Patents
Literature
31results about How to "Avoid disclosure of confidential information" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
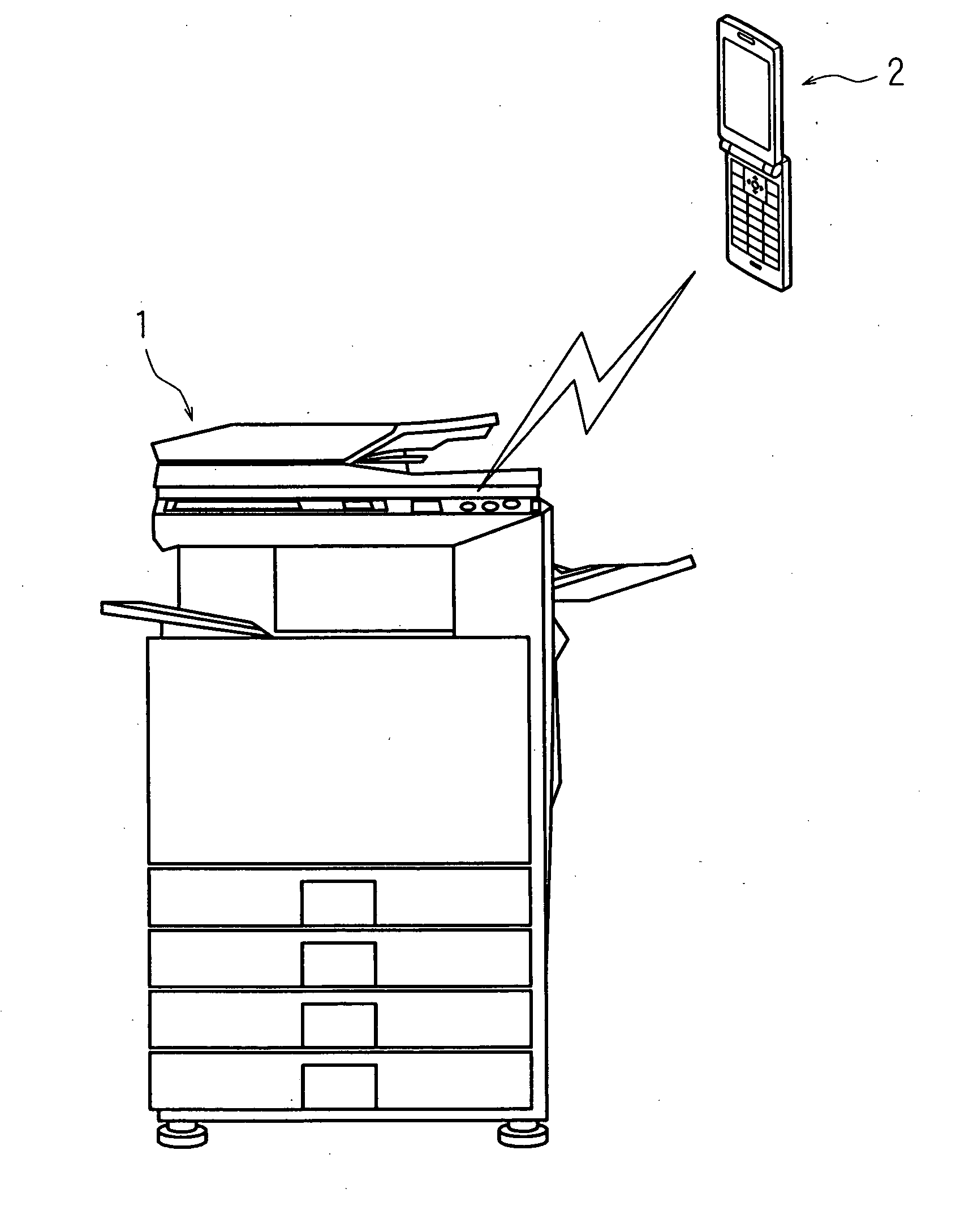
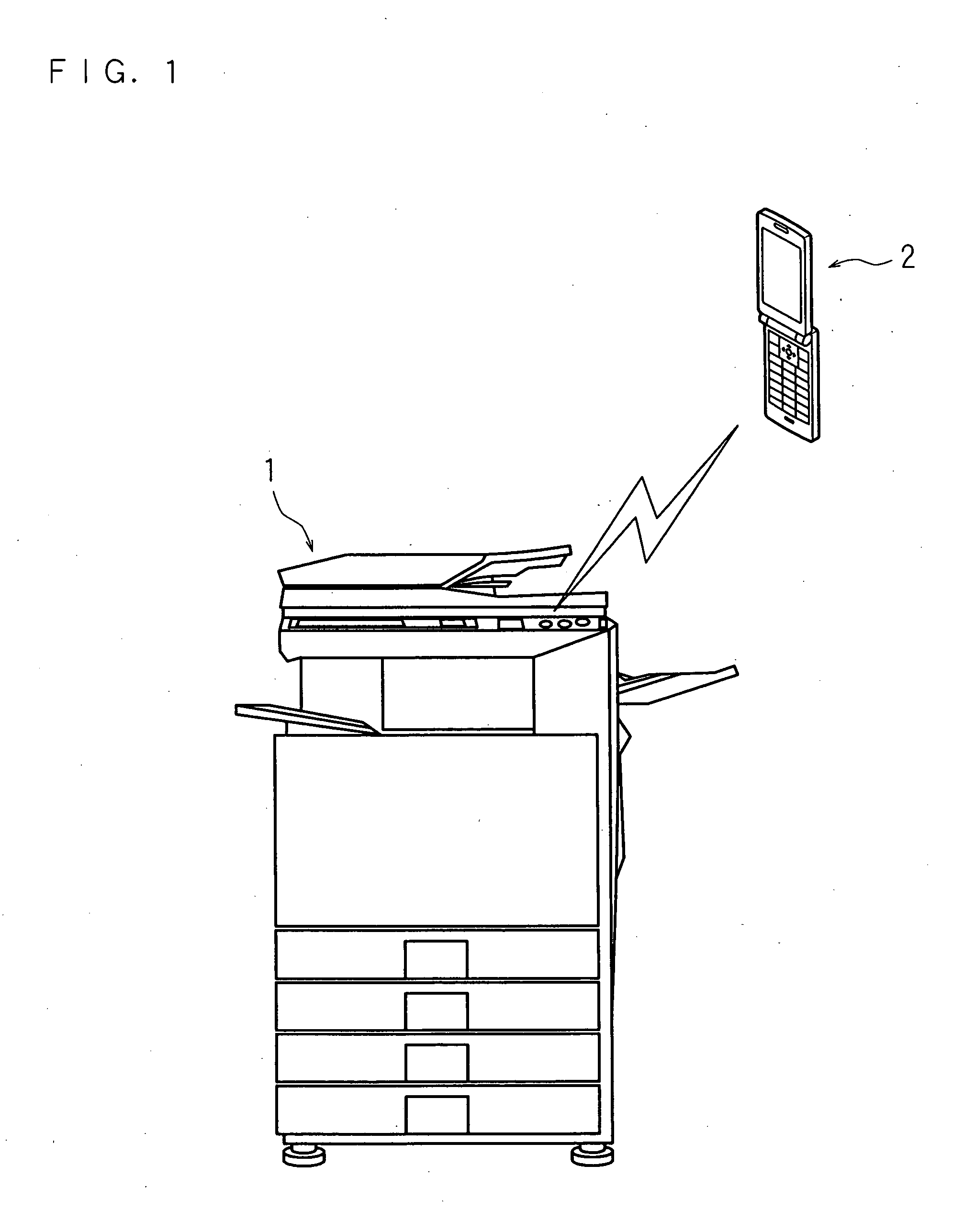
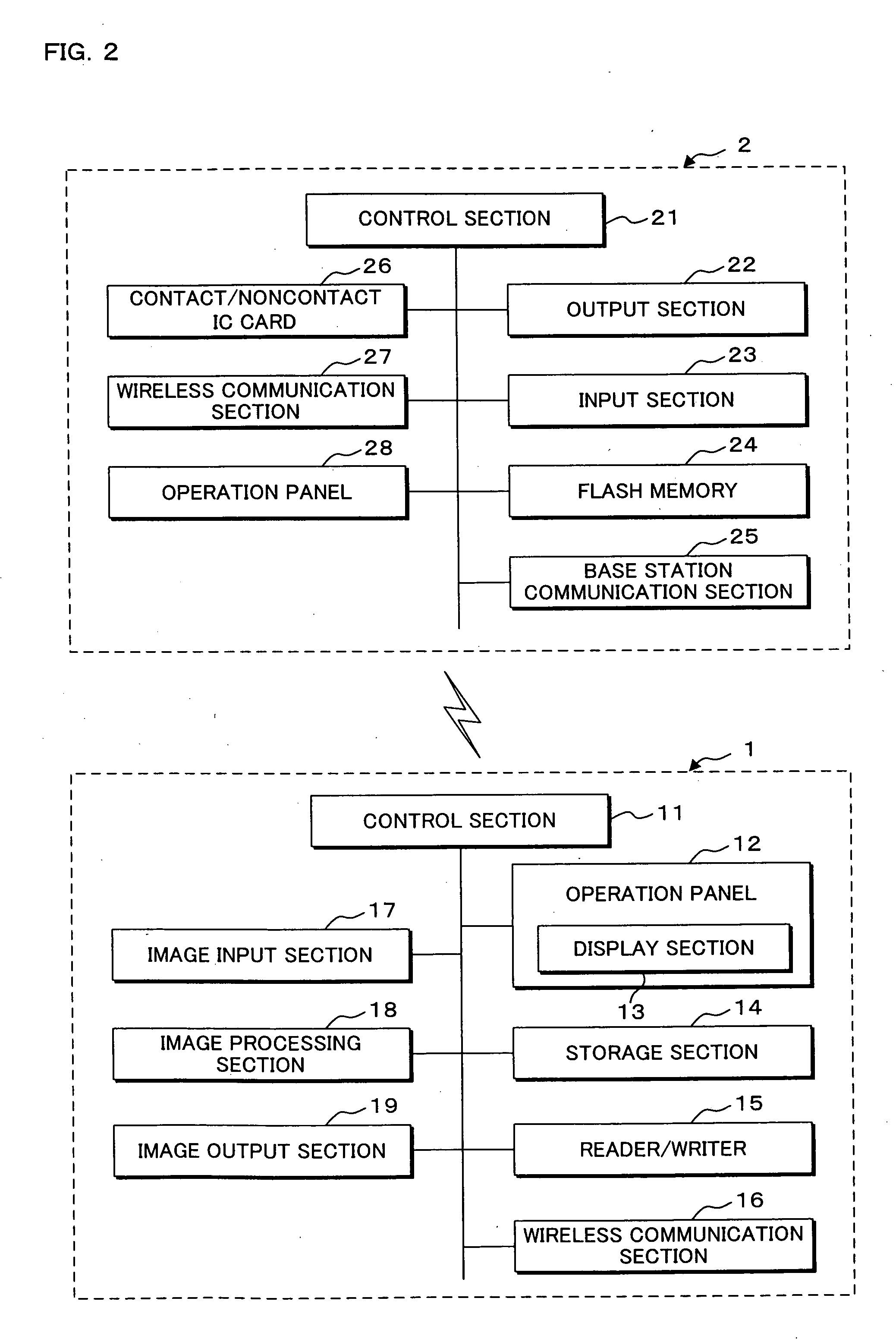
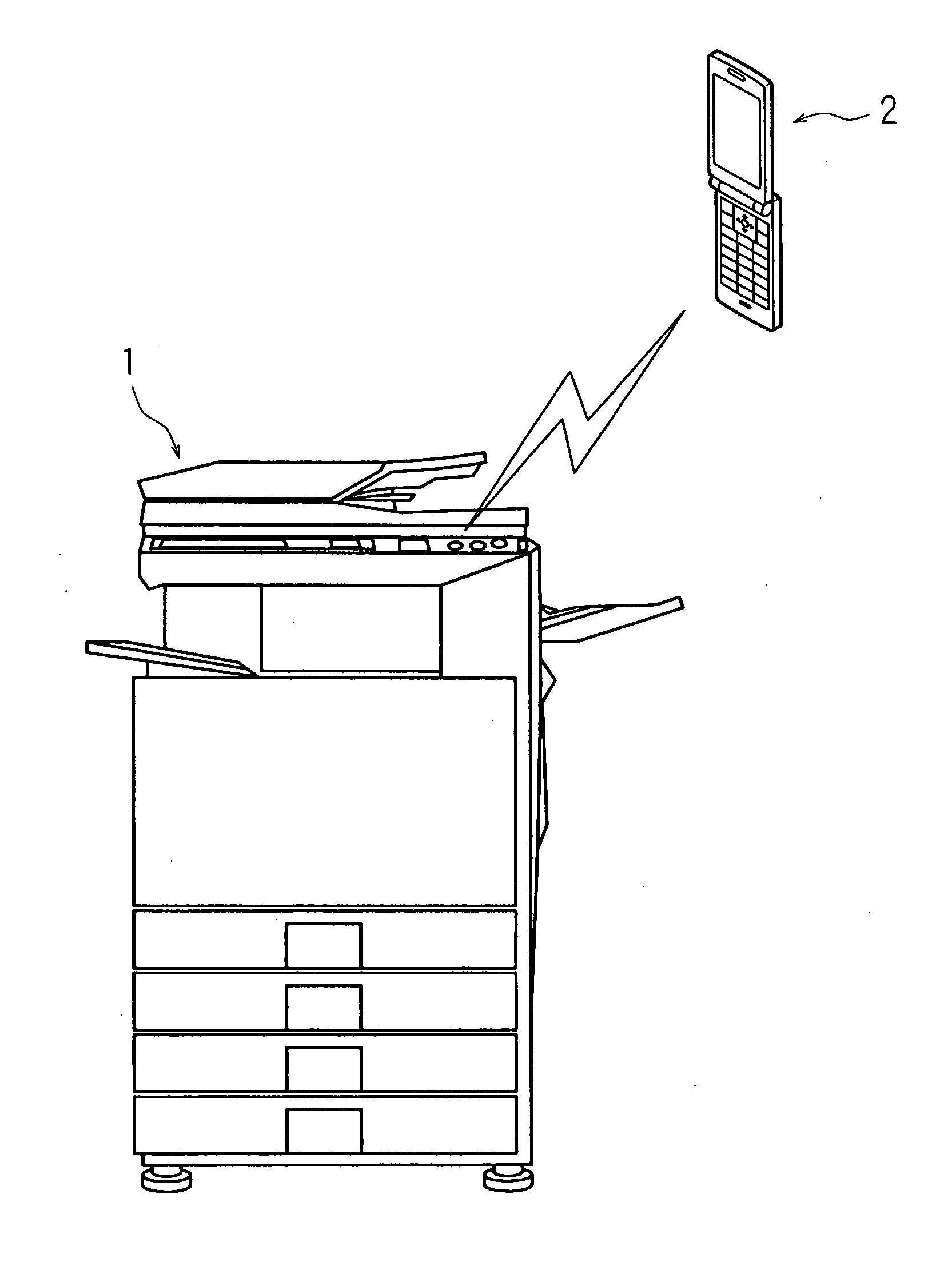
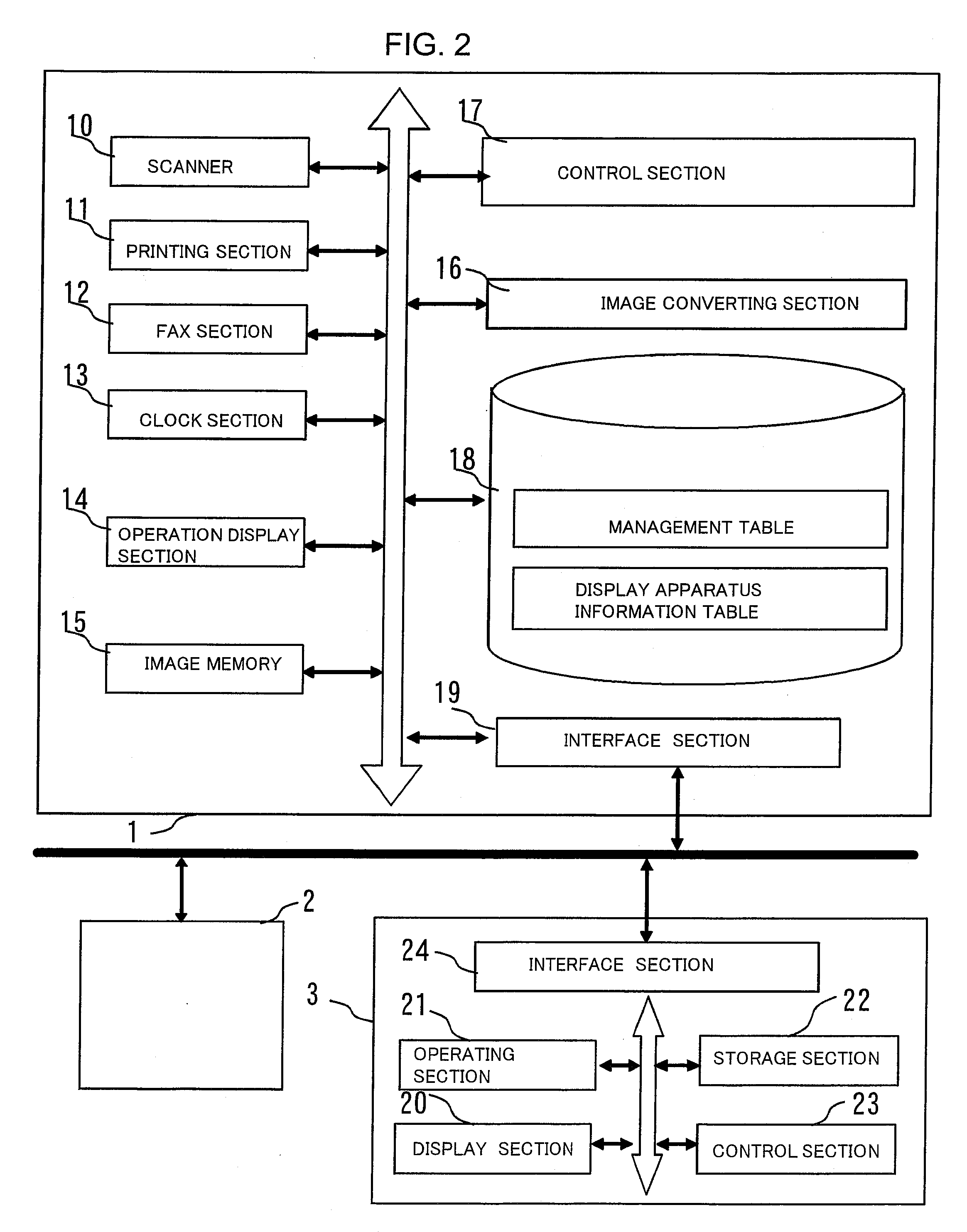
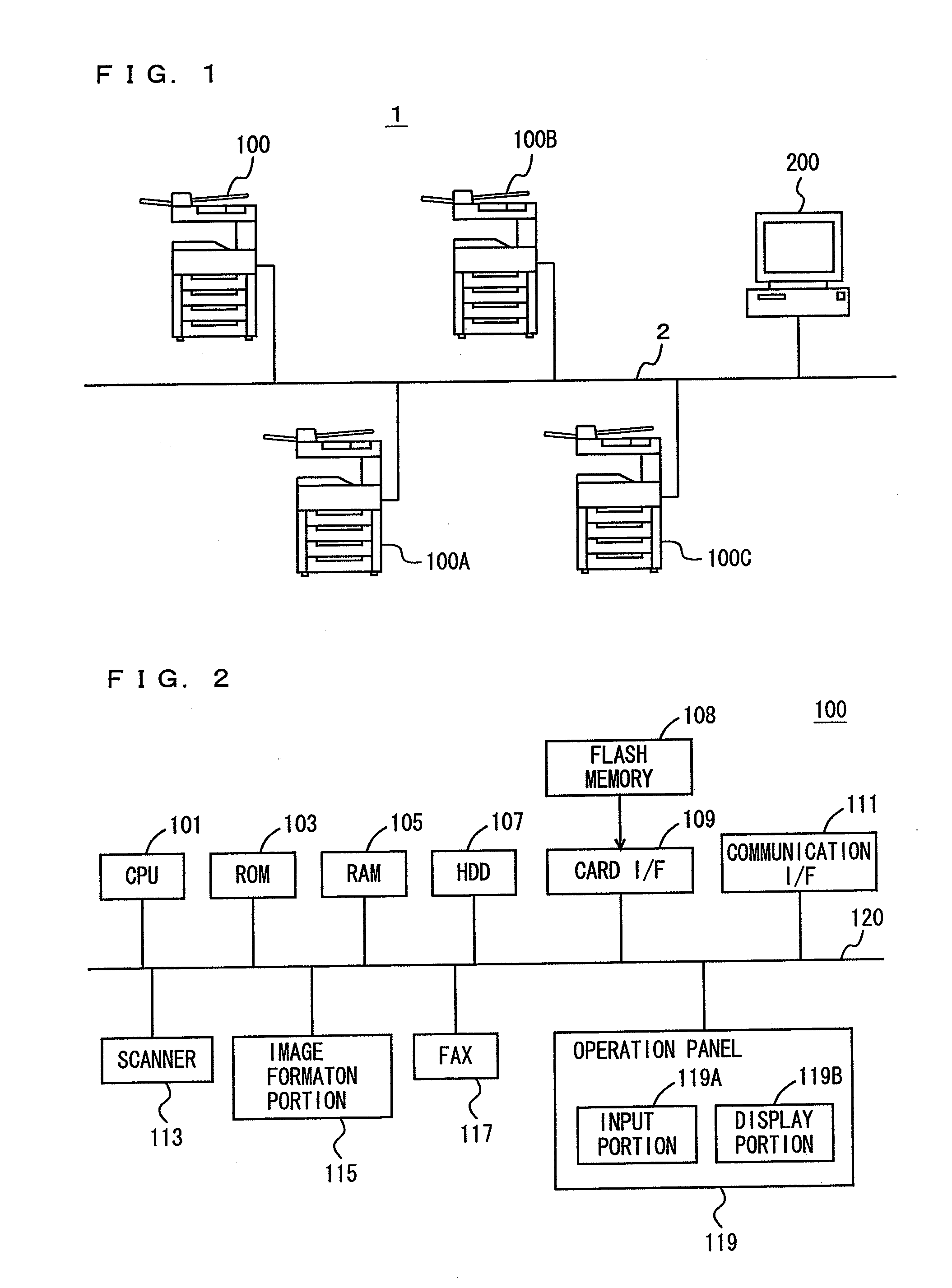
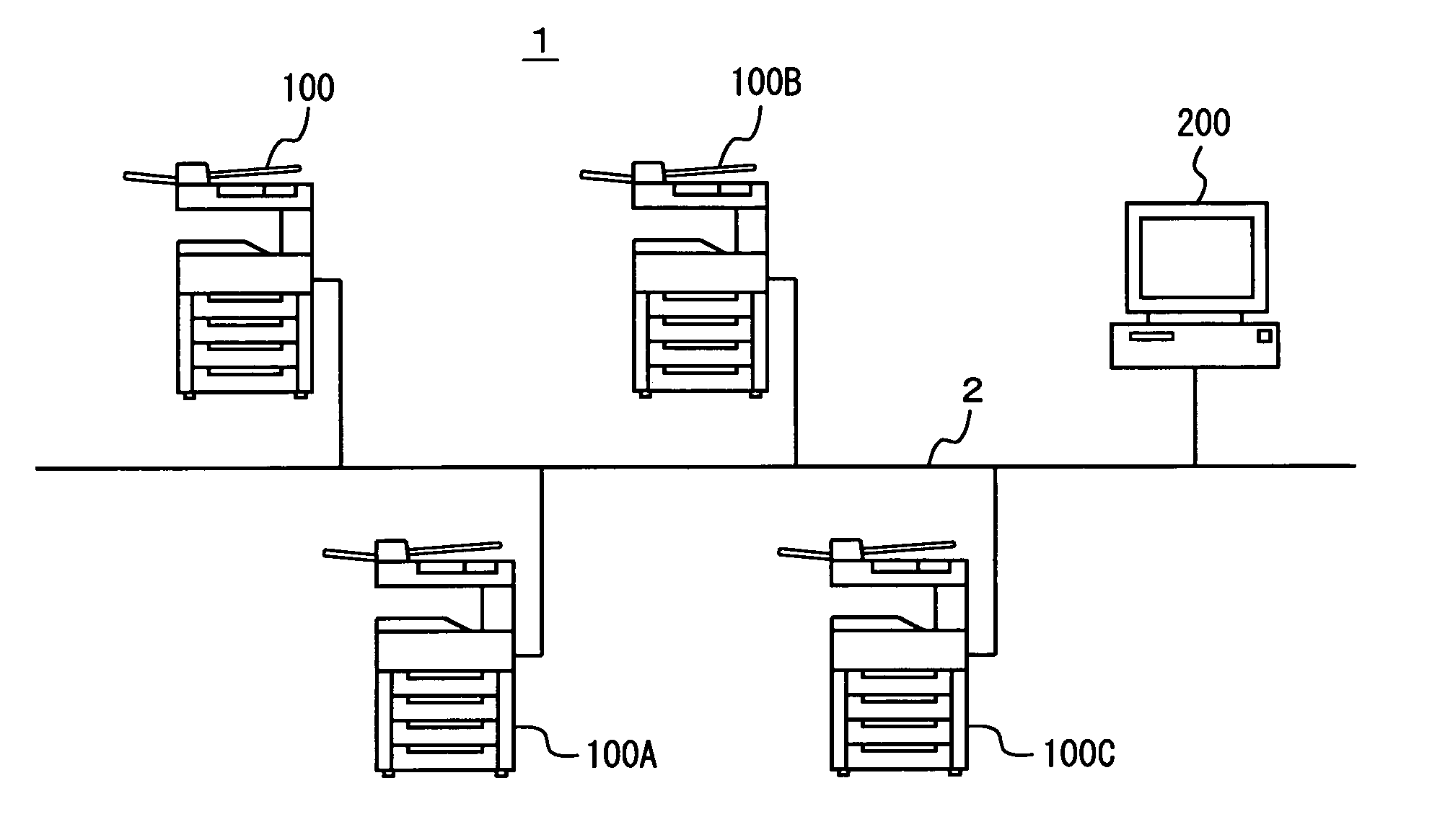
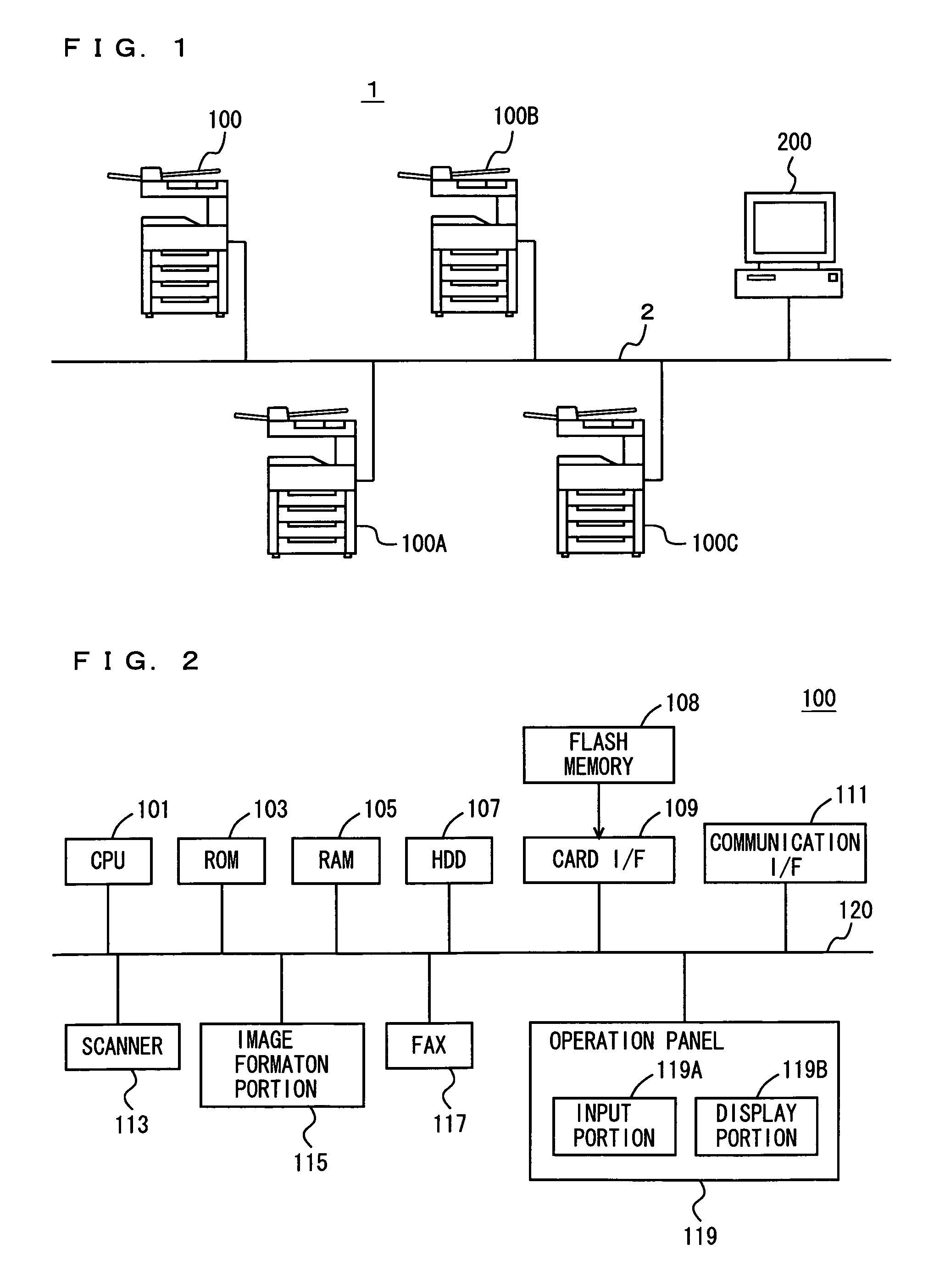
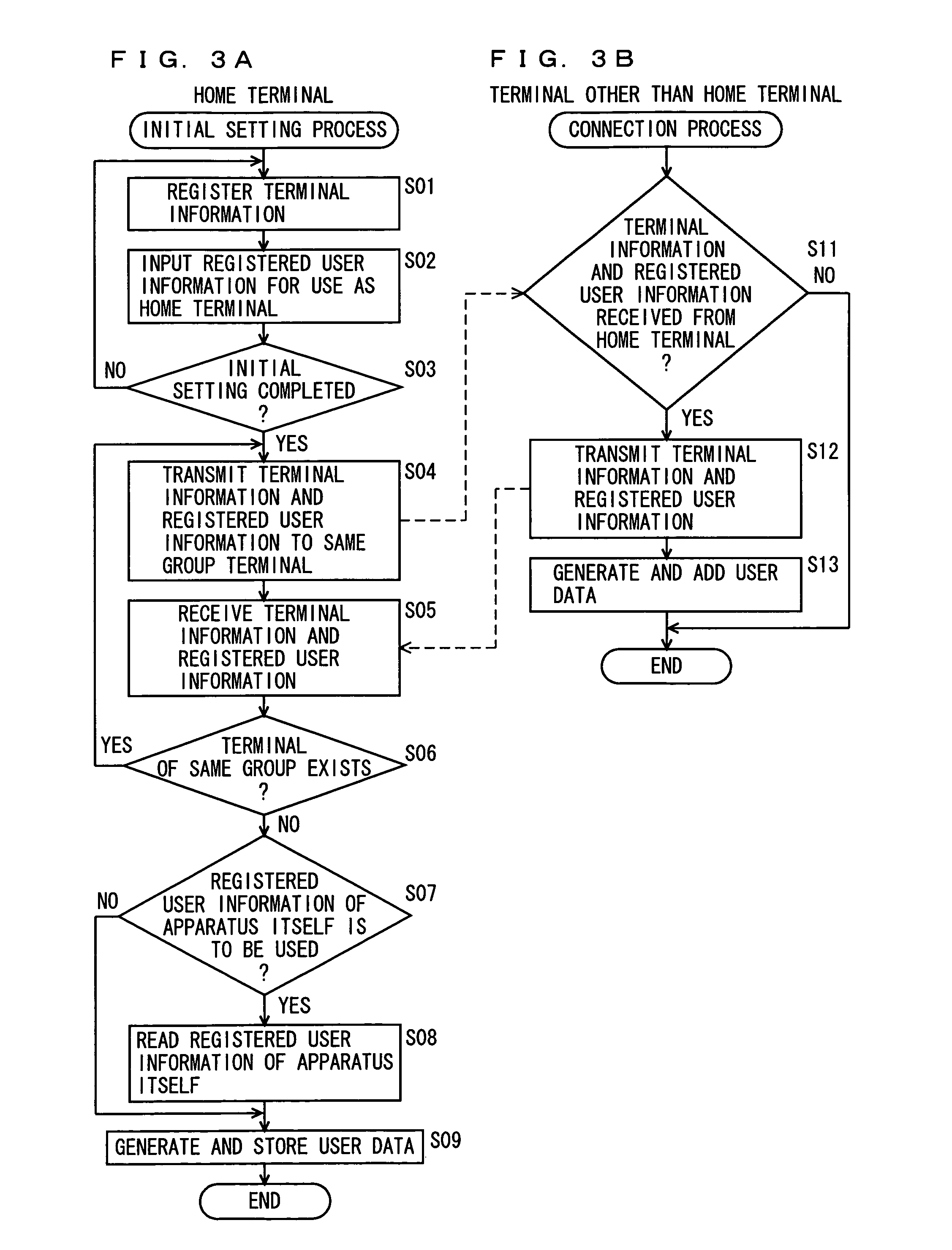
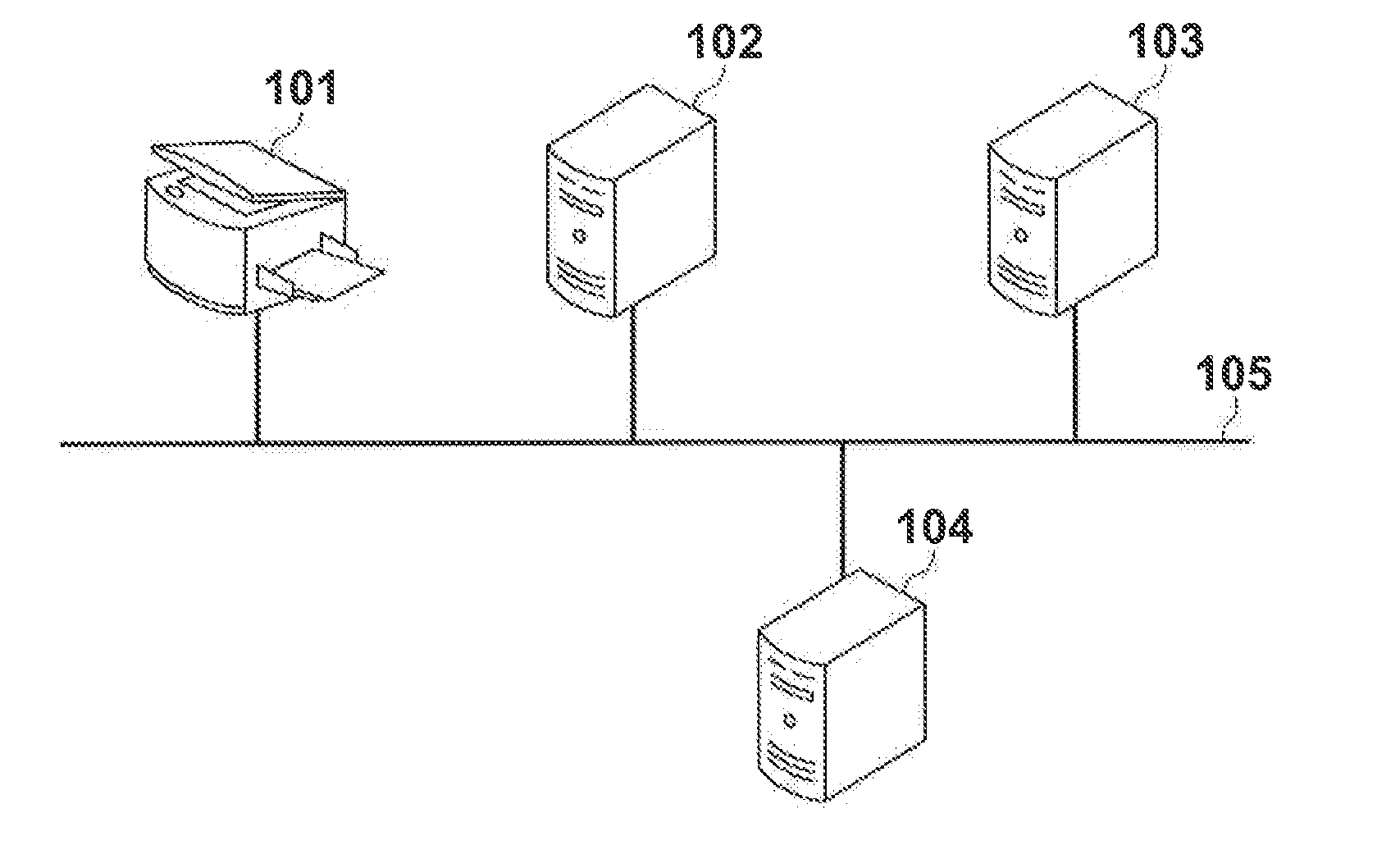
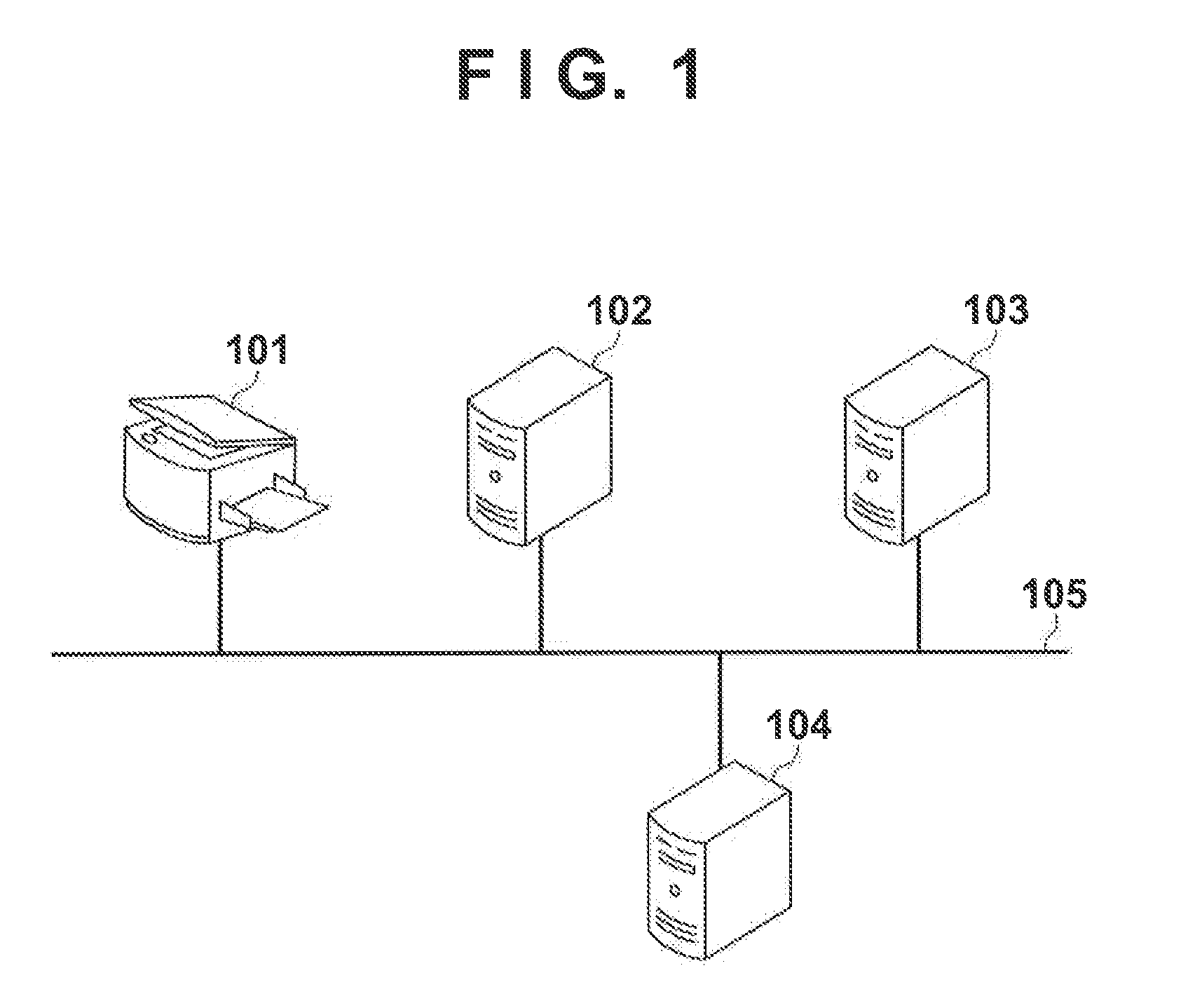
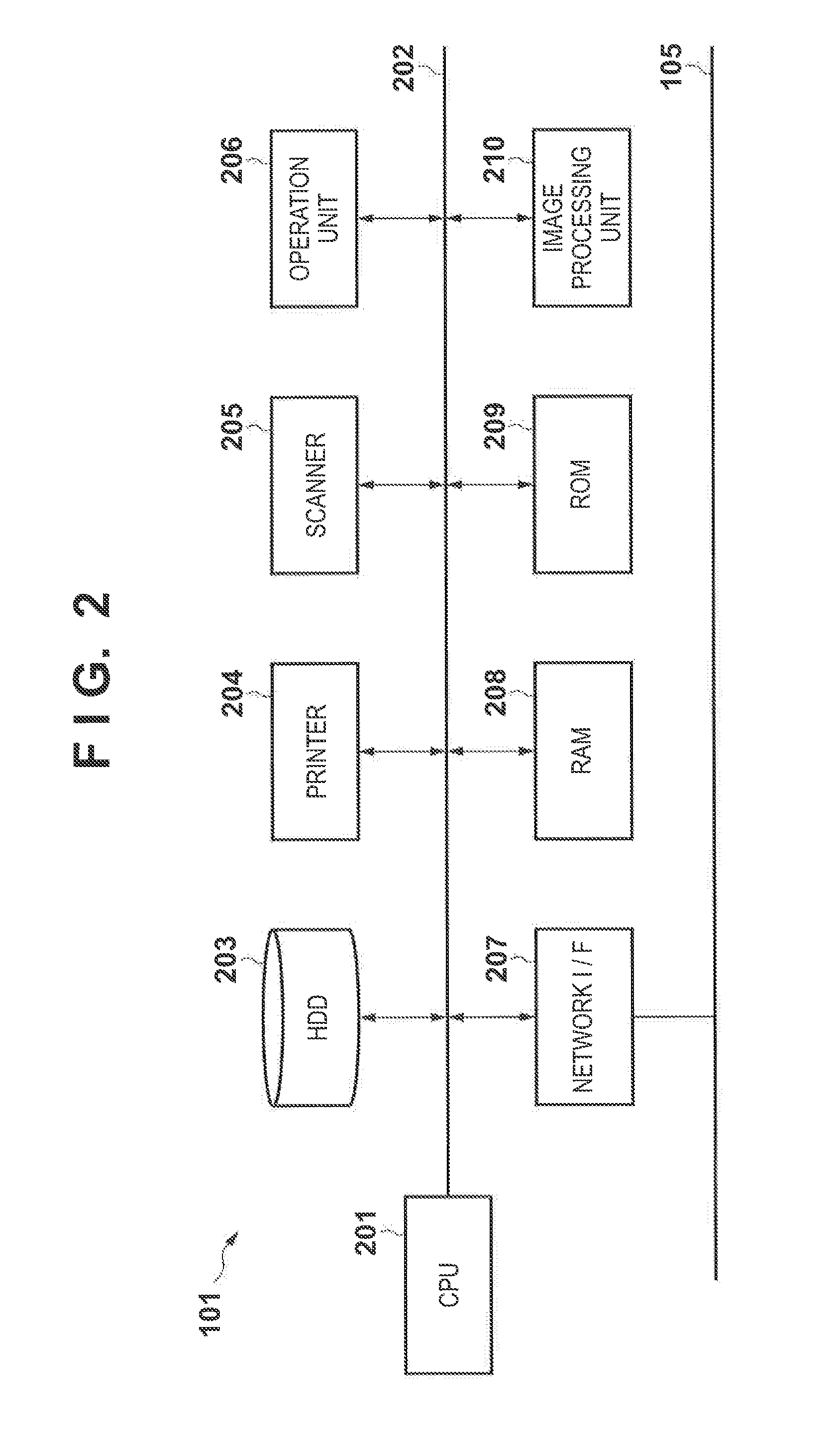
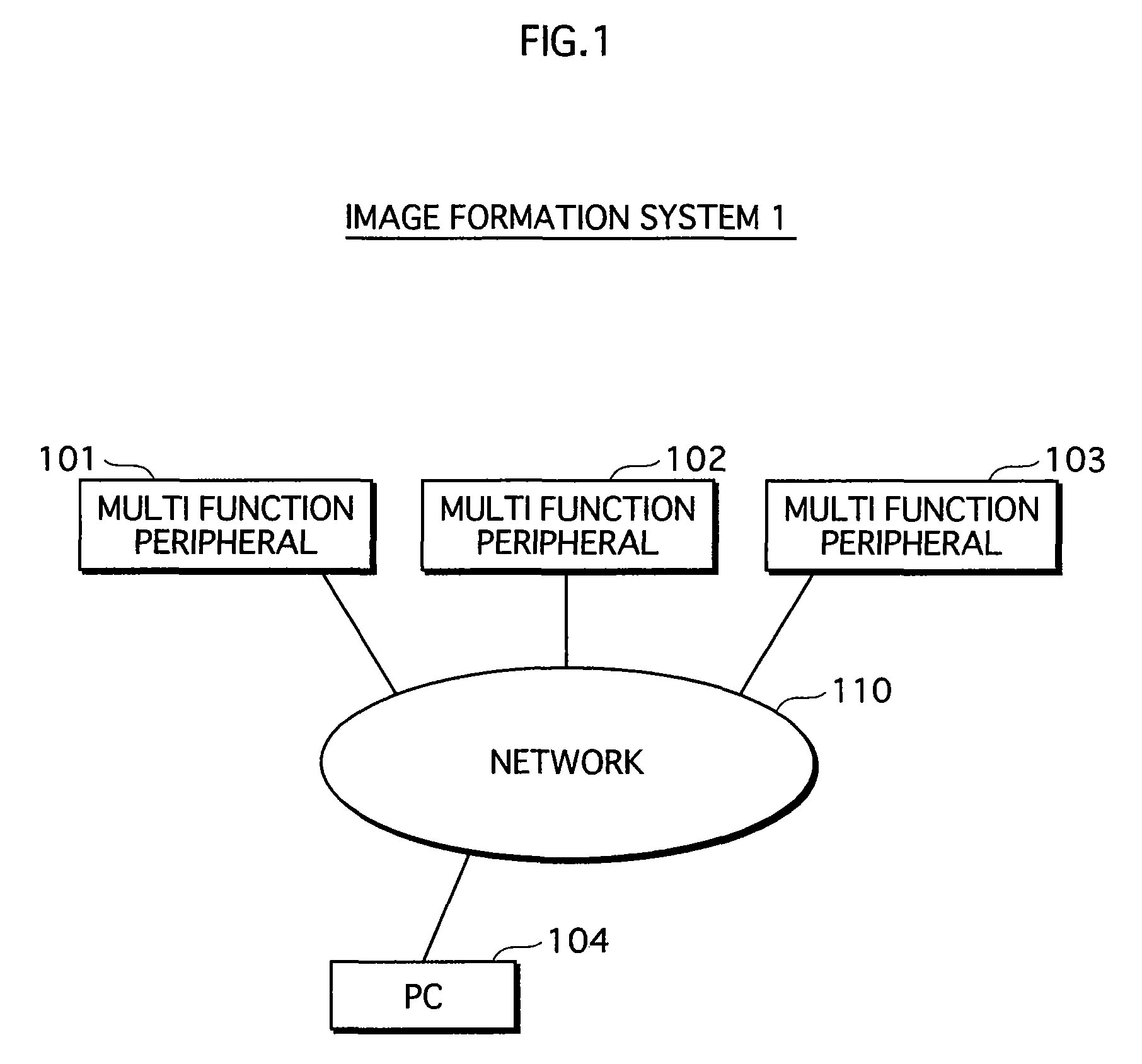
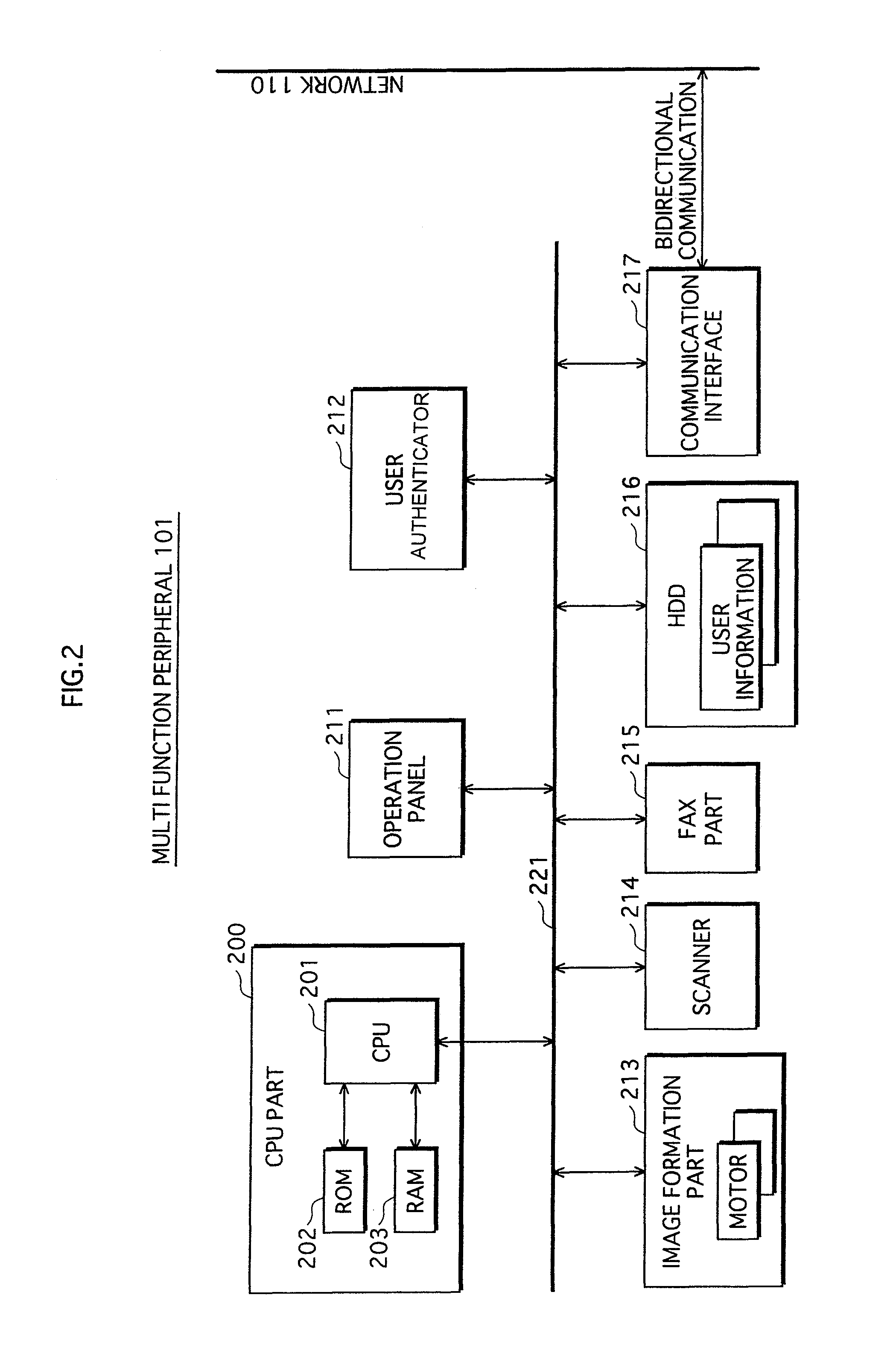
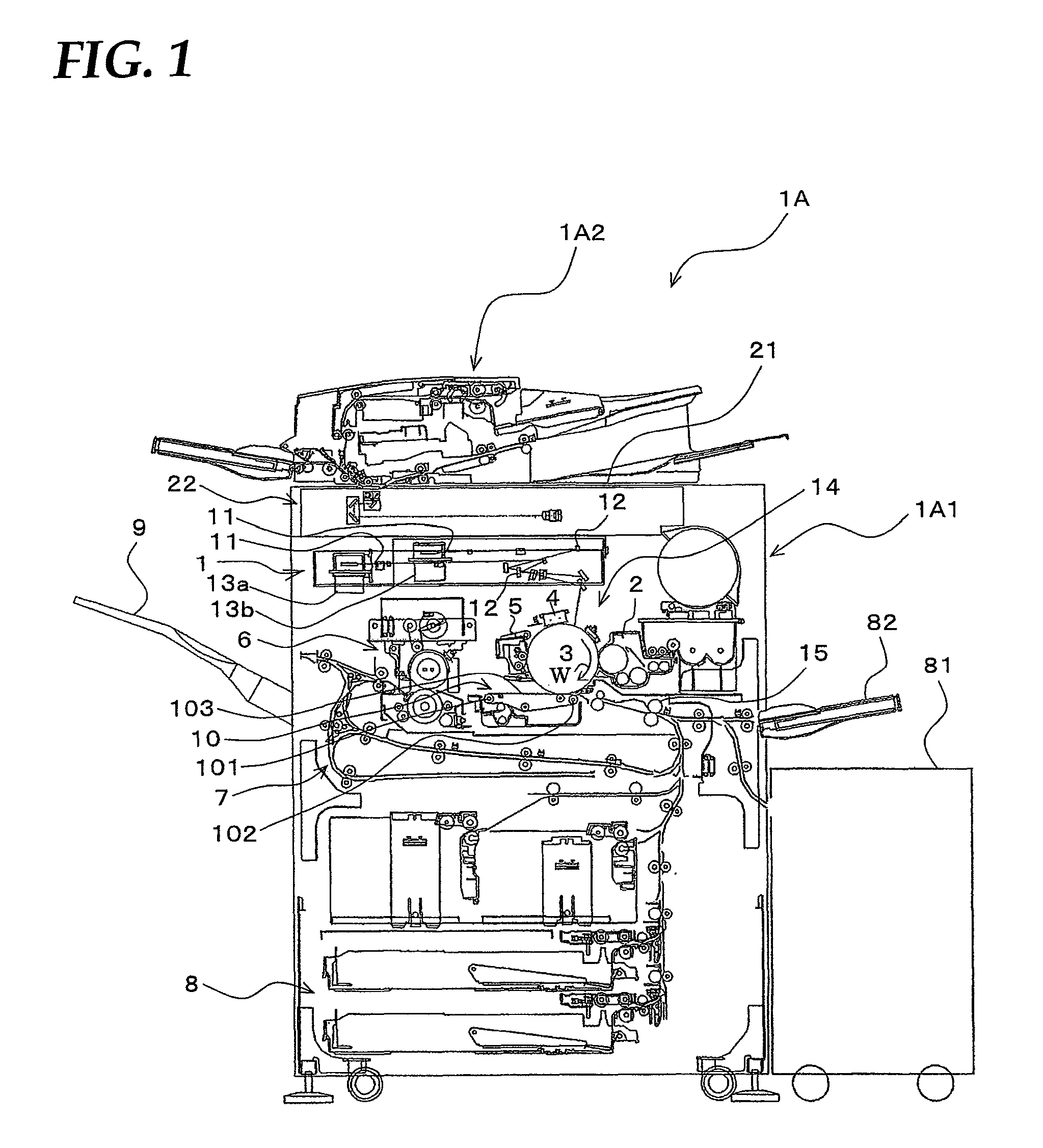
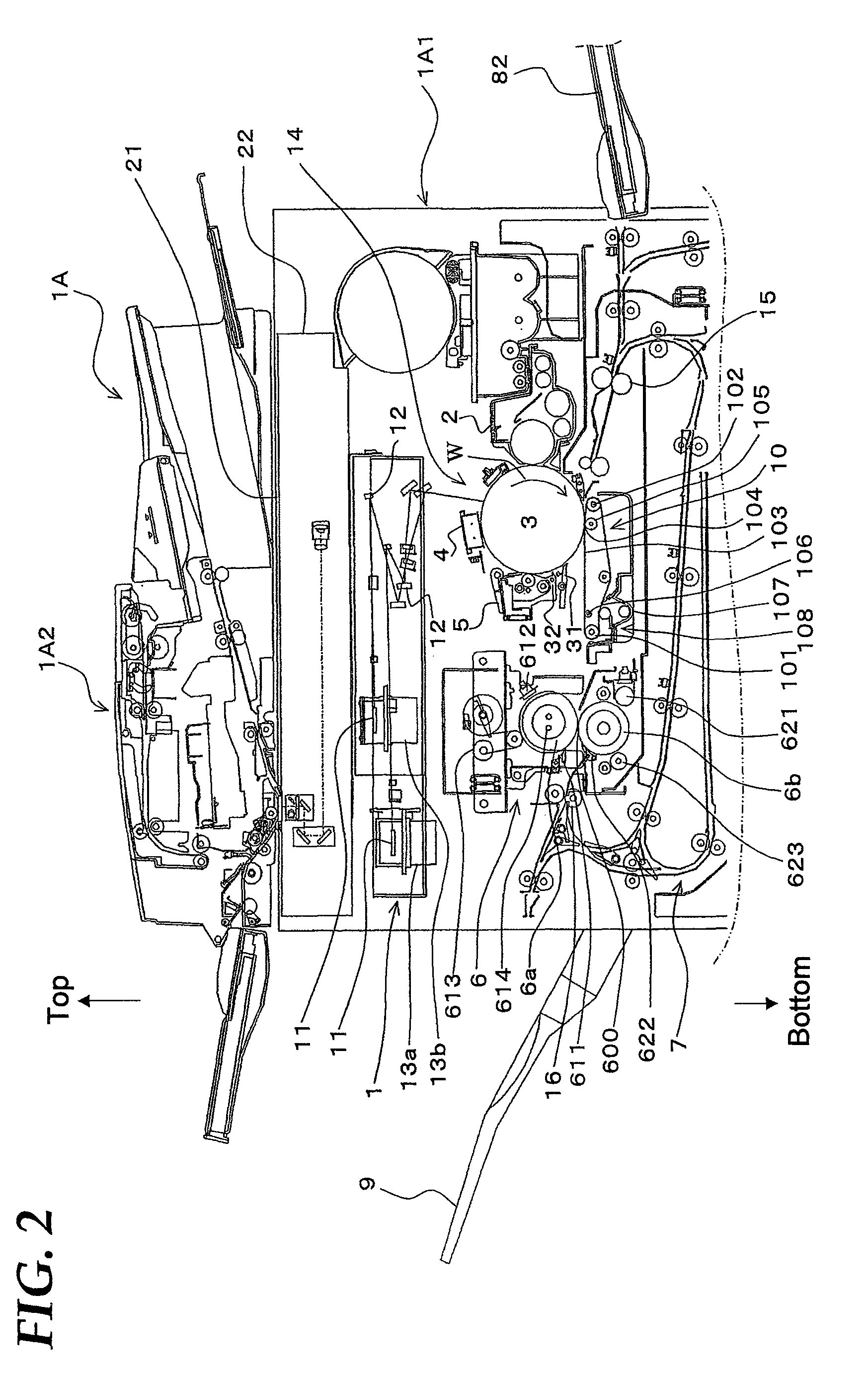
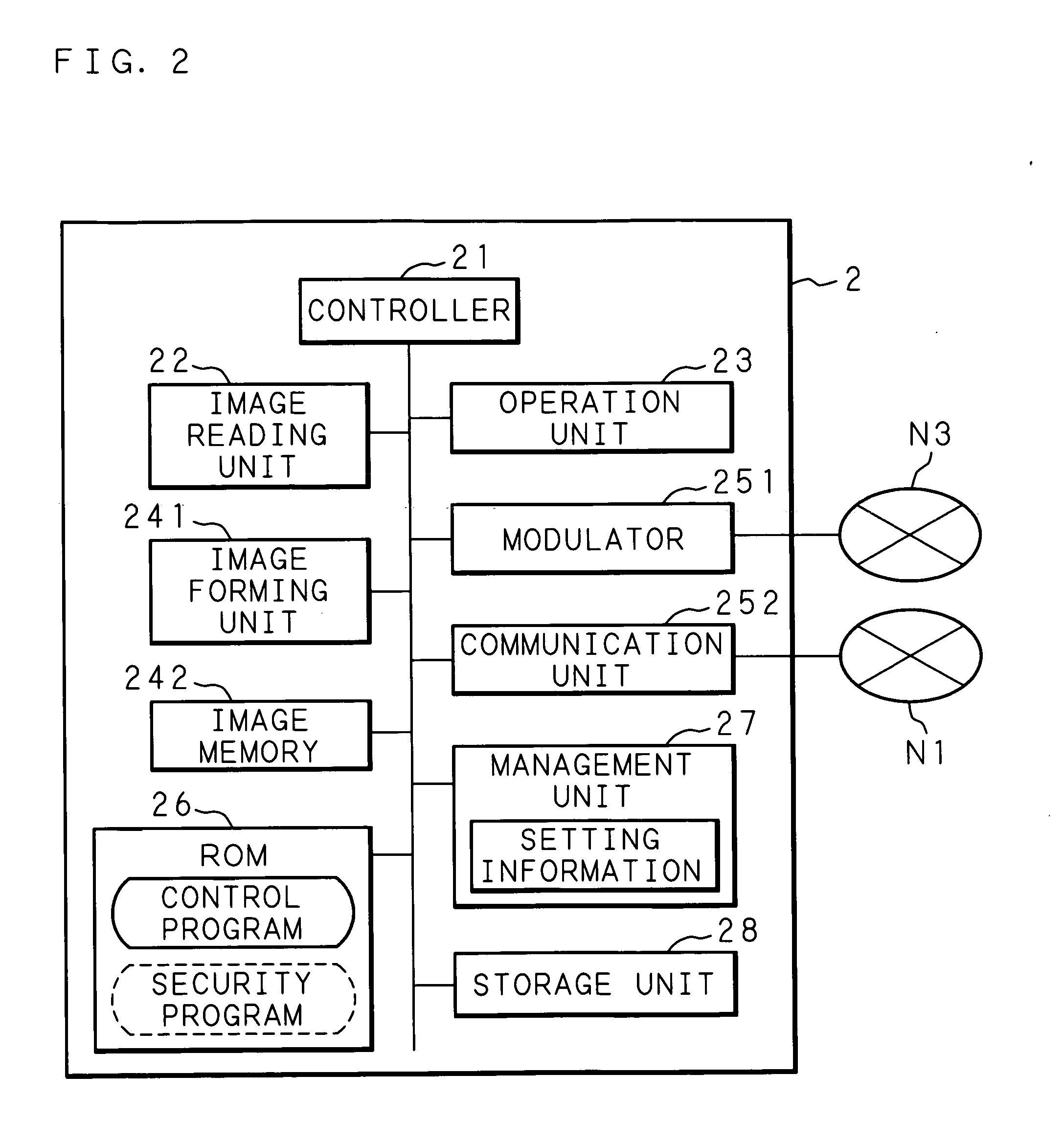
