Method and device used for speed limiting of message
A packet and rate-limiting technology, applied in the field of data network, can solve the problems of indiscriminate discarding, high-priority packet forwarding efficiency delay, link interruption, etc., to ensure no interruption, improve stability and efficiency The effect of ensuring the accuracy of speed limit
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
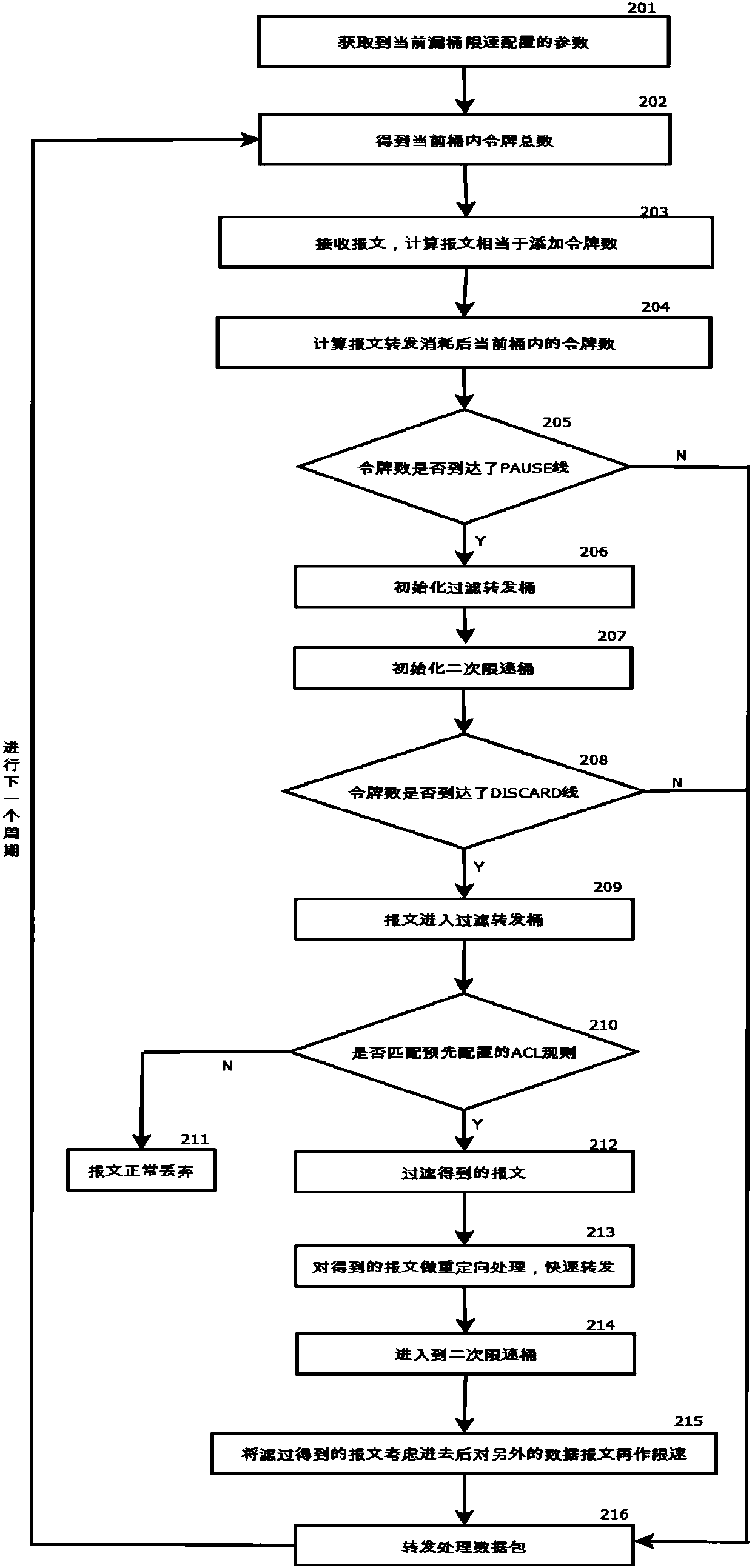
[0059] see figure 2 As mentioned above, the first embodiment of the present invention proposes a packet rate limiting method, including:
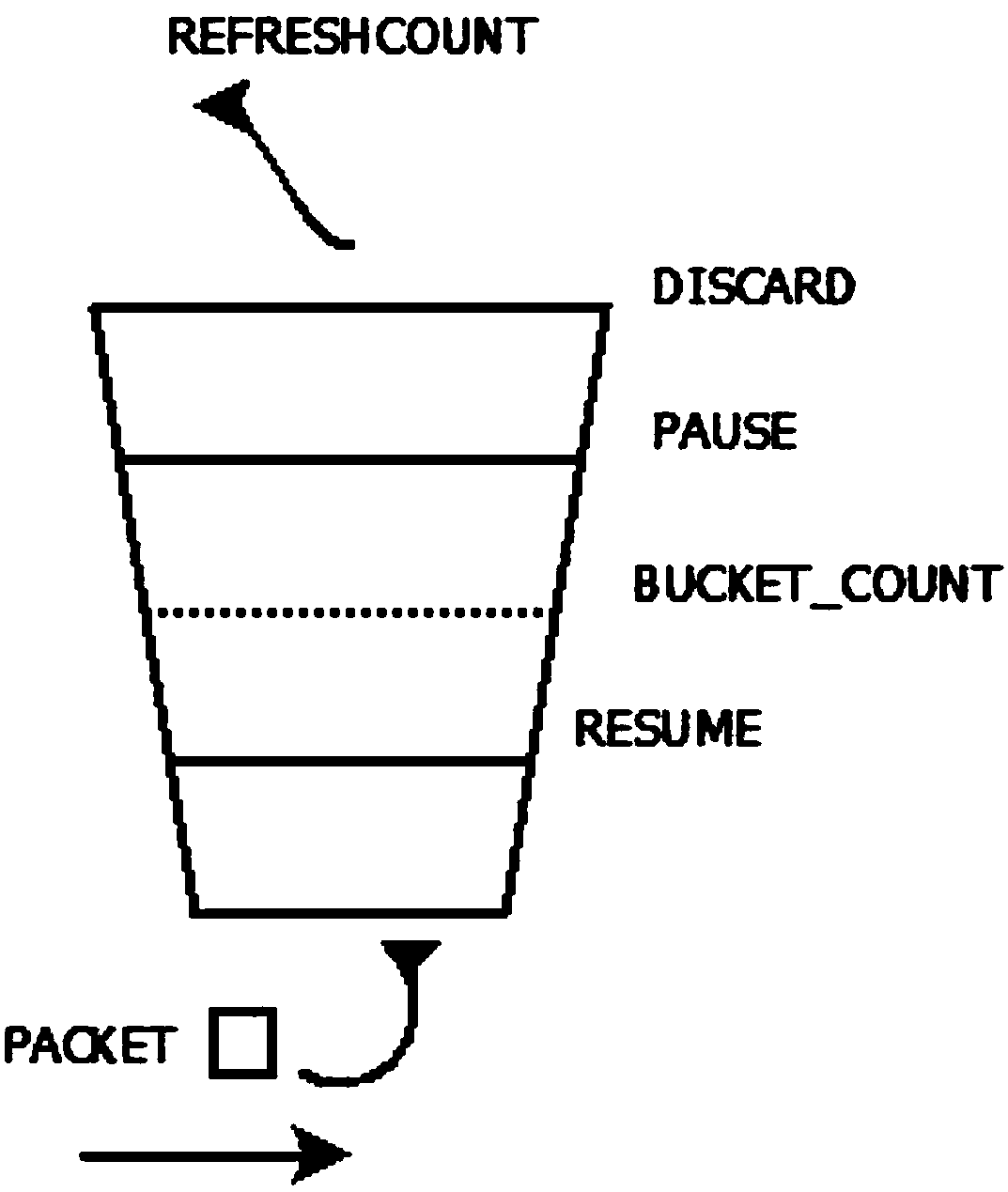
[0060] Step 201: Obtain the parameters of the current leaky bucket speed limit configuration, and the number of leaky bucket tokens arriving at the PAUSE line P n , reaching the number of leaky bucket tokens D corresponding to the DISCARD line n ,, token bucket refresh cycle T, token removal rate V, token number P remaining in the previous cycle s1 .
[0061] Step 202: Get the number P of leaky bucket tokens available in the bucket of the processing cycle a .
[0062] The number of tokens that will be transferred out in this cycle is (T*V), and the number of tokens remaining in the leaky bucket of the previous cycle is P s , the total number of tokens in the current bucket P a =P s -(T*V). In each processing cycle, the number of leaky bucket tokens available at this time needs to be obtained.
