String encryption, verification method, apparatus, computer readable storage medium
A technology of encryption method and verification method, applied in the field of data encryption, can solve the problems of increasing the complexity of passwords, cracking plaintext, inconvenient memory, etc., and achieve the effect of improving the difficulty of cracking
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0045] It should be understood that the specific embodiments described here are only used to explain the present invention, not to limit the present invention.
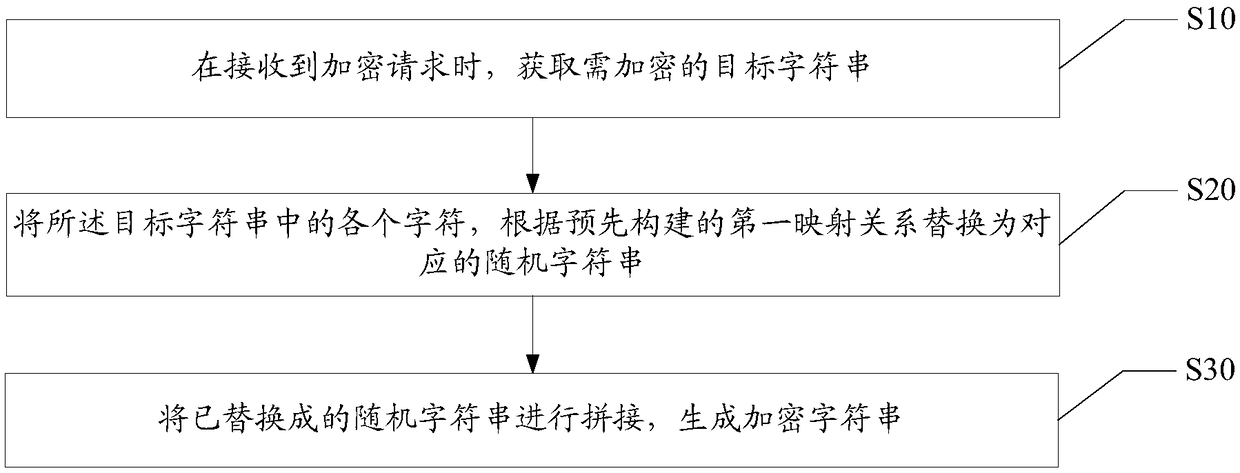
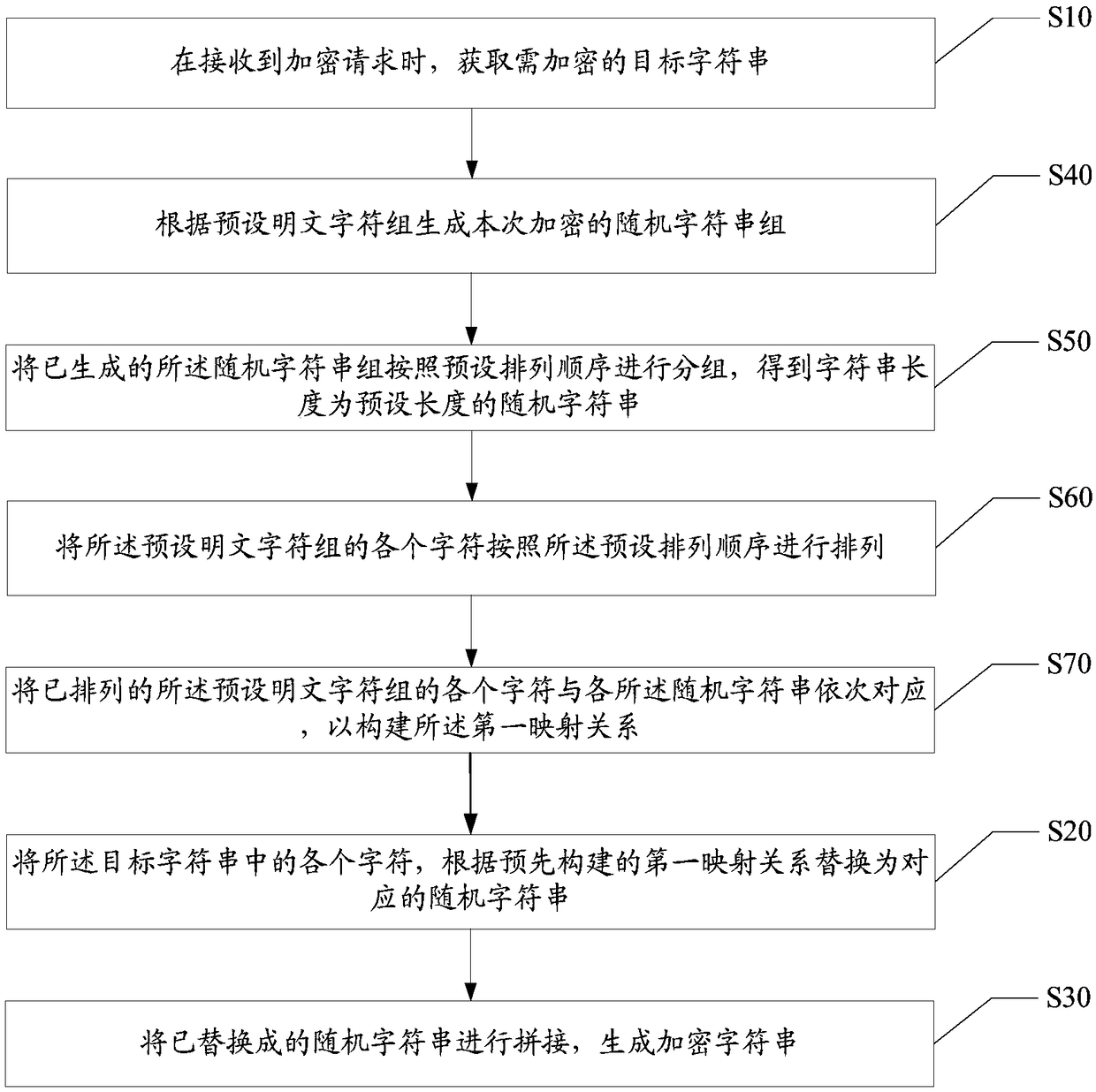
[0046] The main solution of the embodiment of the present invention is: when an encryption request is received, obtain the target