Communication system, information processing system, image formation system, image forming apparatus, mobile information terminal device and information processing device
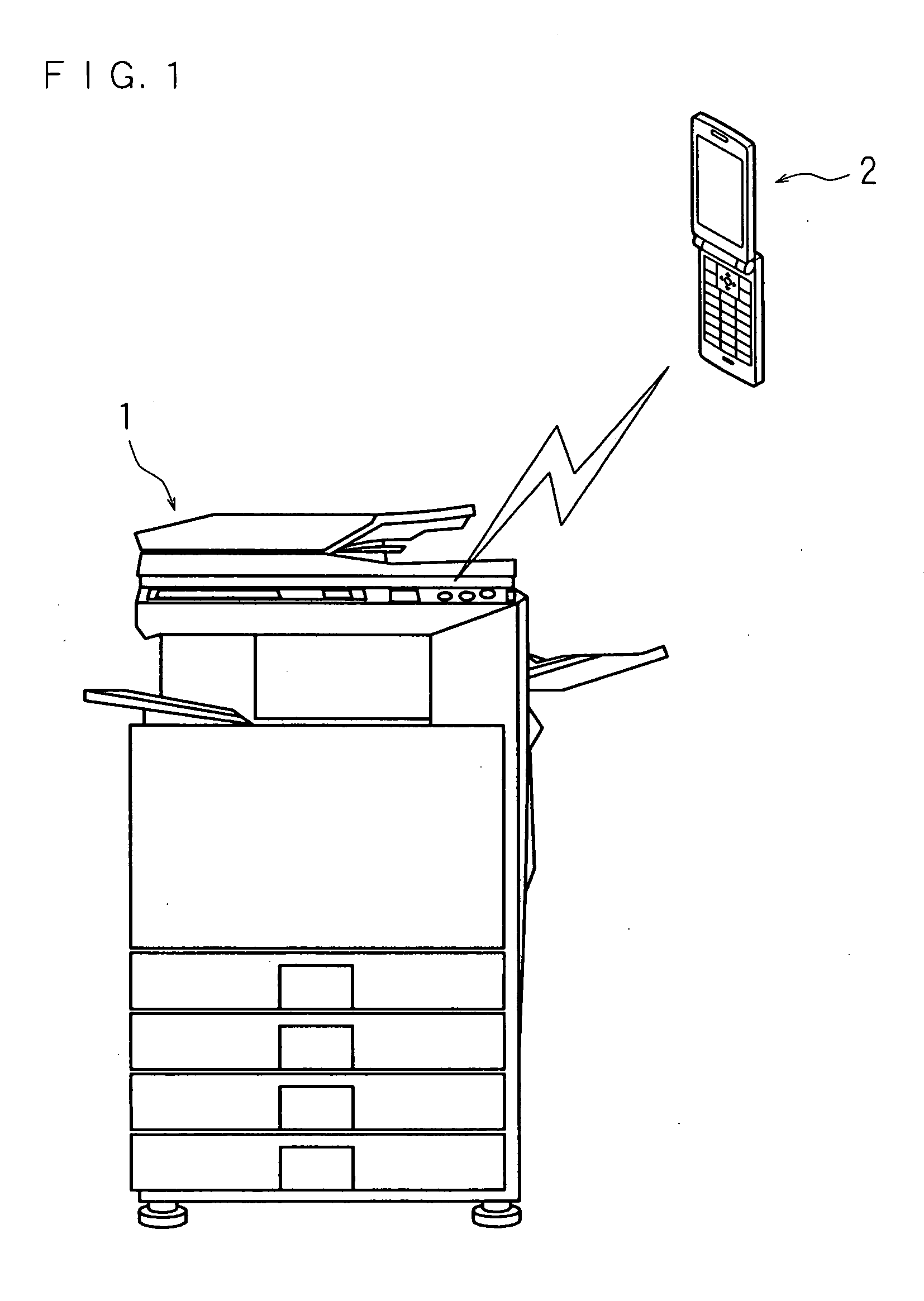
InactiveUS20100225962A1Prevent leakageEstablishment of connectionConnection managementSubstation equipmentInformation processingCommunications system
After a digital multi-function peripheral establishes a connection with a mobile phone once, it rejects connection establishment requests made to a wireless communication section by other devices. Moreover, after a connection is established with a mobile phone once, the digital multi-function peripheral stops sending of the address of the wireless communication section through a reader / writer. After completing the sending / receiving of data, the digital multi-function peripheral and the mobile phone delete the addresses of their partner devices stored in them, respectively, for use in sending / receiving data.
