A method for obtaining an unauthorized user number, an attribution simulator and a system
A technology of user number and attribution, which is applied in the field of communication and can solve problems such as the inability to obtain the user's MSISDN number
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
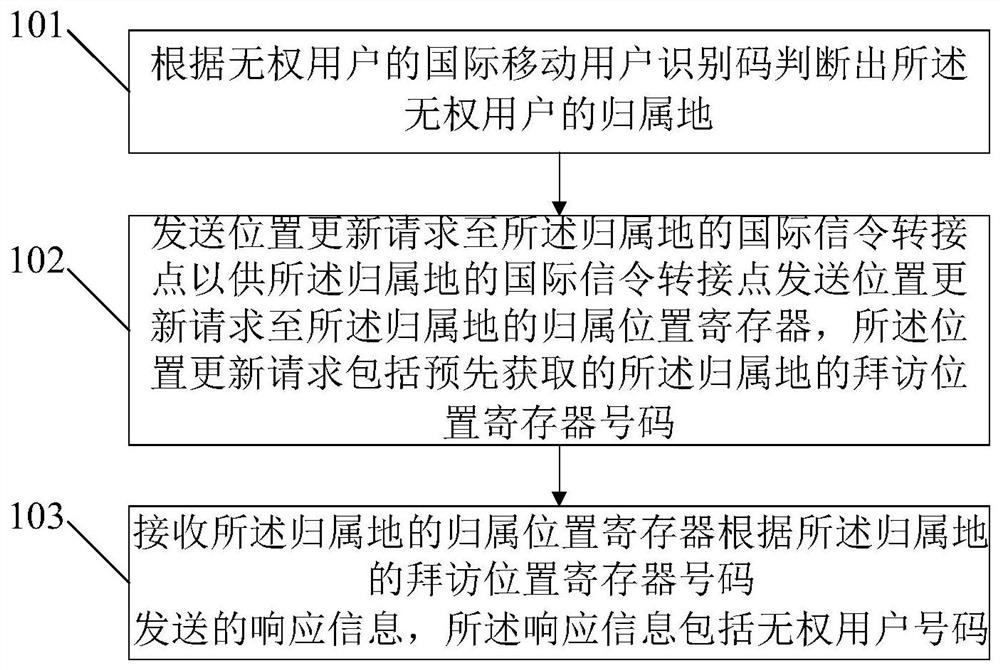
[0041] figure 1 A schematic flowchart of a method for obtaining an unauthorized user number provided in Embodiment 1, as shown in figure 1 As shown, the method includes:
[0042] Step 101. Determine the attribution of the unauthorized user according to the International Mobile Subscriber Identity of the unauthorized user.
[0043] The International Mobile Subscriber Identification Code is a sign to distinguish mobile users. It is a 15-digit decimal number with a structure of MCC (Mobile Country Code, Mobile Country Code) + MNC (Mobile Network Code, Mobile Network Number) + MSIN (Mobile Subscriber Identification Number, Mobile Subscriber Identification Number). The MCC has 3 digits and is used to uniquely identify the country to which the mobile user belongs. MNC is 2 to 3 digits and is used to identify the mobile communication network to which the mobile user belongs. MSIN is a mobile subscriber identification number, which is used to identify mobile subscribers in a certa...
