Quantum key chip issuing method, quantum key chip application method, issuing platform and quantum key application system
A quantum key and key chip technology, applied in the field of application methods, distribution platforms and systems, and quantum key chip distribution methods, can solve problems such as security network cracking
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
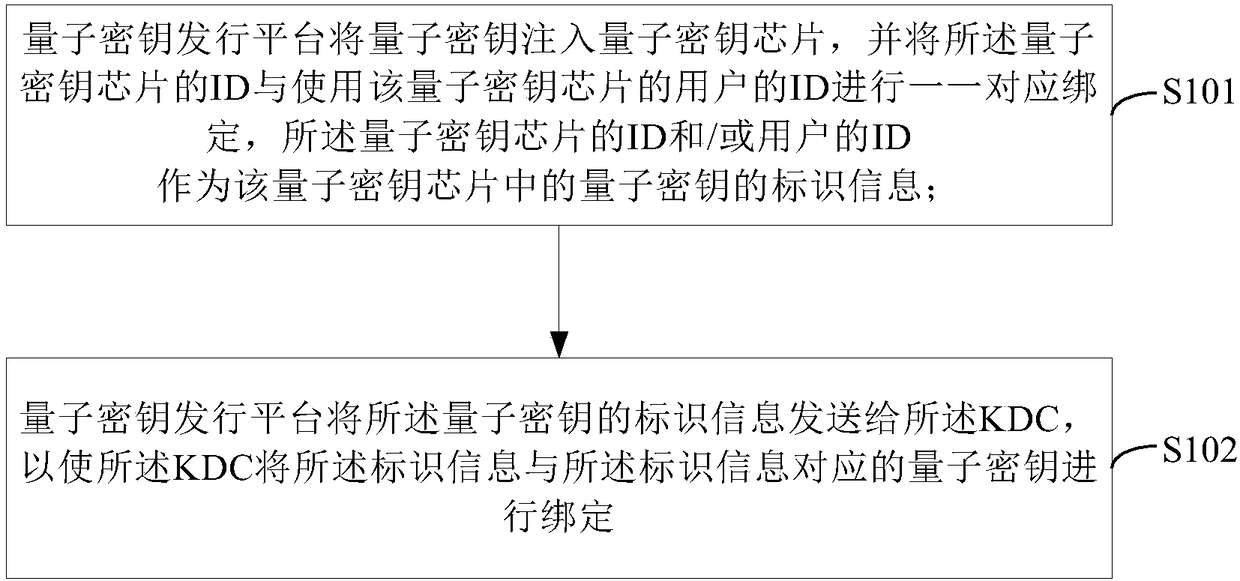
[0085] see figure 1 , which is a flow chart of Embodiment 1 of the quantum key chip issuance method provided by the present invention.
[0086] The issuing method of the quantum key chip provided in this embodiment includes:
[0087] S101: The quantum key issuance platform injects the quantum key into the quantum key chip, and binds the ID of the quantum key chip with the ID of the user using the quantum key chip one by one, and the quantum key The ID of the chip and / or the ID of the user are used as the identification information of the quantum key in the quantum key chip; Obtained through negotiation;
[0088] It can be understood that the quantum key negotiated between the quantum key issuing platform and the KDC is a shared quantum key, that is, the quantum key issuing platform and the KDC have the same number of quantum keys with the same content.
[0089] The quantum key chip is finally issued to the user. Therefore, the quantum key chip is in one-to-one correspondenc...
Embodiment 2
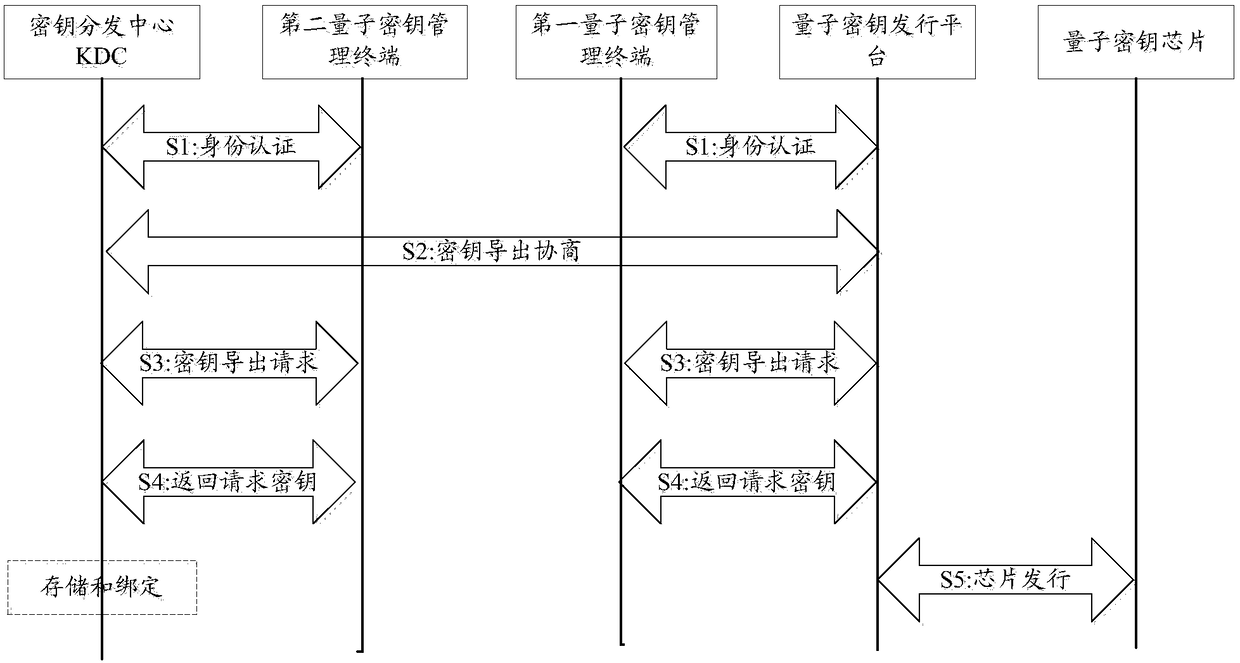
[0095] see figure 2 , which is a signaling diagram of the issuing method of the quantum key chip provided by the present invention.