Owner:SHARP KK
Communication system, information processing system, image forming apparatus and portable information terminal device
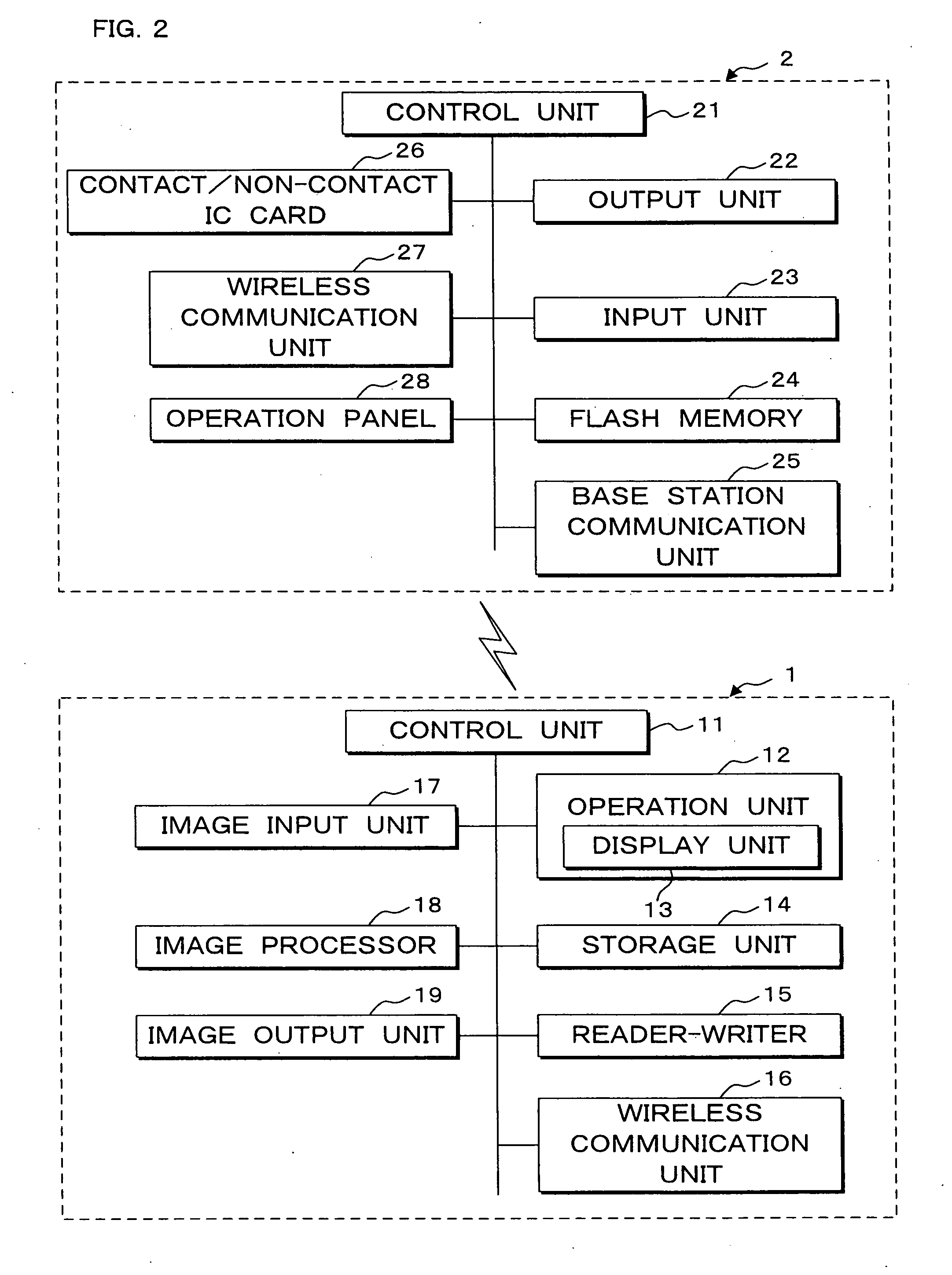
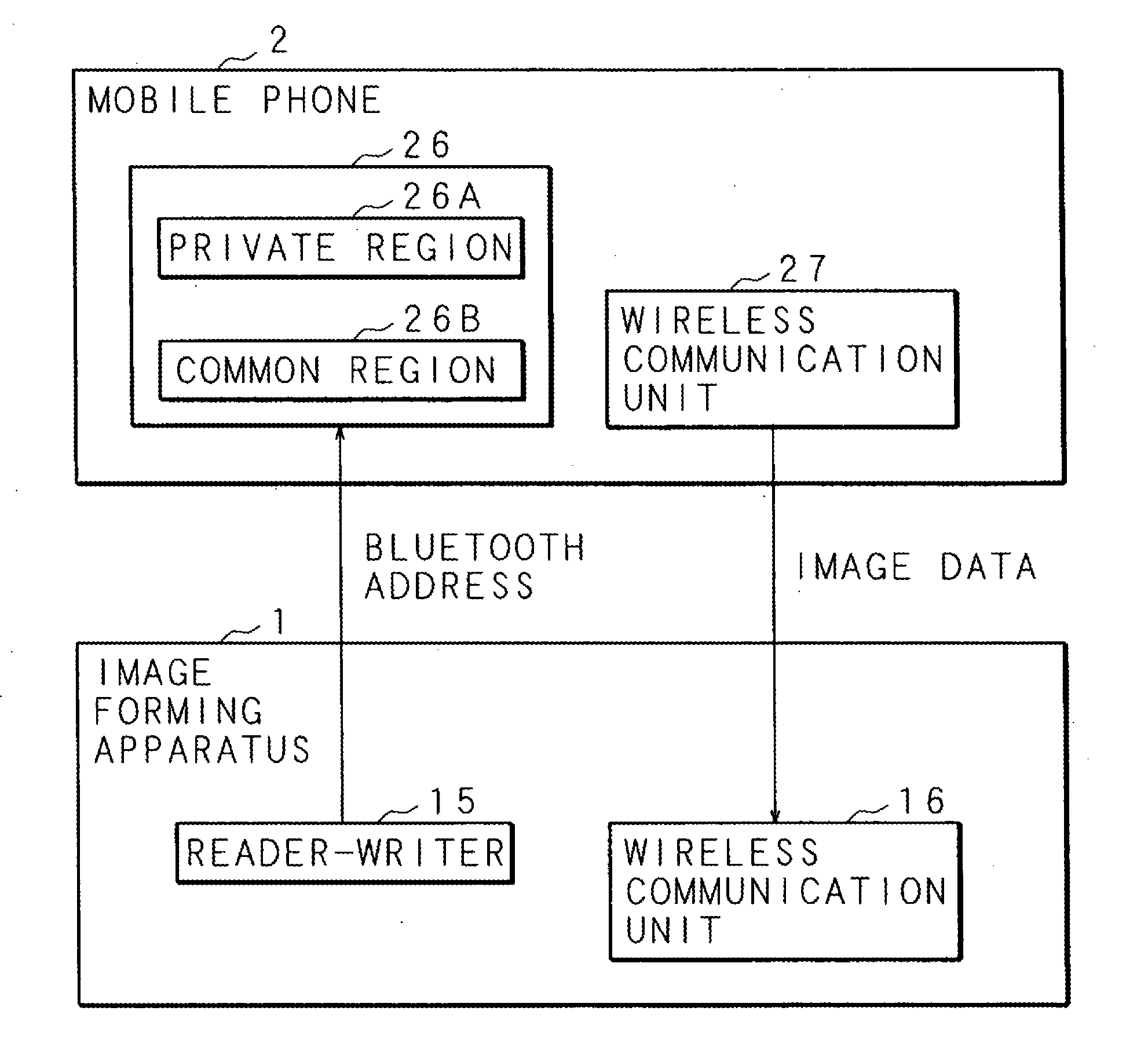
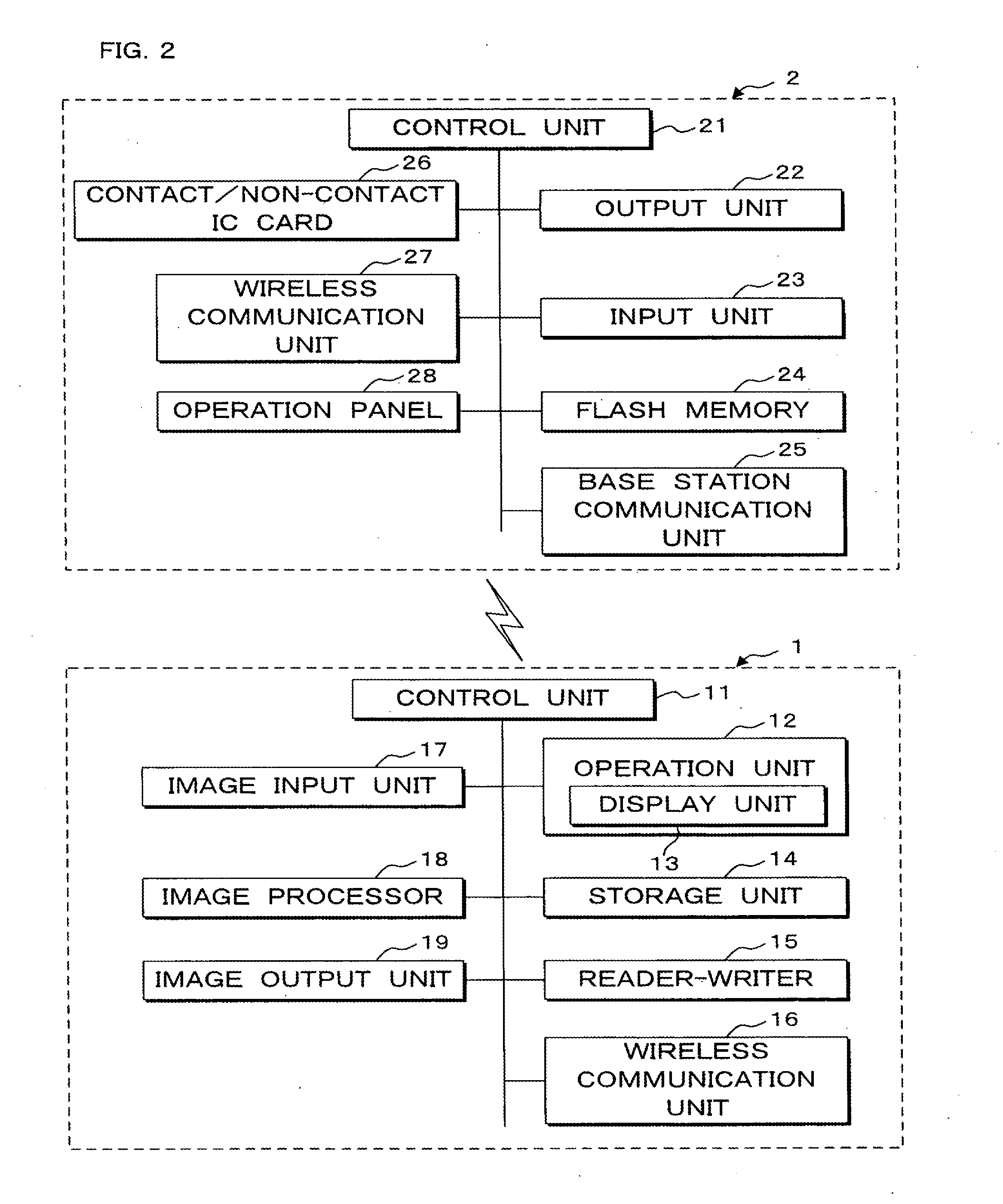
InactiveUS20100188695A1Avoid disclosure of confidential informationDevices with bluetooth interfacesSubstation equipmentInformation processingCommunications system
An image forming apparatus includes a first wireless communication unit that receives data from a mobile phone, and a reader-writer that transmits an address of the first wireless communication unit to the mobile phone. The mobile phone includes a contact / non-contact IC card that receives the address, and a second wireless communication unit that transmits image data to the first wireless communication unit utilizing the address. When communication is made between the mobile phone and the image forming apparatus, the address of the first wireless communication unit is transmitted to the contact / non-contact IC card through the reader-writer, and the second wireless communication unit transmits data to the first wireless communication unit utilizing the address.
Owner:SHARP KK
Display system and image processing apparatus
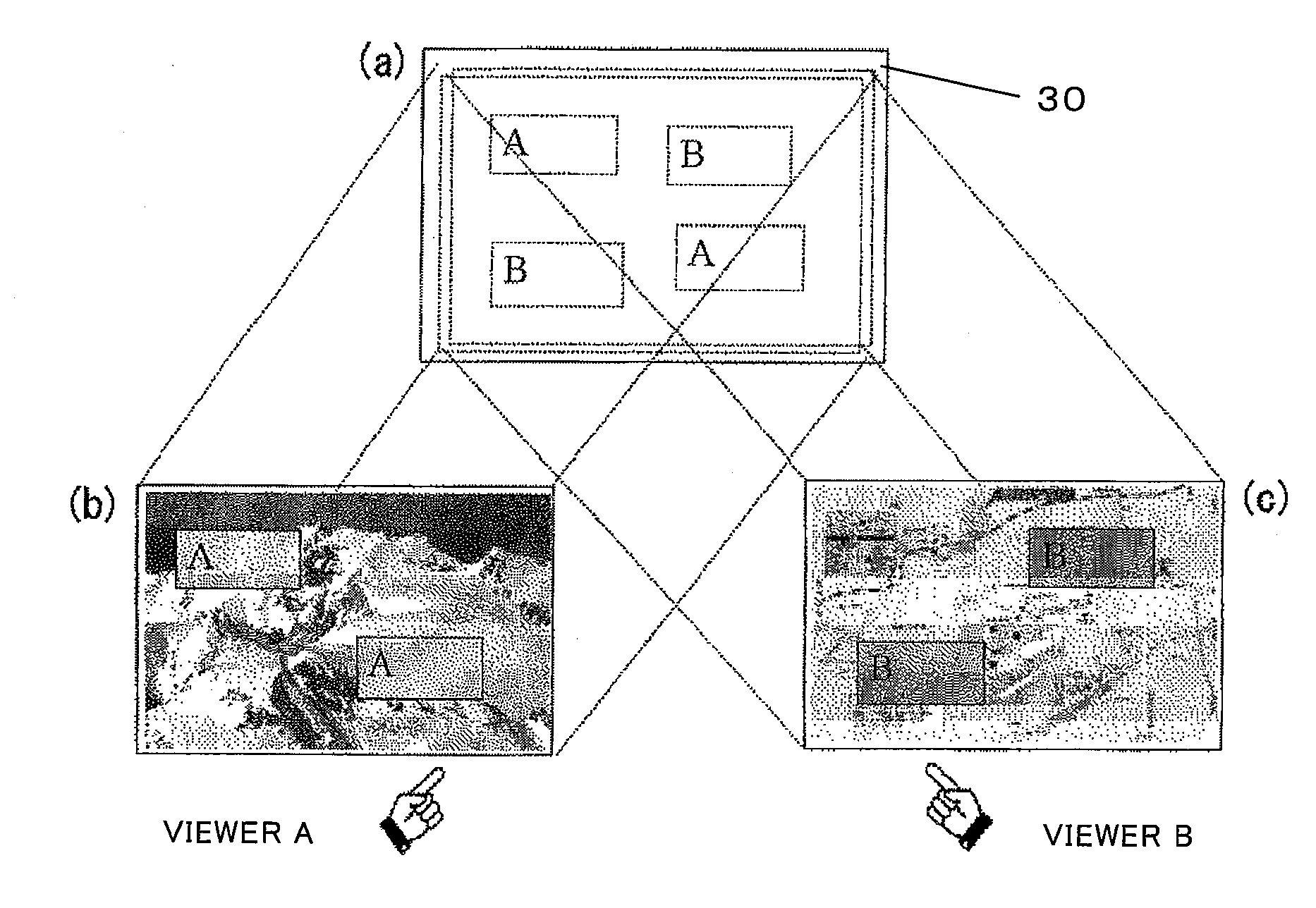
InactiveUS20080303842A1Prevent leakageAvoid disclosure of confidential informationCathode-ray tube indicatorsInput/output processes for data processingComputer graphics (images)Multiple view
In a display apparatus capable of multiple-view display, a restriction is imposed on an image to be displayed depending on the viewing area set with reference to a screen, thereby enhancing security and preventing leakage of confidential information. When an image processing apparatus outputs an image to the display apparatus, the image processing apparatus confirms the display conditions for a specified viewing area. After confirmation, the image processing apparatus reads an image of a document according to the display conditions. The image to be outputted is restricted and differs from the original image. The image processing apparatus transmits the restricted image to the display apparatus. The display apparatus displays the restricted image, which is different from the original image, to the specified viewing area. The display apparatus displays the original image to the other viewing areas.
