Method and device for distributing cloud security resources
A resource and security technology, applied in the field of cloud security, can solve problems such as cloud security service demand differentiation
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
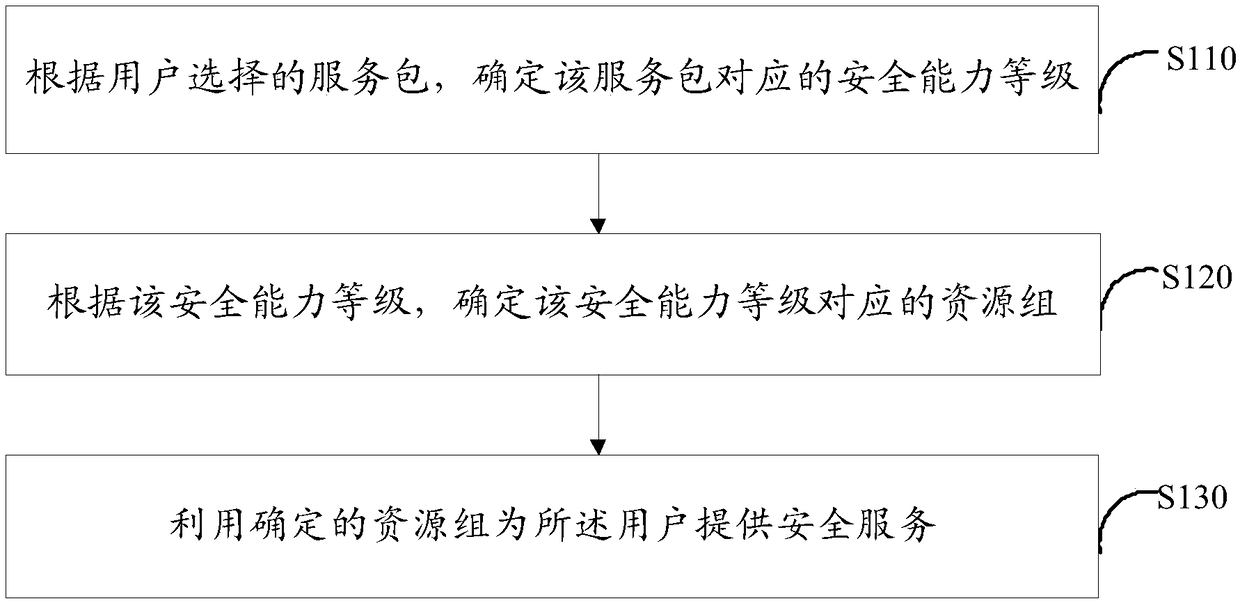
[0047] Embodiment 1 of the present invention provides a method for allocating cloud security resources, see figure 1 , the method includes:
[0048] S110. Determine the security capability level corresponding to the service package according to the service package selected by the user;
[0049] S120. According to the security capability level determined in step S110, determine a resource group corresponding to the security capability level;
[0050] S130. Use the resource group determined in step S120 to provide security services for the user.
[0051]Wherein, the service package includes multiple labels, and the security capability level is only one of them, that is, the correspondence between the service package and the labels is a one-to-many correspondence.
[0052] Among them, the service package includes preset service requirements; specifically, the service requirements include the processing capacity required to handle security events (the size of the security capabi...
