Method for defending inaudible instruction to control voice assistant based on machine learning
A technology of machine learning and command control, which is applied in the security field of artificial intelligence voice assistants, and can solve problems such as long cycle, high difficulty, reducing screen brightness or volume, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0059] Preferred embodiments of the present invention will be described in detail below.
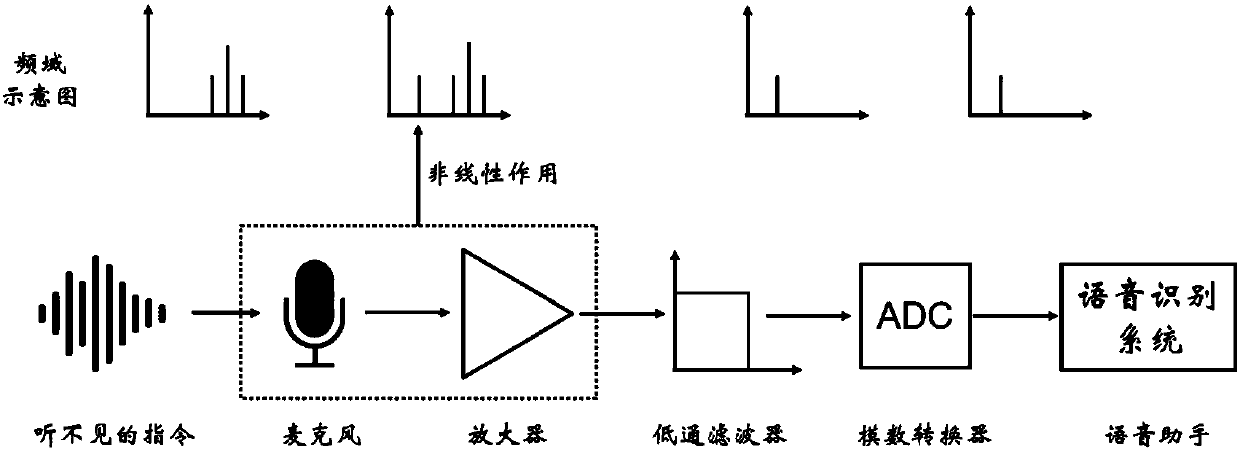
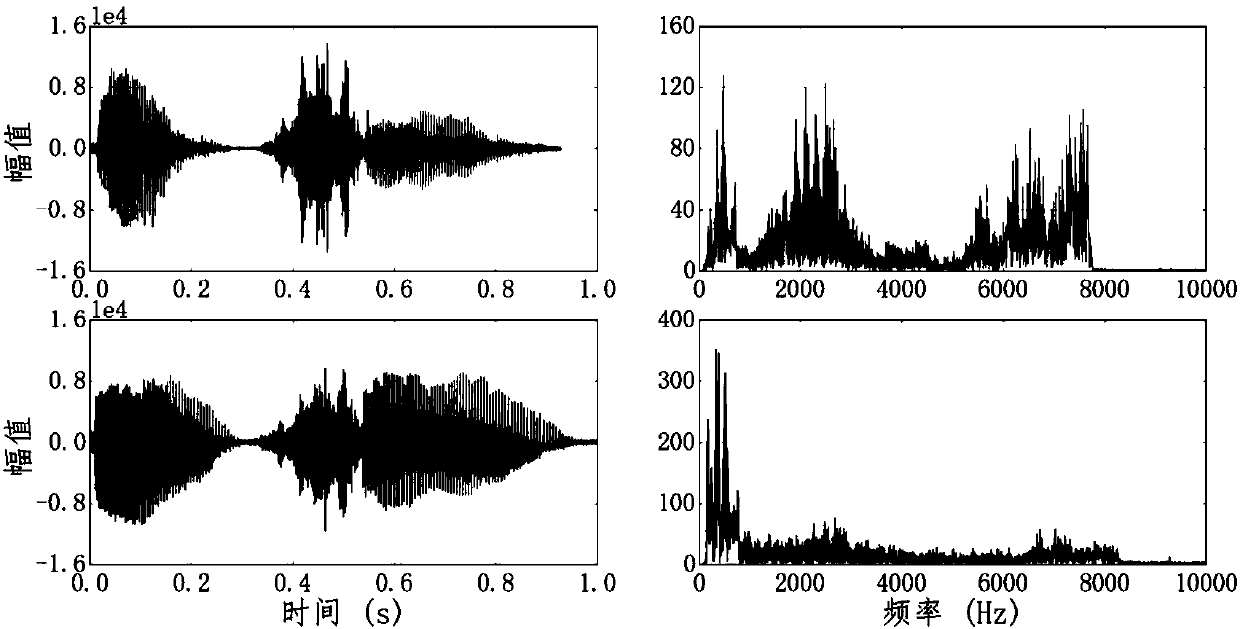
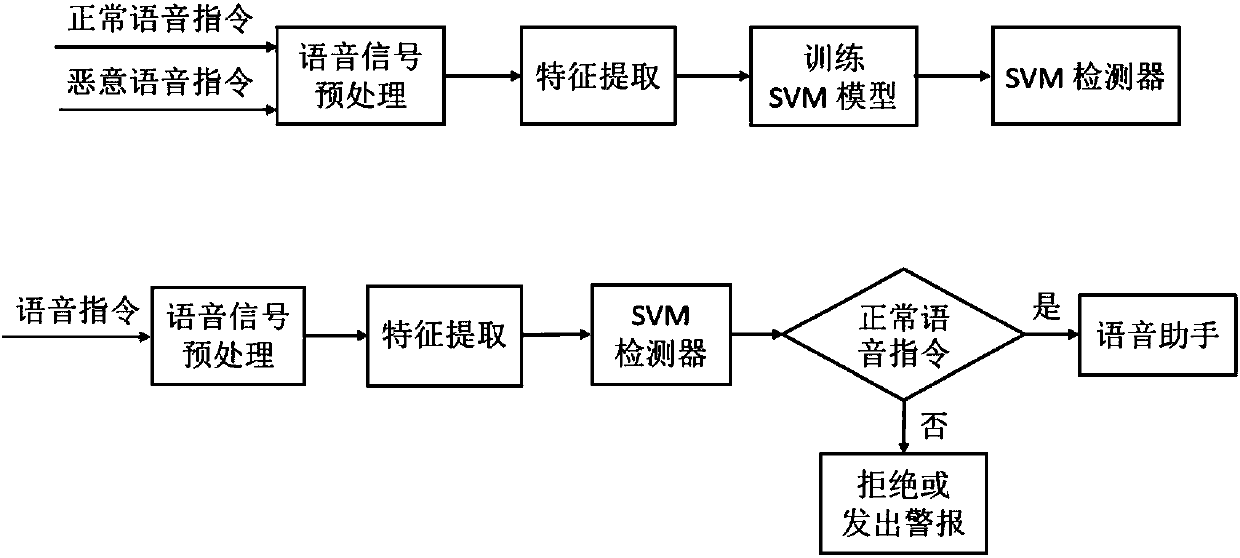
[0060] figure 2 It is a comparison diagram of normal voice signal and malicious voice signal in the time-frequency domain; through figure 2 , it can be found that there is a significant difference in the high frequency band between the ordinary voice signal recorded by the mobile phone and the malicious signal (the demodulated signal). Therefore, malicious voice commands can be identified by machine learning algorithms. Such as image 3 with 4 As shown, the present invention provides targeted defense against "dolphin sound attack", and can detect the silent voice command of "dolphin sound attack", thereby fundamentally solving the possibility of voice assistants and smart devices being controlled by silent voice commands.
[0061] The following embodiment is a method for controlling a voice assistant based on machine learning defense against silent commands, and the defense device ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com