Method and system for remotely upgrading device
A technology for remote upgrade and equipment, applied in transmission system and key distribution, can solve the security problems of remote upgrade of equipment and other problems, and achieve the effect of reducing the risk of key leakage and improving security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
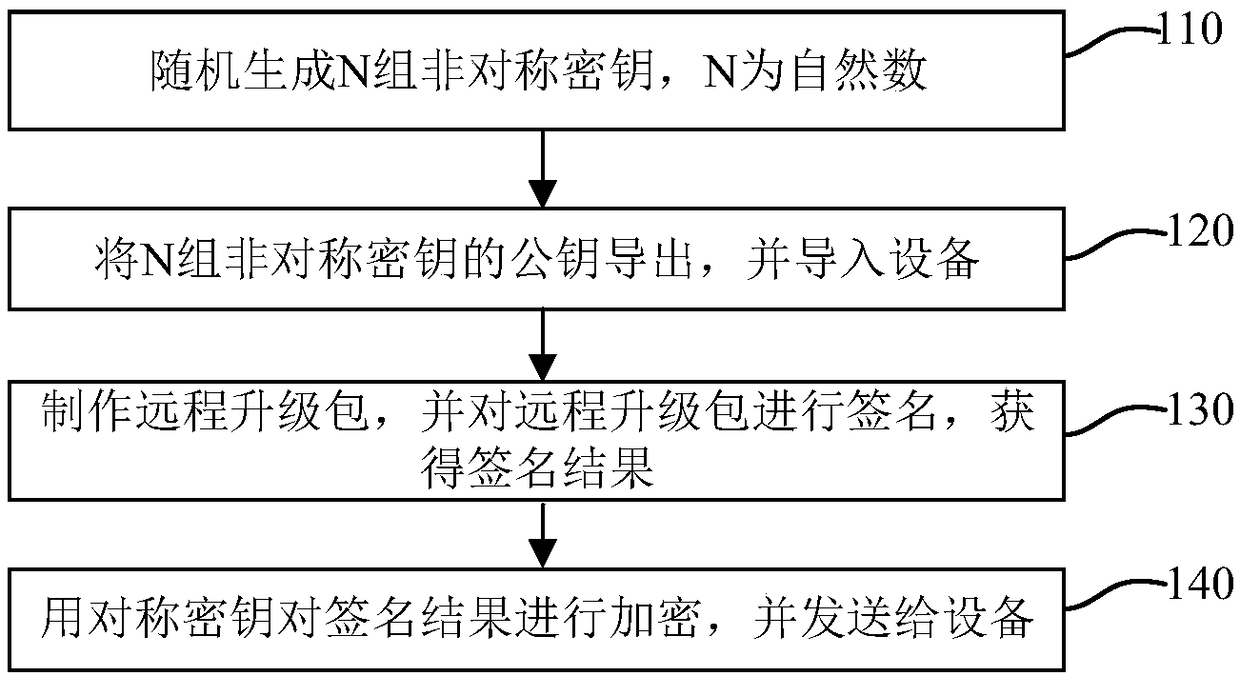
[0027] figure 1 It is a flow chart of the method for remotely upgrading equipment in the present application. Exemplarily, the device remote upgrade method is applicable to an encryption machine or other equipment with the encryption machine function. The private key of the asymmetric key generated by the encryption machine is placed in the safe computer room, and the private key cannot be exported, which ensures the safety of making the upgrade package.
[0028] Such as figure 1 As shown, the method for remotely upgrading equipment of the present application includes: randomly generating N groups of asymmetric keys, where N is a natural number (110); deriving the public keys of N groups of asymmetric keys and importing them into the device (120); making a remote Upgrade the package, and sign the remote upgrade package to obtain the signature result (130); encrypt the signature result with a symmetric key, and send it to the device (140).
[0029] Specifically, in step 120,...