Embodiment 2
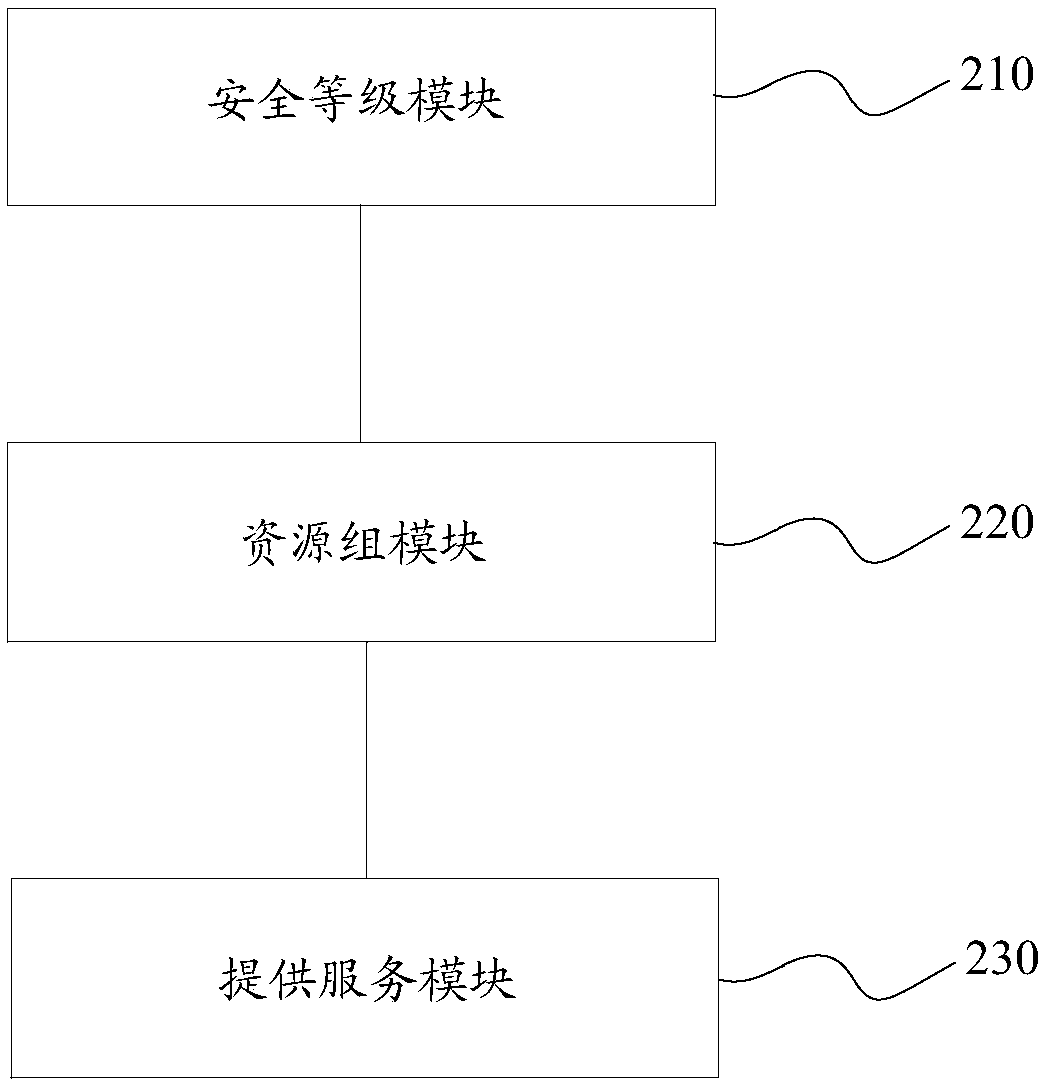
[0099] Embodiment 2 of the present invention provides a device for allocating cloud security resources, see figure 2 , the method includes:
[0100] The security level module 210 is configured to determine the security capability level corresponding to the service package according to the service package selected by the user; wherein, the service package includes preset service requirements, and the service requirements include the size of the security capability;
[0101] A resource group module 220, configured to determine a resource group corresponding to the security capability level according to the security capability level;
[0102] A service providing module 230, configured to use the resource group to provide security services for the user.
[0103] Specifically, the resource group module 220 is specifically used for:
[0104] If there are multiple resource groups corresponding to the security capability level, and the service package includes the user information,...
Embodiment 3
[0118] Embodiment 3 of the present invention provides a computing device, including a memory, a processor, and a computer program stored in the memory and operable on the processor. When the processor executes the program, the implementation of A method for allocating cloud security resources described in Example 1.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com