Owner:SHARP KK
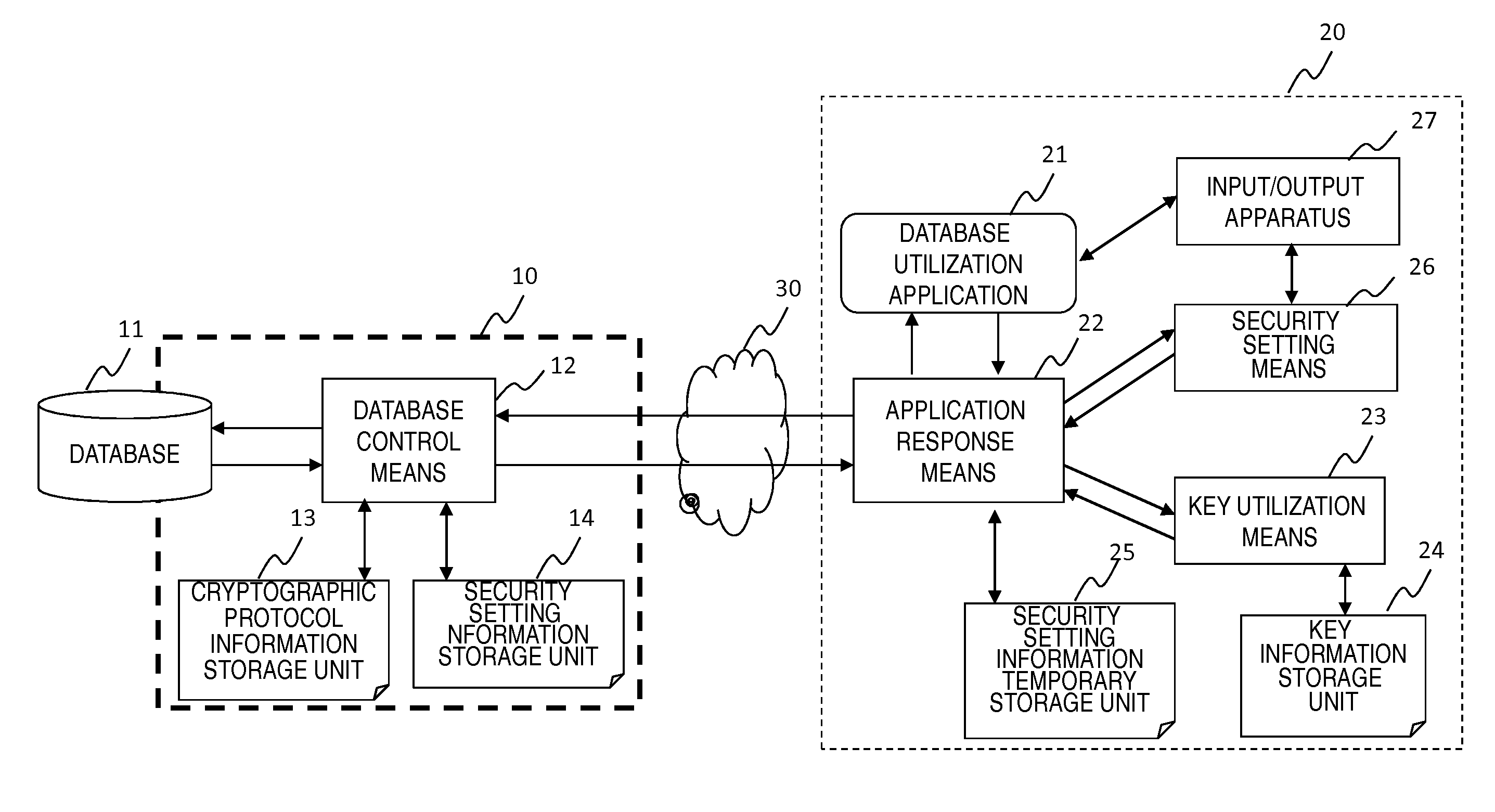
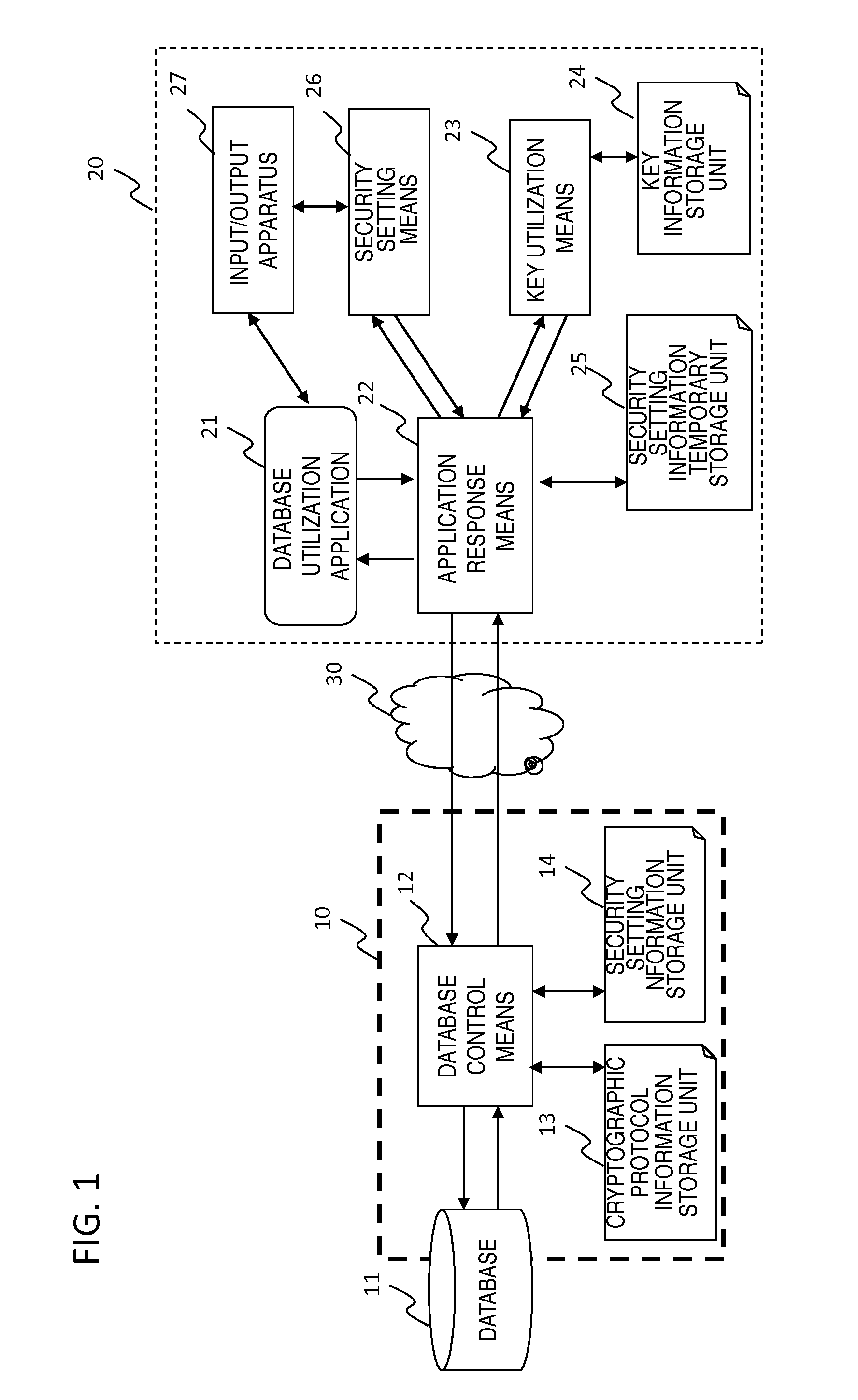
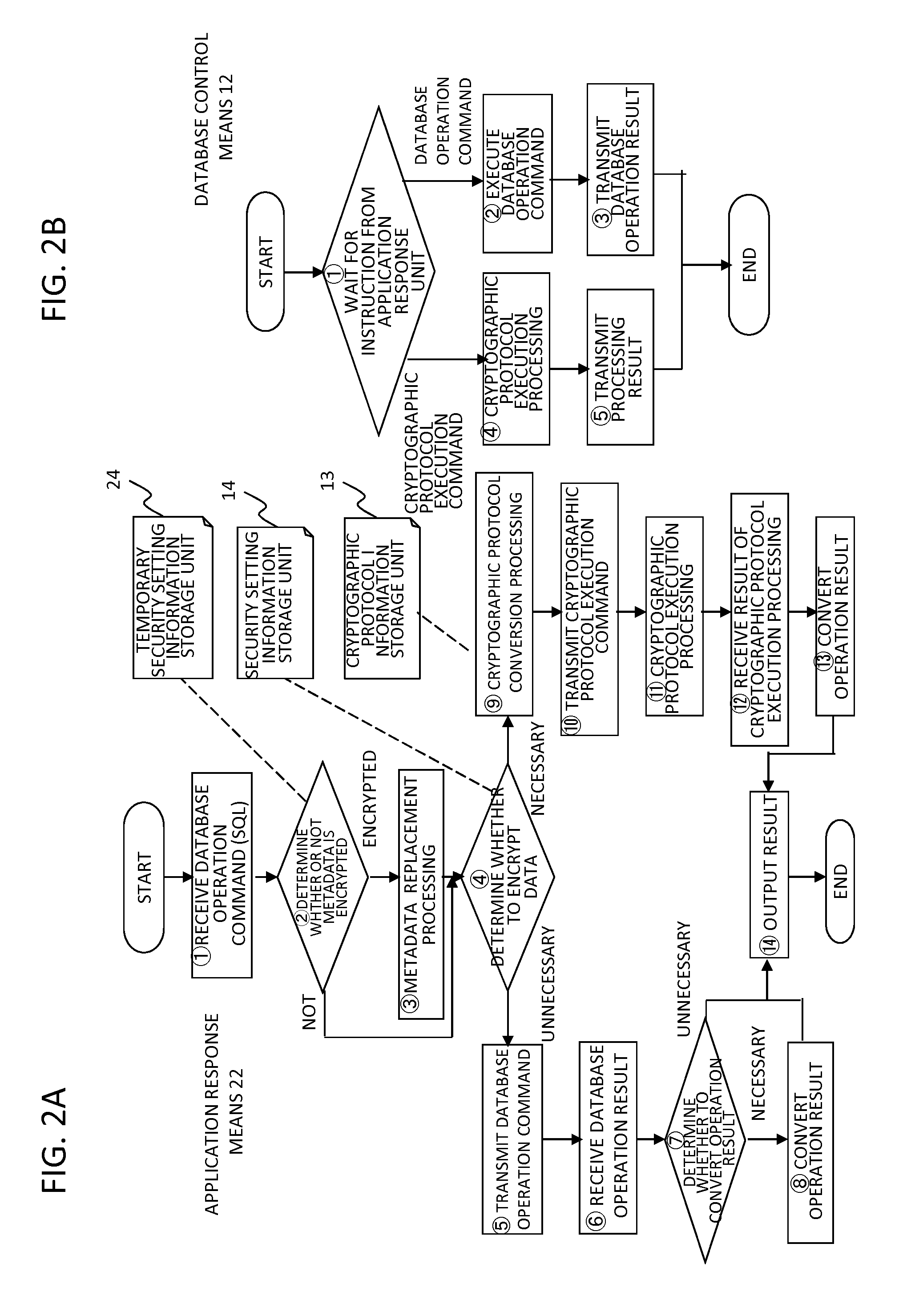
Database apparatus, method, and program
ActiveUS20140325217A1Leakage of information can be preventedImprove processing efficiencyDigital data protectionSpecial data processing applicationsData access controlCiphertext
Provided a database apparatus comprising a control means to execute data access control on a database, wherein the control means, receiving a database operation command from a user apparatus, comprises, regarding data and / or metadata to be handled associated with the database operation command, means for executing database operation or computation on encrypted data and / or encrypted metadata as is in ciphertext and means for executing database operation or computation on plaintext data and / or plaintext metadata, and the control means sends a processing result to the user apparatus.
Owner:NEC CORP
Image processing apparatus
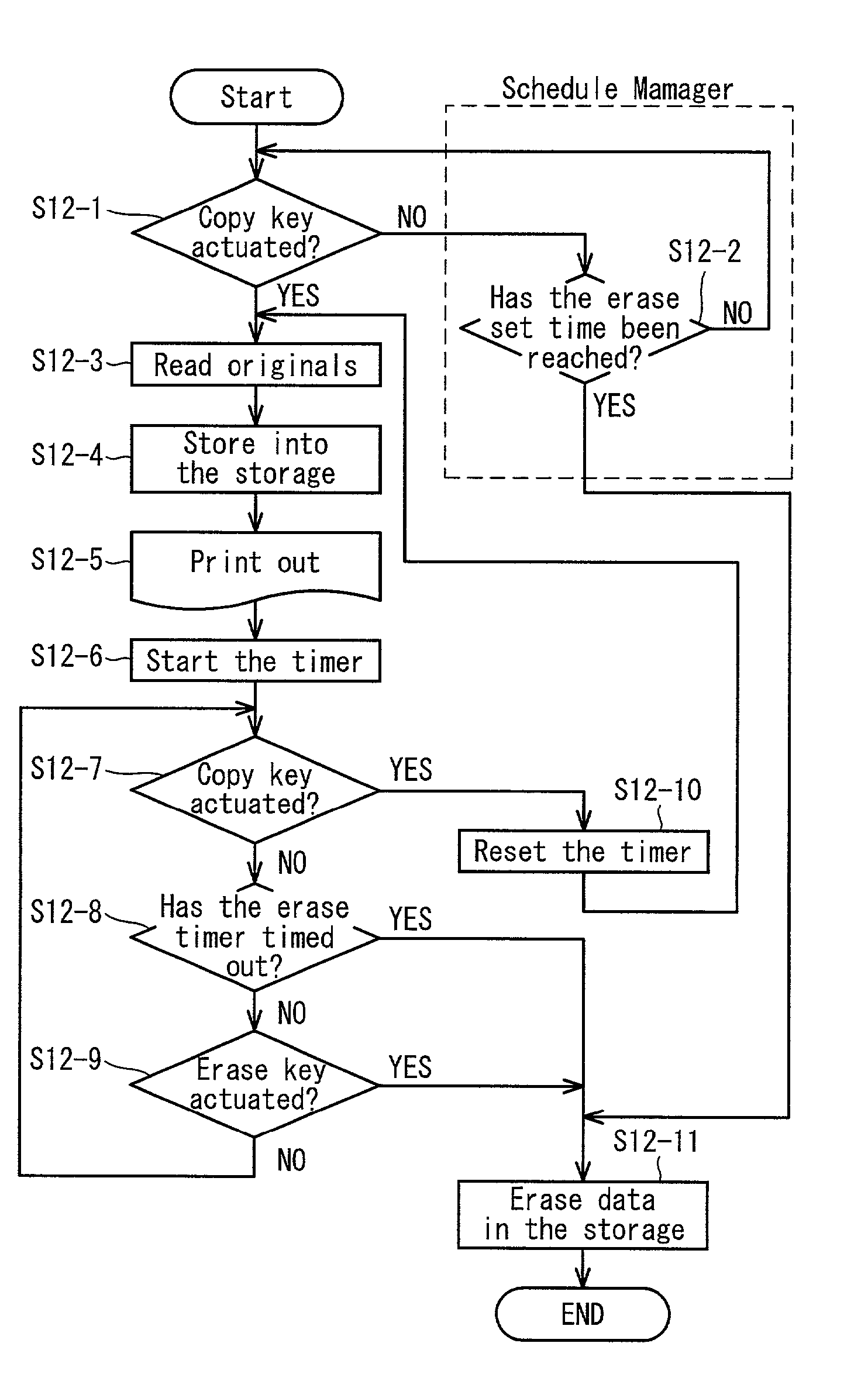
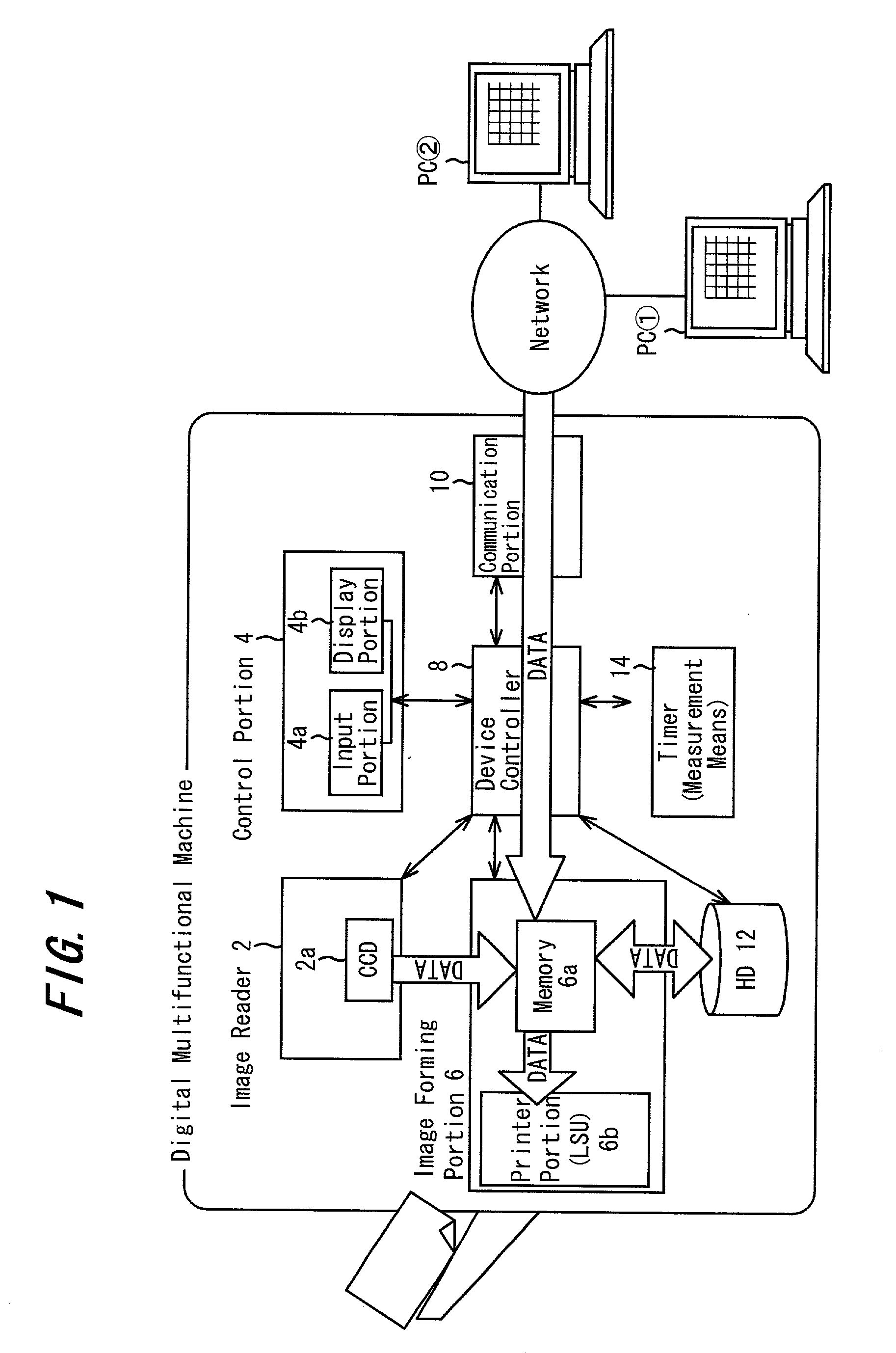
ActiveUS7170622B2Prevent leakageImprove standardsUnauthorized memory use protectionDigital data protectionImaging processingComputer graphics (images)
Image information input through an image information input device (e.g., image reader) is stored into an image information storage device (e.g., hard disk) and erased by an image information erasing device. A manager device (e.g., device controller) manages the status of an image processing apparatus and actuates the image information erasing device in accordance with the status of the image processing apparatus and erases the image information stored in the image information storage.
Owner:SHARP KK
Image forming apparatus performing image formation on print data, image processing system including plurality of image forming apparatuses, print data output method executed on image forming apparatus, and print data output program product
InactiveUS20100195136A1Prevent leakageAvoid disclosure of confidential informationVisual presentation using printersComputer security arrangementsImaging processingComputer graphics (images)
In order to prevent leakage of confidential information, MFP includes a communication I / F to receive print data, an image forming portion to perform image formation on print data, and a CPU to prohibit the image forming portion from performing image formation on the print data before the print data is subjected to image formation by the image forming portion, when a prescribed time has passed since the print data was received or when an input of an instruction to protect the print data is accepted, and to store the print data in a storage device, and to allow the image forming portion to perform image formation on the print data in response to accepting a log-in instruction.
Owner:KONICA MINOLTA BUSINESS TECH INC
Control method for performing management on U disk after access into industrial control system network
InactiveCN104680055AIncrease costAvoid disclosure of confidential informationInternal/peripheral component protectionDigital data authenticationControl networkIndustrial control system
The invention discloses a control method for performing management on a U disk after access into an industrial control system network. The control method is characterized in that a strategy server, a client terminal and a secure U disk are adopted; the strategy server is used for issuing a strategy to the customer terminal; the secure U disk accesses the industrial control system network; the client terminal controls the secure U disk according to the strategy issued to the client terminal by the strategy server. The control method has the advantages that viruses are prevented from invading an industrial control network; the confidential information of the industrial control network is prevented from leaking; the secure U disk can be used for safely sharing data between client terminals in the industrial control network; when the secure U disk is separated from the industrial control system network, a user cannot open or use the U disk, so that the invasion of viruses is avoided; any U disk can be made into the secure U disk via processing with the method, the cost is low, and operation is easy.
Owner:北京威努特技术有限公司
Image forming apparatus performing image formation on print data, image processing system including plurality of image forming apparatuses, print data output method executed on image forming apparatus, and print data output program product
ActiveUS7729000B2Prevent leakageAvoid disclosure of confidential informationVisual presentation using printersComputer security arrangementsImaging processingComputer graphics (images)
In order to prevent leakage of confidential information, MFP includes a communication I / F to receive print data, an image forming portion to perform image formation on print data, and a CPU to prohibit the image forming portion from performing image formation on the print data before the print data is subjected to image formation by the image forming portion, when a prescribed time has passed since the print data was received or when an input of an instruction to protect the print data is accepted, and to store the print data in a storage device, and to allow the image forming portion to perform image formation on the print data in response to accepting a log-in instruction.
Owner:KONICA MINOLTA BUSINESS TECH INC
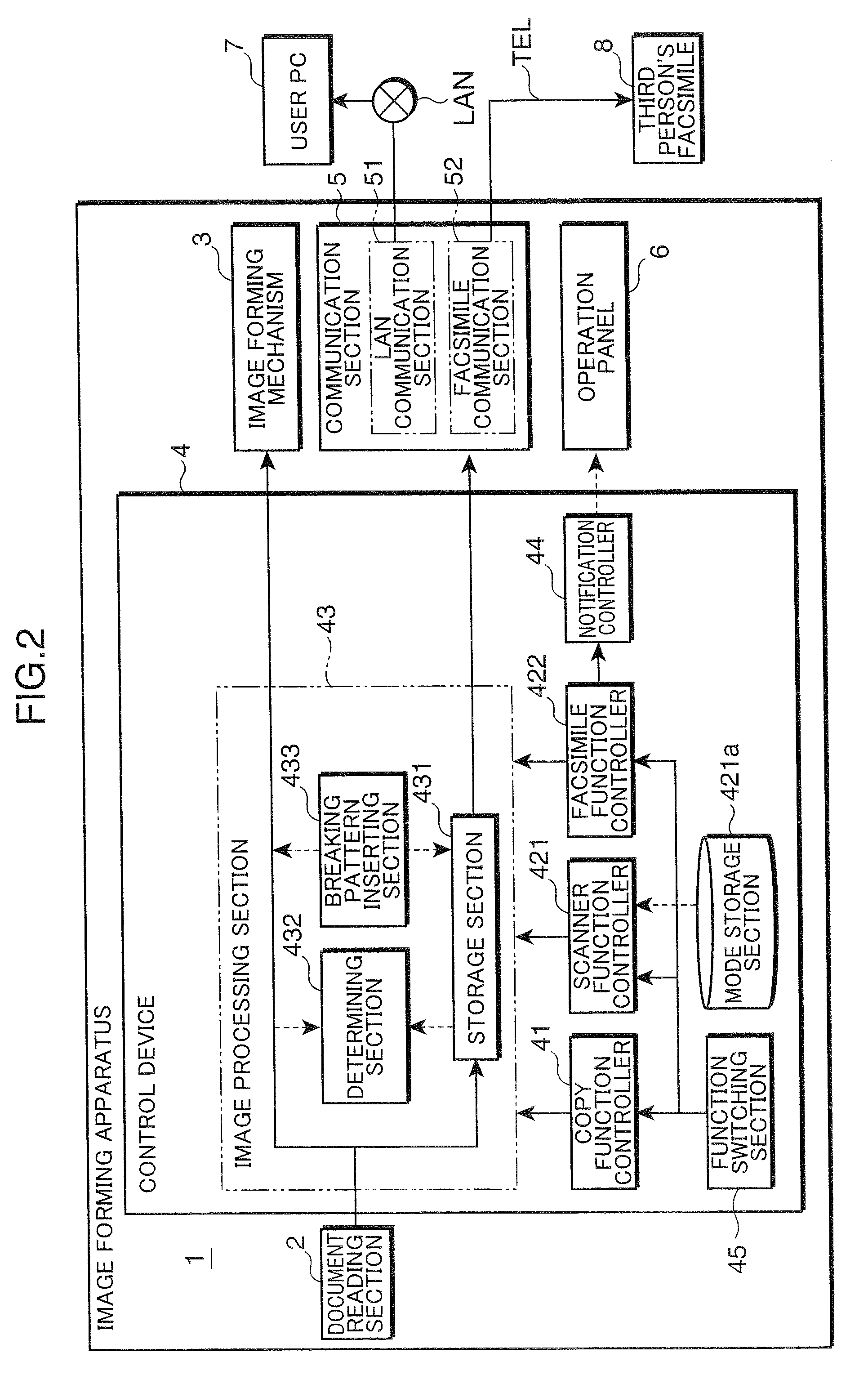
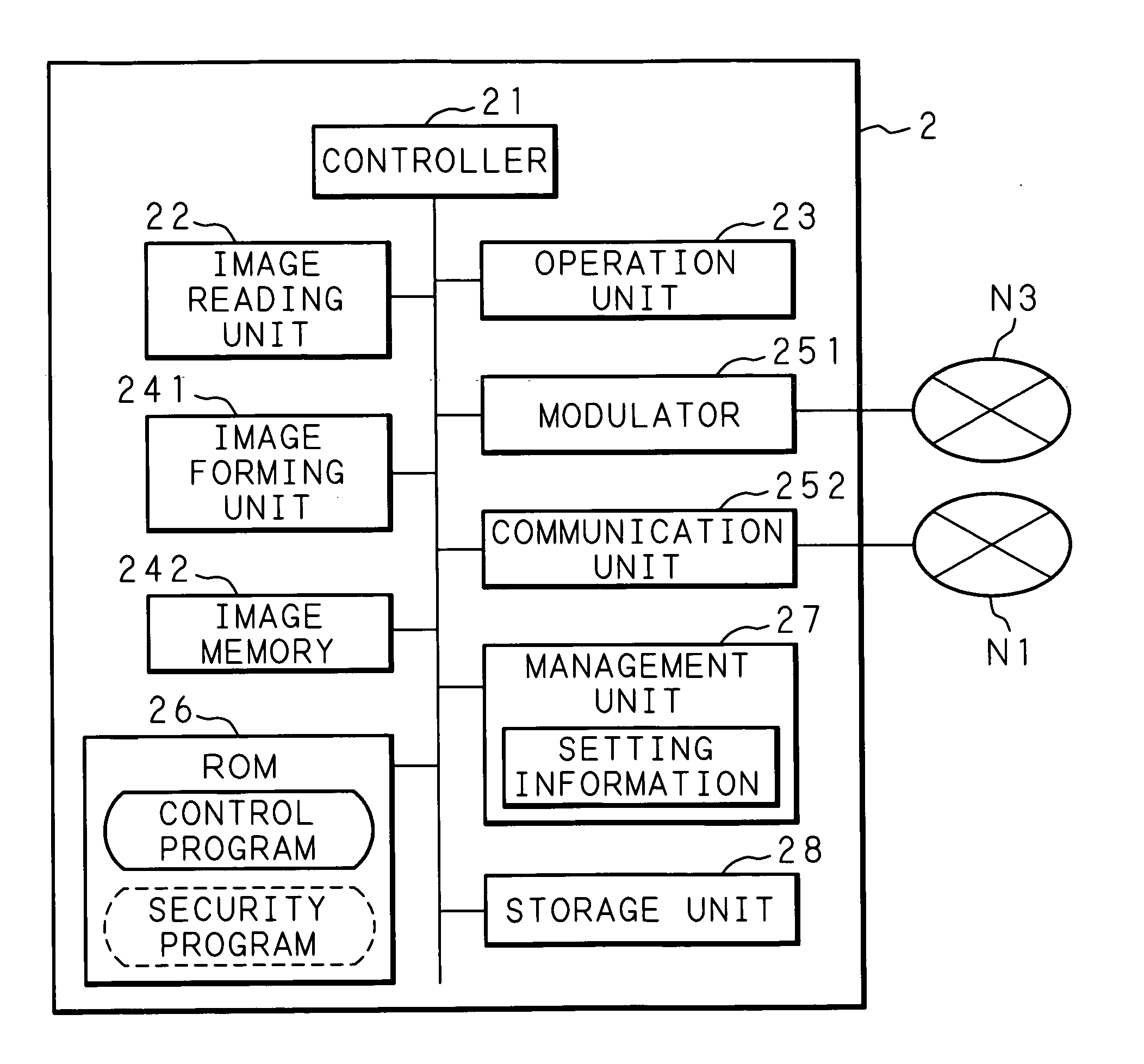
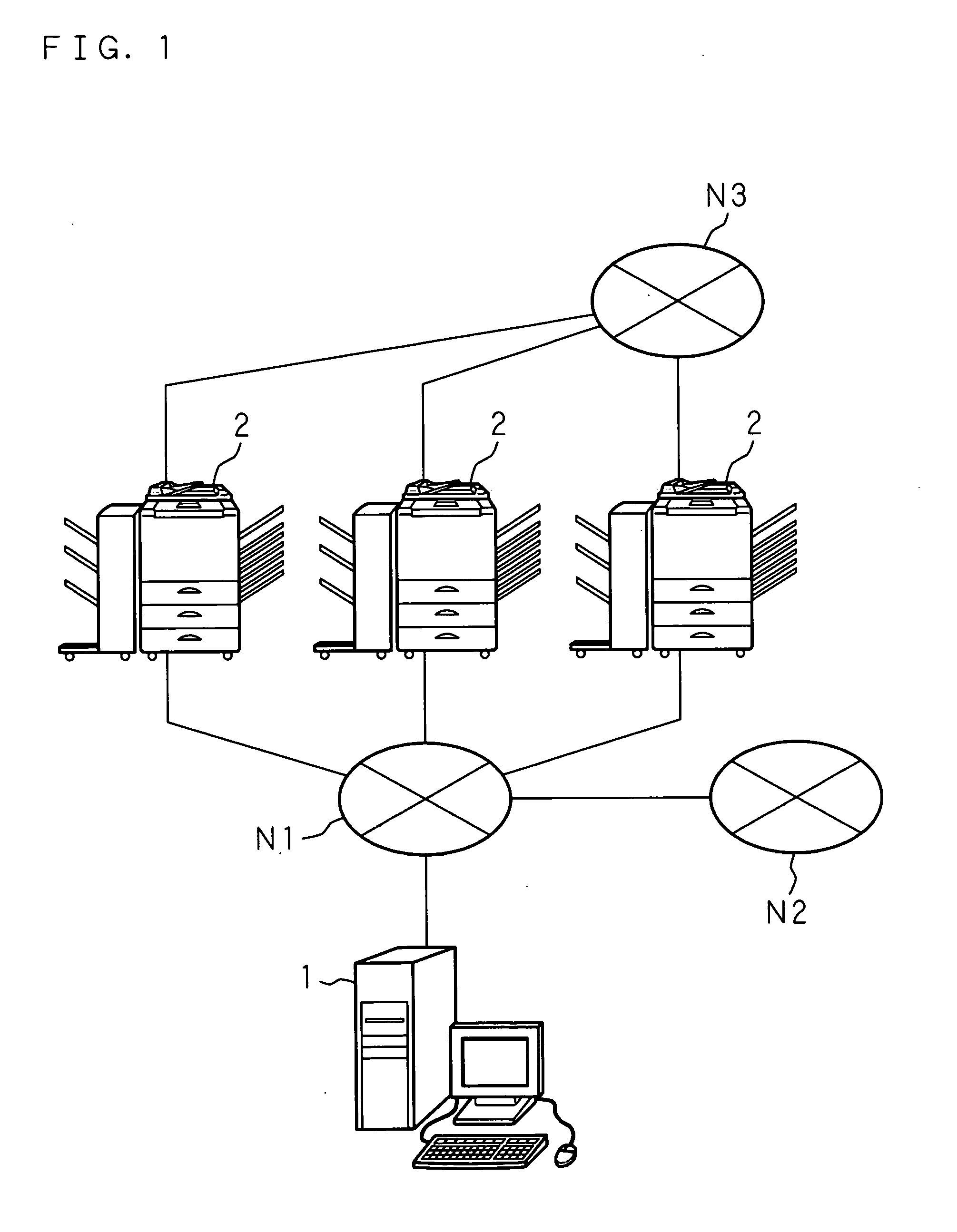
Image processing system, image processing apparatus and server in the image processing system, and data control method and storage medium storing program thereof
InactiveUS20120275647A1Avoid disclosure of confidential informationLeakage of confidential information can be preventedCharacter and pattern recognitionComputer security arrangementsData controlImaging processing
When an image processing apparatus transmits information about image data stored therein to a server, the server determines whether or not the image data contains confidential information, and transmits the determination result to the image processing apparatus. When the image processing apparatus receives, from the server, determination result indicating whether or not the image data contains confidential information, then if the determination result indicates that the image data contains specific information, the image processing apparatus limits use of the image data.
