Secure call connection method
A technology for call connection and security, applied in security devices, computer security devices, telephone communications, etc., can solve the problems of poor use effect, privacy accident, public call security, etc., and achieve excellent use effect and protect information security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0026] The present invention will be further illustrated below in conjunction with specific embodiments. The present embodiment is implemented on the premise of the technical solution of the present invention. It should be understood that these embodiments are only used to illustrate the present invention and not to limit the scope of the present invention.
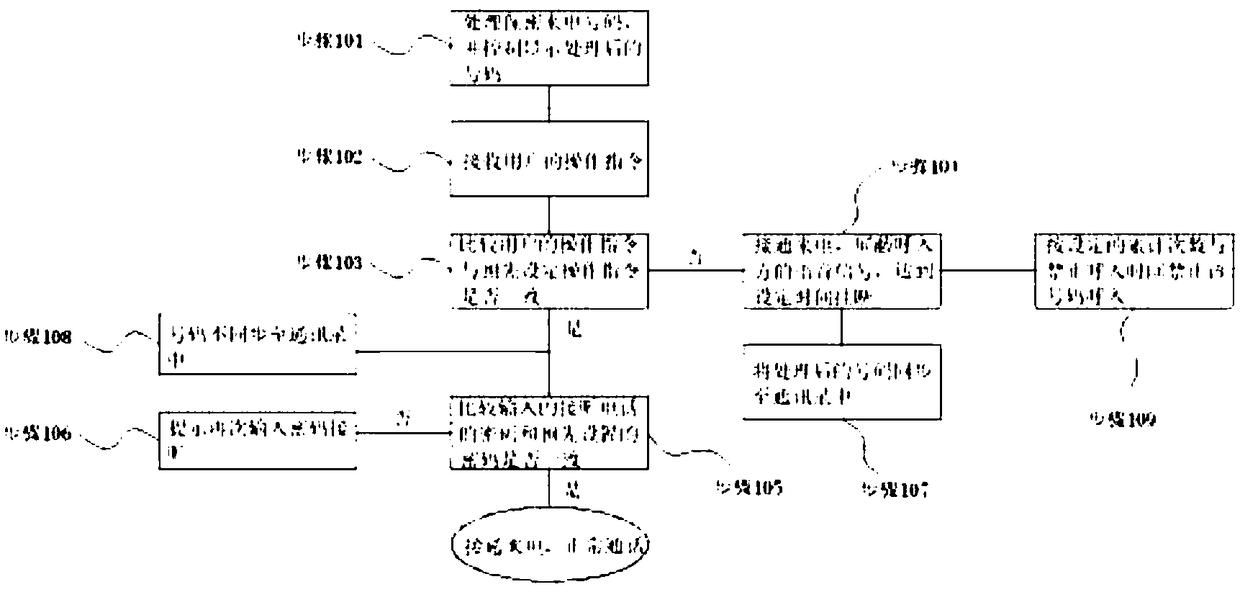
[0027] figure 1 This is a flowchart of a method for connecting a secure call according to an embodiment of the present invention.
[0028] like figure 1 As shown, an embodiment of the present invention is a method for connecting a secure call, which is implemented based on a smart phone.
[0029] In step 101, the number that needs to make a secure call is preset into the secret list, and when a number in the secret list calls, the mobile phone first processes the caller number. The digit is randomly changed to other digits, and the changed caller ID is displayed as the caller ID. Only the changed number is displayed in...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com