Attack detection method, system and electronic device based on threat intelligence
An attack detection and intelligence technology, applied in the field of network security, which can solve the problems of poor accuracy and long detection time.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
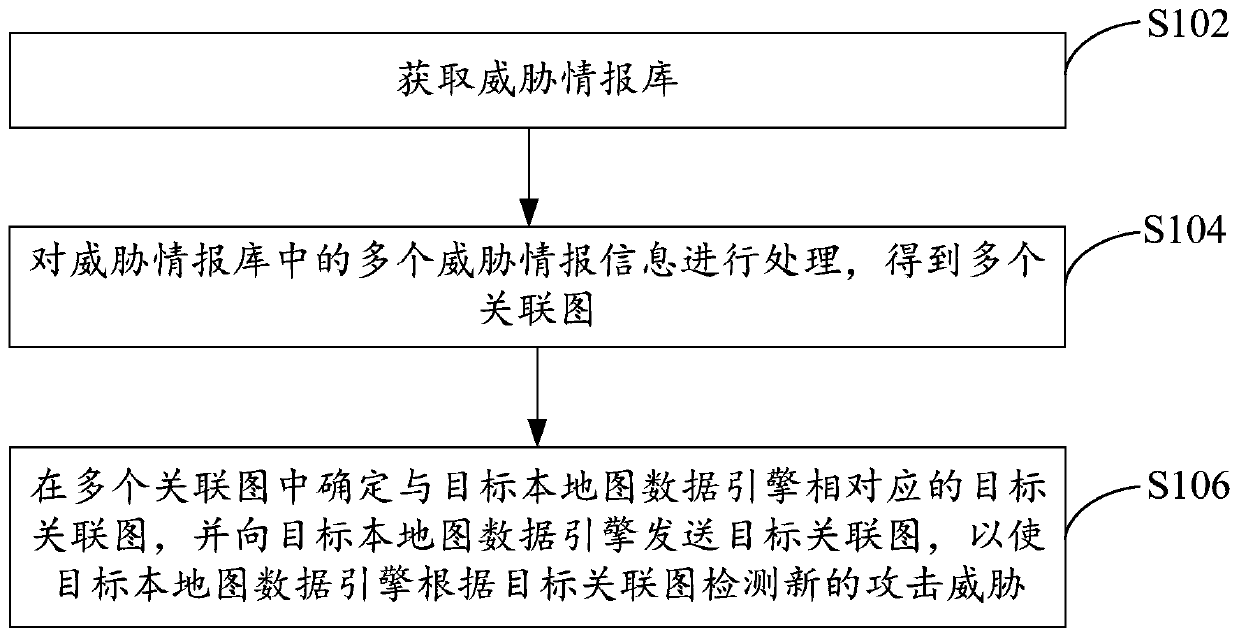
[0045] An attack detection method based on threat intelligence, refer to figure 1 , the method includes:
[0046] S102. Obtain a threat intelligence database, which includes multiple pieces of threat intelligence information obtained in real time, and the threat intelligence information is used to represent the attack threat of the attacker attacking the attacked;
[0047] In the embodiment of the present invention, the method is executed by a graph data engine in the cloud. The graph data engine in the cloud obtains multiple threat intelligence information in real time, and the multiple threat intelligence information is sent by multiple local map data engines in real time. Multiple local map data engines are installed on multiple user terminals. The user terminal can be a local common user terminal or a third-party terminal, such as a specific terminal of some companies. In this way, the map data engine in the cloud can not only Obtaining threat intelligence information of...
