Paillier encryption method based on cloud computing platform
A cloud computing platform and encryption method technology, applied in the field of information security, can solve problems such as speeding up the operation efficiency of Paillier encryption
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0047] The above solution will be further described below in conjunction with specific embodiments. It should be understood that these examples are used to illustrate the present invention and not to limit the scope of the present invention. The implementation conditions used in the examples can be further adjusted according to the conditions of specific manufacturers, and the implementation conditions not indicated are usually the conditions in routine experiments.
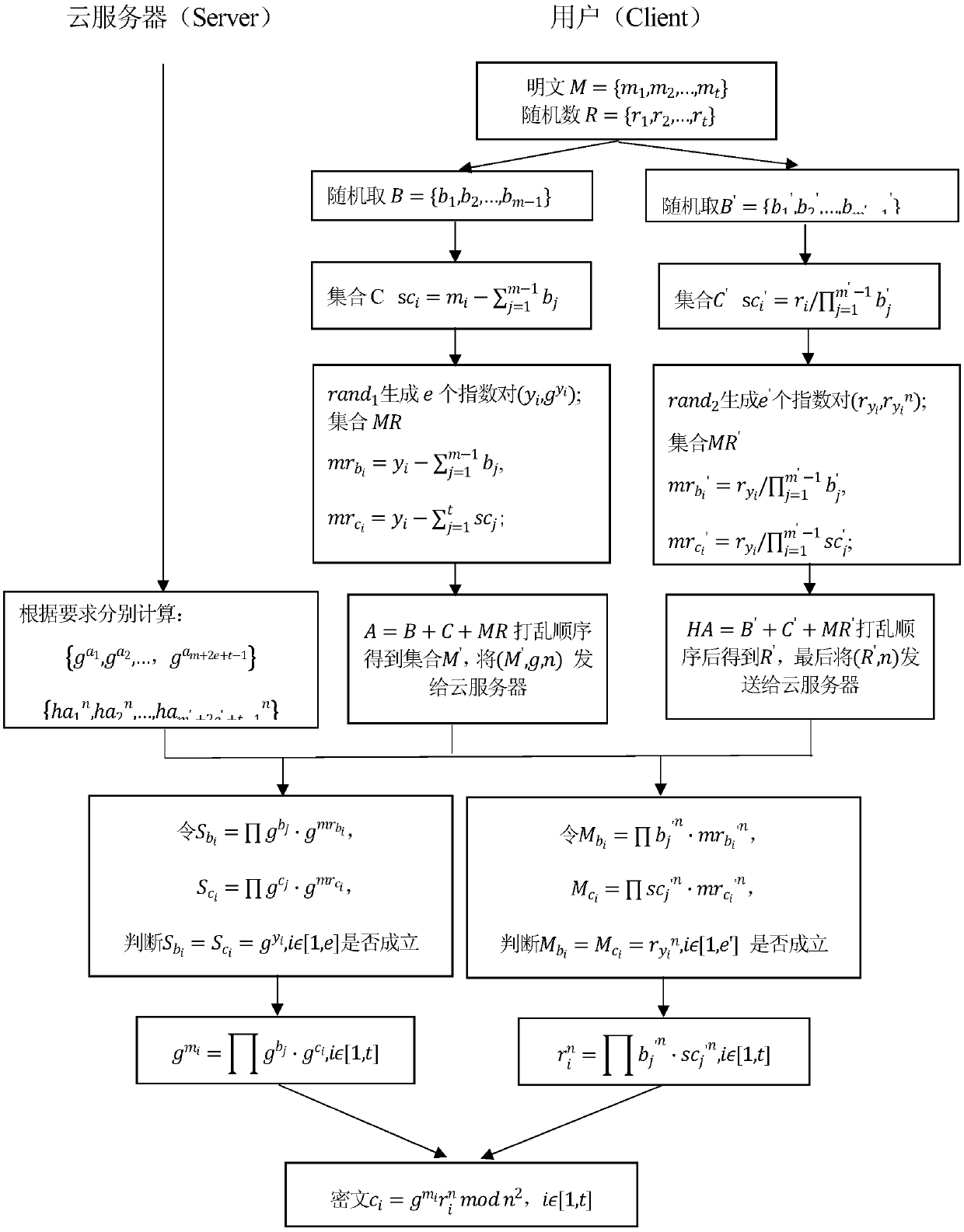
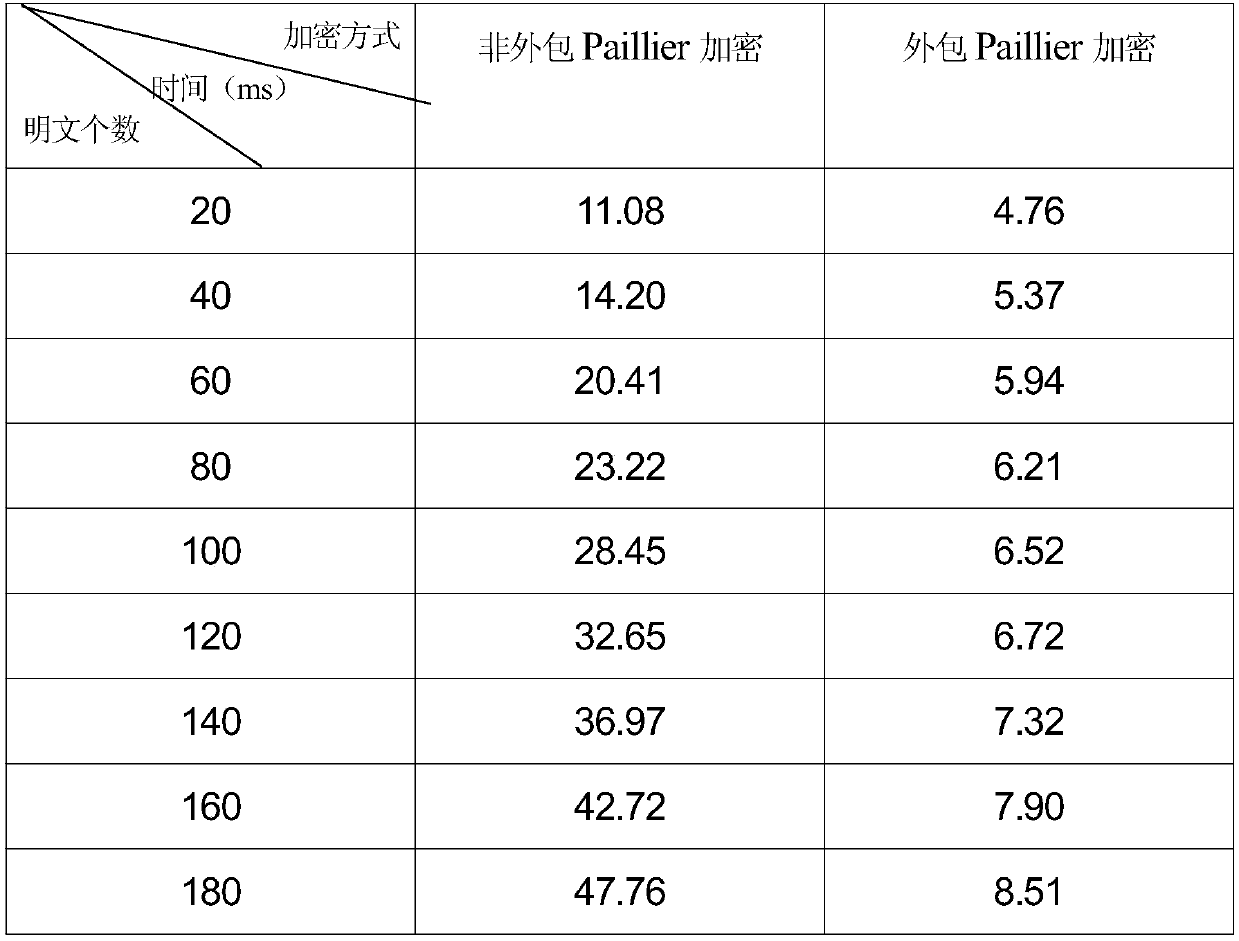
[0048] The secure cloud outsourced Paillier encryption algorithm idea of this embodiment is as follows: Steps 1 to 4, in order to use the secure outsourced modular exponentiation scheme, so that users can obtain the result of the modular exponentiation operation while ensuring that private data is not leaked, thereby speeding up the Paillier encryption speed.
[0049] Step 1: The encryptor randomly selects a random number set R of the same number according to the number of plaintexts, and then uses the plainte...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com