Method and device for detecting behavior of latently stealing user data
A technology of user data and detection methods, applied in the field of network information security, can solve problems such as low access volume and loss of manufacturers
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
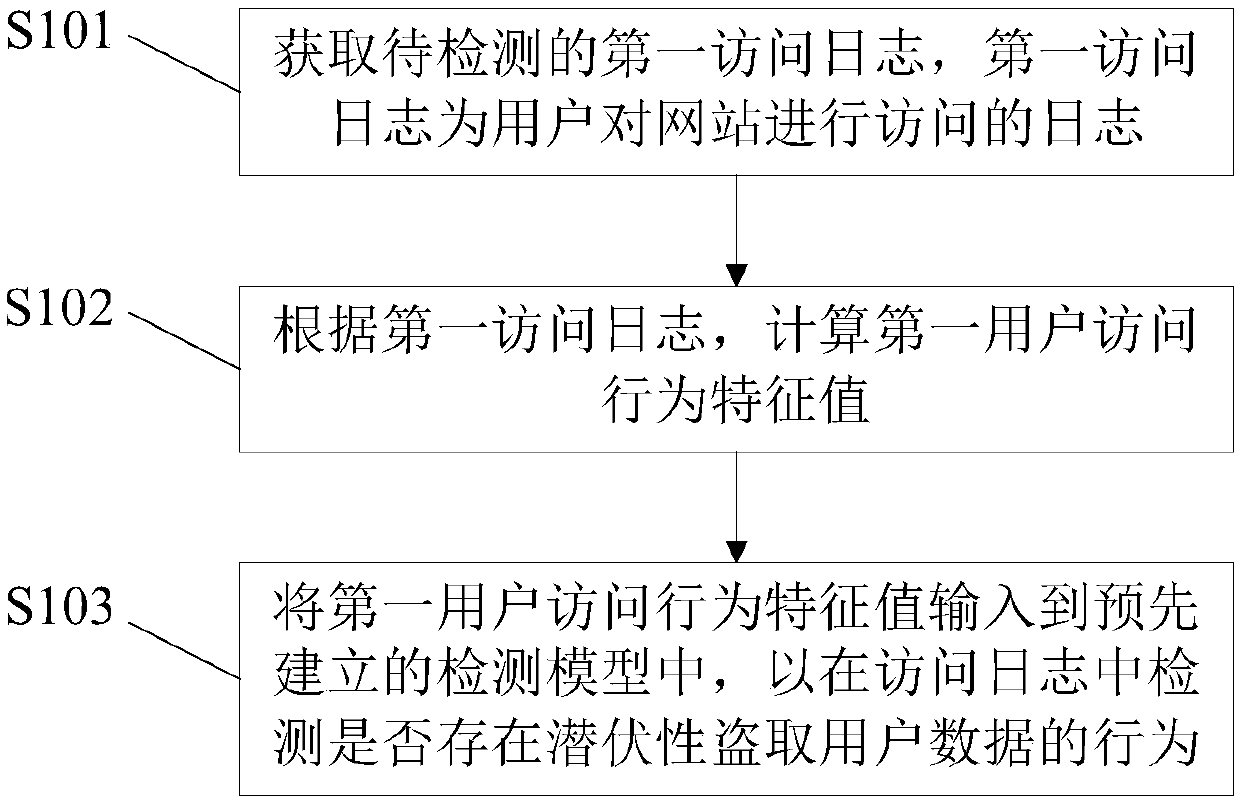
[0066] An embodiment of the present invention provides a method for latently stealing user data behavior detection, the method is executed on the server side, see figure 1 As shown, the method includes the following steps:
[0067] S101: Obtain a first access log to be detected, where the first access log is a log of a user's access to a website.
[0068] The server first obtains the access log of the user's visit to the website to be detected, mainly including logs generated by servers such as "Tomcat" and "Ngnix".
[0069] S102: Calculate the characteristic value of the first user's access behavior according to the first access log.
[0070] After obtaining the access log to be detected, calculate its corresponding user access behavior feature value. For the specific calculation process, see Figure 4-Figure 8 .
[0071] The characteristic value of user access behavior includes at least one of the following: access aggregation degree, access frequency, repeated access fre...