Owner:CANON KK
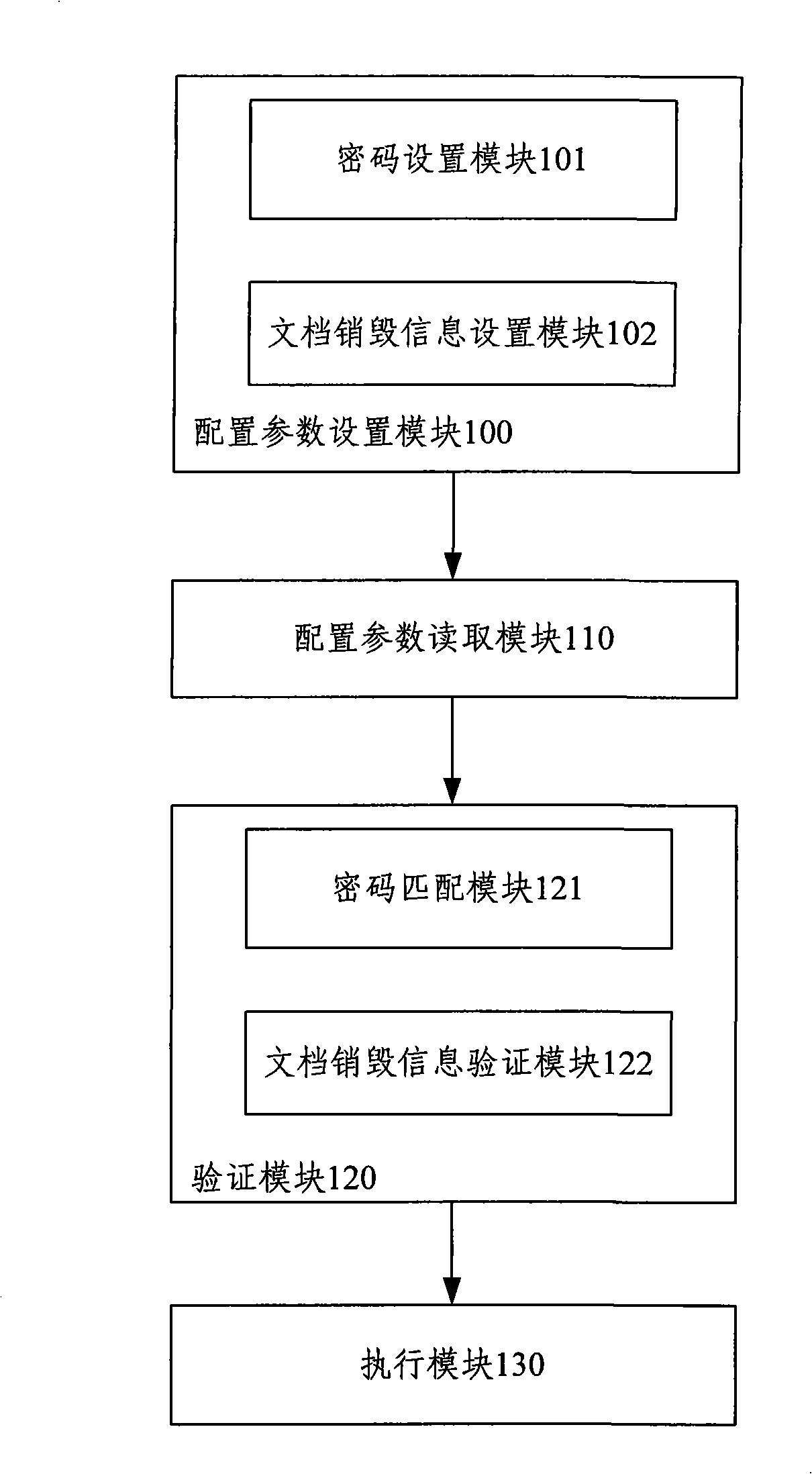
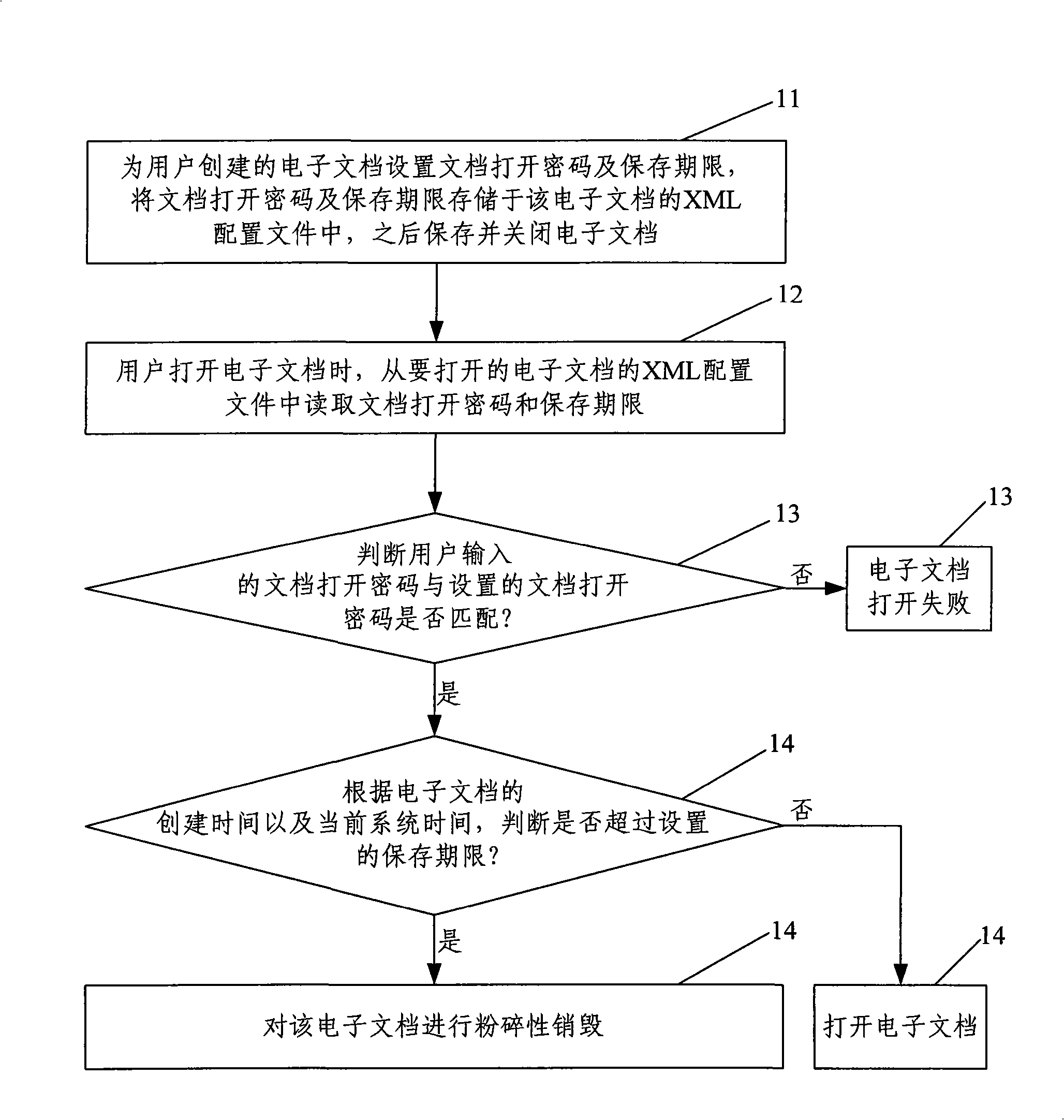
Method for protecting electronic document information and system thereof
InactiveCN101539972AAvoid disclosure of confidential informationRealize automatic shredding destructionDigital data protectionElectronic documentDigital document
The invention provides a method for protecting electronic document information. The method comprises the following steps: A. security configuration information is set for an electronic document which is built for users, the set security configuration information is memorized in the configuration file of the electronic document, then the electronic document is memorized and closed; B. when users open the electronic document, the security configuration information of the electronic document is read from the configuration file of the opened electronic document; C. security parameter information which is inputted by the users and the read security configuration information of the electronic document are matched, if the match is successful, the electronic document is opened; and if the match is fail, the electronic document is destroyed in a comminuting way. The invention also provides a system for protecting the electronic document information, comprising a configuration parameter setting module, a configuration parameter reading module, a verification module and an execution module. The method and the system can prevent confidential information from being leaked, since passwords are decoded or cancelled and electronic documents are maliciously resumed.
Owner:CE DONGLI TECH CO LTD
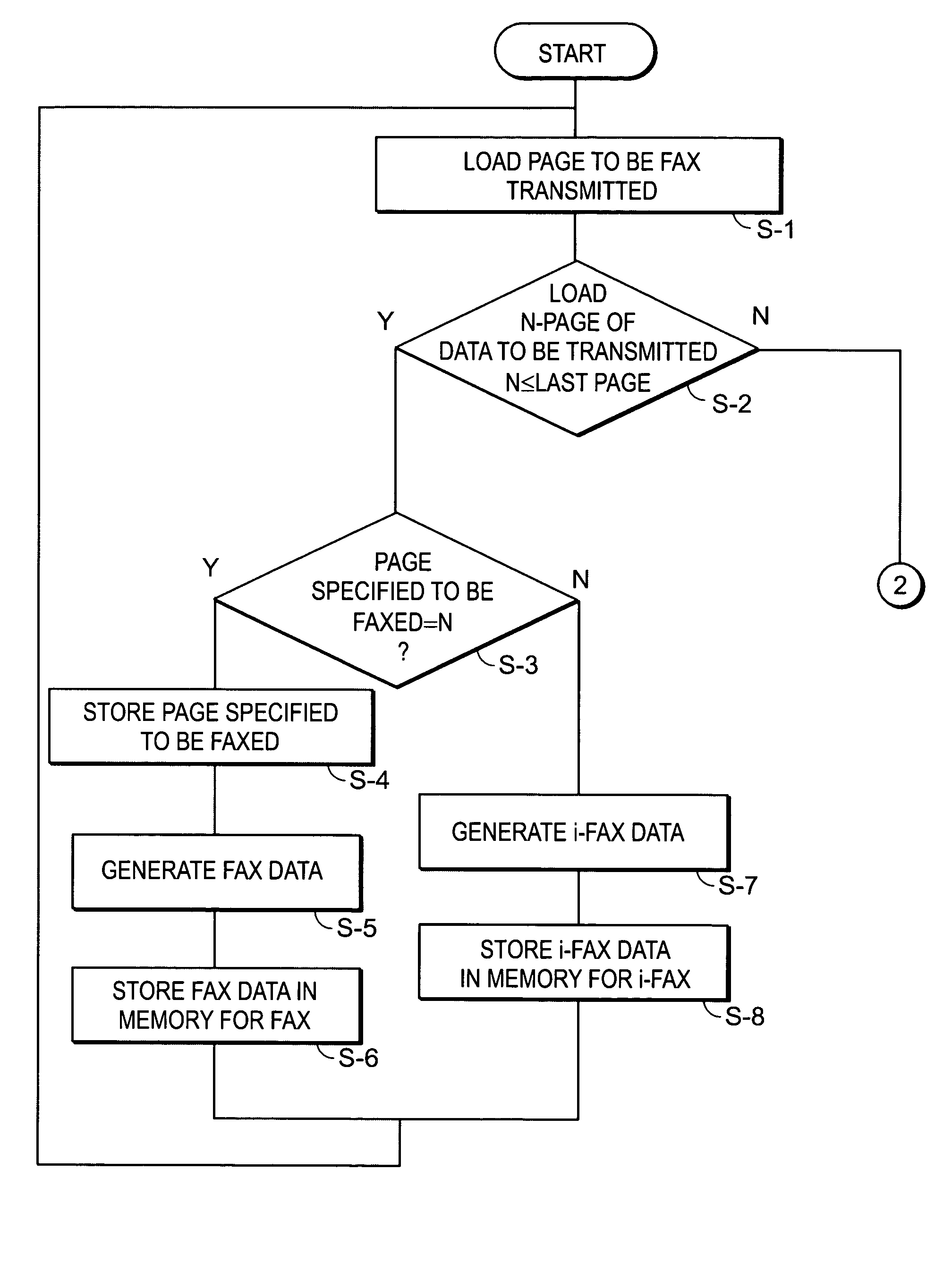
Image communication apparatus
InactiveUS20100002268A1Leakage of confidential information can be preventedReduce communication costsPictoral communicationInformation processingComputer hardware
An information processing apparatus facsimile-transmits specified pages among images constituted by multiple pages, and transmits remaining pages by Internet FAX. The information processing apparatus transmits the specified pages to a FAX number specified by a user, by facsimile transmission. Next, the information processing apparatus transmits the remaining pages to a specified mail address by Internet FAX. Thus, the images are transmitted by the two kinds of FAX transmission to realize both of reduction in communication cost and prevention of leakage of confidential information.
Owner:SHARP KK
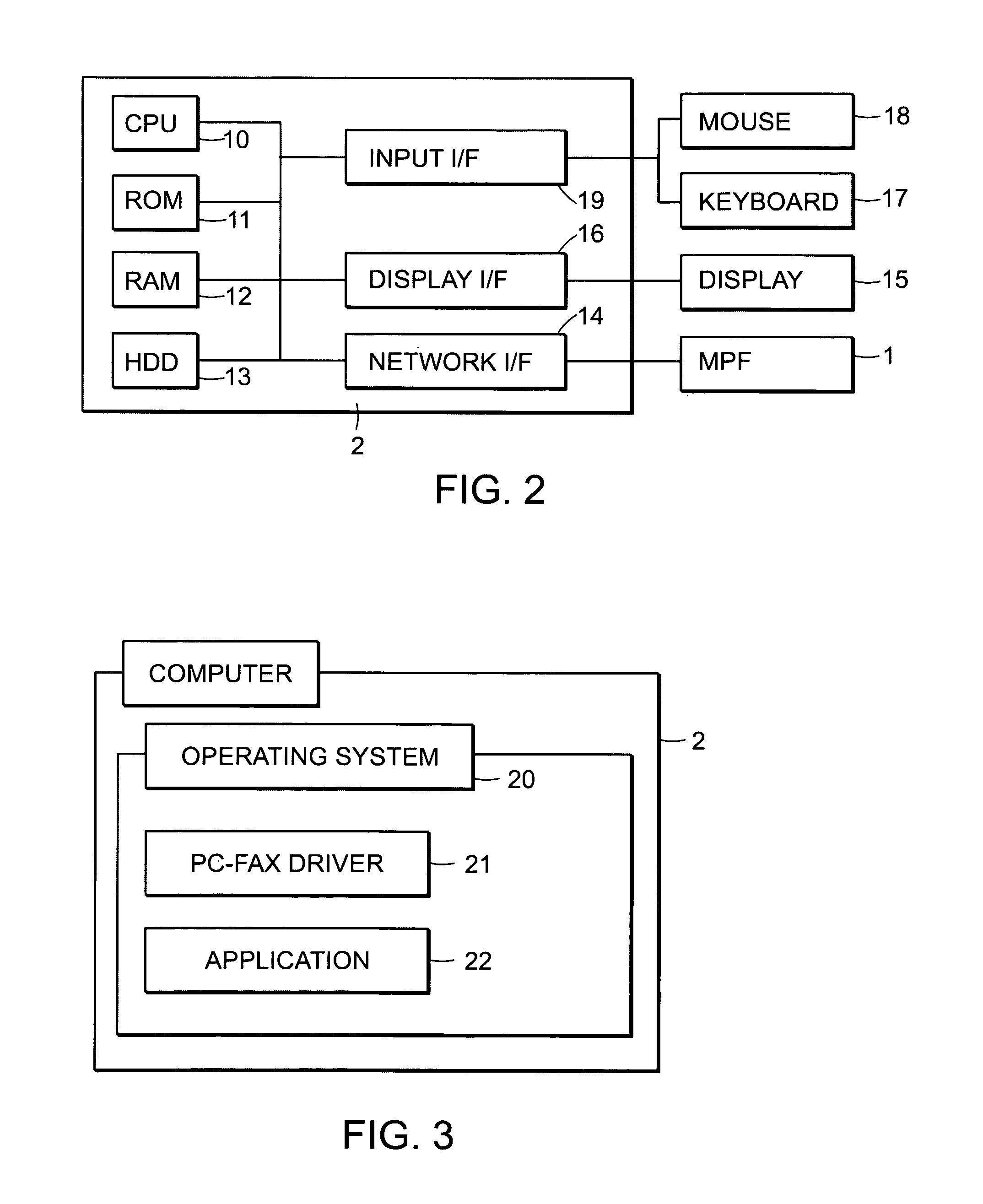
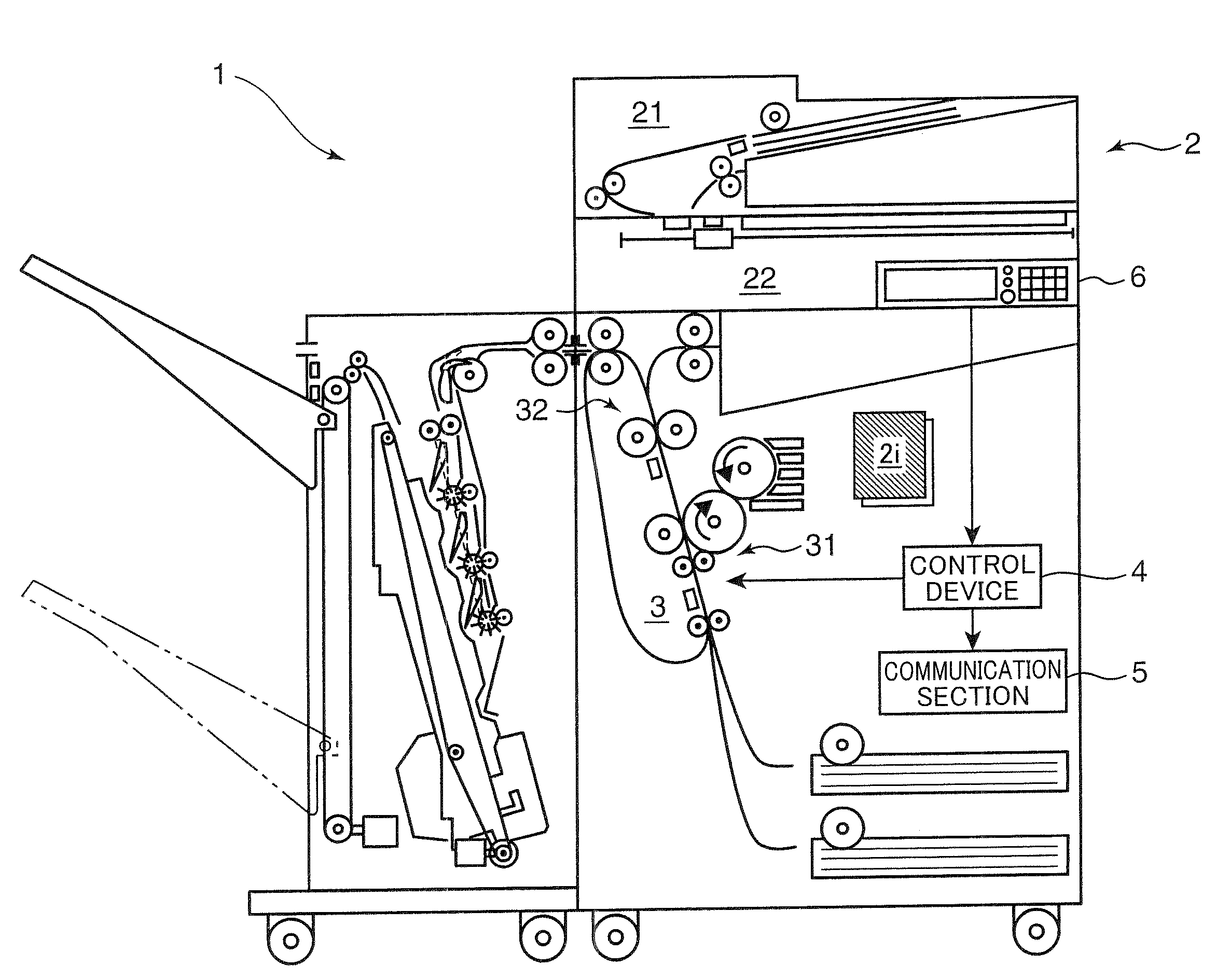
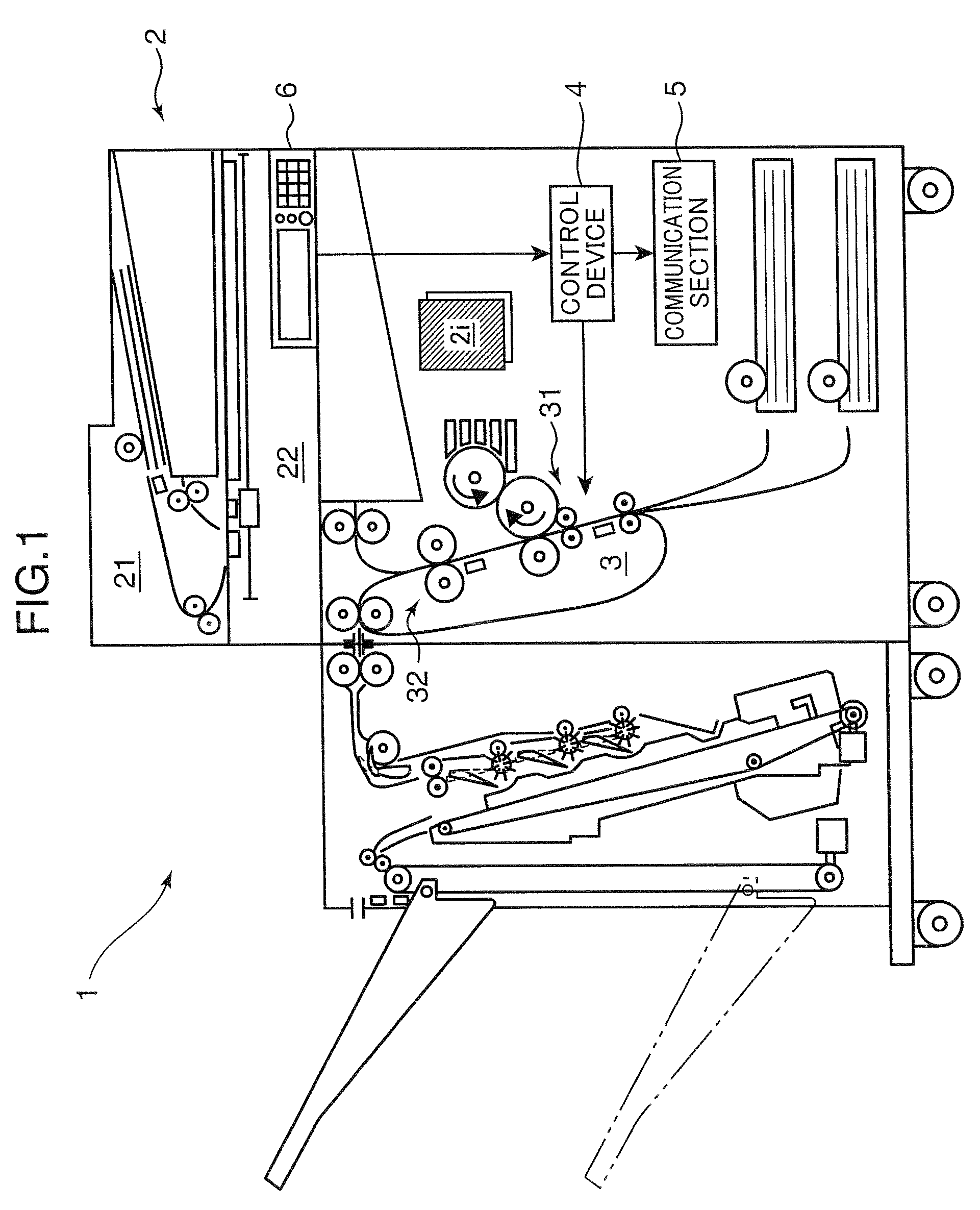
Image forming apparatus
InactiveUS20090003856A1Lowering of communicationIncrease productivityElectrographic process apparatusPictoral communicationComputer graphics (images)Image formation
A complex machine includes an image reading section for reading an image from a document. A determining section determines whether the read image includes a predetermined confidential pattern. A breaking pattern inserting section inserts a breaking pattern to the document image to break the document image. A printing section can print an image onto a recording sheet and a transmitting section can transmit the image read by the image reading section to external equipment. A controller controls the printing section to print a document image, to which the breaking pattern is inserted by the breaking pattern inserting section, if the copy function is executed. However, the controller prohibits the transmission section from transmitting the document image to outside if the facsimile function or the scanner function is executed and if the determining section determines that the image read by the image reading section includes the confidential pattern.
Owner:KYOCERA DOCUMENT SOLUTIONS INC
Image forming apparatus
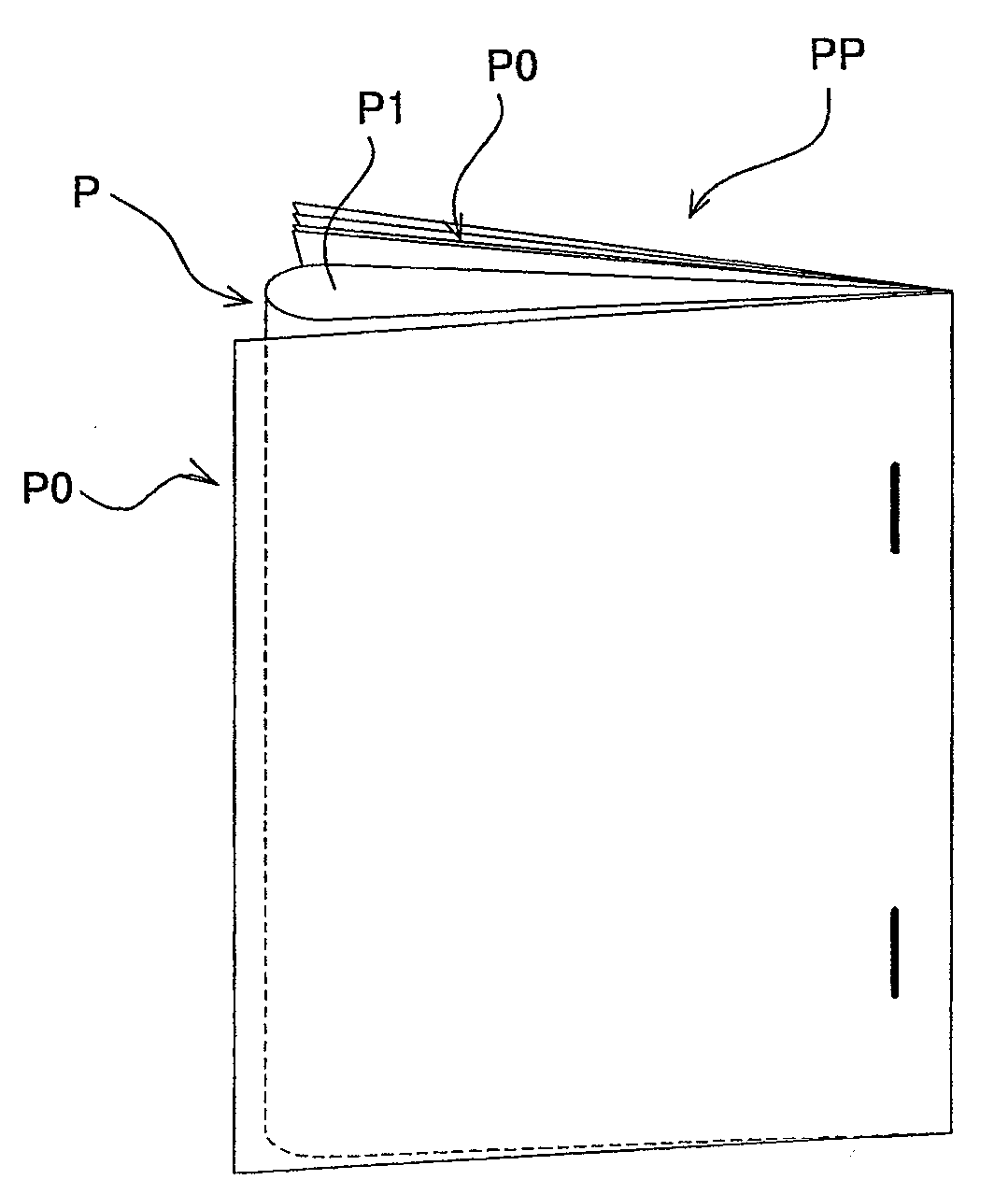
ActiveUS20100001451A1Inhibition of informationAvoid disclosure of confidential informationFolding thin materialsElectrographic process apparatusComputer graphics (images)Paper based
The image forming apparatus includes: an image processor; an image forming portion for forming images on recording paper based on the image data output from the image processor; a folding mechanism for folding the recording paper with images formed by the image forming portion when the input image information is confidential image information; and a stapling mechanism for binding the recording paper folded by the folding mechanism, at the end part when the input image information is confidential image information. When the input image information is confidential image information, the image forming portion outputs the pouch-binding image data for a pouch-bound image to be formed on the facing pages of the recording paper that is folded by the folding mechanism, by editing the layout of the confidential image.
