JPEG image robustness steganography method based on serial concatenated code and DCT coefficient relative relationship
A serial cascading and relative relationship technology, applied in the field of information hiding, can solve the problem of secret information difficulty, etc., and achieve the effect of improving anti-detection, strong anti-detection, and anti-compression
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
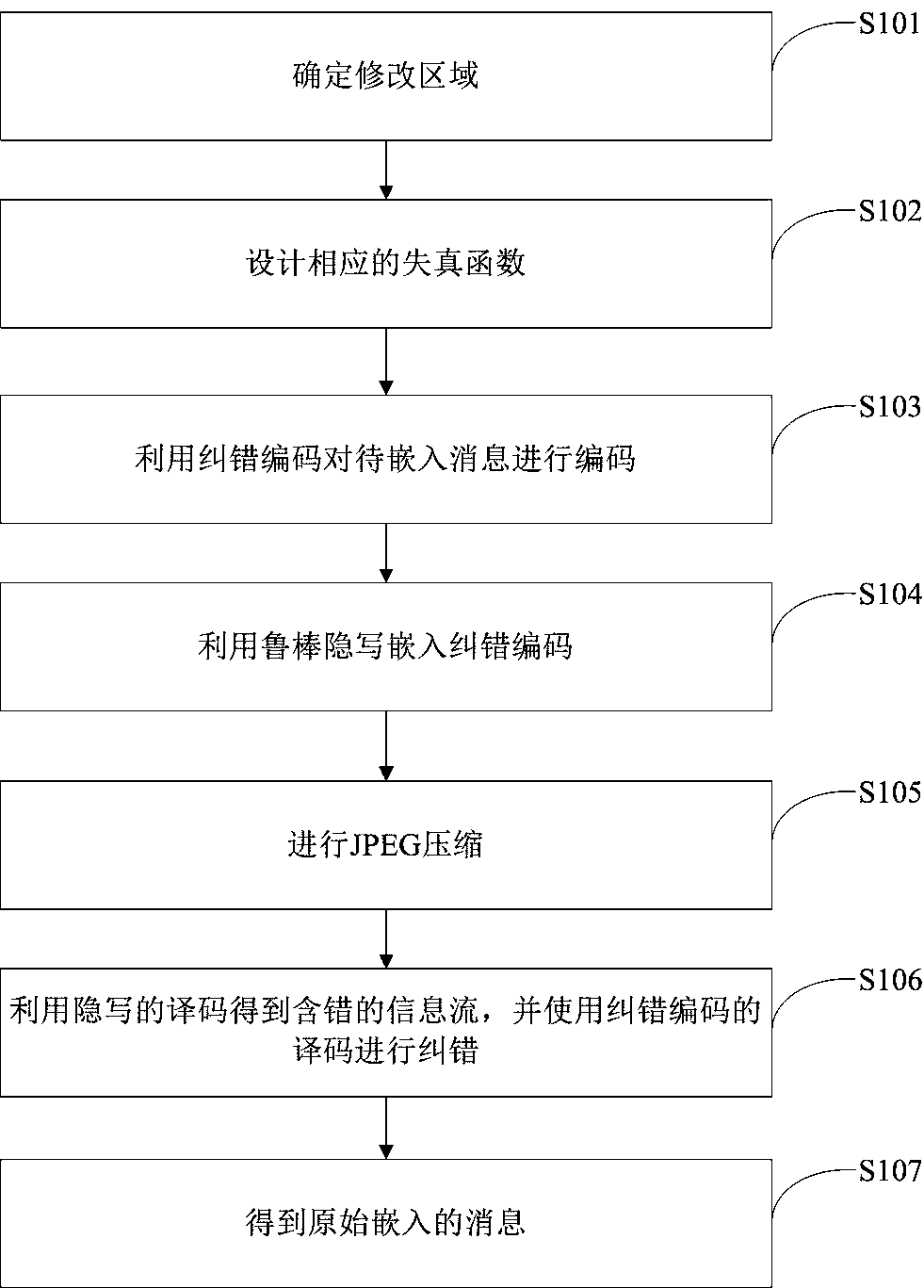
[0039] Such as figure 1 Shown, a kind of JPEG image robust steganography method based on serial concatenated code and DCT coefficient relative relation of the present invention comprises the following steps:
[0040] Step S101: Determine the modification area;
[0041] Step S102: designing a corresponding distortion function;
[0042] Step S103: Encoding the message to be embedded by using error correction coding;
[0043] Step S104: using steganography to embed error correction codes;
[0044] Step S105: performing JPEG compression;
[0045] Step S106: Obtain an error-containing information stream by decoding the error-correcting code, and perform error correction;
[0046] Step S107: Get the original embedded message.
