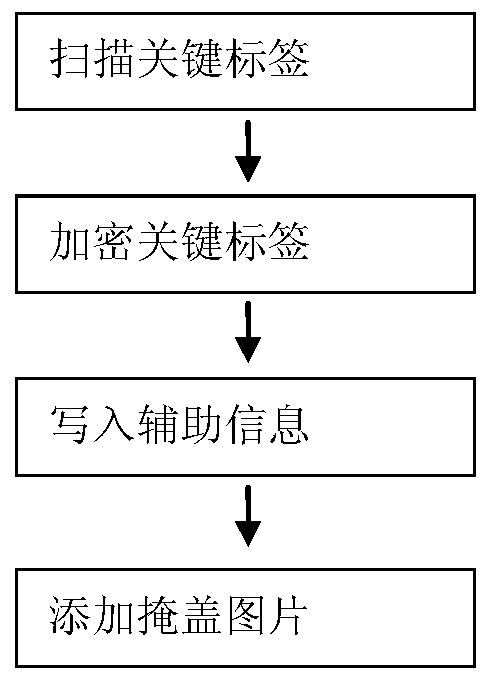
[0112] Step 1 Scan the storage bytes corresponding to the key tags in the original image (source. The section is 0xFFC0, the APP1 position is 2, and the storage byte is 0xFFE1. . . . . . The last one is EOI position 85297, storage byte is 0xFFD9. Collect storage bytes and positions to generate list;
[0113] Step 2 encrypts the key labels in the original image, assuming that the encrypted password pswd_code is 12345678:
[0114] Step 2.1 Fill the password pswd_code with the characters in the random...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com