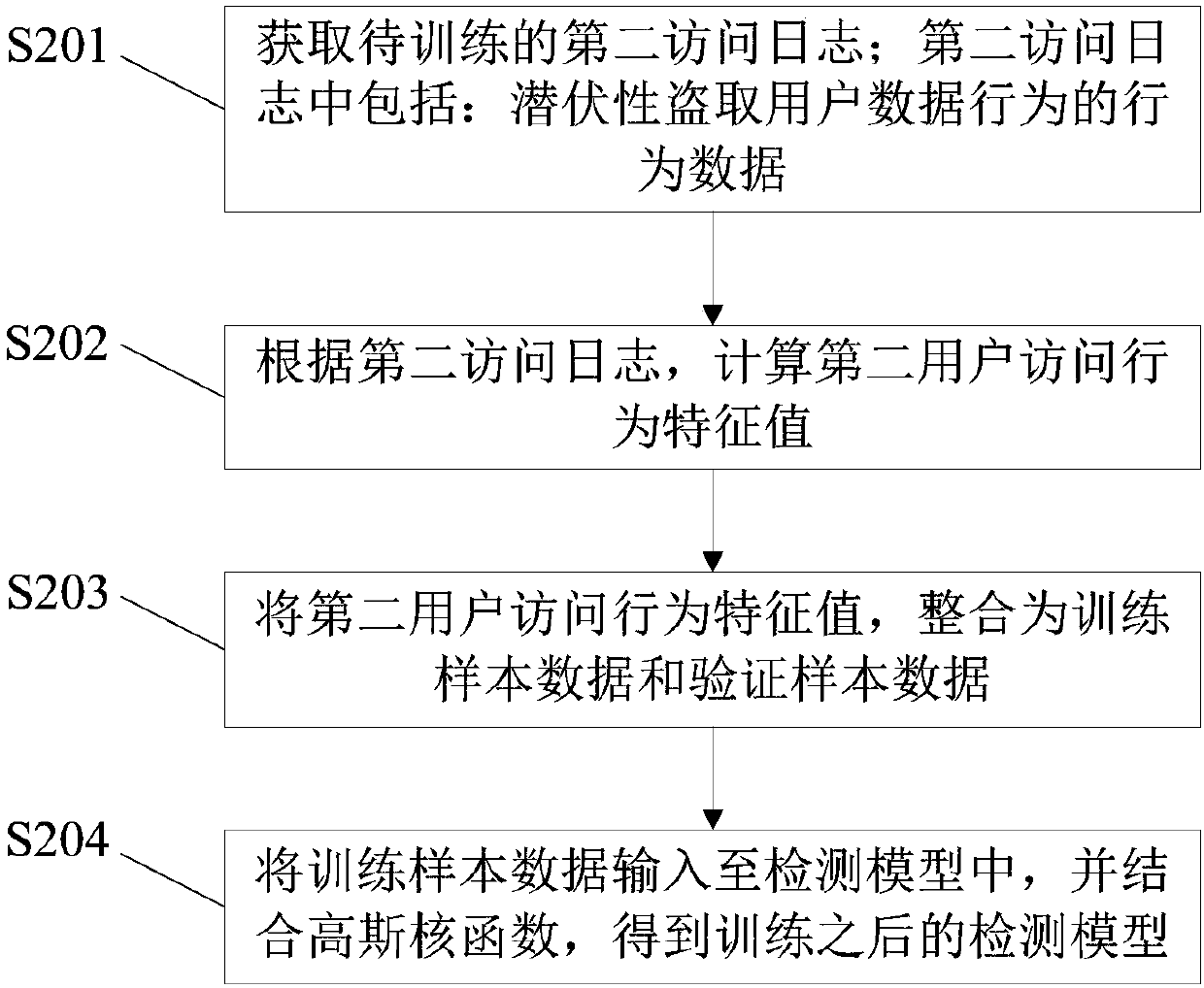
Embodiment 2
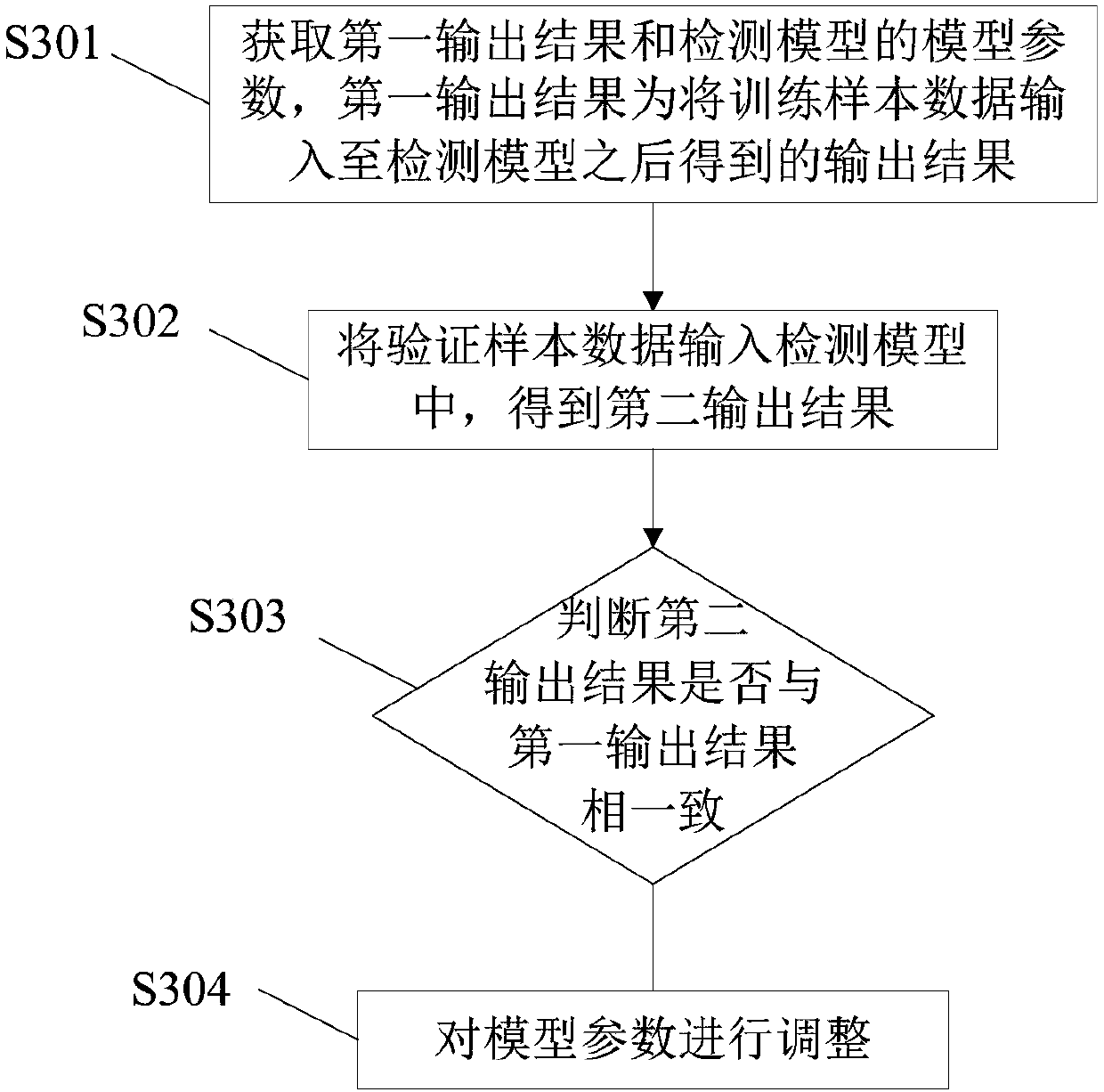
[0151] An embodiment of the present invention provides a method and device for latently stealing user data behavior detection, see Figure 9 As shown, the device includes: a log acquisition module 91 , a feature value calculation module 92 , and a detection module 93 .
[0152] Among them, the log acquisition module 91 is used to obtain the first access log to be detected, and the first access log is the log of the user's visit to the website; the characteristic value calculation module 92 is used to calculate the first user's access log according to the first access log. Behavioral feature value; the first user access behavior feature value includes at least one of the following: access aggregation, access frequency, repeated access frequency, average and variance of access interval time, access return code, access download data density, resource access frequency; The detection module 93 is used to input the first user access behavior feature value into the pre-established de...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com