Embodiment 2
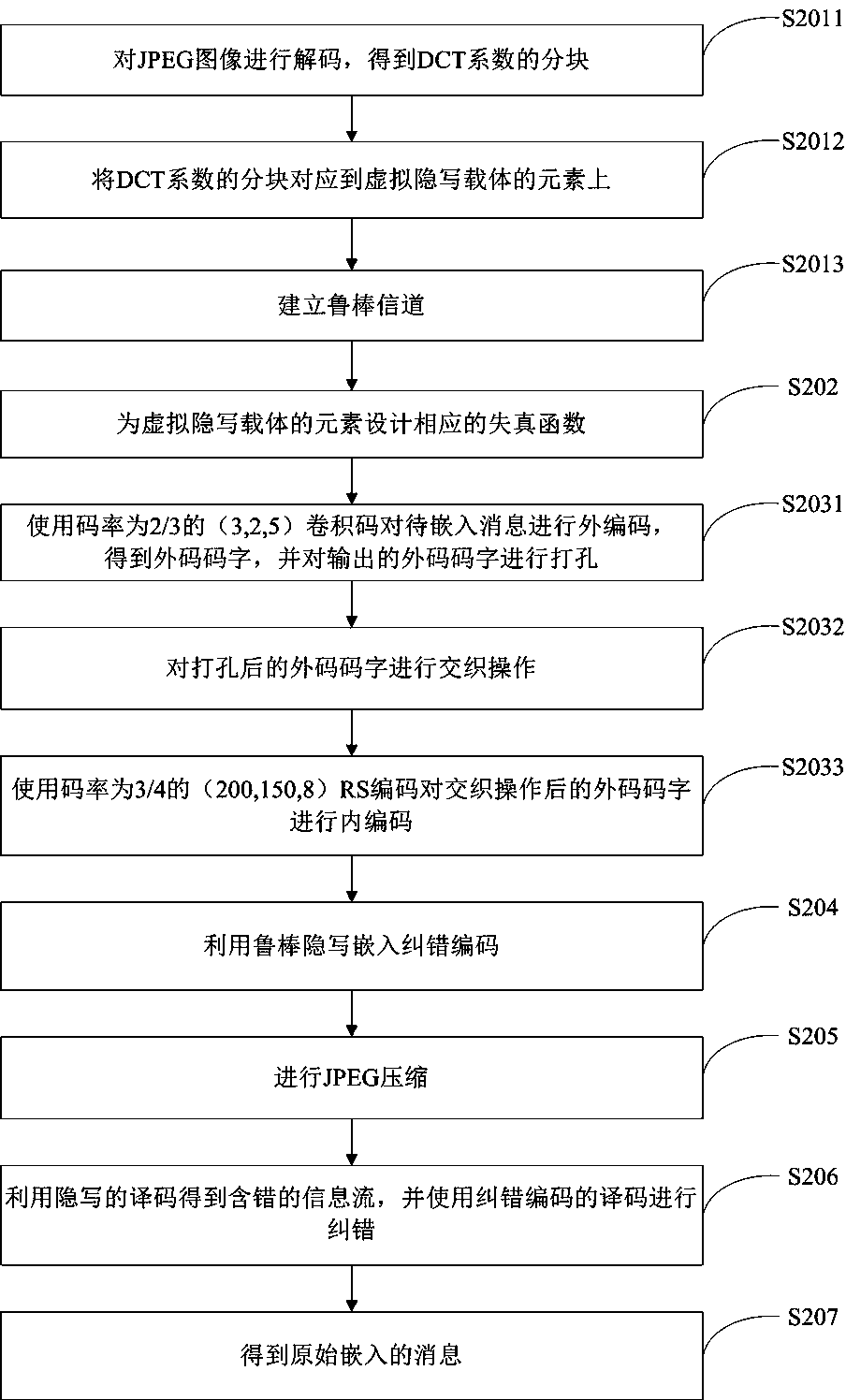
[0048] Such as figure 2 As shown, another kind of JPEG image robust steganography method based on serial concatenated code and DCT coefficient relative relation of the present invention comprises the following steps:
[0049] Step S201: Determine the modification area, including:
[0050] Step S2011: Decode the JPEG image I to obtain a series of 8×8 blocks D of quantized and rounded DCT coefficients D k ={D k (i), i=1,2,...,64,} Among them, k=1,2,...,B, B is the total number of blocks in the image 8×8 blocks, D k (i) represents the i-th coefficient in the k-th quantized DCT block;