Embodiment 2
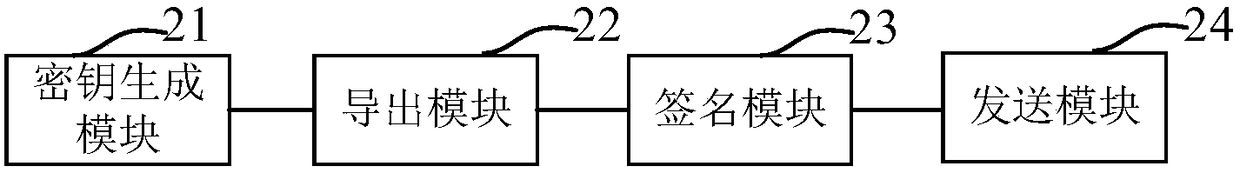
[0038] figure 2 It is a schematic structural diagram of the system for remotely upgrading equipment in this application. It is applicable to the method for remotely upgrading equipment described in Embodiment 1. Such as figure 2 As shown, the remote upgrade system of the equipment of the present application includes:
[0039] Key generation module 21, for randomly generating N groups of asymmetric keys, N is a natural number;
[0040] The export module 22 is used to export the public keys of N groups of asymmetric keys and import them into the device;
[0041] The signature module 23 is used to make a remote upgrade package, and sign the remote upgrade package to obtain a signature result;
[0042] The sending module 24 is configured to encrypt the signature result with a symmetric key and send it to the device.
[0043] Wherein, the sending module 24 is further configured to send the encrypted data of the serial number of the asymmetric key used to sign the remote upgr...
Embodiment 3
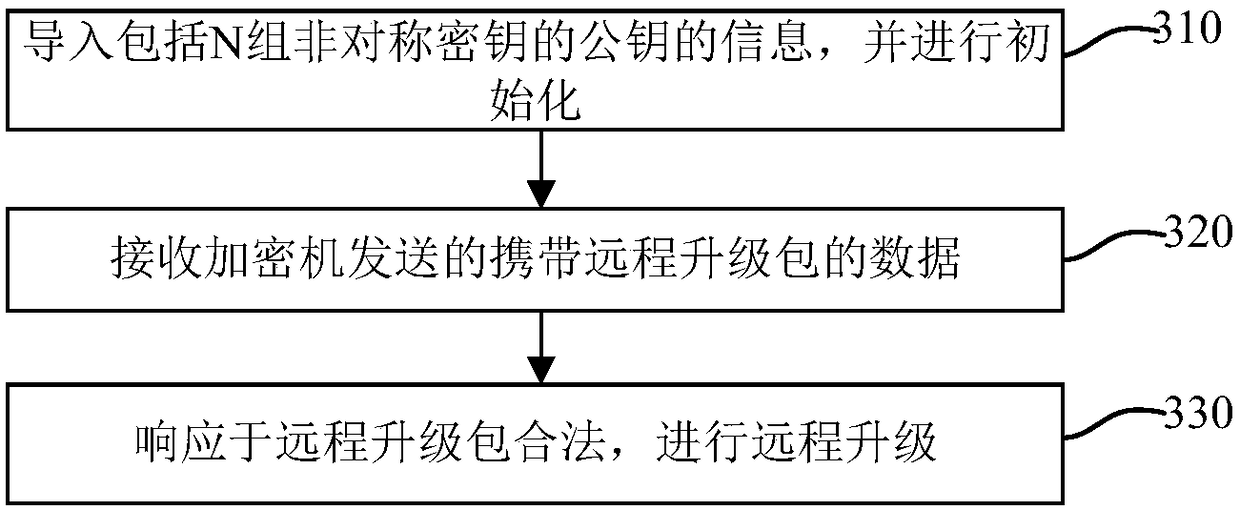
[0046] image 3 It is a flow chart of another method for remotely upgrading equipment of the present application. Exemplarily, the device remote upgrade method is applicable to application devices that need to be upgraded. The application device receives the data sent by the encryption machine to complete the device upgrade.
[0047] Such as image 3 As shown, the method for remotely upgrading equipment of the present application includes: importing information including public keys of N groups of asymmetric keys, and performing initialization (310); receiving data carrying remote upgrade packages sent by an encryption machine (320); responding Since the remote upgrade package is legal, perform remote upgrade (330).
[0048] Specifically, in step 310, the imported information also includes: the same symmetric key as that of the encryption machine, serial numbers of N groups of asymmetric keys, and device parameters. Among them, the device parameters include: certificates, ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com