User safety verification method and system
A security verification and user technology, applied in the field of user security verification methods and systems, can solve problems such as insufficient understanding of protection and safety precautions, interns entering illegal organizations by mistake, and lack of safety supervision and protection mechanisms
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
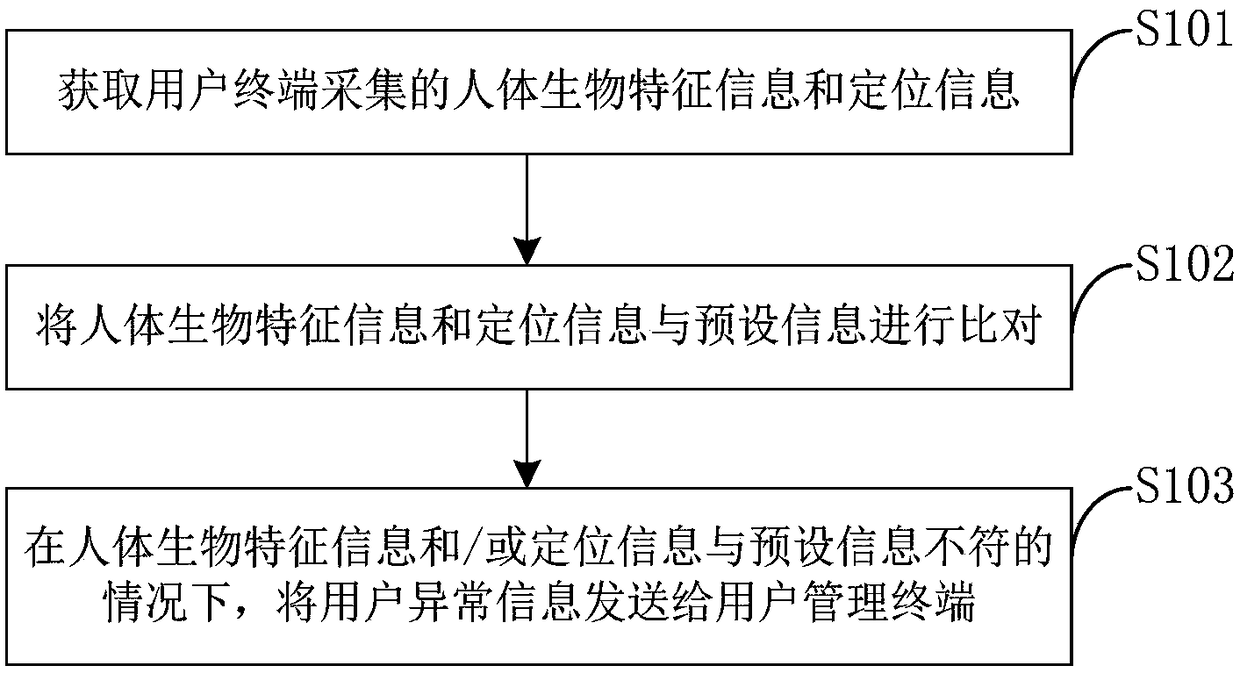
[0045] figure 1 It is a schematic diagram of a user security verification method provided by an embodiment of the present invention.
[0046] This embodiment provides a user security verification method, and the execution subject may be a server, such as figure 1 As shown, the method includes the following steps:
[0047] Step S101, acquiring human body biometric information and location information collected by the user terminal;
[0048] Specifically, the biometric information of a human body includes voiceprint information, fingerprint information, or facial feature information. The user enters the voiceprint, fingerprint or scans the face through the user terminal, so that the user terminal collects the user's biometric information, and the server obtains the biometric information collected by the user terminal, and obtains the positioning information through the GPS positioning system of the user terminal. In order to know the location of the user.
[0049] In order t...
Embodiment 2
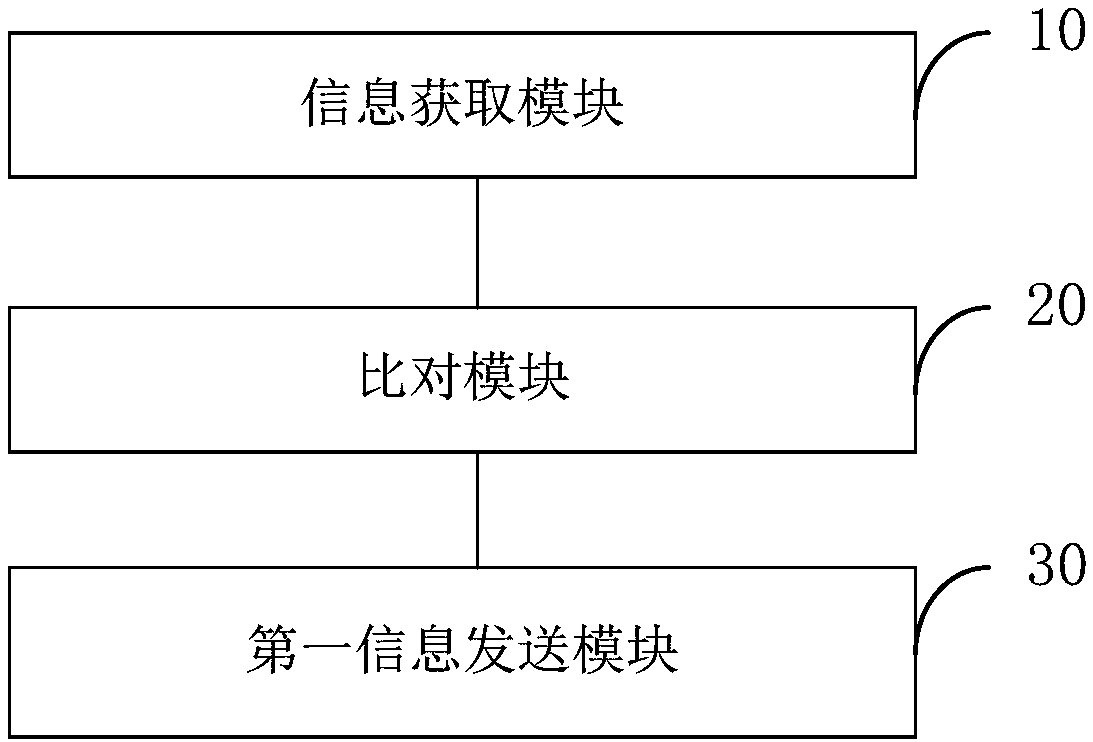
[0064] image 3 It is a schematic diagram of the user security verification system provided by the embodiment of the present invention.
[0065] This embodiment provides a user security verification system, such as image 3 As shown, the system includes an information acquisition module 10, a comparison module 20 and a first information sending module 30:
[0066] An information acquisition module 10, configured to acquire human body biometric information and positioning information collected by a user terminal;
[0067] Specifically, the biometric information of a human body includes voiceprint information, fingerprint information, or facial feature information.
[0068] A comparison module 20, configured to compare human body biometric information and location information with preset information;
[0069] The first information sending module 30 is configured to send user abnormality information to the second receiving unit of the user management terminal when the biometri...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com