A method for secure access and management control of ocf equipment based on asymmetric encryption algorithm
An asymmetric encryption and secure access technology, applied in the field of secure access and management control, to achieve the effect of simplifying complexity and reducing overhead
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0018] In order to make the technical means, creative features, objectives and effects achieved by the present invention easy to understand, the present invention will be further described below in conjunction with specific illustrations.
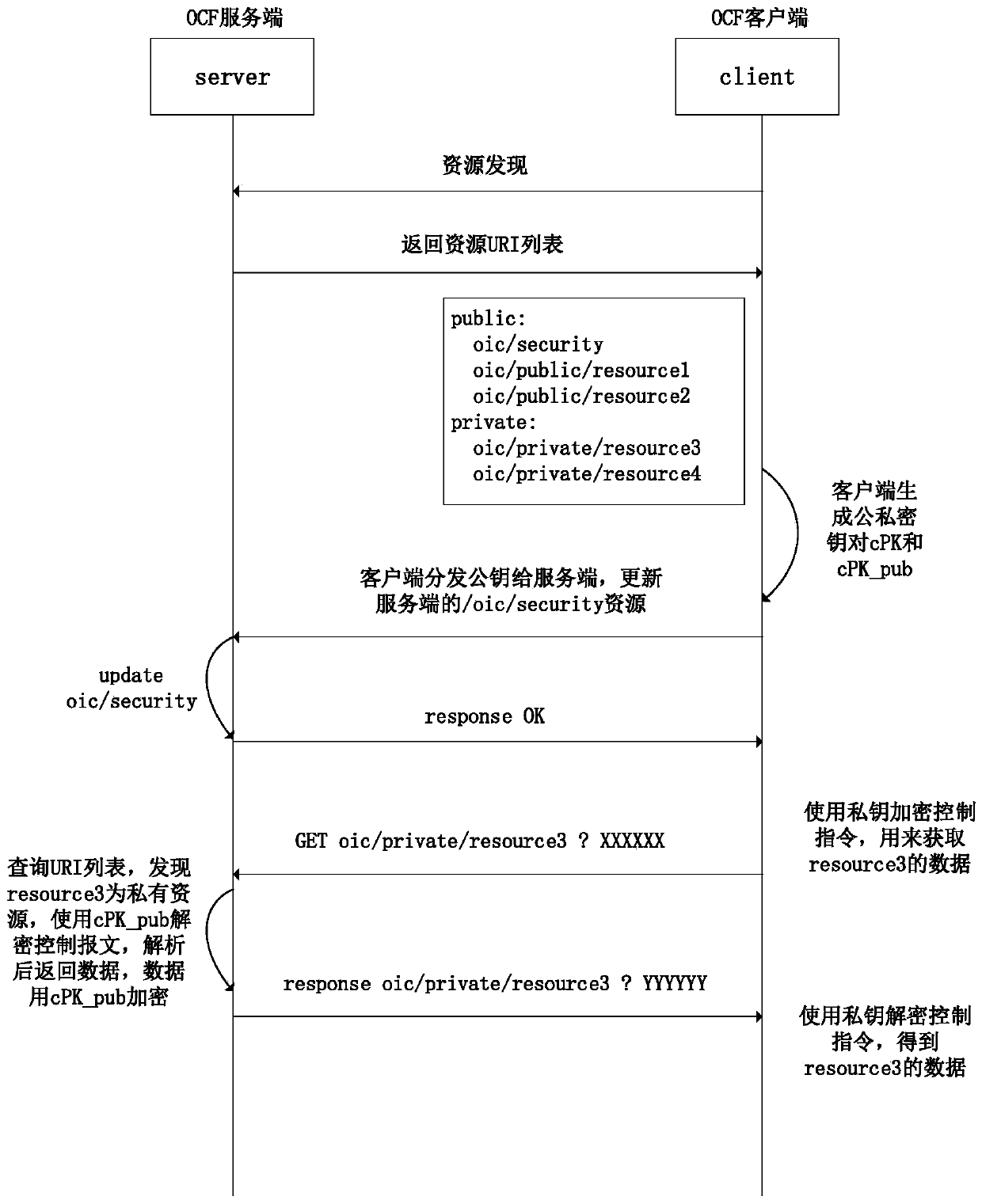
[0019] This solution is based on an asymmetric encryption algorithm to realize the secure access and management control of OCF equipment. This solution only performs simple asymmetric encryption through all control instructions and data to achieve effective simplification while ensuring a certain level of security. The complexity of OCF device security control and data interaction implementation.
[0020] Specifically, this solution is different from the SSL implementation. Only the OCF client generates a set of key pairs, and the public key method is given to the OCF server, that is, the private key cPK in the key pair is saved by the OCF client, and the key pair The public key cPK_pub in is distributed to the OCF server that the client ne...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com