character string to be encrypted; replace each character in the target character string with a corresponding random character string according to the first mapping relationship; The replaced random strings are concatenated to generate encrypted strings.
[0047] Since the string is encrypted by increasing the complexity and length of the password, it is not easy for the user to remember; the method of "adding salt" encryption may also be cracked. Therefore, the present invention provides a solution, aiming to provide an encryption method that does not increase the user's memory burden, and at the same time increases the difficulty of cracking.
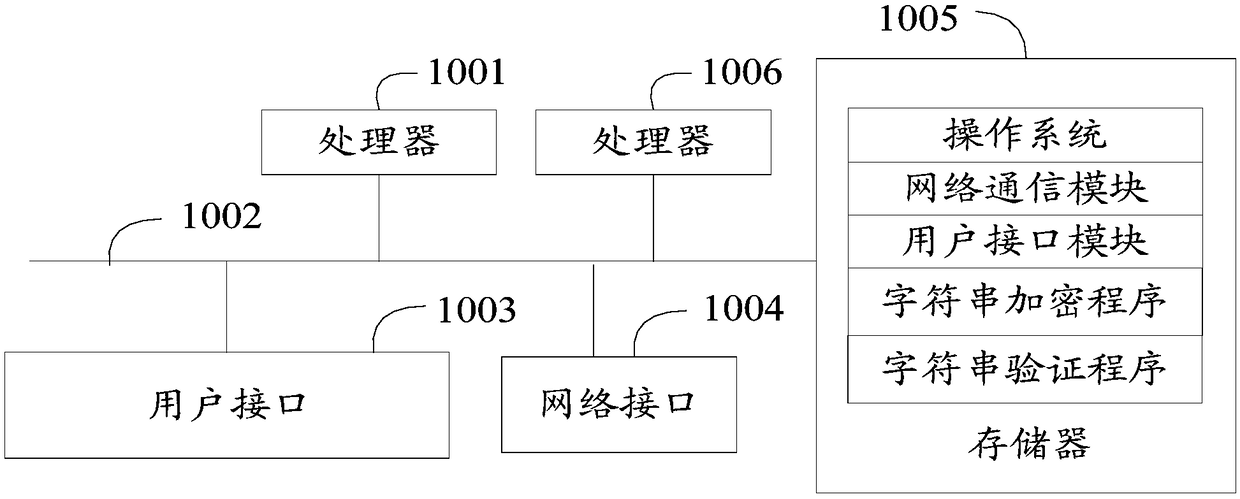
[0048] like figure 1 as shown, figure 1 It...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com