Embodiment 2
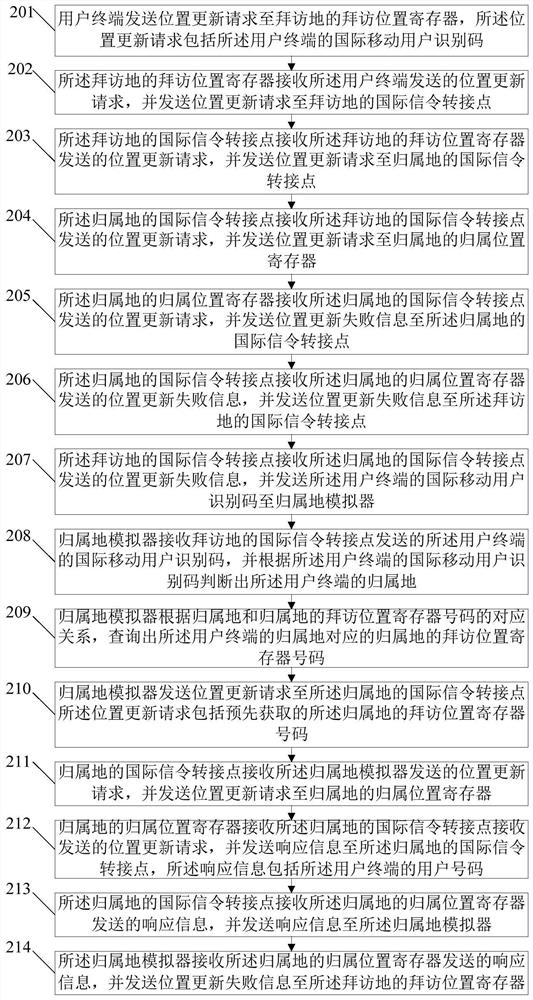
[0052] figure 2 A schematic flowchart of a method for obtaining an unauthorized user number provided in Embodiment 2, as shown in figure 2 As shown, the method includes:
[0053] Step 201, the user terminal sends a location update request to the visitor location register of the visited place, and the location update request includes the international mobile subscriber identity code of the user terminal.
[0054] In this embodiment, the user terminal is an unauthorized user terminal, and the user terminal does not have the roaming authority of the visited place, and cannot register in the visitor location register of the visited place.
[0055] Step 202, the VLR of the visited place receives the location update request sent by the user terminal, and sends the location update request to the international signaling transfer point of the visited place.
[0056] Step 203: The international signaling transfer point of the visited location receives the location update request sen...
Embodiment 3
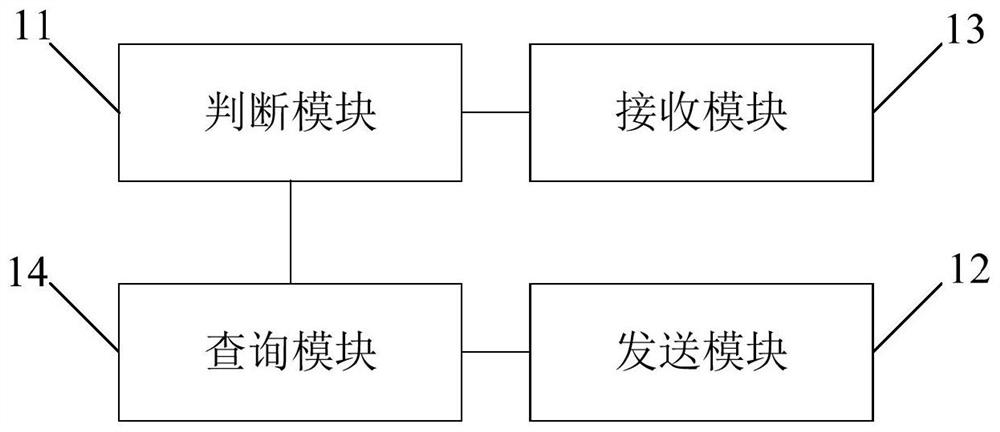
[0079] image 3 A structural schematic diagram of an attribution simulator provided in Embodiment 3, such as image 3 As shown, the attribution simulator includes: a judging module 11 , a sending module 12 and a receiving module 13 .
[0080] The judgment module 11 is used for judging the attribution of the unauthorized user according to the International Mobile Subscriber Identity code of the unauthorized user.
[0081]The sending module 12 is used to send a location update request to the international signaling transfer point of the home place, so that the international signaling transfer point of the home place sends a location update request to the home location register of the home place, the The location update request includes the pre-acquired visitor location register number of the home location.
[0082] The receiving module 13 is configured to receive response information sent by the HLR of the home location according to the VLR number of the home location, where ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com