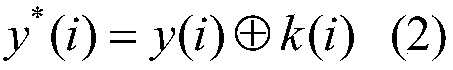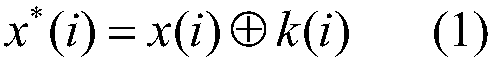Quantum method for safely calculating Hamming distance based on Bell state
A Hamming distance and security technology, applied in the field of modern cryptography, can solve the problems of computational complexity, quantum computer difficulty, no longer security, and inability to resist quantum computer attacks, etc., to achieve unconditional privacy, simplified operation, and realizability strong effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0046] In this embodiment, a quantum method for safely calculating the Hamming distance based on the Bell state is that there are two participants Alice and Bob and an agent Charlie, assuming that the agent Charlie does not conspire with any participant; the participant Alice has a A private bit string X of length n, the bit string X is defined as X={x(1),x(2),...,x(i),...,x(n)}, where x (i) represents the i-th component of the bit string X, i=1,2,...,n; the participant Bob has a private bit string Y of length n, and the bit string Y is defined as Y={y (1), y(2),...,y(i),...,y(n)}, wherein, y(i) represents the i-th component in the bit string Y, i=1,2 ,...,n; the quantum method is carried out as follows:
[0047] Step 1. Participant Alice and participant Bob call the quantum key distribution QKD protocol to share an n-bit key K. Participant Alice uses formula (1) to calculate the i-th component x in the ciphertext vector of the bit string X * (i), so as to obtain the ciphert...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com