Embodiment 2
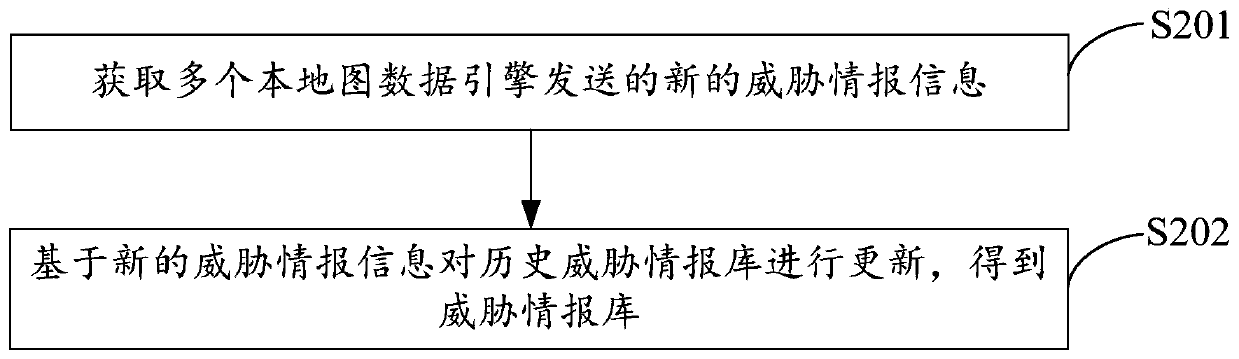
[0085] The embodiment of the present invention also provides an attack detection system based on threat intelligence, refer to Figure 4 , the system consists of:
[0086] The acquiring module 20 is configured to acquire a threat intelligence database, the threat intelligence database includes a plurality of threat intelligence information acquired in real time, and the threat intelligence information is used to represent the attack threat of the attacker attacking the attacked;
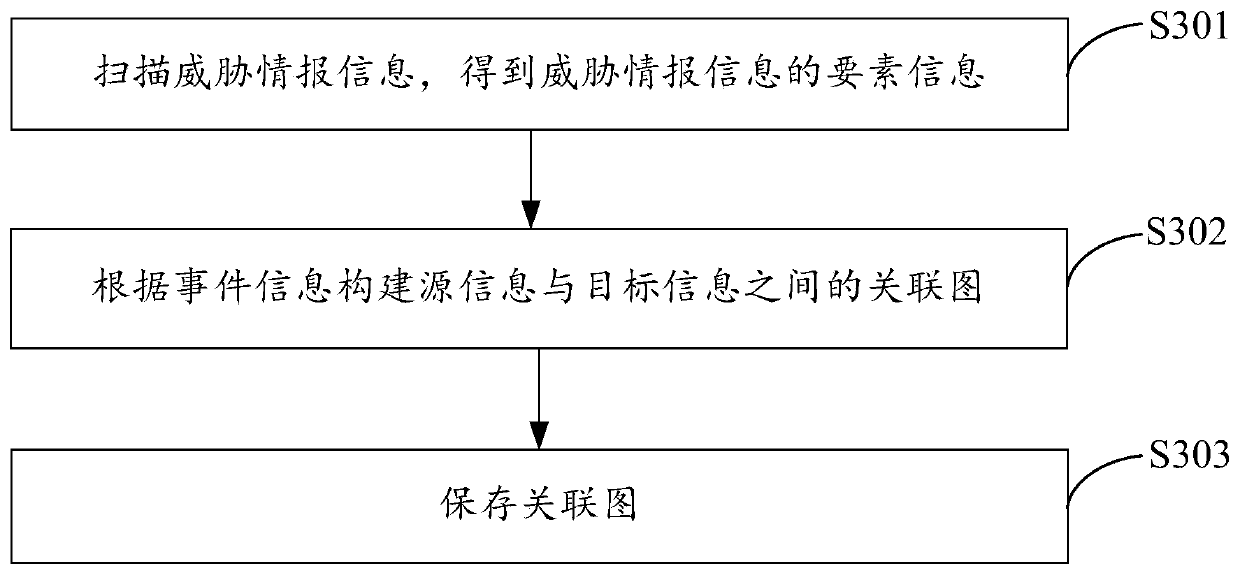
[0087] The processing module 21 is configured to process a plurality of threat intelligence information in the threat intelligence library to obtain a plurality of association graphs, and the association graph is used to represent the association relationship between the attacker and the attacked;
[0088] The sending module 22 is used to determine the target correlation graph corresponding to the target local map data engine in multiple correlation graphs, and send the target correlation graph to th...
Embodiment 3
[0106] An embodiment of the present invention provides an electronic device, referring to Figure 5 , the electronic device includes: a processor 30, a memory 31, a bus 32 and a communication interface 33, the processor 30, the communication interface 33 and the memory 31 are connected through the bus 32; the processor 30 is used to execute the executable module stored in the memory 31, For example a computer program. The processor implements the steps of the methods described in the method embodiments when the processor executes the program.
[0107] Wherein, the memory 31 may include a high-speed random access memory (RAM, Random Access Memory), and may also include a non-volatile memory (non-volatile memory), such as at least one disk memory. The communication connection between the system network element and at least one other network element is realized through at least one communication interface 33 (which may be wired or wireless), and the Internet, wide area network, ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com