Owner:SHARP KK
Image forming apparatus and image forming system
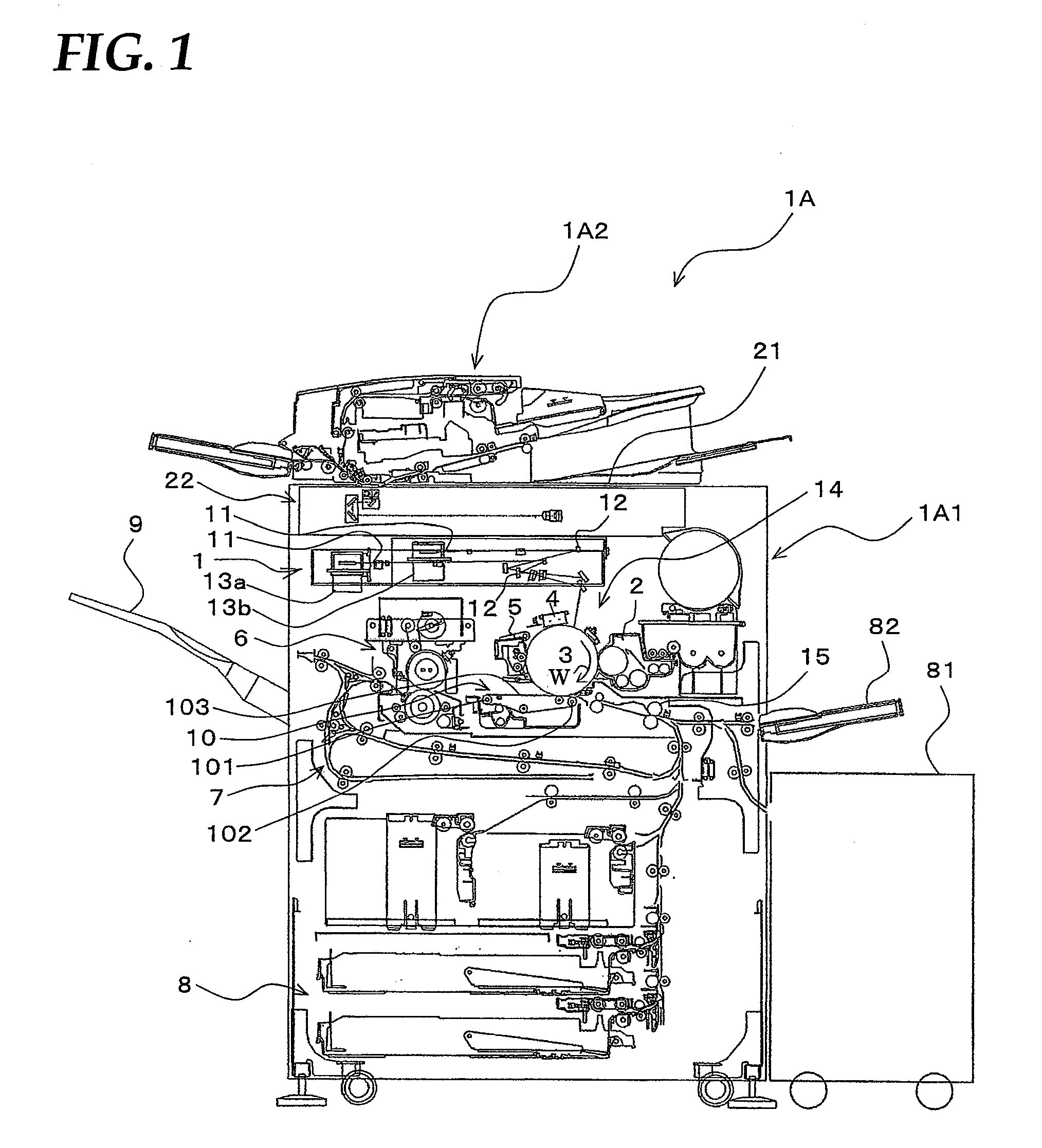
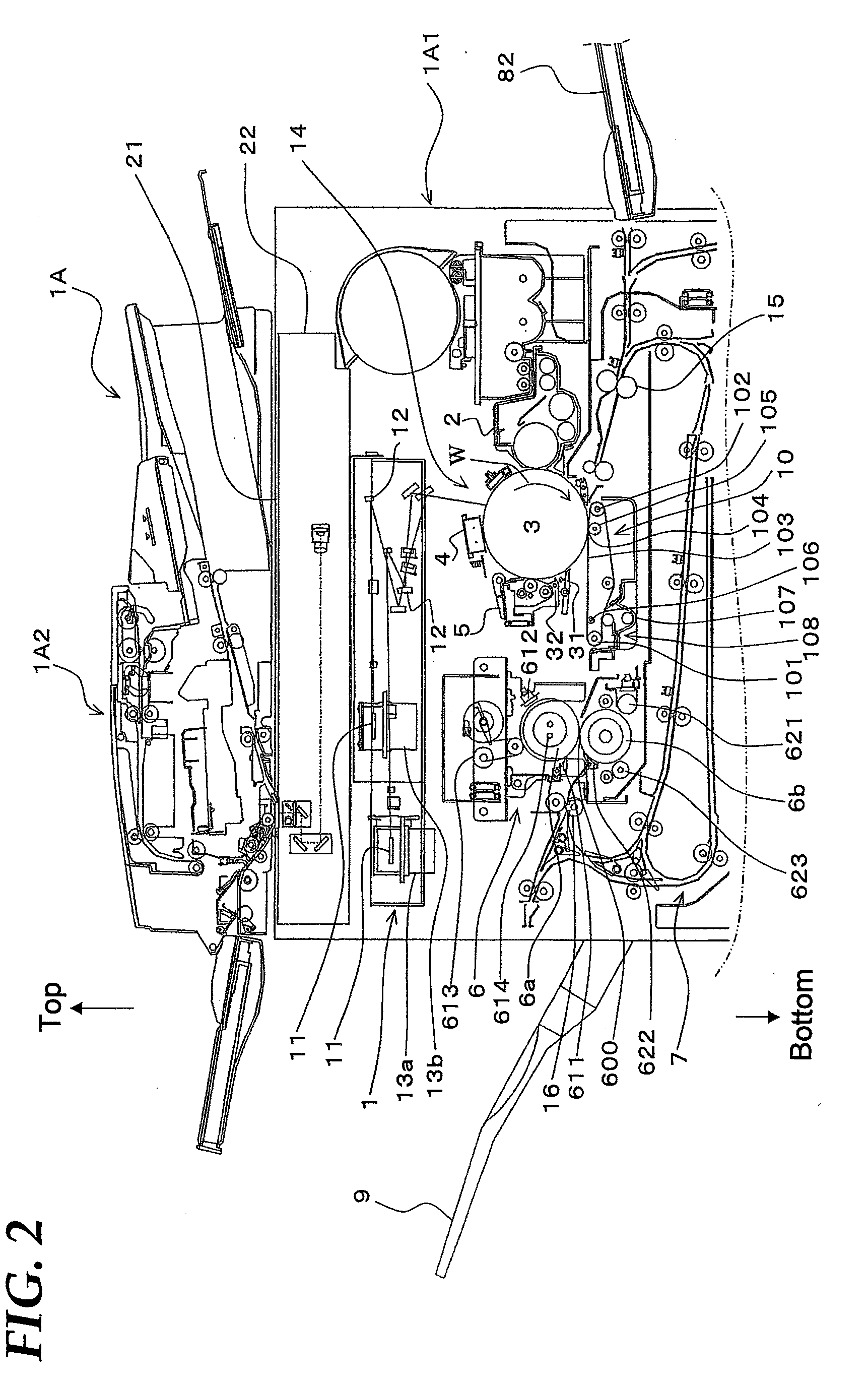
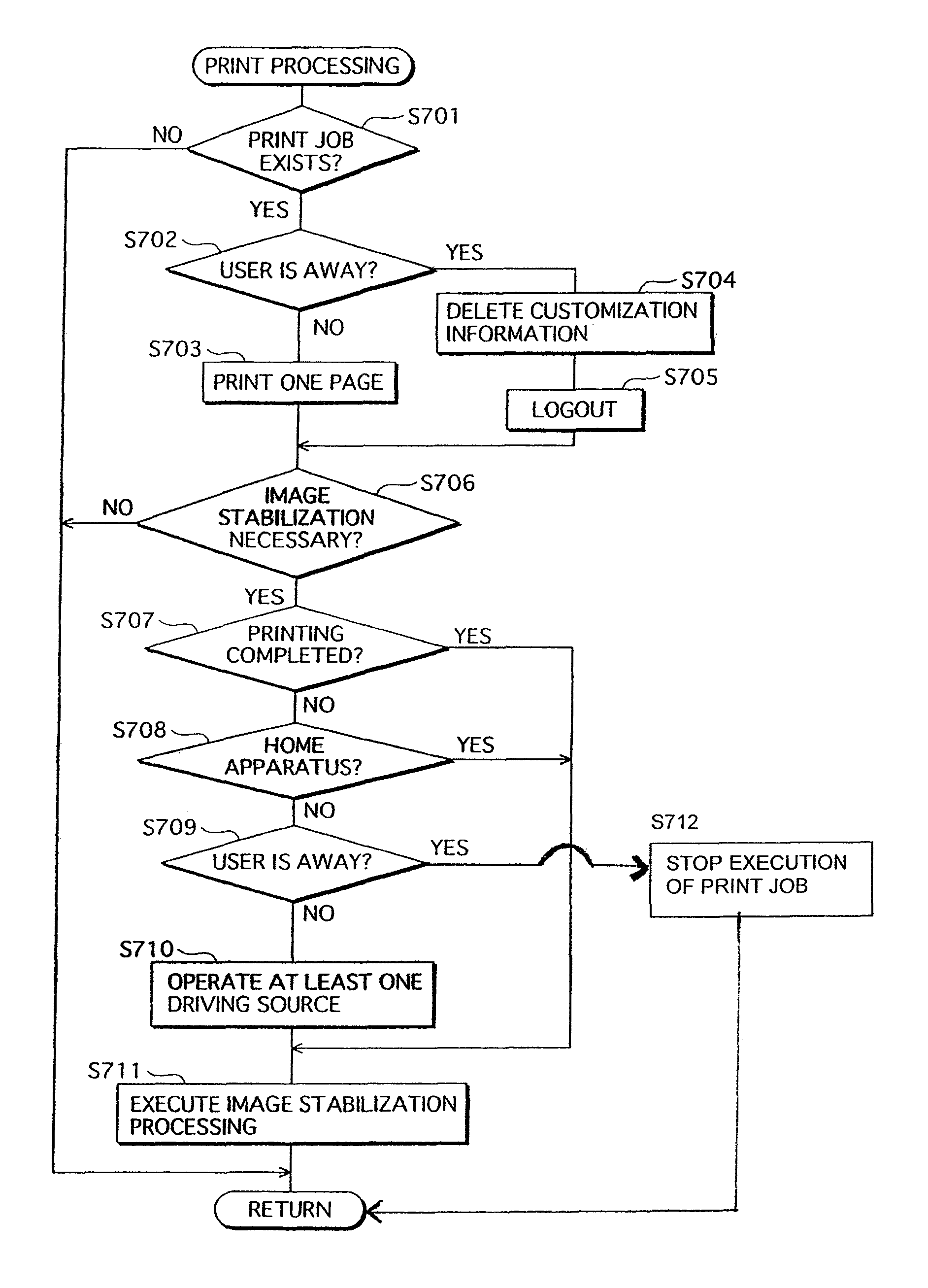
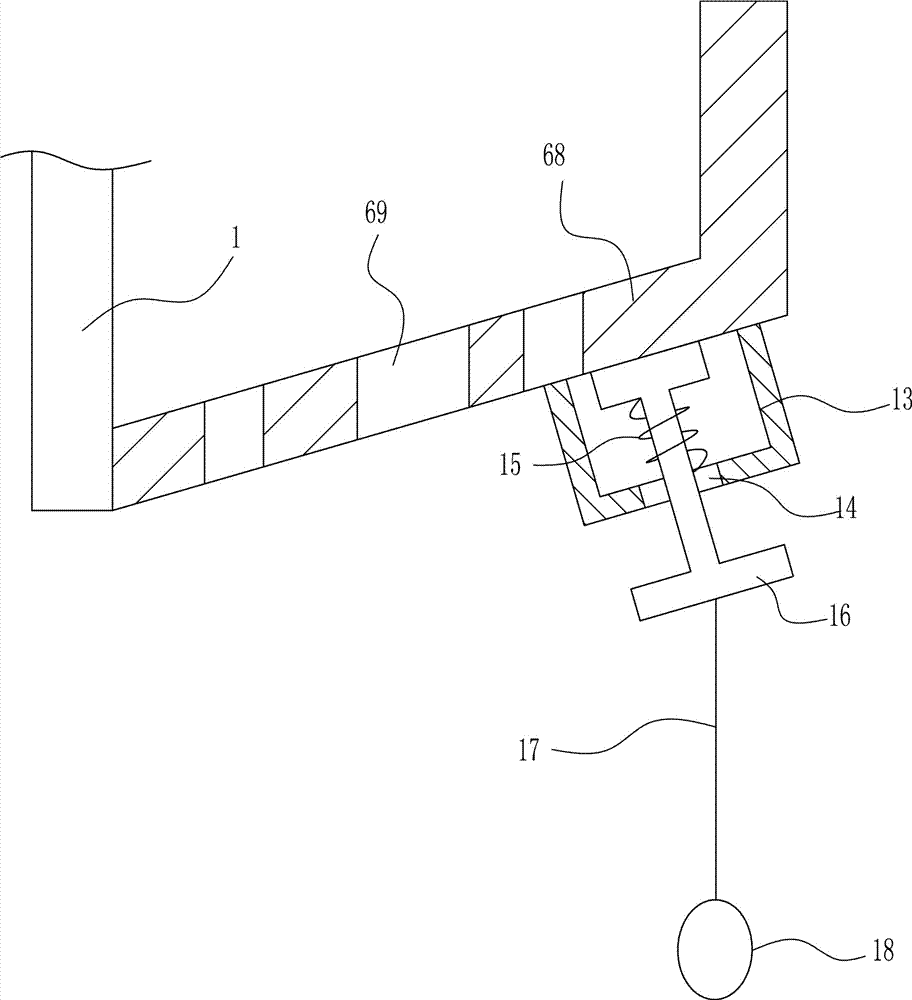
InactiveUS8629998B2Avoid disclosure of confidential informationEnsure convenienceDigitally marking record carriersDigital computer detailsImage formationImage stabilization
If image stabilization becomes necessary while an MFP is executing a print job received from a user, the MFP performs the image stabilization while emitting an operation sound if the user has not moved away from the MFP. Also, if the user has moved away from the MFP, the MFP stops the print job and logs the user out.
Owner:KONICA MINOLTA INC
Multistage demagnetizing and crushing device of computer hardware storage equipment
InactiveCN106881166AAvoid disclosure of confidential informationCompletely brokenGrain treatmentsRappingOptical disc
The invention relates to a demagnetizing and crushing device and particularly relates to a multistage demagnetizing and crushing device of computer hardware storage equipment. The technical problem to be solved by the invention is to provide the multistage demagnetizing and crushing device of the computer hardware storage equipment, by which the computer hardware storage equipment can be thoroughly destroyed. In order to solve the technical problem, the invention provides such a multistage demagnetizing and crushing device of the computer hardware storage equipment. The multistage demagnetizing and crushing device comprises a crushing box and the like; the bottom of the crushing box is connected with a discharging pipe on which a valve is arranged; the middle inside the crushing box is connected with a filter screen; the top of the filter screen is connected with a first-stage crushing mechanism; and the right side of the crushing box is connected with a feeding mechanism. According to the multistage demagnetizing and crushing device, storage equipment such as an optical disc, a U disc and an IC card is poured into the crushing box by a material transportation box with an inclined surface, and meanwhile, a pull ring is pulled by a hand, so that the bottom wall of the material transportation box is rapped by a rapping bar.
Owner:深圳金霸城电子有限公司
Image processing system, image processing apparatus and server in the image processing system, and data control method and storage medium storing program thereof
InactiveUS8818032B2Avoid disclosure of confidential informationLeakage of confidential information can be preventedCharacter and pattern recognitionComputer security arrangementsData controlImaging processing
When an image processing apparatus transmits information about image data stored therein to a server, the server determines whether or not the image data contains confidential information, and transmits the determination result to the image processing apparatus. When the image processing apparatus receives, from the server, determination result indicating whether or not the image data contains confidential information, then if the determination result indicates that the image data contains specific information, the image processing apparatus limits use of the image data.
Owner:CANON KK
Information processing apparatus with hibernation function, control method therefor, and storage medium storing control program therefor
ActiveUS9384355B2Avoid disclosure of confidential informationDigital data protectionInformation processingVolatile memory
An information processing apparatus that is capable of preventing leakage of confidential information from data saved on a nonvolatile memory even when the apparatus makes a transition to a hibernation state. The information processing apparatus with a hibernation function has a volatile memory and a nonvolatile memory. A security-area determination unit determines whether a memory area allocated to the volatile memory is a security area. A transition unit to save data saved on a memory area of the volatile memory that is determined as a non-security area by the security-area determination unit and not to save data saved on a memory area of the volatile memory that is determined as a security area, when going to a hibernation state. A resuming unit writes the data that is saved on the nonvolatile memory back to the volatile memory at the time of resuming from the hibernation state.
Owner:CANON KK
Image forming apparatus
ActiveUS8091881B2Inhibition of informationAvoid disclosure of confidential informationElectrographic process apparatusRotary pressesComputer graphics (images)Image formation
The image forming apparatus includes: an image processor; an image forming portion for forming images on recording paper based on the image data output from the image processor; a folding mechanism for folding the recording paper with images formed by the image forming portion when the input image information is confidential image information; and a stapling mechanism for binding the recording paper folded by the folding mechanism, at the end part when the input image information is confidential image information. When the input image information is confidential image information, the image processor outputs the pouch-binding image data for a pouch-bound image to be formed on the facing pages of the recording paper that is folded by the folding mechanism, by editing the layout of the confidential image.
Owner:SHARP KK
Data processing system, storage device and computer program
InactiveUS20050192928A1Prevent leakageEasy to implementDigital data processing detailsUnauthorized memory use protectionData processing systemComputer printing
A data processing device, such as a facsimile machine or a printer, sends setting information necessary for processing data to a storage device for a back-up purpose, etc., and the storage device stores the setting information of the data processing device. The storage device classifies the data processing device according to whether or not the data processing device has a data protection function for protecting data to be processed, and stores the setting information in association with a type in which the data processing device is classified. When sending the setting information to a data processing device, the storage device sends the setting information corresponding to the type in which the data processing device as a recipient is classified.
Owner:SHARP KK
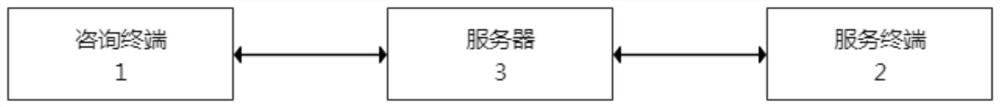
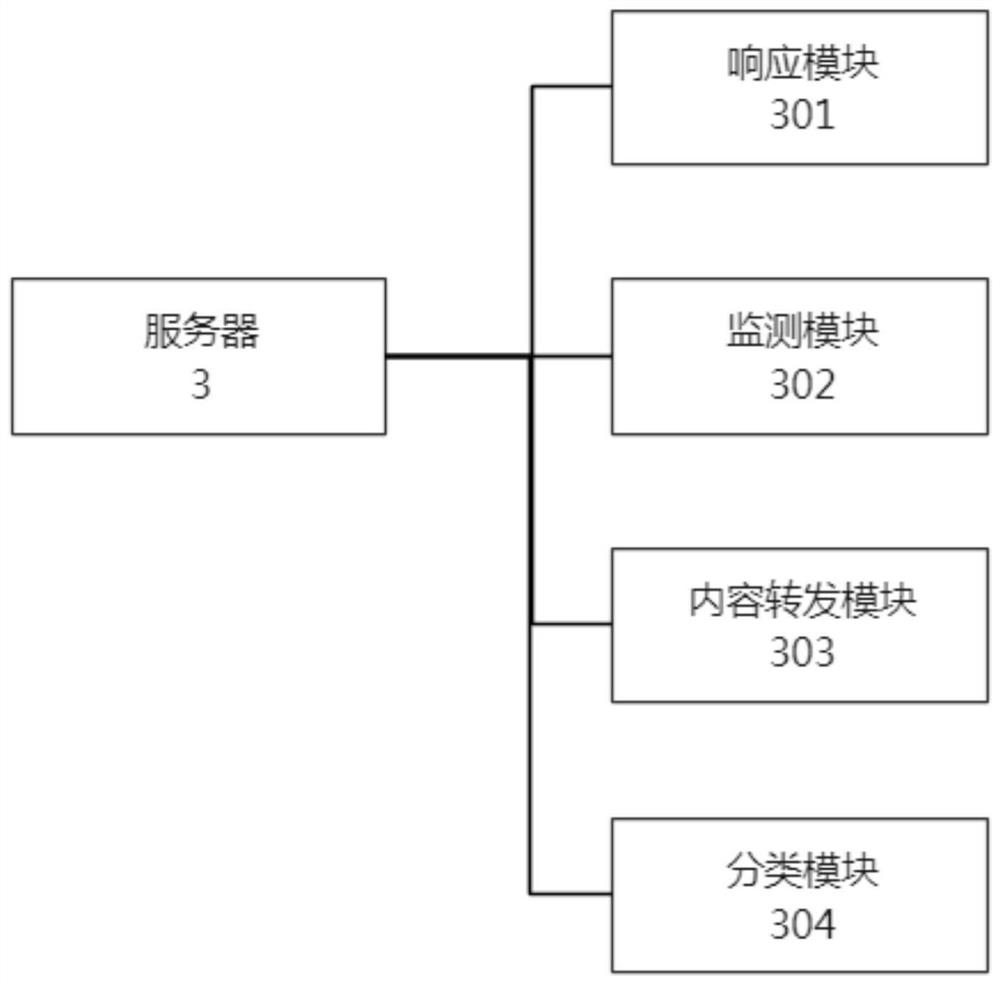
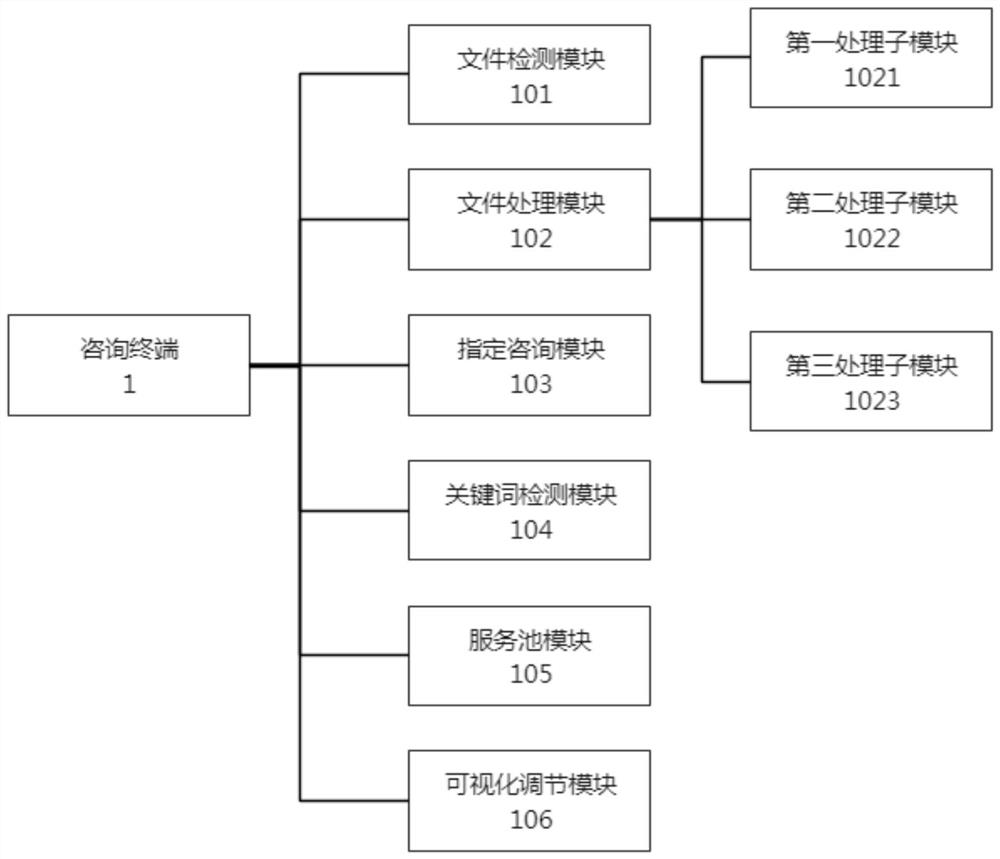
Intellectual property consultation service system
PendingCN113783951AImprove securityAvoid disclosure of confidential informationData processing applicationsDigital data protectionService systemInternet privacy
The invention provides an intellectual property consultation service system, which comprises a consultation terminal, a service terminal and a server; the consultation terminal and the service terminal are connected with the server through a network, and the consultation terminal is used by a user for initiating a consultation request and input consultation content, obtaining, detecting and analyzing the reply content of the service terminal, providing a service comparison function, and protecting the files sent by a user; the service terminal is used for an intellectual property worker to check consultation content, input reply content, receive a file sent by a user and set a service state; the server is used for responding to a consultation request of the consultation terminal, monitoring service states of different service terminals, sending the consultation request to a target service terminal according to the service states of the different service terminals, obtaining consultation content and forwarding the consultation content to the target service terminal, and obtaining reply content of the target service terminal and forwarding the reply content to the consultation terminal. The system can protect the safety of user information and help the user to quickly select a proper intellectual property agency.
Owner:海口创梦技术转移转化服务有限公司
Communication system, information processing system, image forming apparatus and portable information terminal device
InactiveUS20130229691A1Avoid disclosure of confidential informationDevices with bluetooth interfacesSubstation equipmentInformation processingCommunications system
Owner:SHARP KK
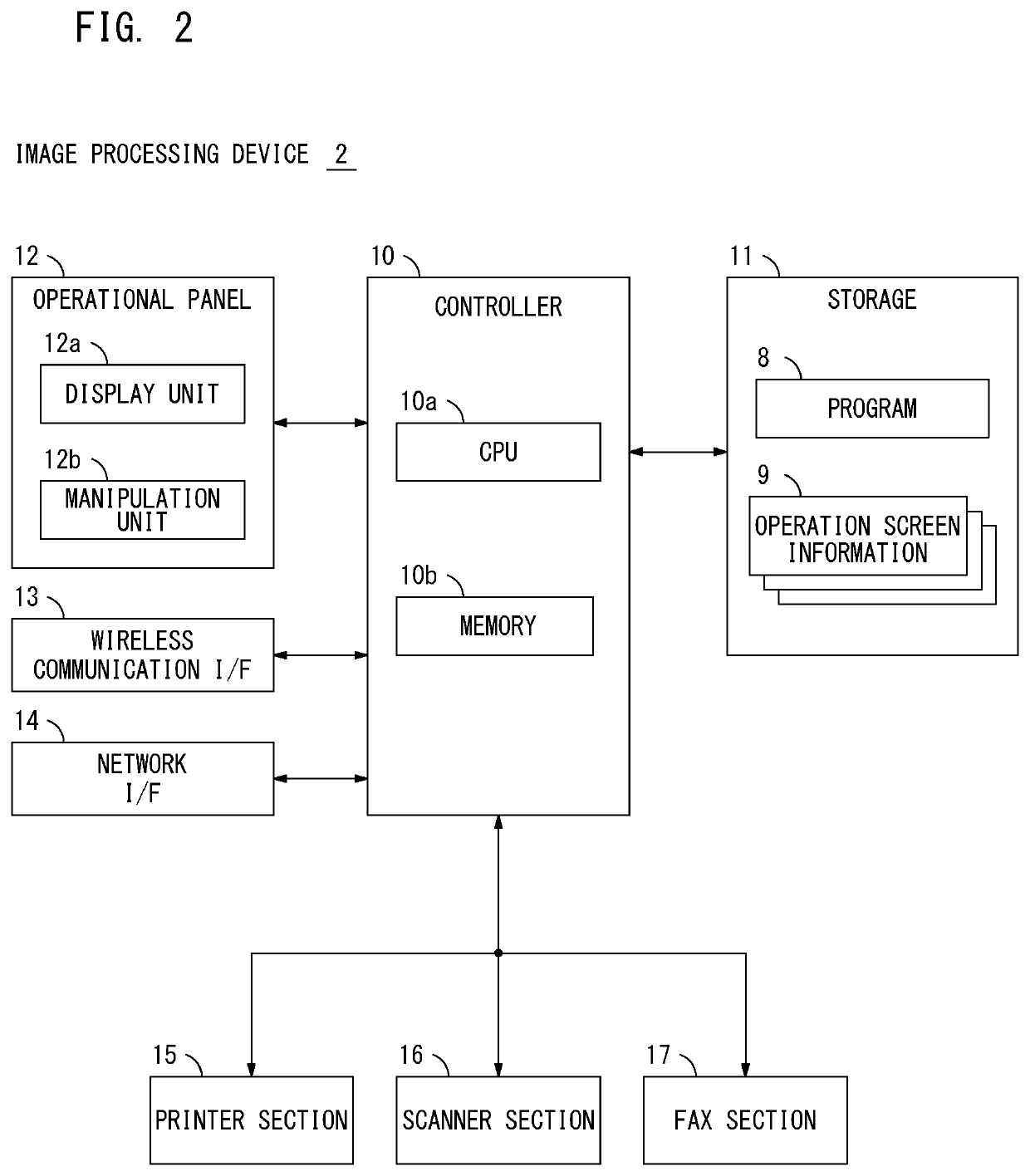
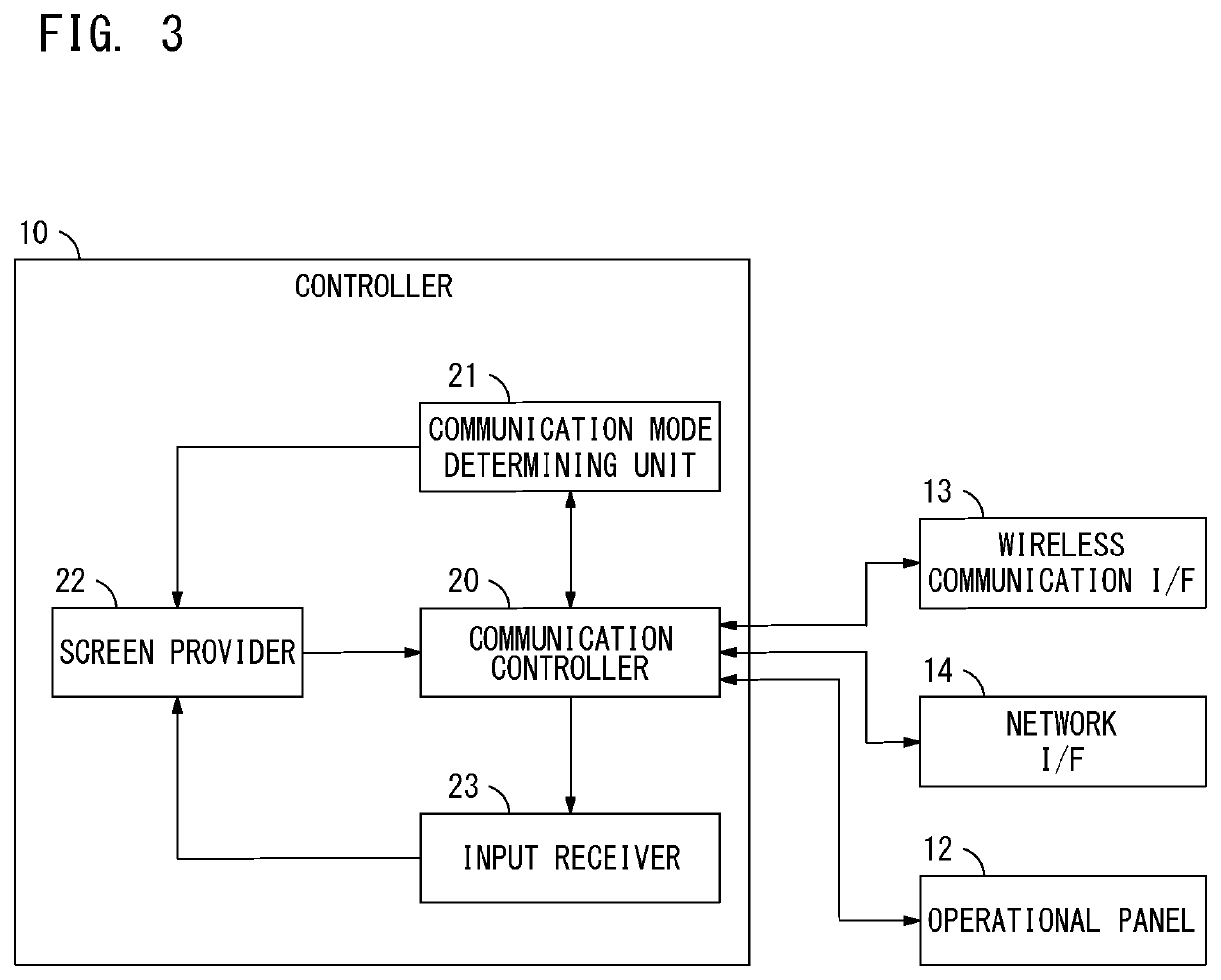
Image processing device, image processing system and non-transitory recording medium with communication-based access control
ActiveUS10540126B2Avoid disclosure of confidential informationImprove security levelComputer security arrangementsTransmissionComputer hardwareImaging processing
An image processing device that provides an operation terminal device with an operation screen and receives input information from the operation terminal device, comprising a hardware processor that: communicates with the operation terminal device in either a first communication mode or a second communication mode, which is different from the first communication mode; determines whether the communication with the operation terminal device is in the first communication mode or the second communication mode; and creates a first screen, which is the operation screen imposed with no limit, and provides the operation terminal device with the created first screen when the communication is determined to be made in the first communication mode, and creates a second screen, which is the operation screen imposed with a limit, and provides the operation terminal device with the created second screen when the communication is determined to be made in the second communication mode.