[0051] Step S2012: Using DCT coefficient D k (i) DCT coefficients in the same block as the adjacent block average The relative relationship of the four adjacent DCT coefficients corresponds to a length l 1 virtual steganographic carrier element x on j On, 1≤j≤l 1 ,satisfy:
[0052]
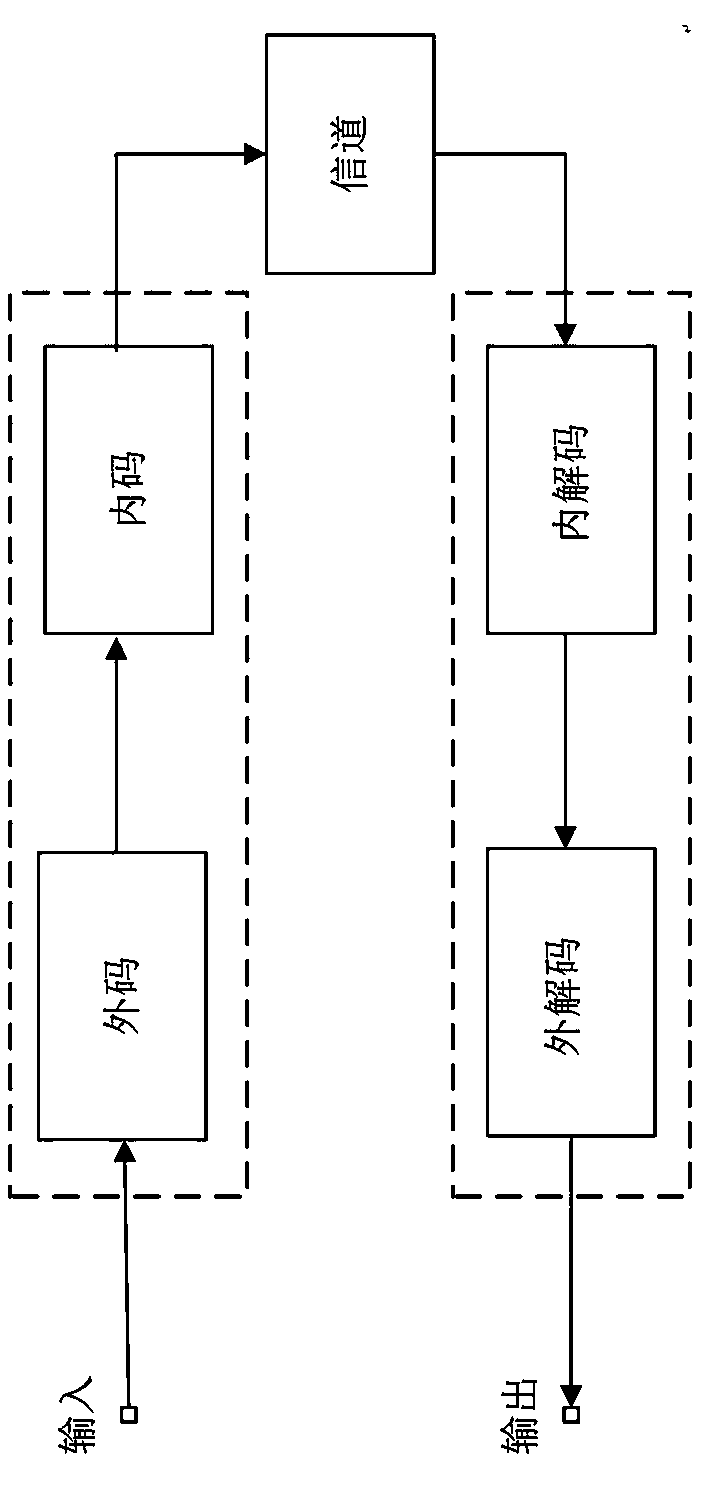
[0053] Step S2013: Establish a robust channel:
[0054] Establish a robust channel based on X a...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com