Method, device and equipment for identifying risk content
A risk and content technology, applied in the field of identifying risk content, can solve the problems of risk content identification, manufacturing, difficulty, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
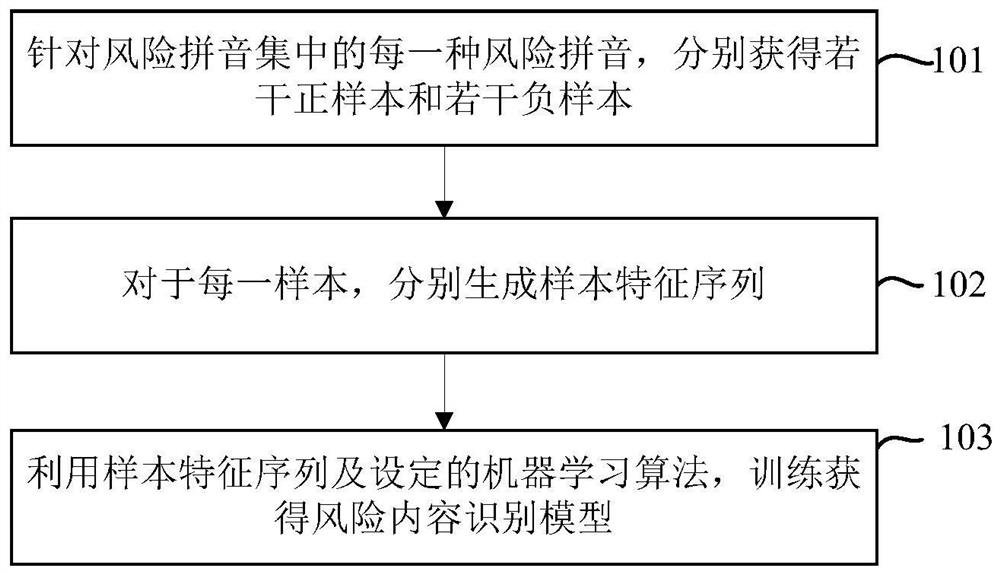
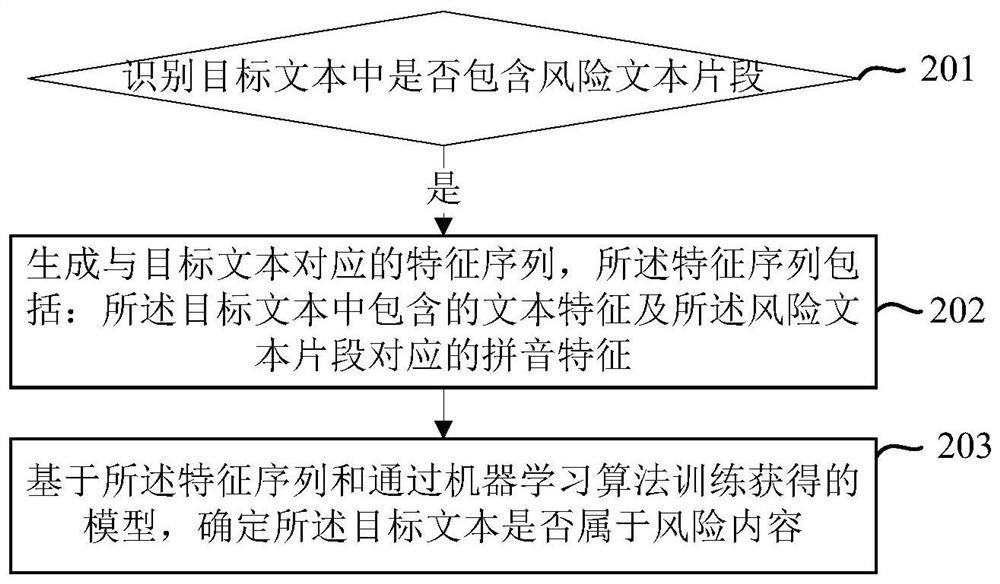
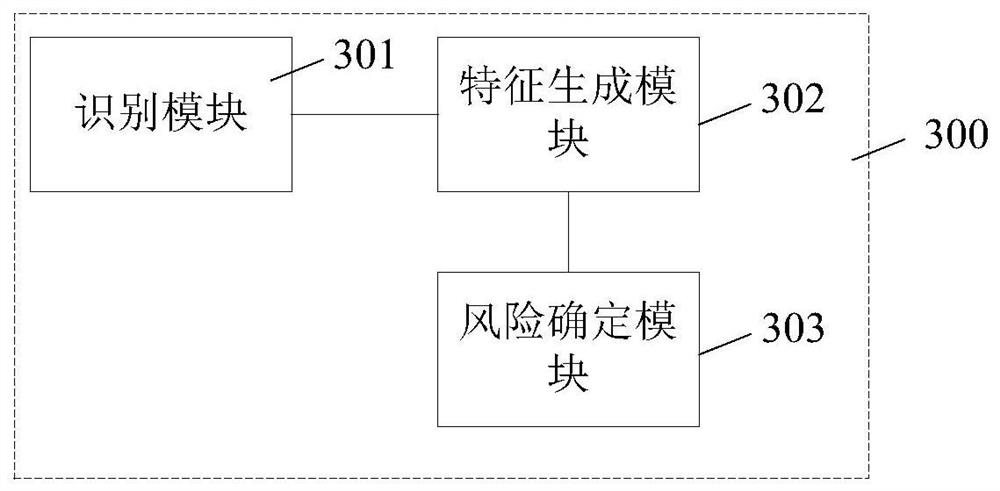
[0025] At present, in order to prevent the published content from being identified as risky content (risky content refers to information that has a negative impact on the purity of the network environment), information publishers create more and more variant information, which makes the identification of risky content difficult. difficulty. Generally, the methods of variation include but are not limited to: using homophones, or English, or abbreviated letters, or deformed Chinese characters, etc. to replace sensitive words in sentences that originally belonged to risky content. For example: "I lost 41,000, dog, fart, chicken, gold, cut the meat", "Interested + I'm Weixin sd232433, Huakoubei will help you mention it", etc. Among them, replacing "fund" with "jijin", "WeChat" with "weixin", and "huabei" with "huakoubei" all make identification more difficult. On the other hand, if only homonyms are considered, but the context of the sentence is not considered, there is a possibi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com