Owner:KONICA MINOLTA INC
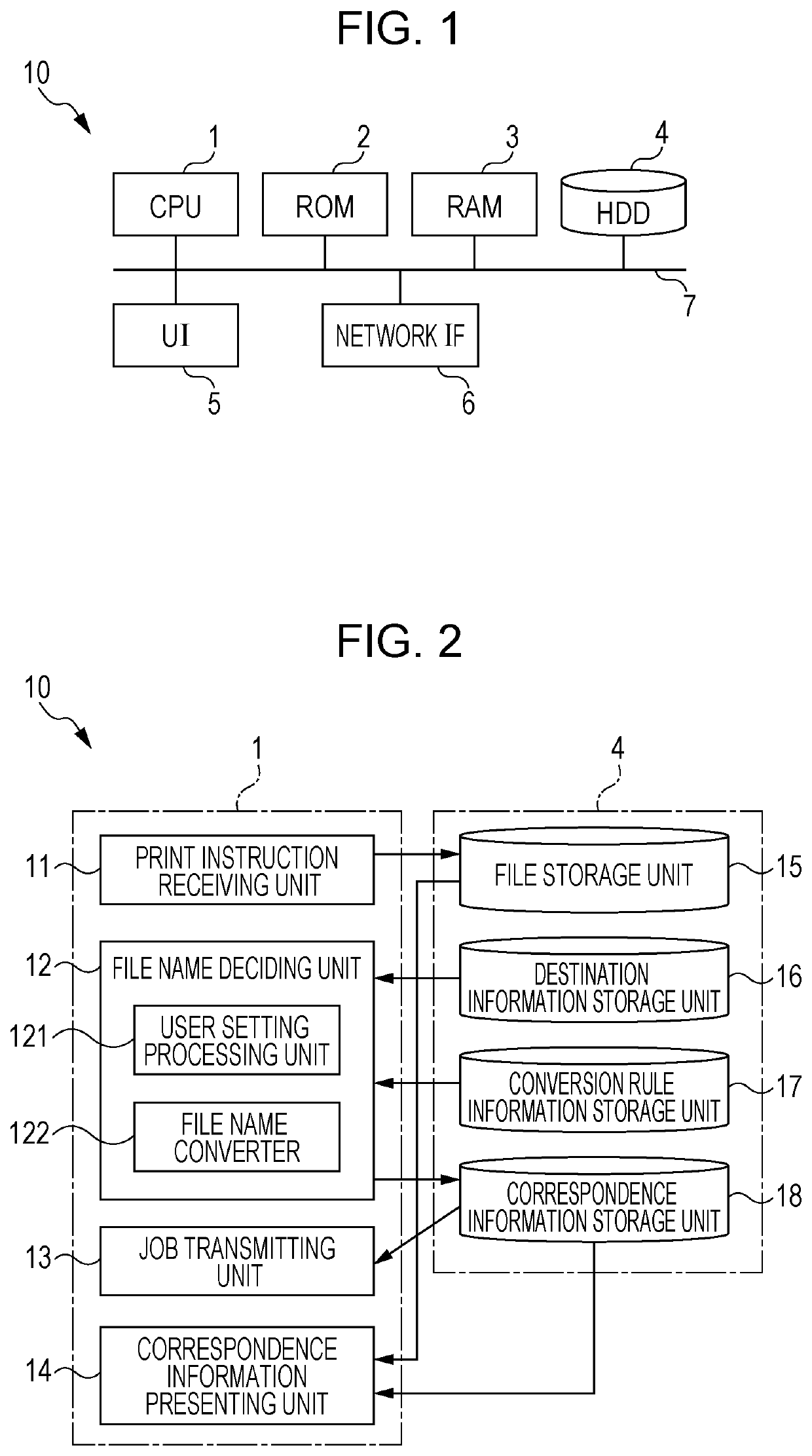
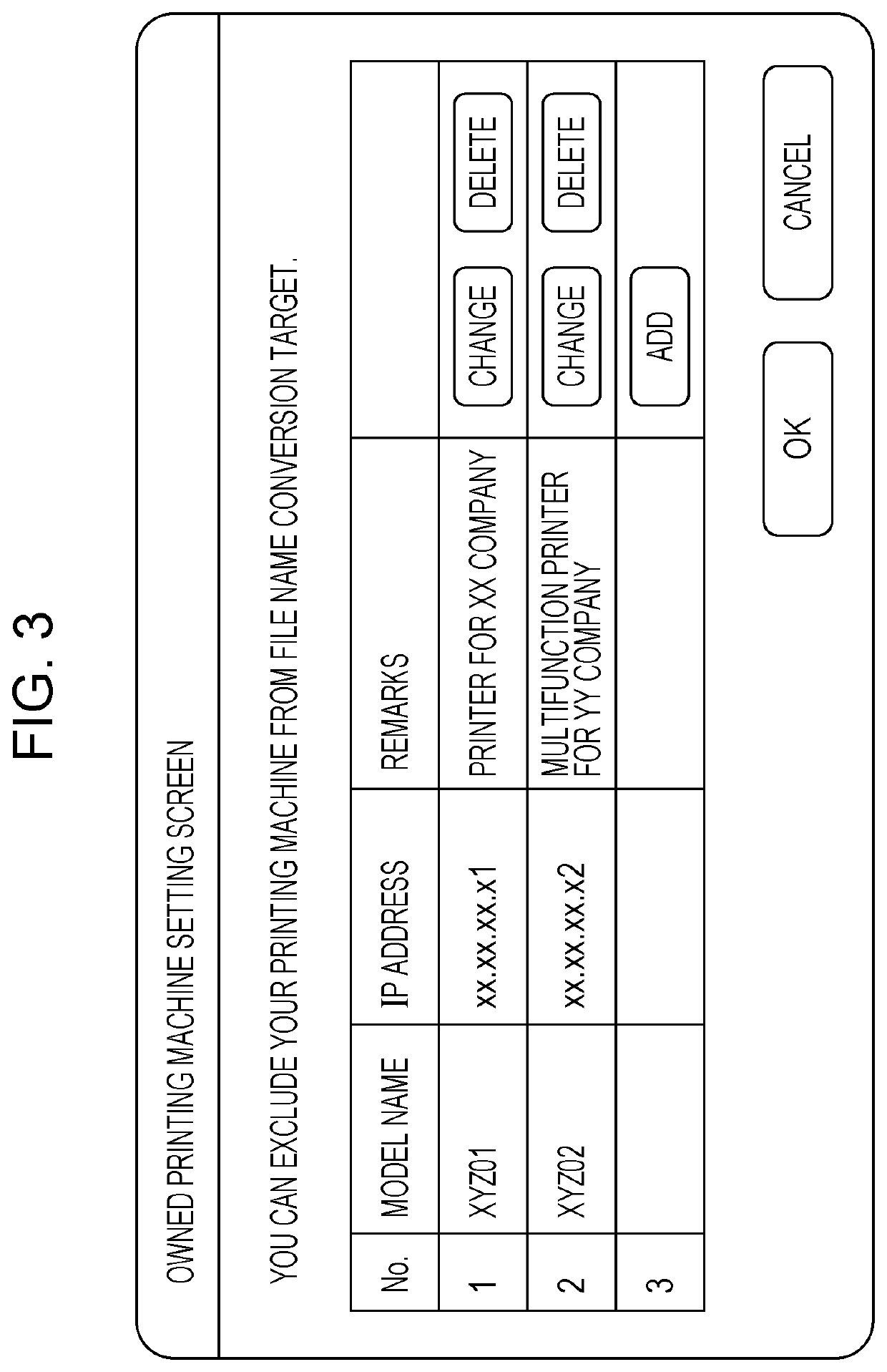
Information processing apparatus and non-transitory computer readable medium
PendingUS20210081359A1Prevent leakageAvoid Information LeakageFile system administrationFile/folder operationsInformation processingSoftware engineering
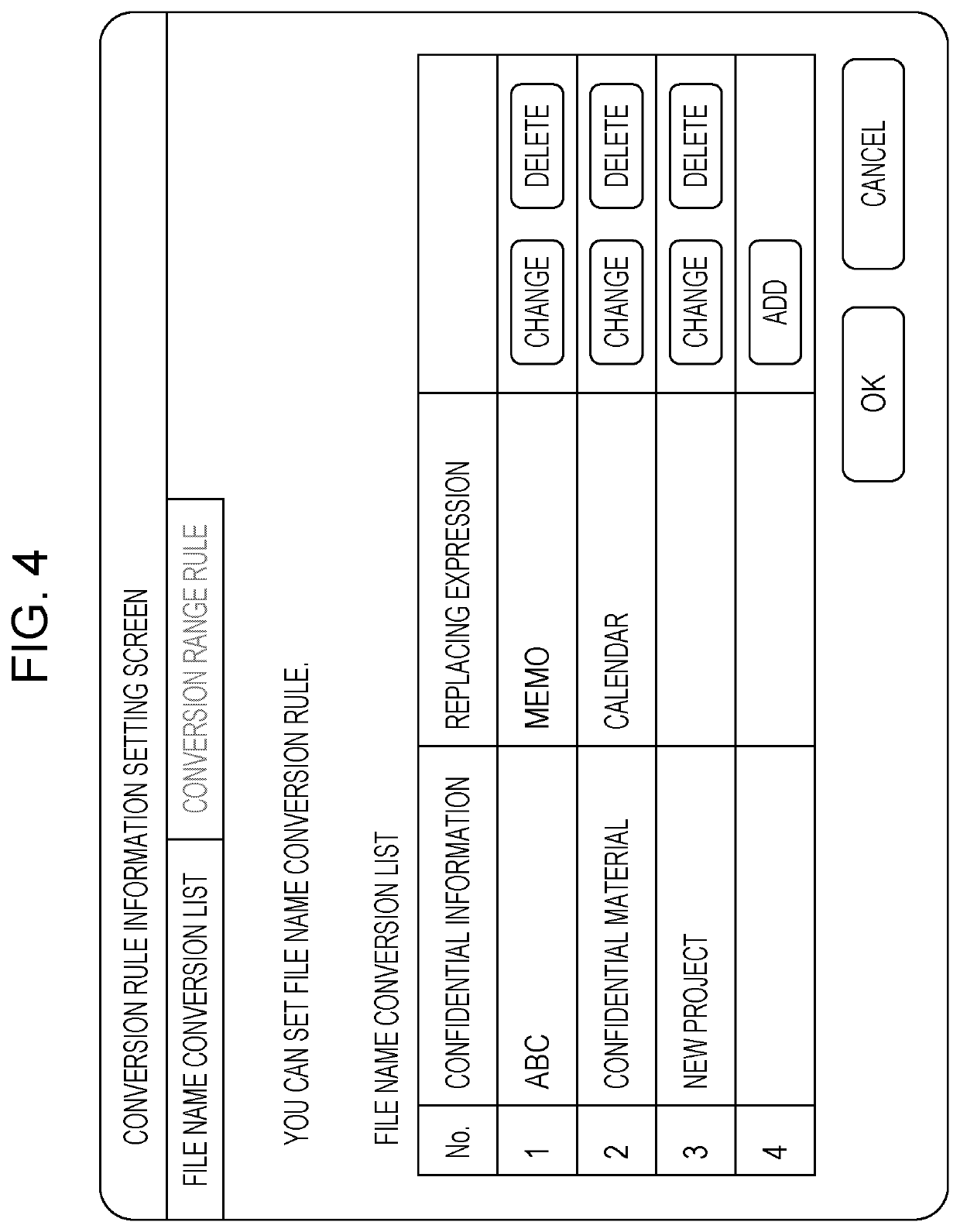
An information processing apparatus includes a processor configured to, in a case where a destination of a job is a shared apparatus shared by plural groups and a file name of a file to be processed by the job includes confidential information, transmit the job to the shared apparatus after converting the confidential information into a different character string.
Owner:FUJIFILM BUSINESS INNOVATION CORP
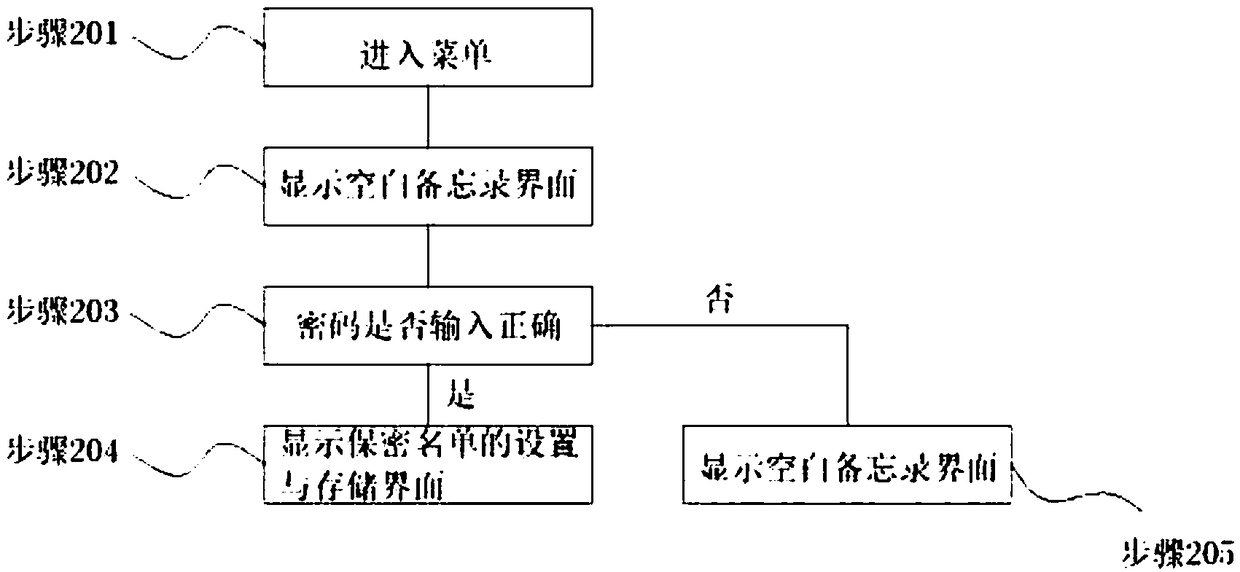
A method for secure call connection
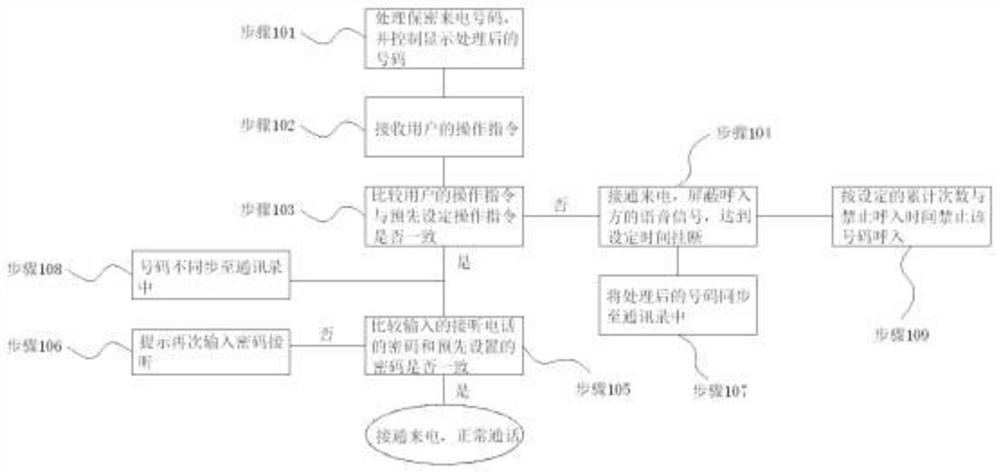
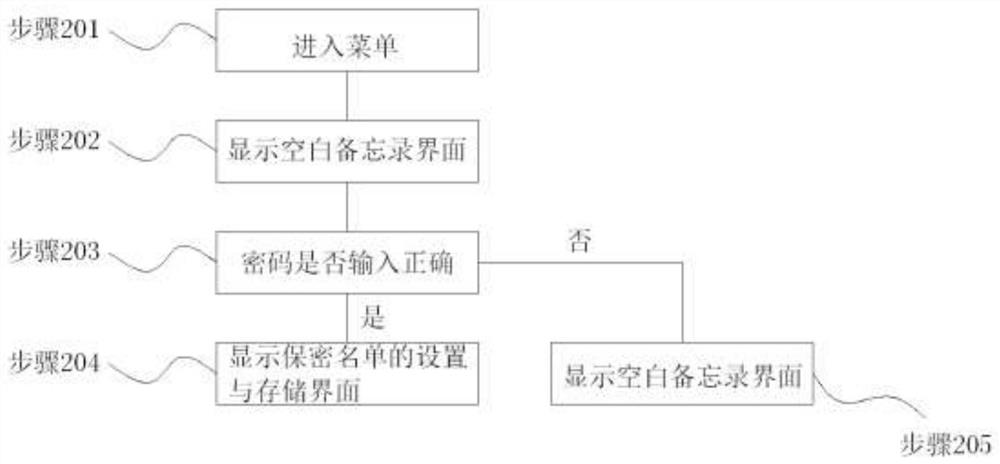
ActiveCN108184212BAvoid privacyAvoid disclosure of confidential informationDigital data protectionCommmunication supplementary servicesInternet privacyPassword
The invention discloses a safe call connection method. The method includes: randomly changing the multi-digit number at the end of the caller number in the secret list to other numbers, and displaying the changed caller number as the caller number, receiving the user's operation instruction, and comparing the user's operation instruction with the preset number. Check whether the set operation instructions are consistent, if yes, enter the password input interface, compare whether the input password is consistent with the preset password, if yes, then connect the phone. The present invention can effectively prevent others from answering the user's mobile phone without authorization when the mobile phone is not with the user, causing the user's relevant privacy or confidential information to leak, effectively protecting the information security of the mobile phone user, and it is not easy for the answerer to find that the user is deliberately Protects and works great.
Owner:JIAGUTECH CO LTD +1
Secure call connection method
ActiveCN108184212AAvoid privacyAvoid disclosure of confidential informationCommmunication supplementary servicesDigital data protectionPasswordInformation security
The invention discloses a secure call connection method. The method includes the following steps: randomly changing the multi-digit numbers at the tail of an incoming call number in a secret list intoother numbers, displaying the changed incoming call number as the current incoming call number, receiving an operation instruction of a user, comparing whether the operation instruction of the user is consistent with a preset operation instruction, if yes, entering a password input interface, comparing whether an input password is consistent with a preset password, and if yes, putting through a call. According to the scheme of the invention, the phenomena that other people answer a mobile phone of the user without permissions when the mobile phone is not carried by the user and the leakage ofrelevant privacy or confidential information of the user is caused can be effectively prevented, the information security of the mobile phone user can be effectively protected, mobile phone receiverscannot easily find that the user protects information deliberately, and an excellent use effect can be achieved.
Owner:JIAGUTECH CO LTD +1
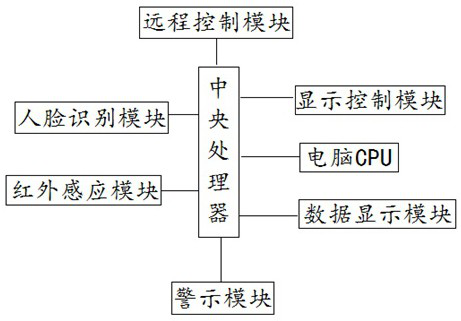
Office safety management system based on Internet-of-things
InactiveCN112395655AAvoid disclosure of confidential informationHigh degree of intelligenceCharacter and pattern recognitionInternal/peripheral component protectionInternet of ThingsSystems design
The invention discloses an office safety management system based on the Internet of Things. The office safety management system comprises a central processing unit, and a face recognition module, an infrared induction module, a display control module, a computer CPU, a data display module, a remote control module and a warning module which are connected with the central processing unit. By means of scientific and reasonable system design, on-off control can be automatically conducted when the staff leaves or returns, leakage of confidential information is effectively avoided, meanwhile, the staff can be automatically reminded after leaving for a long time, remote on-off control can be automatically conducted, the intelligent degree is high, and the system is worthy of application and popularization.
Owner:马鞍山揽月工业设计工作室
Image processing apparatus, method of controlling the same, and storage medium
InactiveUS20190020786A1Avoid disclosure of confidential informationDigital data protectionPictoral communicationComputer hardwareImaging processing
The image processing apparatus capable of executing a transmission job for transmitting image data to a destination that accepts a setting for notifying an end of the transmission job, converts image data to image data of a first format without encrypting, and executes a first transmission job for transmitting the image data of the first format. In accordance with the setting, the image data of the first format and an end of the first transmission job are notified to a predetermined destination. In addition, the image data is encrypted to convert it to image data of a second format, and a second transmission job for transmitting the image data of the second format is executed. In accordance with the setting, an end of the second transmission job is notified to the predetermined destination.
