Executable file data anti-leakage scanning method, system and gateway
A technology for executing files and scanning methods, applied in the field of data security, can solve problems such as data leakage, inability to determine the sensitive data of executable files, and inability to identify the content of executable files, so as to achieve convenient operation, reduce the risk of data leakage, and facilitate The effect of promotion
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
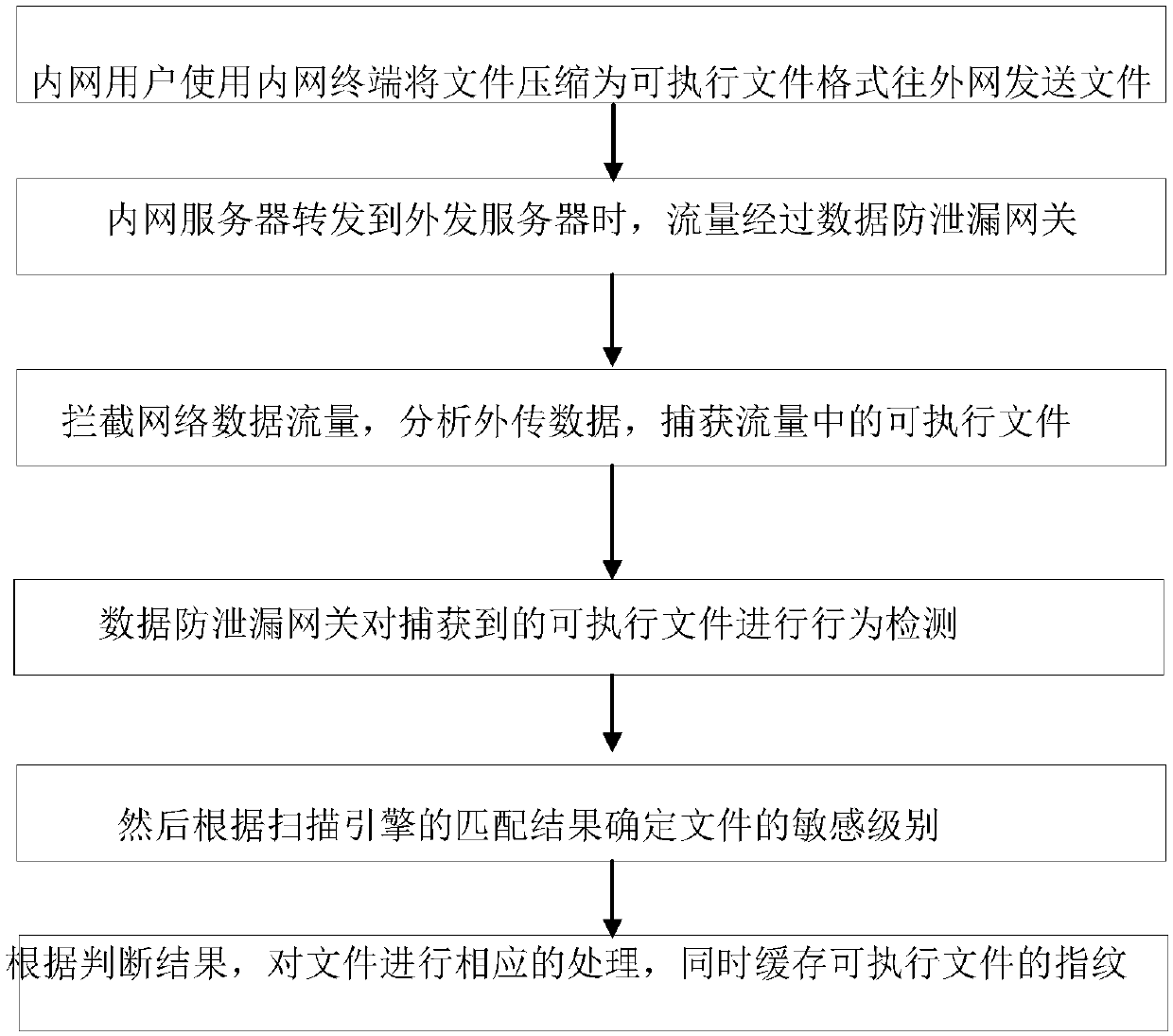
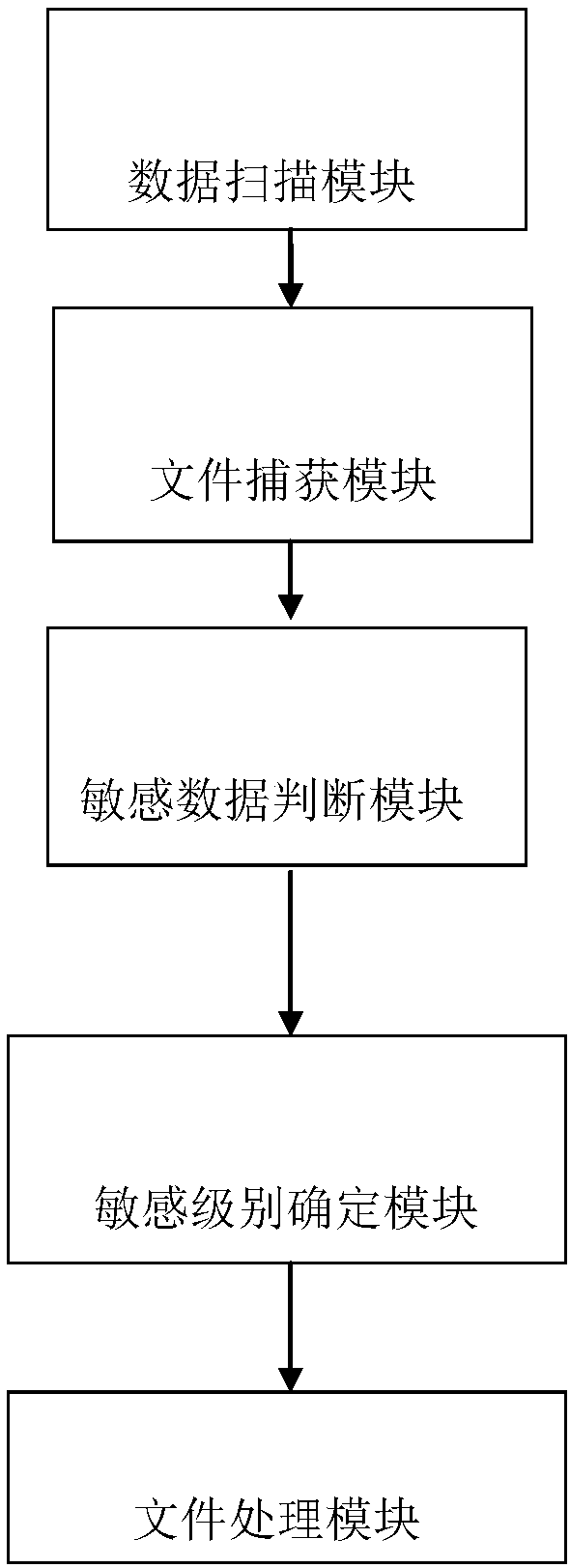
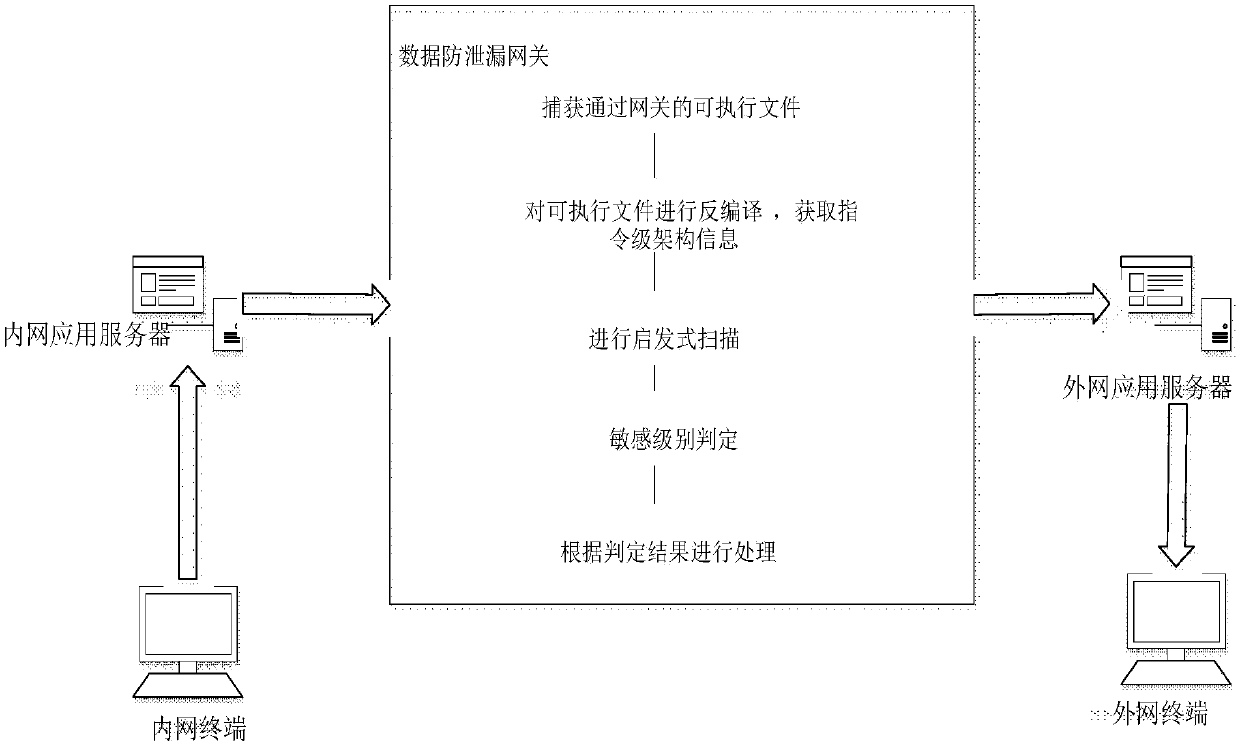
[0033] Data leakage prevention: refers to the content-centric control method, which generates fingerprint records for the content of files, and controls files through terminals, gateways, and storage.
[0034] Executable file: refers to a file that can be loaded and executed by the operating system. Under different operating systems, executable files are presented in different ways. Under the windows operating system, the executable program can be .exe file, .sys file, .com and other file types, while under different operating systems such as Linux, Unix and IOS, it will be other different files.
[0035] Heuristic: Refers to the ability of self-discovery or the knowledge and skills of using a certain method or method to judge mistakes. It is the antivirus software that can analyze whether the logical structure of the file code contains the characteristics of a malicious program, or judge whether it has malicious behavior by proactively executing the code in a virtual safe env...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com