Systems and methods of command authorization
A command, unauthorized technology applied in the direction of memory systems, input/output processes for data processing, instruments, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
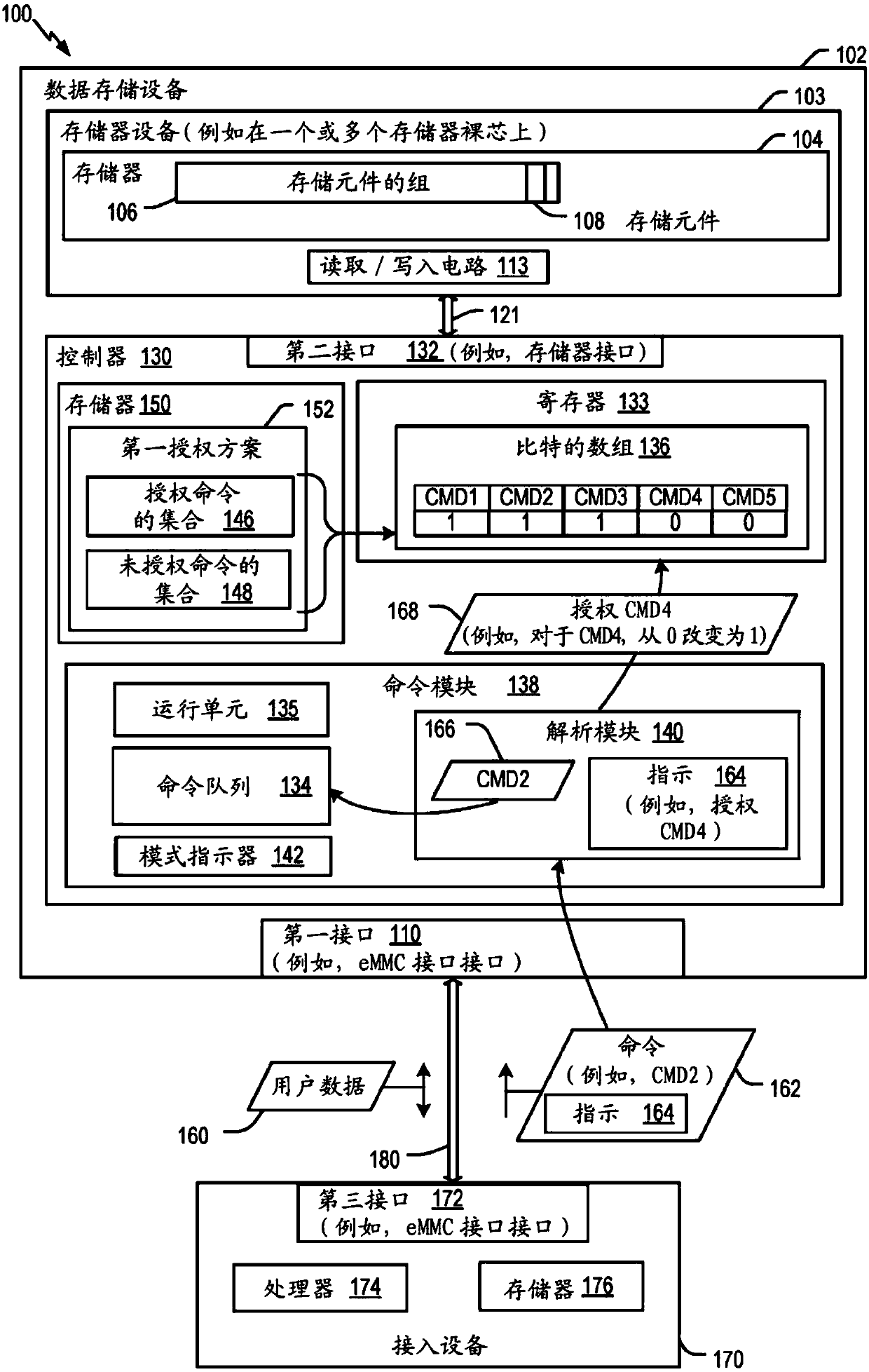
[0009] Certain aspects of the present disclosure are described below with reference to the accompanying drawings. In the description, common features are designated by common reference numbers. Although certain examples are described herein with reference to data storage devices, it should be understood that the techniques described herein may be applied to other implementations. Additionally, it should be understood that certain ordinal terms (eg, "first" or "second") may be provided for ease of reference and do not necessarily imply a physical characteristic or order. Accordingly, as used herein, ordinal number terms (e.g., "first," "second," "third," etc.) used to modify an element, such as structure, assembly, operation, etc., do not necessarily denote that the element is relative to another element. Priority or order of an element, but to distinguish that element from another element with the same name (but different use of ordinal terminology). Also, as used herein, th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com