Owner:CANON KK
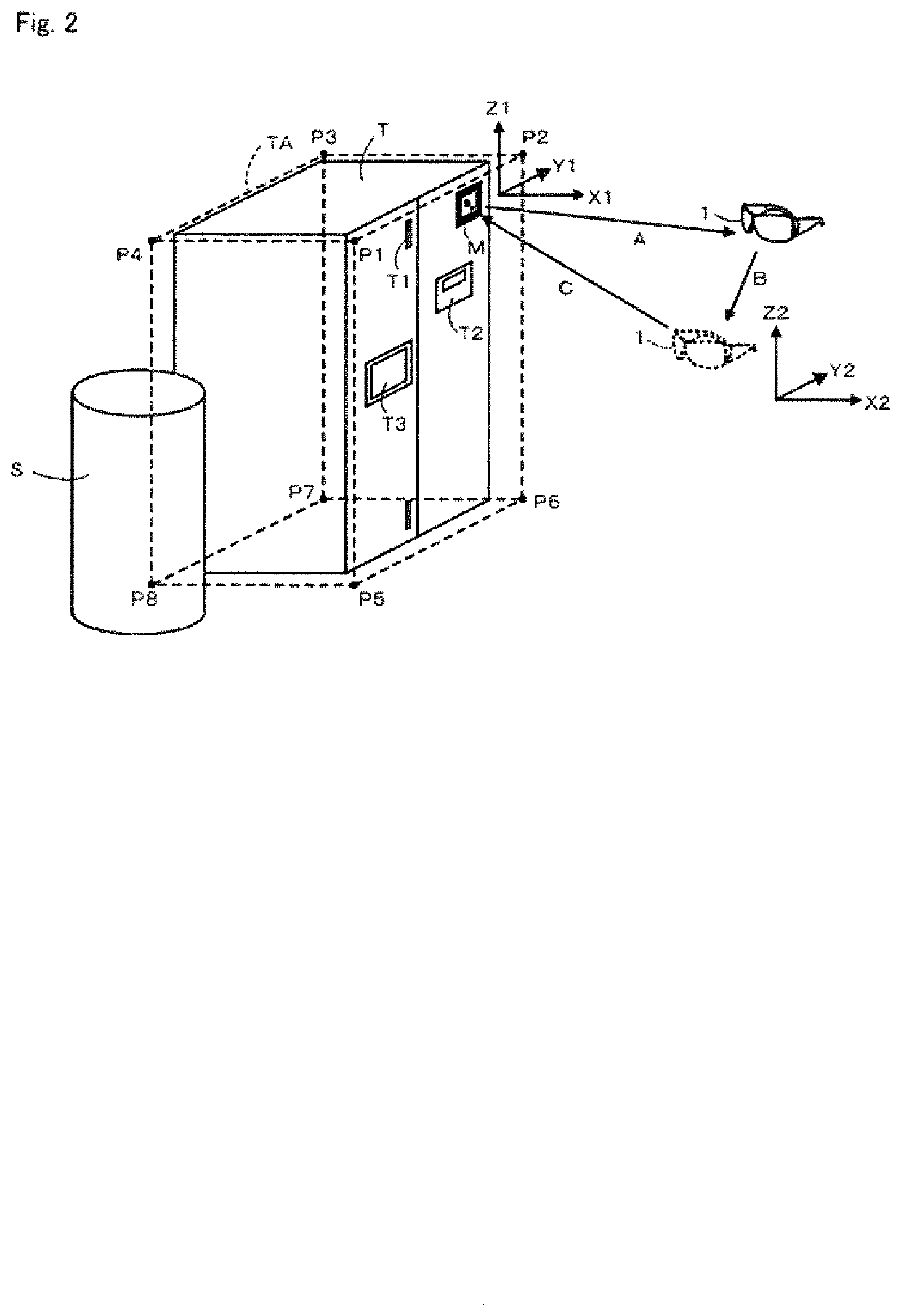
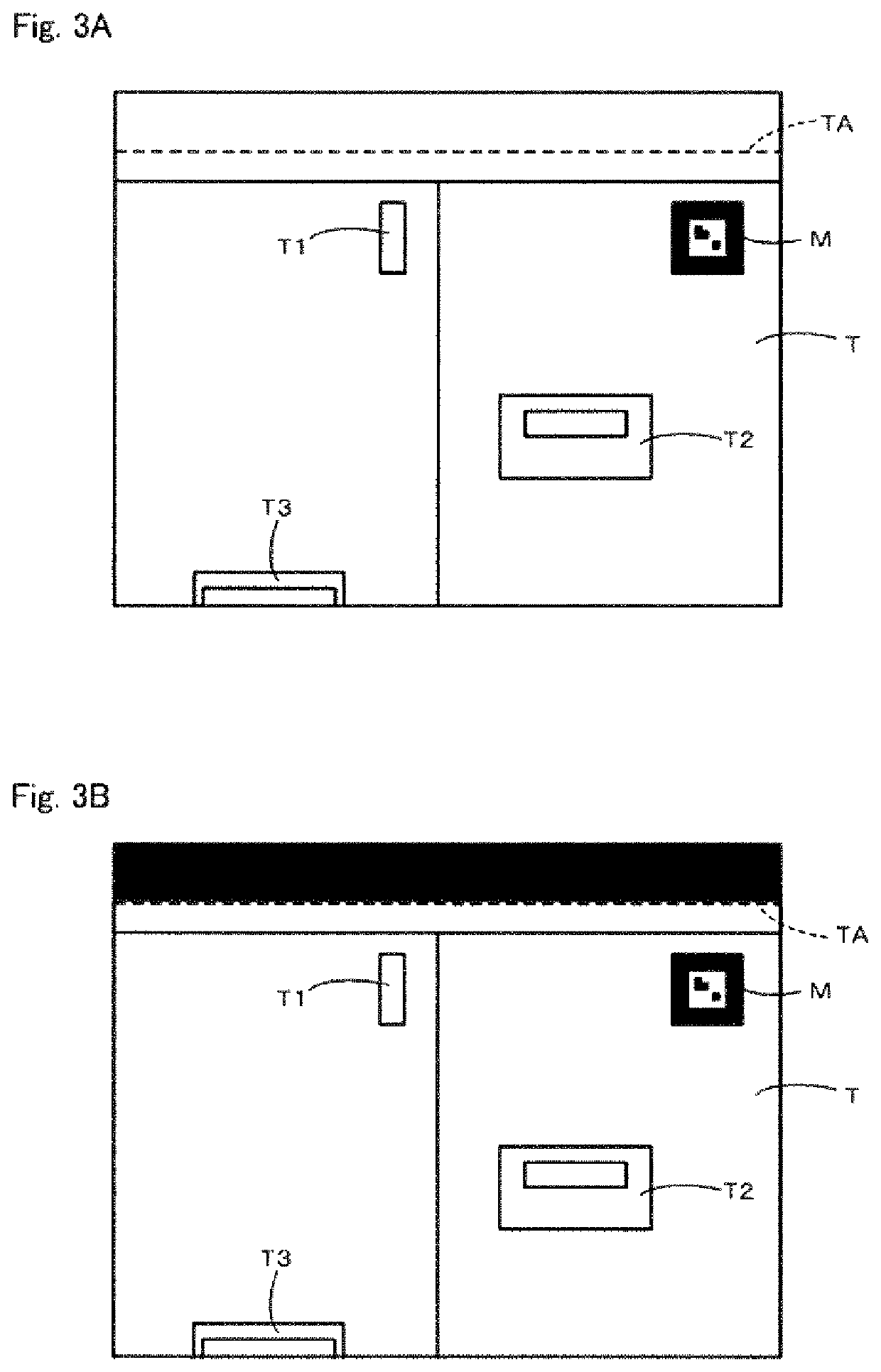
Maintenance support system, maintenance support method, and program
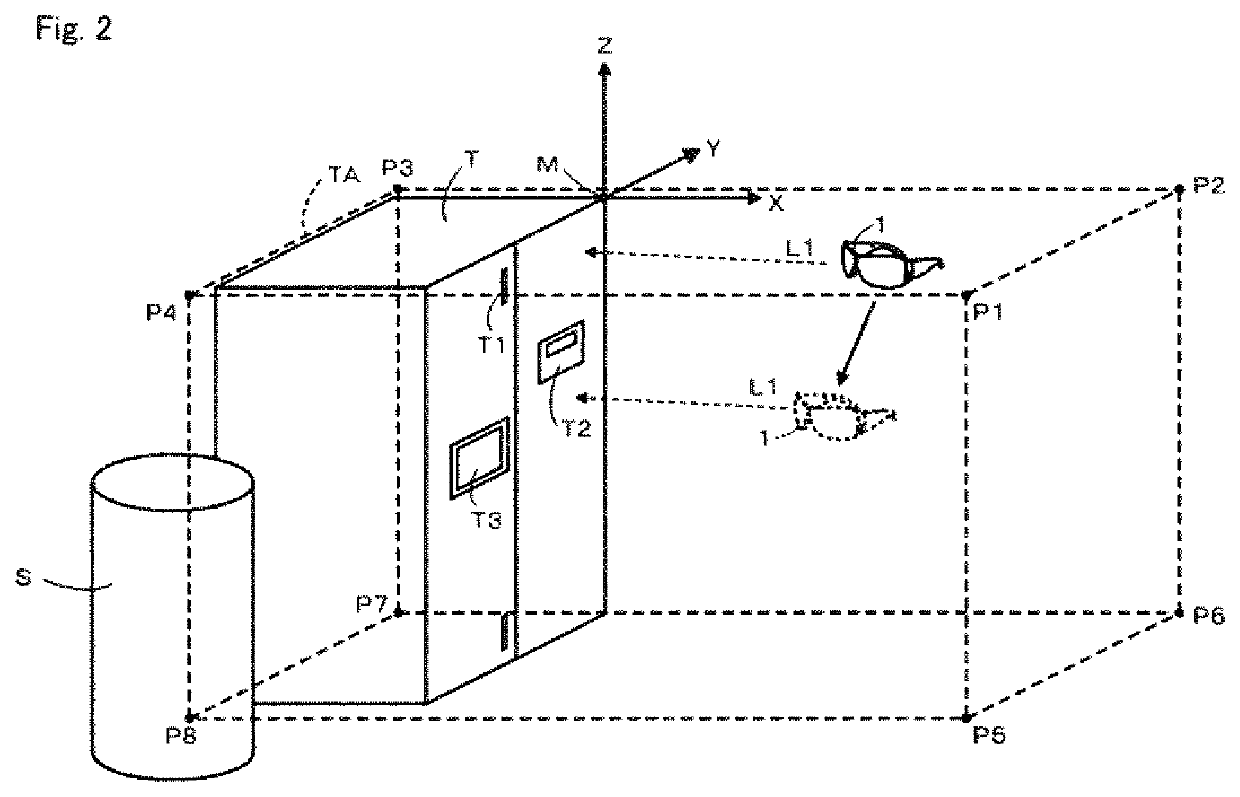
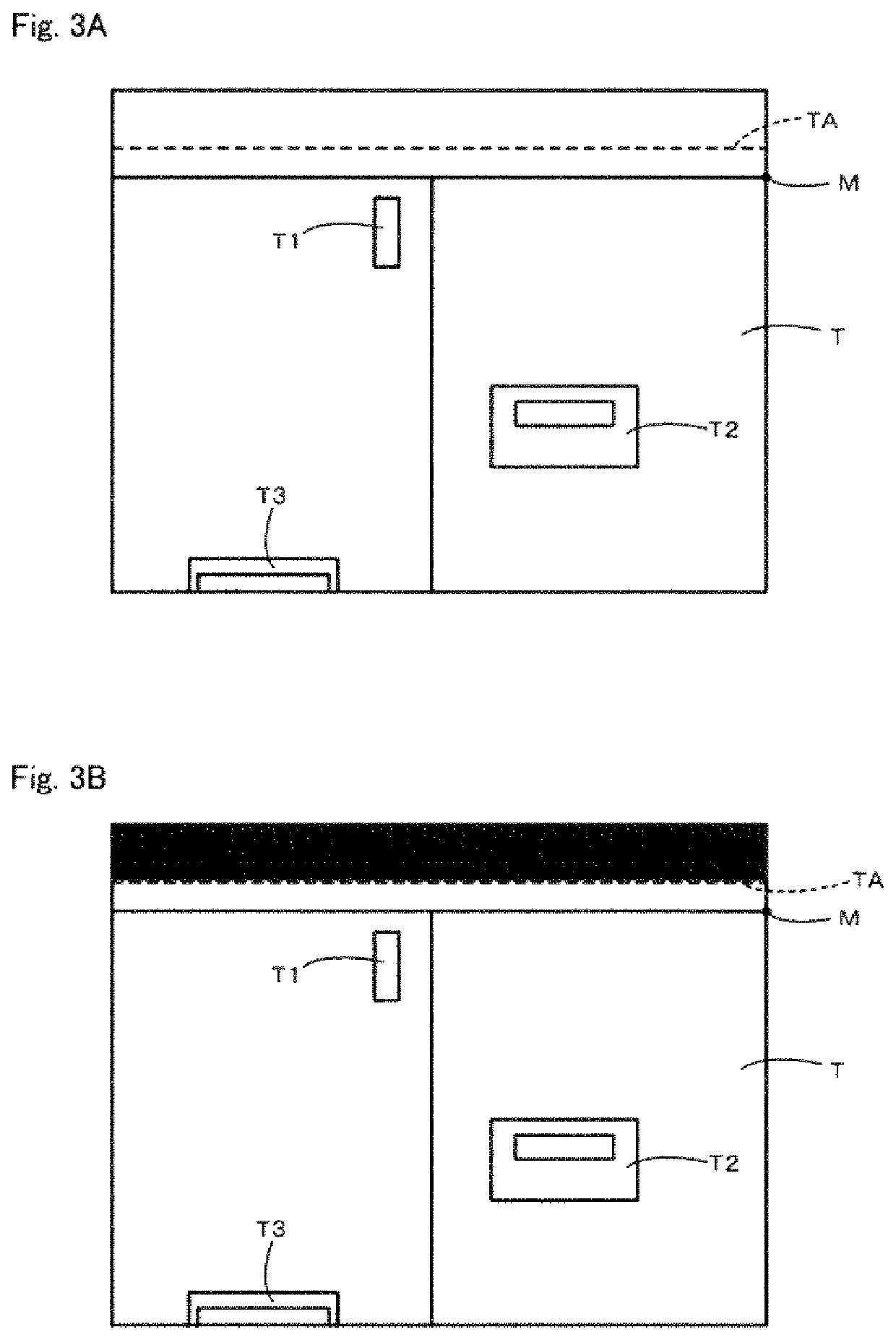
PendingUS20220165044A1Prevent leakageRestricting imaging conditionImage enhancementImage analysisComputer visionImaging equipment
A maintenance support system includes a terminal including an imaging device, a device configured to identify a three-dimensional area TA including a maintenance target T with reference to a predetermined reference point, a device for identifying a position (vector A) of the imaging device in an initial state with respect to the reference point, a device for identifying a change of position (vector B) from the initial state of the imaging device, a device for identifying a position (vector C) of the reference point with reference to the imaging device in a post-movement state in which the terminal has moved, and identifying a pixel area corresponding to the three-dimensional area in a captured image, and a device for generating a processed image in which a portion other than the pixel area is made invisible. A communication device is provided for transmitting the processed image to a support terminal.
Owner:SUMITOMO PRECISION PROD CO LTD
Image processing apparatus, image forming apparatus, confidential information management method, and recording medium
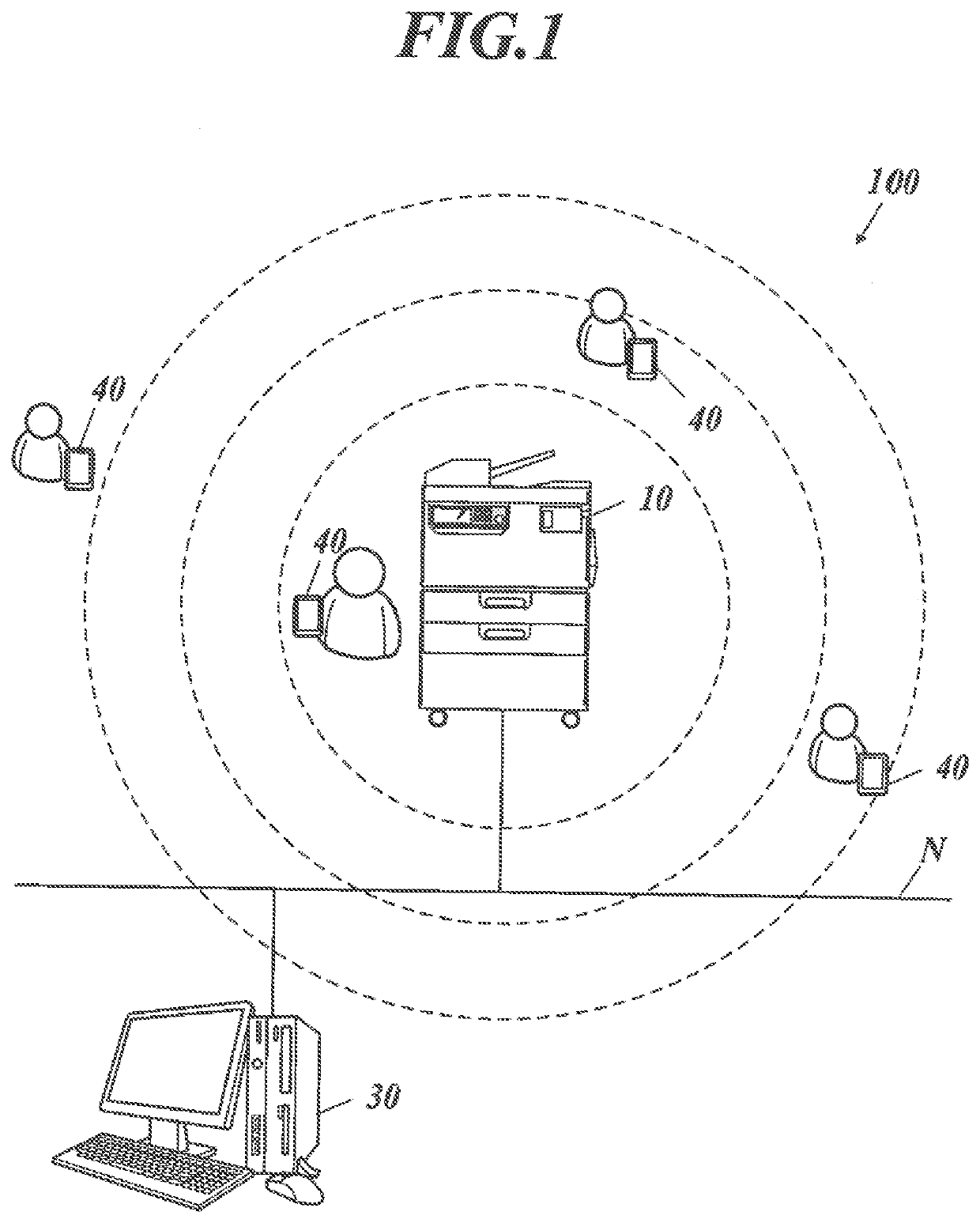
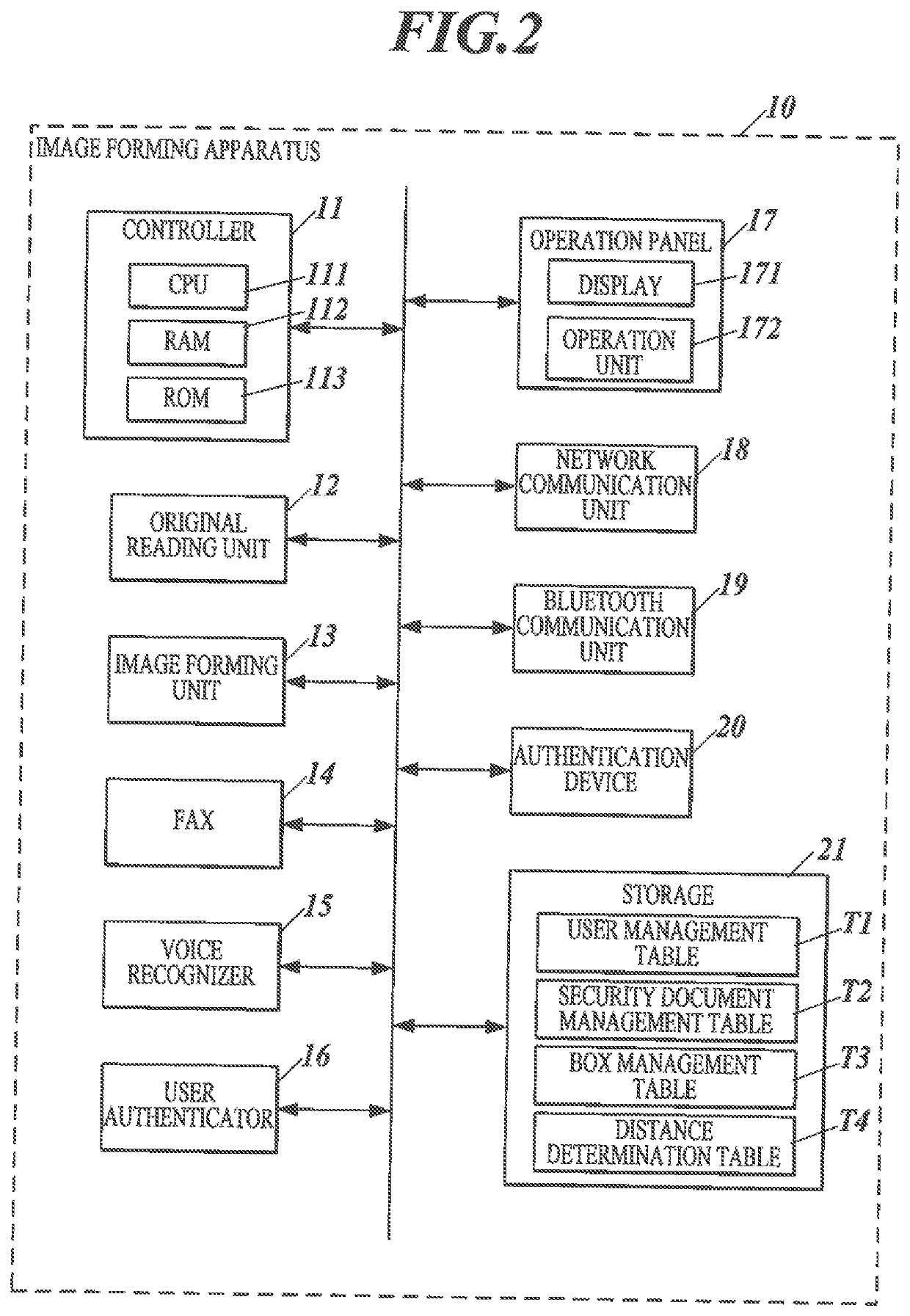
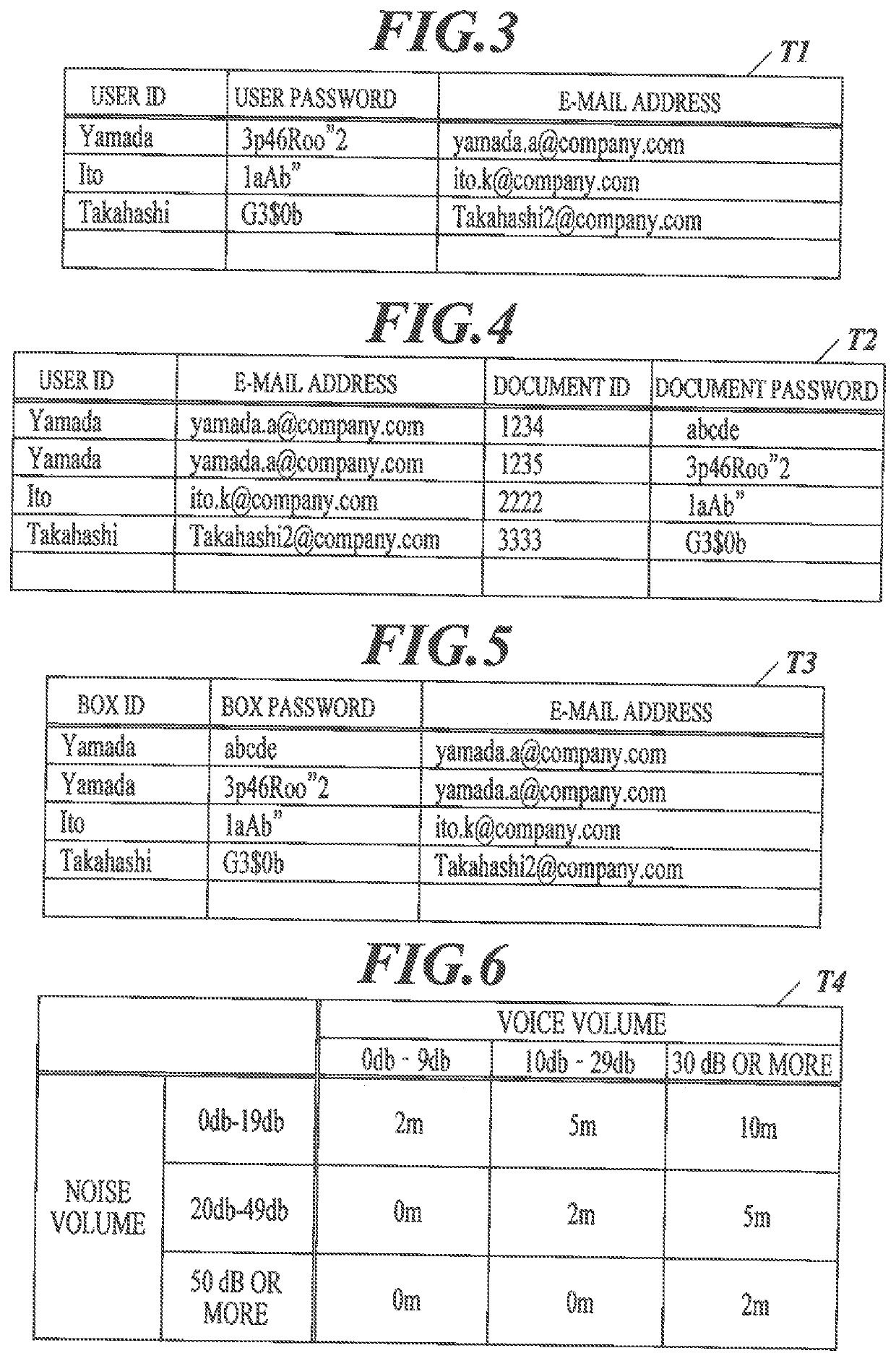
PendingUS20220139397A1Avoid disclosure of confidential informationDigital data authenticationSpeech recognitionComputer hardwareImaging processing
An apparatus includes: a hardware processor that executes, based on recognized information obtained by voice recognition, a process requiring an execution authority; and an authenticator that performs authentication to determine, using first confidential information that is preset, whether the execution authority has been given. Upon determining that the recognized information corresponds to the preset confidential information, the hardware processor provides a user with a predetermined notification regarding security of the preset confidential information.
Owner:KONICA MINOLTA INC
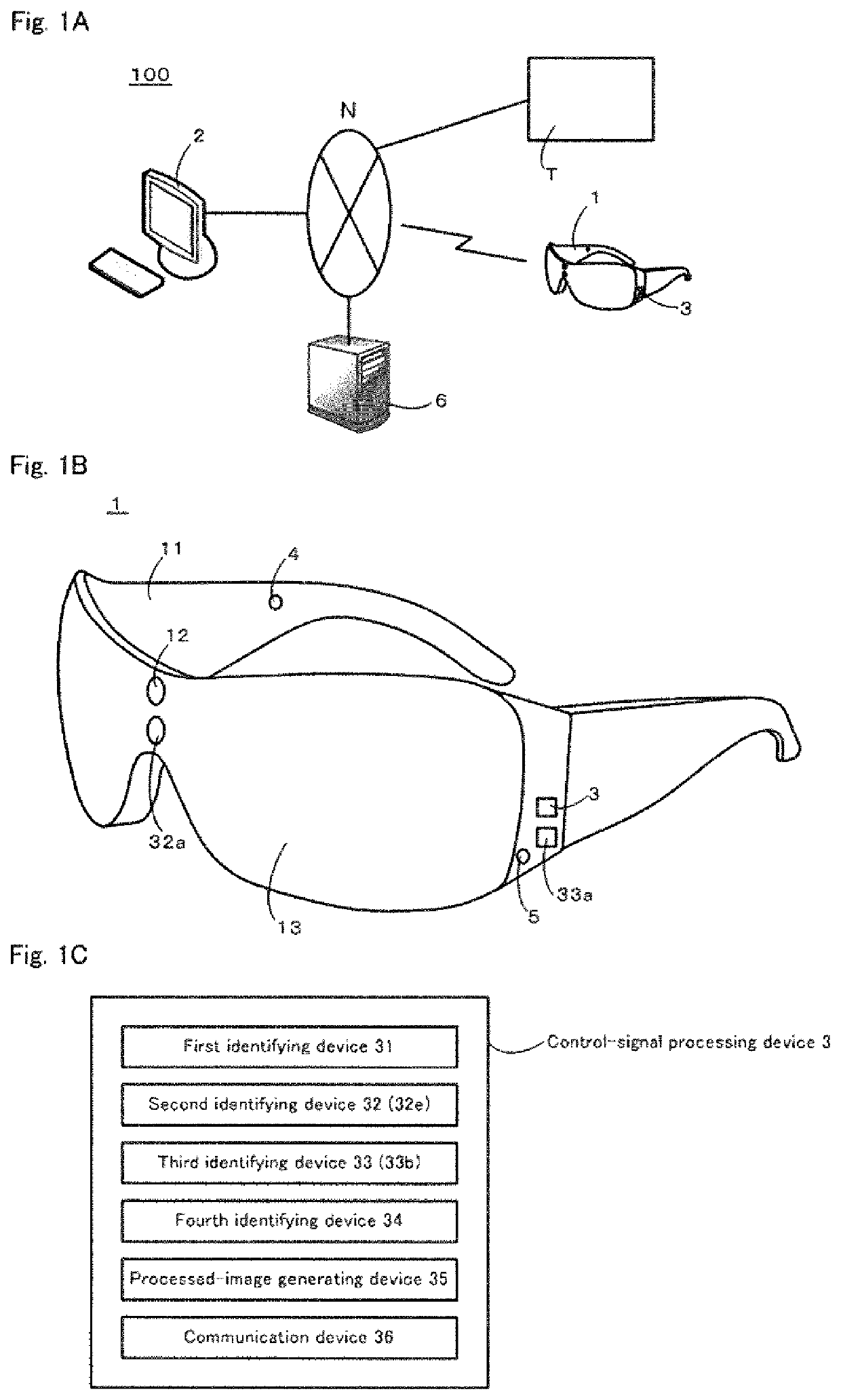
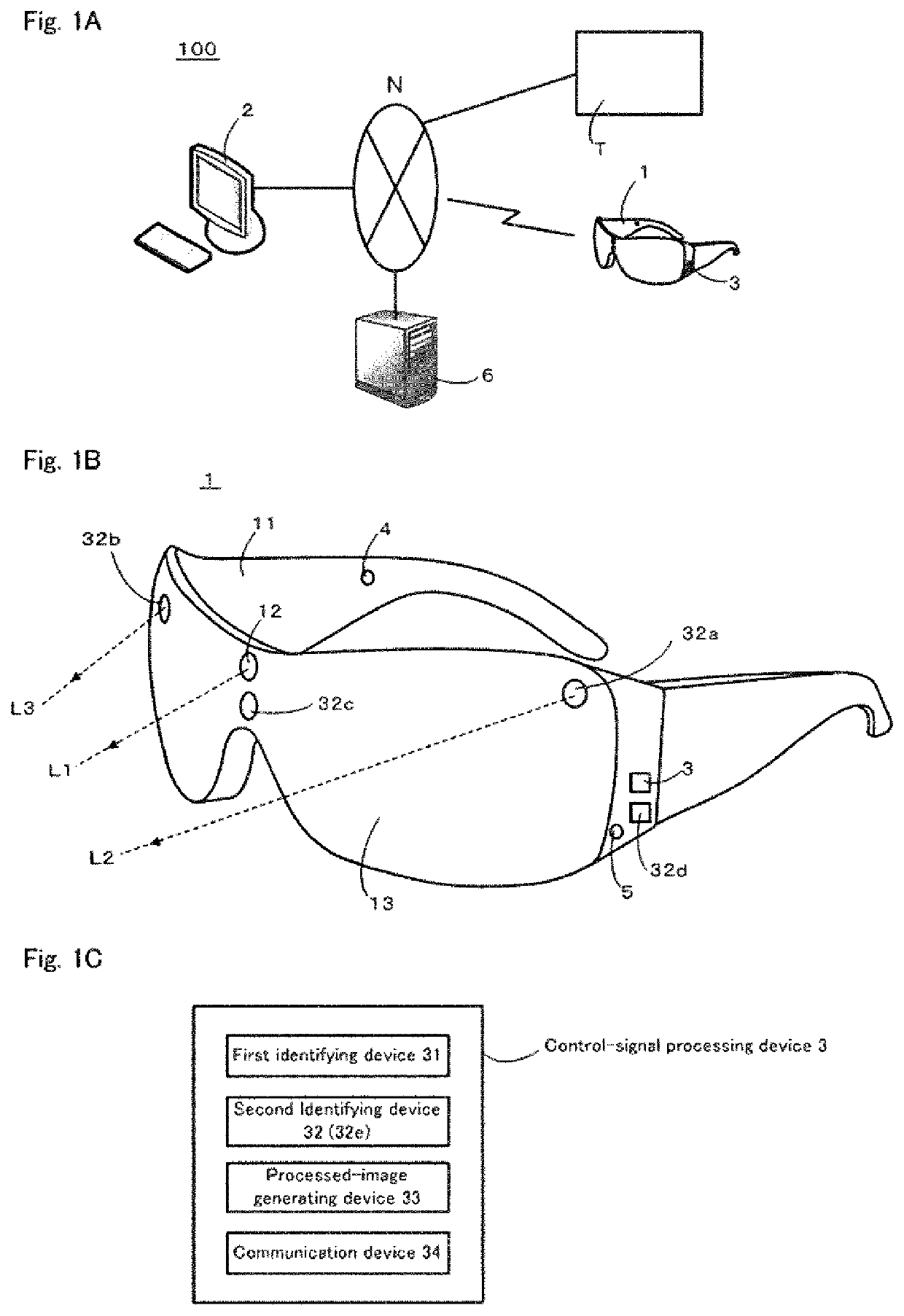
Maintenance support system, maintenance support method, program, method for generating processed image, and processed image
PendingUS20220012868A1Prevent leakageReduce restrictionsImage enhancementImage analysisImaging conditionSystem maintenance
A maintenance support system prevents leakage of confidential information by excluding a maintenance target while imposing few restrictions on imaging conditions. A maintenance support system 100 includes a wearable terminal 1 including an imaging device 12, a first identifying device 31 configured to identify a first three-dimensional area TA including a maintenance target T with reference to a predetermined reference point M, and a second identifying device 32 configured to identify a mask pixel area excluding an effective pixel area corresponding to the first three-dimensional area for a captured image acquired by the imaging device in a post-movement state in which the wearable terminal has moved. A processed-image generating device 33 is configured to generate a processed image in which the mask pixel area is made invisible and a communication device 34 is configured to transmit the processed image to a support terminal 2.
Owner:SUMITOMO PRECISION PROD CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com