[0063] Step 203: Receive the message...
no. 2 example
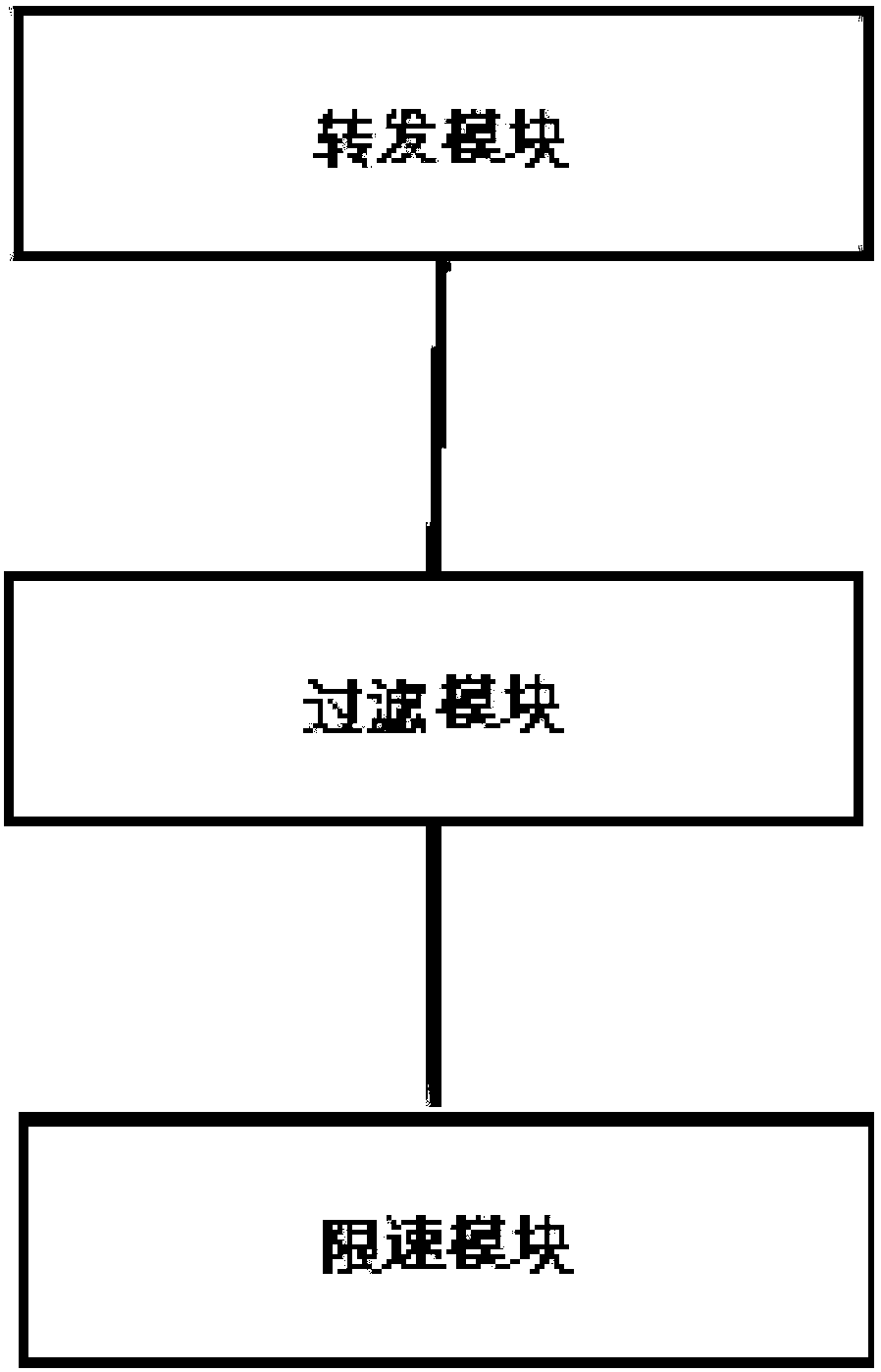
[0085] see image 3 As mentioned above, the second embodiment of the present invention proposes a message rate limiting device, the device comprising:
[0086] The forwarding module is used to transfer the packets discarded beyond the rate limit DISCARD line of the first leaky bucket into the filtering and forwarding bucket;
[0087] A filtering module, configured to perform ACL matching on the packets transferred into the filtering and forwarding bucket according to preset ACL rules, and redirect and forward the packets obtained by matching and filtering;
[0088] A rate limiting module, configured to determine the number of tokens corresponding to the secondary arrival DISCARD line according to the number of tokens corresponding to the message obtained by the matching filter, and limit the rate of the message passing through the first rate limiting bucket.
[0089] Obviously, those skilled in the art should understand that each module or each step of the above-mentioned pre...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com