Safety mode starting method and device
A technology of security mode and mode, which is applied in the field of communication, can solve the problem of enabling the security mode in scenarios without slicing networks, etc., and achieve the effects of reducing computing resource consumption, improving security processing efficiency, and improving efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
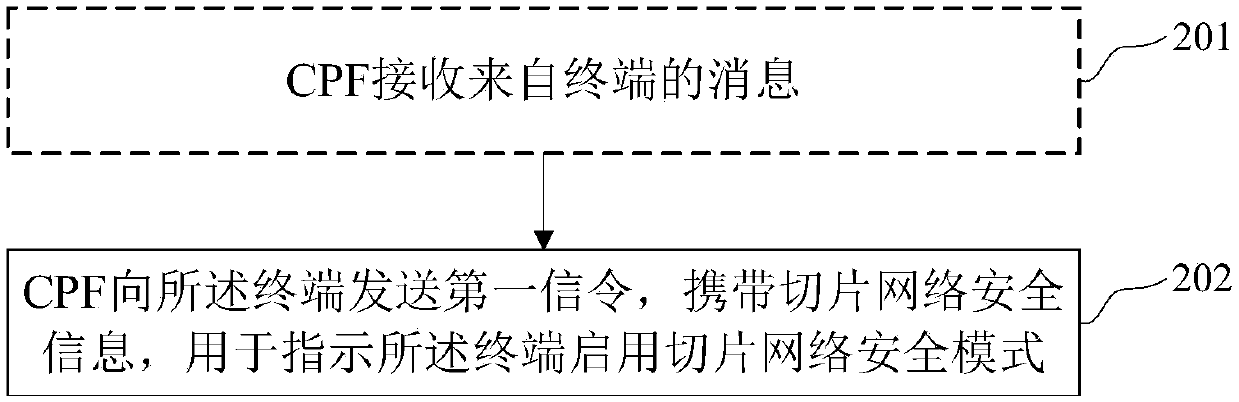
[0063] Such as figure 2 As shown, this embodiment provides a method for enabling a security mode, which is applied to a sliced network, and may include:
[0064] Step 202, the CPF sends a first signaling to the terminal, carrying slice network security information, for instructing the terminal to enable slice network security mode.
[0065] In some implementation manners, the slice network security information may include one or more of slice network identifier, slice network name, and slice network selection information; and include one of integrity algorithm information and confidentiality algorithm information.
[0066] In some implementation manners, the method in this embodiment may further include: the CPF receiving second signaling from the terminal, the slice network security information corresponding to a slice network; the CPF using the Processing the second signaling with a key related to the network slice.
[0067] In some implementation manners, the above-men...
Embodiment 2
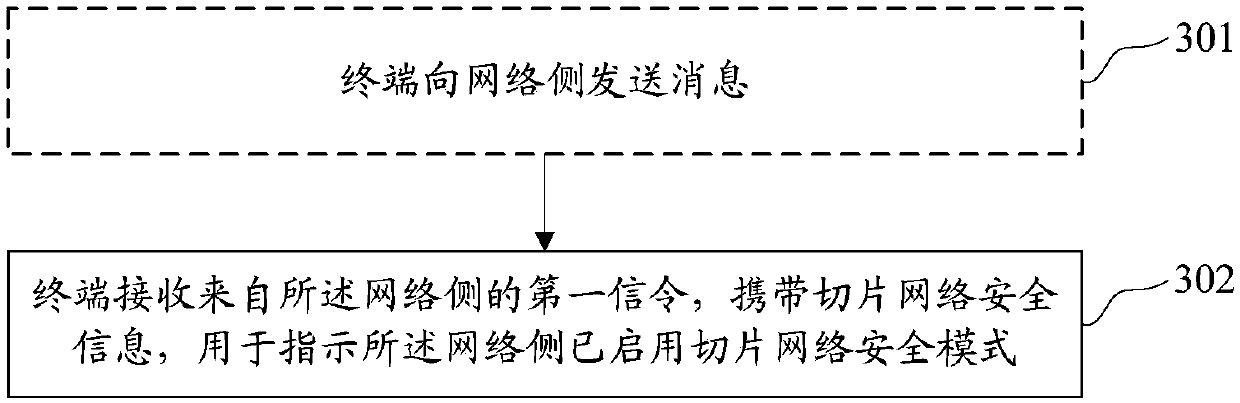
[0075] Such as image 3 As shown, this embodiment provides a method for enabling a security mode, which is applied to a sliced network, and may include:
[0076] Step 302, the terminal receives first signaling from the network side, carrying security information of the network slice, used to indicate that the security mode of the network slice has been enabled on the network side.
[0077] In some implementations, the slice network security information may include one or more of slice network identifiers, slice network names, and slice network selection information; and may include one of integrity algorithm information and confidentiality algorithm information .
[0078] In some implementation manners, the terminal may also send a second signaling to the network side, and the slice network security information corresponds to a slice network; the terminal may use a key related to the slice network to process all Describe the second signaling.
[0079] In some implementati...
Embodiment 3
[0087] Figure 4 It is a flow chart of the method for enabling the security mode in this embodiment, and the process includes:
[0088] In step 401, the terminal and the CPF complete access to the physical network.
[0089] Step 402, the terminal sends a signaling message to the network, the message carries user identification and signature information, and the message reaches the CPF.
[0090] For example, the subscriber identity may be an International Mobile Subscriber Identity (IMSI, International Mobile Subscriber Identity) or a temporary subscriber identity assigned by the network.
[0091] In this embodiment, the terminal carries signature information in the signaling message to protect the integrity of the message. Specifically, the manner in which the terminal carries the signature information is: calculating the signature information using a key not related to any slice network.
[0092] Step 403, the CPF receives the signaling message, and verifies the message, p...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com