Method, apparatus and system for multiplexing same digital certificate to a plurality of terminals
A digital certificate and terminal technology, applied in the field of information security, can solve the problems of increasing the cost of digital certificates, increasing the complexity of digital certificate maintenance and management, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0081] Embodiment 1 of the present invention provides a method for multiplexing the same digital certificate to multiple terminals. Wherein, the source terminal and the server form a source key chain corresponding to the public key bound when the digital certificate is issued, and the target terminal is a terminal that multiplexes the certificate in the source terminal. The method includes:
[0082] At least one target terminal, the source terminal, and the server dynamically construct at least one target key chain corresponding to the public key bound when the digital certificate is issued, after performing an identity transformation on the source key chain, and each of the target key chains is related to Source keychain equivalent.
[0083] Further, the at least one target terminal, the source terminal and the server dynamically construct at least one target key chain corresponding to the public key bound when the digital certificate is issued after performing an identity tr...
Embodiment 2
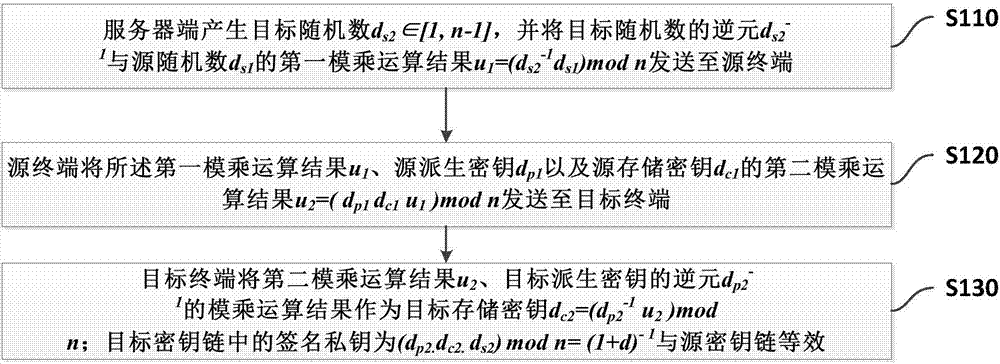
[0169] Embodiment 2 of the present invention provides a method for multiplexing the same digital certificate to multiple terminals. The method is applied to the server, wherein the source terminal and the server constitute the source corresponding to the public key bound when the digital certificate is issued. Keychain, the method includes:
[0170] Generate target random number d s2 ∈[1,n-1], where n is the order of the elliptic curve;
[0171] The inverse element d of the target random number that will be stored s2 -1 with source random number d s1 The first modular multiplication result u of 1 =(d s2 - 1 d s1 ) mod n is sent to the source terminal; the source terminal makes the modular multiplication result u 1 , source derived key d p1 and the stored source storage key d c1 The second modular multiplication result u 2 =(d p1 d c1 u 1 ) mod n is sent to the target terminal, so that the target terminal will take the second modular multiplication result u 2 ,...
Embodiment 3
[0178] Embodiment 3 of the present invention provides a method for multiplexing the same digital certificate to multiple terminals. The method is applied to the source terminal, wherein the source terminal and the server constitute the source corresponding to the public key bound when the digital certificate is issued. Keychain, the method includes:
[0179] Receive the first modular multiplication result u sent by the server 1 =(d s2 -1 d s1 ) mod n, where, d s2 -1 is the inverse of the target random number stored by the server, d s1 the source nonce stored for the server;
[0180] The result of the modular multiplication operation u 1 , source derived key d p1 and the stored source storage key d c1 The second modular multiplication result u 2 =(d p1 d c1 u 1 ) mod n is sent to the target terminal, so that the target terminal will multiply the second modular multiplication result u 2 , the inverse element d of the target derived key p2 -1 The modular multiplic...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com