[0096] It should be noted that the quantum key issuance platform and KDC can correspond to the same quantum key management terminal, or they can correspond to different quantum key management terminals. The following is an example of corresponding to different quantum key management terminals. When the quantum key issuance platform and KDC correspond to the same quantum key management terminal, the principle is the same.
[0097]S1: The quantum key issuance platform establishes a corresponding relationship with the first quantum key management terminal connected to itself, and the key distribution center KDC establishes a corresponding relationship with the second quantum key management terminal connected to itself; use the established Corresponding relationship, the KDC and the quantum key issuance platform perform identity authentication to ...
Embodiment 1
[0123] see Figure 4 , which is a flow chart of Embodiment 1 of the application method of the quantum key chip provided by the present invention.
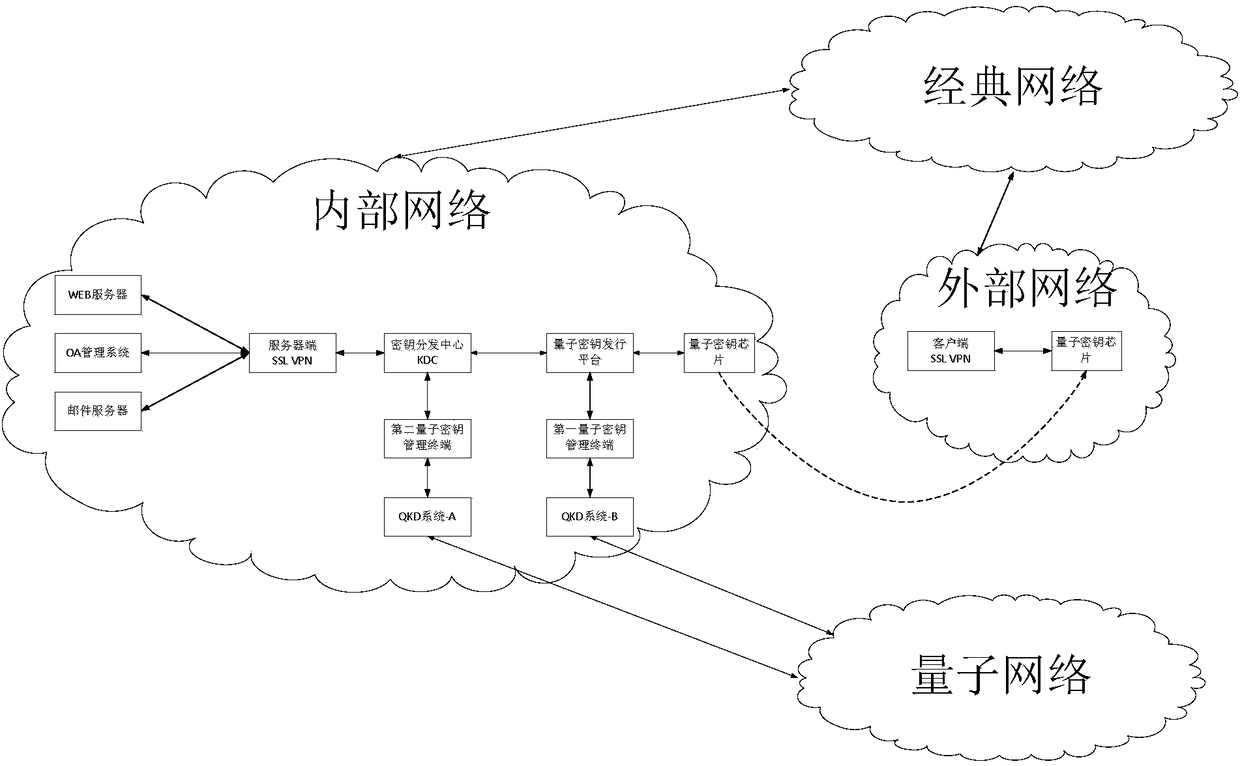
[0124] The application method of the quantum key chip provided in this embodiment is applied to a secure socket layer virtual private network SSLVPN communication system, and the system includes: client SSL VPN, server SSL VPN, key distribution center KDC and quantum key chip;
[0125] When the quantum key negotiation between the client SSL VPN and the server SSL VPN is normal, the method includes:
[0126] S401: The client SSL VPN obtains a first random number from the quantum key chip, sends the first random number to the server-side SSL VPN, and receives the first random number sent by the server-side SSL VPN. Two random numbers;
[0127] S402: The client-side SSL VPN negotiates with the server-side SSL VPN to use the quantum key in the quantum key chip as a pre-master key, and use the quantum key in the quantum key chip as a ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com